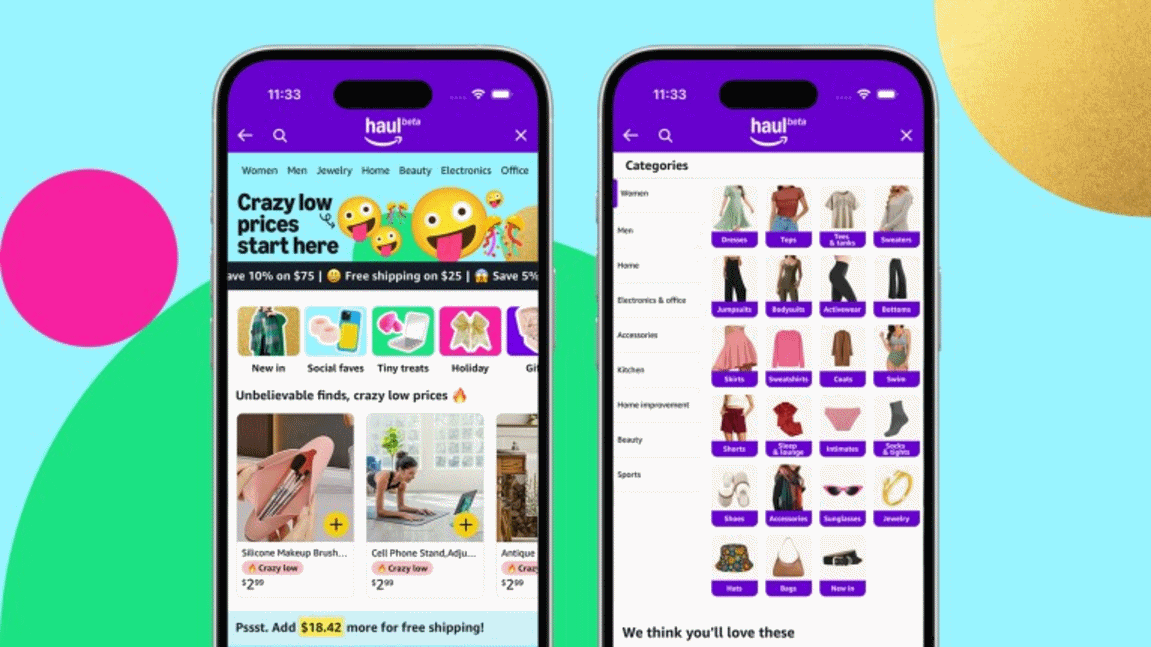
Amazon launches Amazon Haul in beta as a low-cost Temu alternative
Amazon may be one of the biggest names in online retail, but in recent years the likes of Temu has started to encroach on its territory by offering products at absurdly low prices.
Now Amazon has come up with a response. Amazon Haul is a new shopping experience that has launched in beta for US shoppers. Building on the Fulfillment by Amazon (FBA) service, Haul is home to “affordable fashion, home, lifestyle, electronics, and other products with ultra-low prices”. Most things are priced under $10, so what’s the catch?

The Guardian’s exit from Elon Musk’s X shows a lack of journalistic courage
The Guardian’s recent decision to stop posting on X, Elon Musk’s social media platform, is a move that screams weakness. The outlet, which proudly touts itself as a champion of bold reporting, announced it would cease activity on the platform due to “often disturbing content,” such as far-right conspiracy theories. But instead of taking a stand and contributing to the conversation with balanced reporting, The Guardian is turning tail and walking away.
This move doesn’t look like a show of strength. In fact, it comes across as a cop-out, a move fueled by fear rather than the backbone you’d expect from a major news organization. By withdrawing, The Guardian is giving up any chance to challenge misinformation head-on or offer perspectives that counter the narratives it finds so troubling. It’s ironic, really -- an organization that prides itself on being fearless and forthright suddenly choosing the path of least resistance.

HighPoint launches RocketAIC 6542AAW NVMe storage solution with massive 491.52TB capacity for only $78,999
HighPoint has announced its RocketAIC 6542AAW, claiming to be the world’s first near half-petabyte NVMe storage drive that is smaller than a shoebox. Compact at 4.84 inches tall, 8.27 inches deep, and 9.25 inches long, this external RAID powerhouse packs eight Solidigm D5-P5336 NVMe SSDs for a massive 491.52TB of storage. Beyond its storage heft, the device boasts real-world transfer speeds reaching 28GB/s, making it ideal for edge applications that need high-density, rapid-access storage in a small footprint.
The chassis is not just compact; it comes with its own power supply and an advanced cooling system to keep the NVMe media isolated from the host hardware. This strategic design means more interior space for the server or workstation and improved overall reliability. By keeping waste heat away from the main system, the RocketAIC 6542AAW reduces power consumption and enhances efficiency.

