
Verizon boosts software defined networking with Cloud IP Platform
Businesses are moving more of their systems to the cloud and that includes infrastructure projects like networking and provision for branch offices.
Telecoms provider Verizon is updating its software defined networking (SDN) platform with a new Software Defined Secure Branch (SD-Branch) managed service powered by Versa Networks' Cloud IP platform.

Bitcoin Cash breaks $1,000
The new offshoot of Bitcoin has dropped in value after reaching a record high which saw the cryptocurrency peak at over $1,000.
Last month, a group of Bitcoin miners implemented a hard fork of the blockchain and as a result Bitcoin Cash was created. On Friday of last week, the offshoot was able to surge by 40 percent in a single day and it reached $600.

Here's what's new in Android 8.0 Oreo
Yesterday Google finally revealed Android 8.0, also known as Oreo. Aside from the name, release date and the question of whether individual handsets will be treated to an upgrade, the query on most Android users' lips is "what's new?".
Google says that one of the primary aims with Oreo was to create "fluid experiences," as well as improving speed and efficiency. The company says that it is "smarter, faster, more powerful and sweeter than ever" -- but what does this actually mean in terms of new features?
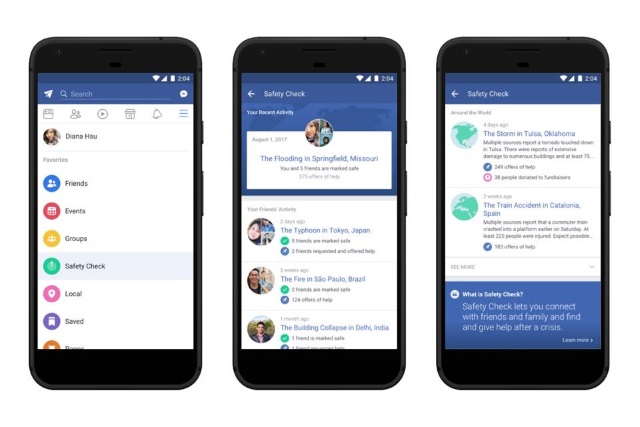
Facebook introduces a dedicated button to make it easier to access Safety Check
Facebook's Safety Check feature has been around for some time now, giving people the chance to use the social network to let friends and family know they're OK in the event of a natural disaster or other catastrophe.
It is Facebook that decides which events warrant activation of Safety Check, and until now it has also been down to the site to advertise the feature to users so they can either mark themselves safe, or check up on others -- but this is about to change.

Linksys begins selling the WRT32X AC3200 MU-MIMO open source gaming router
Routers are getting more powerful and elaborate nowadays. What was once a device that a person would set up and then never pay any mind (except when he/she needed to reboot it), has become much more. Ostentatious designs with multiple external antennas are not just for performance, but they can also make wireless routers focal points of a room. For some consumers, these routers can even be seen as works of art. While appearance is obviously good for sales and marketing purposes, it can actually benefit some users too. After all, if a wireless router is put in, say, a living room, it is important that it looks attractive too. It really does matter.
Today, Linksys finally begins taking pre-orders for a wireless router that we covered at the beginning of the year, called WRT32X. This router is quite intriguing for many reasons. For one, it is being listed as a "gaming" device, and thanks to the use of Killer Networking KPE technology, that could be more than just marketing. Another interesting aspect is the beautiful design -- it looks both angry and intimidating, and yes, that is a good thing. If this was put next to an Xbox or gaming PC, it would totally fit in. Most intriguing, however, is that theWRT32X is open source-friendly so you can flash alternative firmware, such as OpenWrt.

Cyber-security is an investment, not a burden
CEOs across the UK are increasingly seeing cyber-security not as a burden, but rather an investment opportunity, a new study has claimed.
The KPMG CEO Outlook 2017 report, based on a poll of 150 CEOs in the UK, found that 70 percent considered investing in cyber-security an opportunity to find new streams of revenue.

