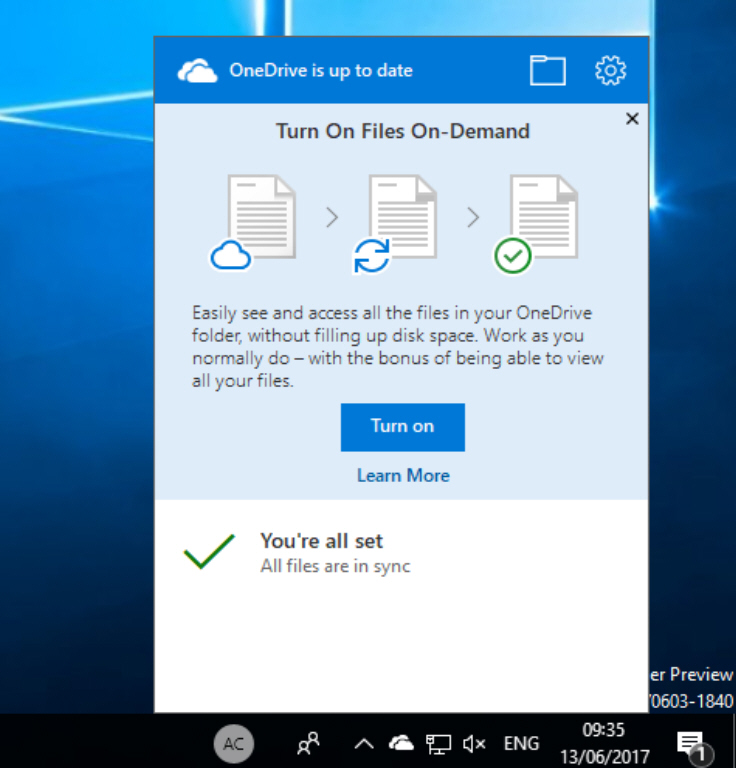
Windows Insiders can now try out OneDrive's Files On-Demand feature -- here's how
Microsoft announced a new Files On-Demand feature for OneDrive at Build last month. This lets you access all of your files in the cloud without having to download them first.
The files you have stored in OneDrive can be viewed in File Explorer and interacted with just like every other file on your device. If you used OneDrive on Windows 8.1 previously, you’ll be familiar with idea as it’s essentially an improved version of the old placeholders feature.

Nintendo very briefly confirms new Pokémon game on Switch
Likely to emerge as the biggest story out of today's latest round of news at the 2017 Electronic Entertainment Expo (E3), Nintendo has announced that it is working on a new Pokémon title for its Switch console.
In the very brief announcement, the title was described as a new entry to the "core RPG" series of Pokémon games. Presumably that means it will be the launching pad for a new generation of Pokémon creatures, and if so, it would be the first time that has happened on a home console.

Yahoo is now officially Verizon's problem and Marissa Mayer waves goodbye
Verizon today reveals that it has completed the acquisition of Yahoo, nearly a year after announcing the deal. Big red initially agreed to pay $4.83 billion, but after the massive security breach that resulted in over one billion hacked accounts was disclosed to the public the value dropped to $4.48 billion.
What is interesting is that Yahoo will not operate as an individual subsidiary, as you might expect. Instead, Verizon will combine it with AOL under a different brand, called Oath, which it describes as a "diverse house of more than 50 media and technology brands that engages more than a billion people around the world."

Creative unveils Sound BlasterX AE-5 gaming sound card with 32-bit DAC and RGB lighting
If you thought the concept of a sound card was dead, you'd be wrong, but I wouldn't blame you for thinking it. After all, on-board motherboard sound is often excellent, and many people will choose a USB DAC nowadays as an upgrade.
Today, Creative unveils a new PCIe sound card that will get you excited. Called "Sound BlasterX AE-5," it is chock full of features and impressive specs. While overkill for most, it features an insane 32-bit/384kHz DAC. It offers connectivity for a 5.1 speaker setup. Since this is a gaming product in 2017, it of course has RGB lighting -- it comes with attachable RGB light strips to illuminate your case. While this card is designed for gamers, it will also be ideal for audiophiles listening to music.

Ransomware attacks are becoming more sophisticated
Following the WannaCry attack last month, ransomware was one of the big topics at the recent Infosecurity Europe event in London.
The worldwide assault woke many businesses and organizations up to the real danger that ransomware poses, but new research has also discovered that the criminals behind such attacks could be gearing up for even bigger attacks soon.
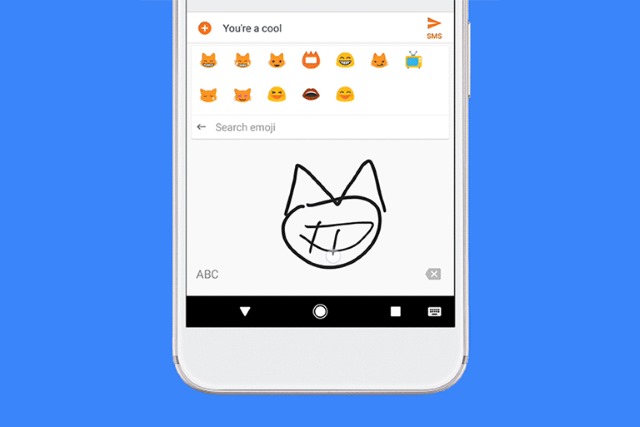
Gboard for Android now recognizes the emoji you draw by hand and suggests phrases for you
Emoji offer a great way to spice up your chats, and the Android version of Gboard has been updated to make it easier to find the perfect ones. The update means you can now use the emoji search box to draw the sort of emoji you're looking for, and Google's keyboard will track down what it thinks you mean.
Google uses machine learning to interpret even the most primitive of squiggles, so now there's no need to think about how you would describe a particular emoji in order to perform a text-based search for it -- just draw what you want! But there's more.