Three-quarters of most visited websites not compliant with privacy regs
A new report finds that 75 percent of the 100 most visited websites in the US and Europe are not compliant with current privacy regulations.
The study from privacy solution provider Privado.ai shows despite stricter privacy enforcement in Europe a surprising 74 percent of top websites do not honor opt-in consent as required by Europe's General Data Protection Regulation (GDPR).

The challenge of encrypted traffic for network defenders [Q&A]
When it comes to protecting sensitive information like financial data, personal information, and intellectual property, encryption has become a must. By scrambling data through the use of algorithms, only those with access to decryption keys are able to read what's being secured.
Encrypted traffic has fulfilled its intended mission: to lock down data. But, could it simultaneously be helping bad actors slip by undetected? And could encrypted traffic actually make it harder for network defenders to spot threats before it's too late?

SurveyMonkey adds WhatsApp support for easier survey sharing
SurveyMonkey, a widely used platform for creating surveys and forms, has expanded its social sharing capabilities to include WhatsApp. This addition allows users to share their surveys and forms directly with WhatsApp contacts and groups, aiming to simplify the distribution process. WhatsApp joins SurveyMonkey’s existing social sharing options, which include LinkedIn, X (formerly Twitter), Facebook, and Microsoft Teams.
With over 2 billion active users globally, WhatsApp is recognized as one of the most popular messaging apps. SurveyMonkey customers in over 130 countries, speaking 56 different languages, can now leverage this integration to share surveys and forms through a platform that many already use daily. Early results have shown that the WhatsApp sharing feature has garnered twice as many clicks and shares compared to other social sharing options.

Logitech launches Sync smart office tools to streamline workplace efficiency
Logitech has introduced a range of Sync smart office tools designed to improve workplace efficiency and provide enhanced analytics for IT teams. The new suite includes Auto Book and Auto Release, which automate room reservations and cancellations based on user activity. Additionally, Logitech View offers interactive digital office maps to assist with navigation in large office spaces.
Henry Levak, VP of Product at Logitech for Business, highlighted the AI capabilities of the tools, stating, “Rally Bars use AI in-camera sensors to automatically detect and respond to natural workplace behaviors with no human intervention needed.” This approach aims to simplify room management, allowing employees to focus on collaboration while IT teams gain more accurate insights into actual room utilization.

Get 'An Introduction to Optimization: With Applications to Machine Learning, 5th Edition' for FREE and save $106!
Fully updated to reflect modern developments in the field, the Fifth Edition of An Introduction to Optimization fills the need for an accessible, yet rigorous, introduction to optimization theory and methods, featuring innovative coverage and a straightforward approach. The book begins with a review of basic definitions and notations while also providing the related fundamental background of linear algebra, geometry, and calculus.
With this foundation, the authors explore the essential topics of unconstrained optimization problems, linear programming problems, and nonlinear constrained optimization. In addition, the book includes an introduction to artificial neural networks, convex optimization, multi-objective optimization, and applications of optimization in machine learning.

OWC launches Thunderbolt 5 Hub to supercharge Mac and PC connectivity
Other World Computing (OWC) has launched the Thunderbolt 5 Hub, which promises to elevate device connectivity for Macs, PCs, and even tablets like the iPad Pro. This new hub delivers an impressive 80Gb/s of bi-directional data speed -- double that of Thunderbolt 4 and USB4 -- and supports up to 120Gb/s for users needing higher display bandwidth. With just a single cable, users can expand their device’s ports to include three Thunderbolt 5 ports and a USB-A port, making this hub a productivity game changer.
For tablet users, the OWC Thunderbolt 5 Hub is especially transformative, turning an iPad Pro or similar device into a full-fledged workstation capable of connecting to external drives, displays, and a variety of peripherals. This means users can push the limits of their tablets without the need for a laptop or desktop nearby.

Failed security controls cost businesses billions
A new report finds 61 percent of organizations have suffered a security breach in the past year because their policies, governance, and controls failed or were not working effectively. This is costing US businesses $30bn and UK businesses £10bn per year.
The study from security posture management firm Panaseer surveyed 400 security decision makers across the US and UK and found 72 percent have taken out indemnity insurance in response to growing personal liability, whilst 15 percent have considered leaving the industry.

New defense suite is designed to secure AI workloads
As organizations increasingly adopt AI capabilities, the most common and dangerous attacks often go undetected by static code scanning or traditional security methods.
The only effective way to stop common AI attacks, such as prompt injection and zero-day vulnerabilities, is through active runtime detection and defense. Operant AI is launching a new 3D Runtime Defense Suite aimed at protecting live cloud applications, including AI models and APIs in their native environments.

Microsoft’s answer to Apple Intelligence may be Windows Intelligence
Branding is important, and this is something we’ve already seen with digital assistants like Siri. Moving into the artificial intelligence era, companies have been falling over themselves to get their own stamp on their version of AI.
Apple has opted for the reasonably predictable “Apple Intelligence”, while Microsoft’s approach has been a little more haphazard. But now there are clues that suggest the company has finally come to understand the importance of giving people an overarching term to cover all of its AI-related offerings. Say hello to Windows Intelligence.