Black Lab Enterprise Linux 11.0.3 Ubuntu-based operating system now available
The perfect Linux distribution doesn't exist. Take it from someone that does a lot of distro-hopping -- you will find yourself searching forever. Instead, it is wise to find a Linux-based operating system that meets your needs and try to stick with it. After all, constantly fiddling with various distributions will just drain your energy and steal your time.
With that said, Black Lab Enterprise Linux 11.0.3 is now available. Should you download it? Well, if you are not satisfied with your current Linux-based operating system, then maybe. I've got to tell you, this Ubuntu-based distro looks like a winner. It features modern versions of both Google Chrome and the Linux kernel, plus it offers support for many file systems. Despite being designed for organizations, it should serve as a great desktop OS for home users too.

Android 8.0 Oreo is here, and as usual, your device will probably never get it -- hooray!
Look, we all knew Android 8.0 would probably be called "Oreo," and we now have confirmation. Today, Google releases 8.0 of its Android operating system and officially names it "Oreo" after the sandwich cookie. This is the search-giant's second time partnering with a brand for a dessert name, with the other time being "Kit Kat". Strangely, Google even used the solar eclipse to promote the Oreo name.
Truth be told, it does feel kind of cheap and commercialized to have a corporate product tie-in. After all, if Windows 10 was named "Slim Jim," for example, and Microsoft urged you to snap into its operating system, consumers would be up in arms. When Google does, it, however, people celebrate.

Hackers can disable your car's safety systems
Hackers could disable a modern car's airbags and other safety systems, putting the driver and the passengers at grave risk, according to a new warning.
Researchers from security firm Trend Micro have revealed a flaw that could allow the controlling network of a connected car to be overloaded, allowing possible hackers to compromise key systems in the vehicle, including safety aspects.

Xbox One X Project Scorpion Edition now available to pre-order
The Xbox One X will not hit store shelves until November 7, but, as you may know, it is slated to be available for pre-order well ahead of its big release.
And, like expected, pre-orders for the Xbox One X just kicked off. On offer is a special edition of Microsoft's latest and greatest gaming console, which is dubbed Project Scorpio Edition. The price?

HTC Vive VR gets a significant price cut
Most consumers are either unfamiliar with VR headsets or not interested in owning one. Part of the problem, at least with devices like HTC Vive VR, is the high price, which is hard to justify when we're talking about a technology in its infancy.
However, as the barrier of entry is lowered, VR headsets will become more appealing to a larger number of consumers. HTC is aware of this, which is why it's given the Vive VR a major price cut.

Barclays lets businesses view banking data in real-time
Small businesses struggling to keep track of all their data as they grow have been given a helping hand thanks to a new tool from Barclays.
Designed for SMEs experiencing a surge in growth, SmartBusiness Dashboard offers a place for companies to view all real-time banking data and information about their business in one place.

Intel's new 8th-gen Core processors promise massive performance gains
Intel today unveils a new generation of Core processors, promising a massive performance improvement over the Kaby Lake range announced nearly a year ago.
Just how big of a gain can you expect? Intel says that the 8th-gen Core line is up to 40 percent faster over the previous generation. Compared to a "five-year-old machine," however, the difference is even more substantial, delivering a boost in performance of up to 200 percent.

Get 'Successful Time Management For Dummies, 2nd Edition' ($12 value) FREE for a limited time
If you always feel like there's not enough time in the day to get everything accomplished -- and we certainly do! -- this is the resource that can help change your workday and your life.
Filled with insights into how the most successful people manage distractions, fight procrastination, and optimize their workspace, Successful Time Management For Dummies, 2nd Edition provides an in-depth look at the specific steps you can use to take back those precious hours and minutes to make more of your workday and your leisure time.

How network segmentation can help contain cyber attacks
Cyber crime continues to be a major problem globally and companies are seeking new ways of combating it.
However, there are some older technologies that remain an effective defense. One of these is network segmentation, and network security specialist Tufin Technologies has produced an infographic explaining how segmentation works and how it can help keep organizations secure from today’s sophisticated cyber attacks.



