
HPE buys Nimble for $1bn
Hewlett Packard Enterprise (HPE) says it came to an agreement with Nimble Storage to acquire it for approximately $1 billion in cash.
HP Enterprise should assume, or pay out, Nimble’s unvested equity awards, with a value of $200m, at closing. According to Wall Street Journal, the deal has roughly a 41 percent premium to Nimble’s $700m market value.

Oh joy -- playable ads arrive in Windows 10
Playable ads -- that is ads that mimic an app and let you interact with it -- aren’t new. I see them from time to time on my iPhone, and never interact with any of them. Because, why would you? However, Microsoft says that playable ads are not only better than regular ads, they are more profitable.
And now they are arriving on Windows 10. The Playable Ads preview goes live in the Windows Dev Center today, allowing developers to offer their own interactive adverts.
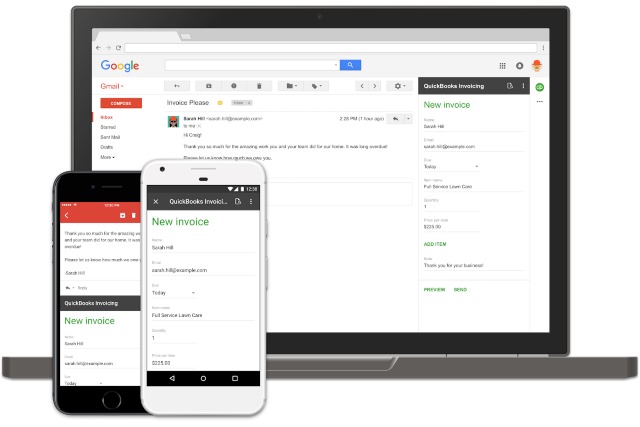
Google is bringing add-ons to Gmail
It's something that Gmail users have been asking for for ages now -- the ability to use third-party add-ons to extend the capabilities of the email service. Today at its Cloud Next conference in San Francisco, Google announced that plugins that can integrate with Gmail are on their way.
While "add-ons" are already around, they exist in the form of browser extensions. What Google is talking about now is native add-ins that are not dependant on Chrome extensions, and will therefore work online in any browser, on just about any device -- including iOS and Android.

TeamViewer unveils web conferencing solution for enterprises
TeamViewer is looking for a piece of Amazon Chime's pie as it introduces a competitor, Blizz by TeamViewer. It is a dedicated web conferencing and collaboration solution, aimed at the needs of small and medium sized businesses and mid enterprise organizations.
The product is available right now, and comes in three plans with different functionalities.
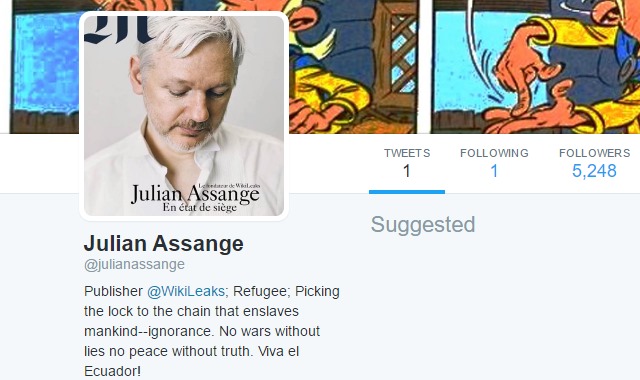
Julian Assange says WikiLeaks will share CIA hacking tools from Vault 7 with technology companies
Technology companies will be given access to the CIA's hacking tools revealed earlier in the week, Julian Assange said today. The WikiLeaks founder said that full details of the exploits used by the CIA would be shared with a view to allowing companies to patch the security holes.
Apple has already said that it has fixed many of the iOS vulnerabilities mentioned in the document cache, and we know that the CIA exploited vulnerabilities in all major operating systems as well as weaponizing numerous popular programs. While WikiLeaks has made certain details of the CIA's hacking tools public, it intends to share them in their entirety privately so software developers can create patches.

Project Scorpio next-generation Xbox gaming console debuts in Microsoft Store
There is a new trend in console gaming, where existing consoles are enhanced rather than replaced. For instance, the Xbox One S and PlayStation 4 Pro aren't really new consoles, but upgrades of the current generation. They may have new features, but they play the exact same games.
Microsoft's next generation of video game console is currently called "Project Scorpio." This will be a truly new console, although it will be backwards compatible with all Xbox One games -- nice. In fact, you will even be able to use your Xbox One controllers and other accessories. While we do not have a definitive date of when it will go on sale, today the next Xbox console makes its debut in the Microsoft Store. We even get a slightly better idea of when it will be in stores.