New tool helps prepare workforces for cyber threats
Humans are generally the weakest link in the cybersecurity chain, so training and awareness are essential alongside technology to keep organizations safe.
With the launch of its AI Scenario Generator, Immersive Labs enables organizations to seamlessly generate threat scenarios for crisis simulations to ensure their workforces are ready for the latest threats.
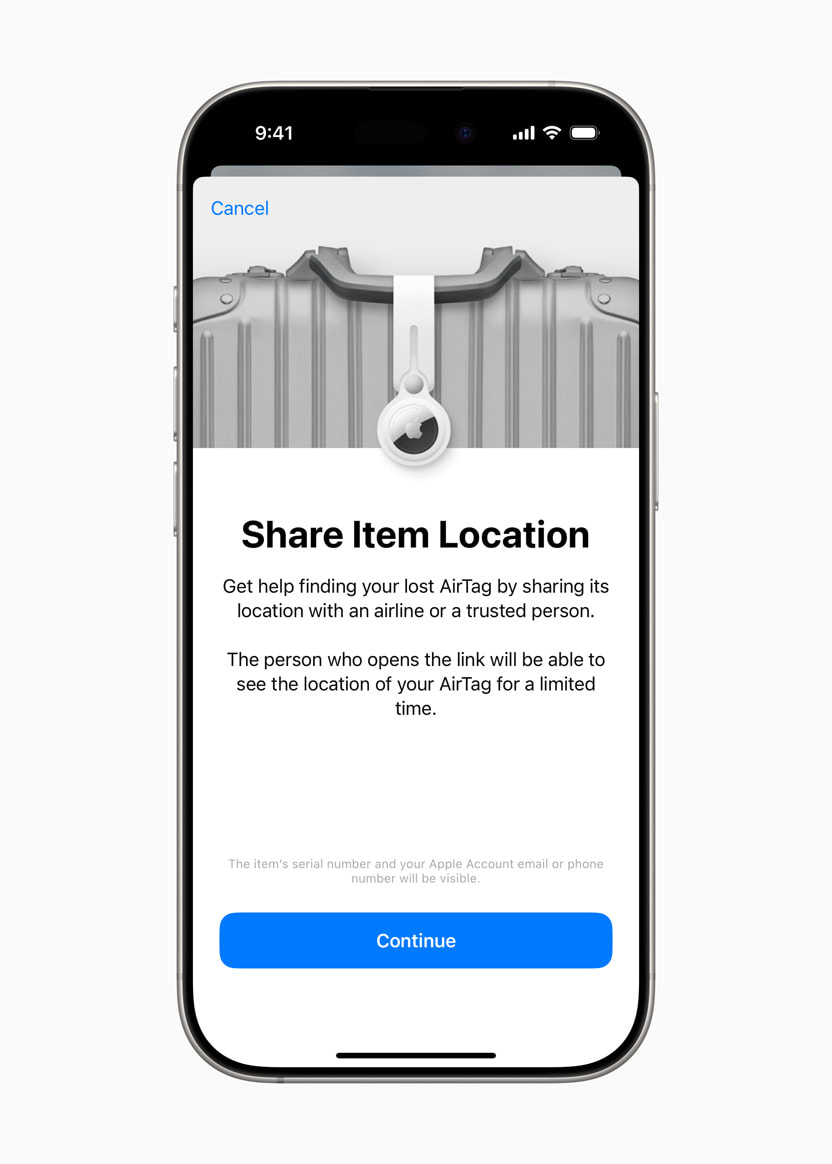
Apple Find My can now share AirTag locations with airlines and third parties
Apple has launched a beta feature called Share Item Location in iOS 18.2, allowing users to share the location of an AirTag or Find My network accessory with third parties. This update is designed to simplify the process of locating misplaced items, particularly when traveling. Users can generate a secure link in the Find My app on their iPhone, iPad, or Mac, which can then be shared. The recipient can access an interactive map that shows the item’s location and updates automatically. The shared link expires after seven days or when the item is recovered, maintaining privacy and security.
“Find My is an essential tool for users around the world to keep track of and find their belongings,” said Eddy Cue, Apple’s senior vice president of Services. “The Find My network and AirTag have proven to be a powerful combination for users while traveling, providing invaluable location information when bags have been misplaced or mishandled. With Share Item Location, we’re excited to give users a new way to easily share this information directly with third parties like airlines, all while protecting their privacy.”

Logitech expands availability of refurbished products in North America and Europe
Logitech is making it easier for consumers to access refurbished devices with the expansion of its Certified Refurbished program. Now, customers in North America and Europe can purchase a wide range of products, including mice, keyboards, tablet accessories, gaming gear from Logitech G, and Bluetooth speakers through Logitech’s eBay Refurbished brand store and its own websites.
The company is tapping into a growing trend as more consumers seek out high-quality refurbished products. The appeal of these devices lies in their cost-effectiveness and environmental benefits, offering users a way to own premium technology while contributing to waste reduction.