Logitech Circle 2 is a versatile home internet surveillance camera for both inside and outside
Internet-based home surveillance cameras are gaining in popularity nowadays, thanks to decreasing cost and easier setup. These devices allow you to monitor your home using your smartphone for ultimate convenience.
Back in 2015, Logitech unveiled its first such product. Simply called "Circle," it was affordable and easy to use. The problem? It lacked versatility. It didn't offer much in the way of positioning and couldn't be used outside. With that said, the battery aspect allowed it to be moved about a residence. Today, the company unveils the successor -- Circle 2. This time the camera is far more useful, even offering the ability to be used outdoors. There are two models -- wired or wire-free, both of which work with Amazon Alexa.

AI-driven platform improves sales forecasts and visibility
Success in a sales environment increasingly needs access to accurate real-time data on which to base decisions.
To provide companies with better information, sales forecasting specialist Aviso is launching its latest Aviso Sales Vision, an AI-based platform that provides accurate sales forecasts, detailed pipeline visibility, and actionable insights to drive sales performance.

Fedora 26 Beta Linux distro is finally here with GNOME 3.24 and updated LibreOffice
Fedora 26 Beta is finally here! Why do I say "finally?" Well, as is becoming more common nowadays, the Beta release was delayed. This isn't the end of the world, however, as there is nothing wrong with making sure everything is ready -- especially a beta.
While you never want to run pre-release software on a production machine, I must confess that the Alpha version has been rock solid on my laptop -- it is probably safe. With that said, if you can be patient, we should have a final version on July 11. Can't wait for a stable Fedora 26 and like living dangerously? You can download the Beta today -- at your own risk.

What does the scrapping of EU roaming charges mean for UK mobile users?
It's just a couple of days until new EU regulations come into force which makes European roaming charges a thing of the past. Put simply, all mobile operators will have to permit their customers to use their bundled text, call and data allowance within the EU at no extra charge from June 15.
With many UK travelers caught out by high mobile bills after a trip, this change should be great news. But consumer watchdog Which? warns that there could be a catch, and mobile users are warned to continue to keep an eye on their bills.

New platform helps integrate big data across the cloud
As enterprises continue to move their data to the cloud, they often find themselves using multiple different services. But a multi-cloud approach brings problems when it comes to managing and integrating information.
To tackle this issue, cloud and big data integration company Talend is releasing a new version of its Talend Data Fabric integration platform that is optimized to manage multi-cloud, enterprise IT environments.

Enterprises overwhelmed by endpoint alerts
Organizations receive an average of more than 600 endpoint alerts in a typical week according to a new report. These represent a severe drain on an organization's financial resources and IT security personnel and the cost can average $1.4 million annually.
The study by endpoint security company Absolute and the Ponemon Institute reveals that, of all alerts, 45 percent (277 alerts) are considered reliable and an average of 115 are investigated. An average of 61 percent or 369 of these alerts involve malware infections.

Blocked from running security software? AVCertClean can help
Malware will often try to block security software from running, and one of the ways it does this is by adding their code signing certificate to Windows’ Untrusted list.
If you try to run a program with an untrusted certificate, Windows displays a message like "this program has been blocked for your protection", or "an administrator has blocked you from running this program." (These messages can also appear for other reasons.)

Kodi add-ons site TVAddons vanishes from the internet
The negative attention that Kodi has been attracting recently continues. A number of high-profile add-ons, such as Phoenix, have disappeared recently as interest in the piracy potential for the media player increases.
The latest victim appears to be TVAddons, a site which lists unofficial Kodi add-ons. The site was sued last week in a federal court in Texas, so the disappearance is not entirely surprising. But the removal of DNS records -- rendering the site inaccessible -- without any explanation is a little strange.

Microsoft wins Supreme Court case about scratched Xbox 360 discs
With staggeringly coincidental timing, just as Microsoft revealed its upcoming Xbox One X console, the company received some great news from the US Supreme Court. In an 8-0 decision, the court overturned an earlier ruling in what has become a complex and lengthy case.
What originally started off as a fairly simple case around a decade ago about game discs scratched by Xbox 360 consoles, has evolved into quite a different beast. The latest ruling means that a case that was to be brought collectively by tens of thousands of gamers cannot be granted class action status.