Samsung Galaxy S6 and Galaxy S6 edge receive Android 7.0 Nougat
If you look at Google's Android distribution chart you will see that very few devices run Nougat. Despite the fact that it was officially introduced in late-August last year, it is only found on 2.8 percent of Android devices. However, things are slowly improving.
Manufacturers, like Samsung, are starting to release software updates to bring Nougat to their flagship offerings, which will help it gain more traction among Android users. The Samsung Galaxy S7 and Galaxy S7 edge, for instance, got Nougat in mid-January and their predecessors, the Galaxy S6 and Galaxy S6 edge, are now receiving a similar treatment.

Renault adds Android Auto to 2017 models
Advanced smartphone integration is a feature that more and more consumers will be looking for in a new car. Renault knows this, and to make its 2017 range more attractive to potential buyers it is now adding support for Android Auto.
The first models to have Android Auto support are the Espace, Kadjar, Mégane, Mégane Estate, Scénic, Grand Scénic, Talisman and Talisman Estate. Other models in the line, which are listed below, will also get the integration soon.

AMD details Zen-based Naples server processors
After the successful launch of its new Ryzen processors last week, AMD has announced the first details of its upcoming Naples CPUs intended for servers and data centers.
These processors were designed around the same Zen architecture as Ryzen though they will be a great deal more powerful. AMD has described them as having "superior" memory bandwidth and some models will even feature up to 32 cores in order to handle a more demanding workload.

Apple starts selling refurbished 2016 MacBook Pro -- better hurry if you want one!
One of the best ways to save money on an Apple product is to buy refurbished. Not only do you enjoy a significant discount but the device also passes a rigorous inspection and comes with a factory warranty as well.
The 2016 MacBook Pro, which was introduced in October 2016, is the latest device Apple added to its Certified Refurbished program, being introduced in multiple configurations to its online store. Here's what you should know about it.

Vault 7: The CIA weaponized these popular programs to spy on people
Two days ago, WikiLeaks unleashed a treasure trove of data relating to the CIA's supposed arsenal of hacking tools. Code-named Vault 7, the "Year Zero" cache contains over 8,500 documents and files, and is, according to WikiLeaks, just the first batch. More content will be leaked over time.
While we know that the CIA’s zero day weapons could be used to exploit iPhones, Android devices, Windows PCs and even Samsung TVs, one of the hacking tools is particularly interesting.

Better consumer education could help cut video piracy
A new survey reveals that education could have a big impact on piracy, cutting the numbers who illegally share video content.
The study by digital platform security specialist Irdeto of more than 25,000 adults across 30 countries finds that despite the high number of consumers around the world watching pirated video content (52 percent), almost half (48 percent) would stop or watch less illegal content after learning the damage that piracy causes to the media industry.

Mysterious Windows driver causing problems for users
If you’ve been experiencing weird problems with Windows over the past couple of days, the problem could be down to a mysterious driver that Microsoft has pushed out for Windows 7, Windows 8.1, and Windows 10.
The driver, called "Microsoft -- WPD -- 2/22/2016 12:00:00 AM -- 5.2.5326.4762" is causing a couple of problems for users, including failed installations, and Windows Phones and Android devices failing to connect to the target PC.
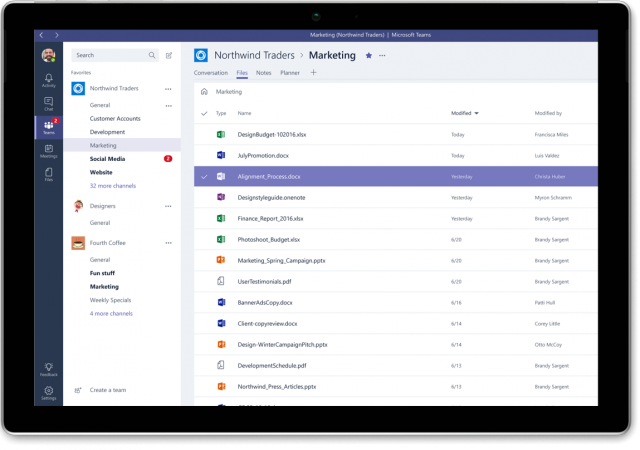
Microsoft Teams will be generally available on March 14
Microsoft is preparing to officially launch its competitor to Slack, Teams, which it announced last November.
Microsoft will begin the rollout of its new product by first making it available to Office 365 customers. The launch event and the global rollout will take place on March 14.

Security concerns hold back mobile payment adoption
Businesses and consumers recognize the benefits of mobile payments, but worries over security are holding back adoption according to a new report.
The study by Oxford Economics interviewed 2,000 consumers and 300 business executives and finds that 62 percent of consumers say mobile money enhances their buying experience, and 72 percent of executives say mobile payments can boost their sales.


