
HSBC online banking hit by DDoS attack
As workers eagerly awaited the arrival of their first payday of 2016, and others rushed to file their tax returns ahead of Sunday's deadline, HSBC's online banking services were knocked offline today.
The banking giant was hit by a DDoS, but it is not yet clear who is responsible. The attack meant that customers were unable to access their online accounts, and it is just the latest in a strong of high-profile security issues to affect well-known sites.

Bull's Bullion S server sets performance record
Bullion, high-end servers from Atos' technology brand Bull, has set a new global record in performance, the company has announced.
The record was set in accordance with the Standard Performance Evaluation Corporation.

Best Windows apps this week
One-hundred and sixty-five in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days.
There have not been that many app releases or updates this week, at least when it comes to notable ones.

Apple releases surprise update for no-longer-supported OS X 10.6 Snow Leopard
When it comes to supporting older operating systems (or not), it is usually Microsoft that we are talking about. But this week Apple took its users by surprise by releasing an update to Snow Leopard -- the lengthily-named Mac App Store Update for OS X Snow Leopard.
If you are wondering why an OS update should come as a surprise, it is because support for Snow Leopard came to an end in the latter half of 2013. It is an update that is ostensibly about ensuring continued access to the Mac App Store, but it also helps to give Snow Leopard users an easier path to upgrade to El Capitan.

How technology is ruining your mind
Do you find that you don't remember facts any more because you know you can easily look them up online? Or does using phones and gadgets late at night make it harder for you to sleep?
According to an infographic from London-based support specialist Conosco these are just some of the ways in which technology is harmful to our minds.
Intel aims to make life easier for small businesses
Small businesses make up around 17 percent of the total PC market, yet often they don’t have dedicated resources to manage their systems.
Chip maker Intel has spotted an opportunity here and is launching its Small Business Advantage program, offering a blend of systems management and business collaboration.

IT security professionals are looking for a challenge
The notion that IT security professionals are mercenaries when it comes to work and would most likely move if given an opportunity to earn more is, by a large margin, incorrect.
That’s basically what a new report by AlienVault says. The report, entitled Blood on HR's floor -- The Challenge of Retaining IT Security Skills, has a couple of interesting points.

Fluance Fi70 is a high-quality and elegant home Bluetooth speaker system
Bluetooth speakers are awesome. They are convenient, often inexpensive, and sometimes portable. If I want to listen to music in my backyard, at the beach, or in my home, an inexpensive unit can do the trick.
Unfortunately, these little speakers are often lacking in sound quality. Yeah, they are usually better than integrated smartphone and tablet speakers, but hardly up to snuff for audiophiles or hardcore music enthusiasts. Enter the Fluance Fi70. This elegant three-way music system looks to be the Bluetooth speaker of which many of us have been dreaming.

Microsoft's Q2 earnings are hugely impressive, buoyed by cloud revenue
Microsoft's cloud first, mobile first philosophy seems to be paying off. The company today announced its Q2 2016 earnings, with profit and revenue exceeding predictions. Revenue fell very slightly to $25.69 billion, but this was still higher than analysts expected; the slight drop has been partially blamed on a decreased interest in Windows.
Confidence in Satya Nadella's leadership seems high, with stock prices rising by more than 26 percent in the last year. His belief in the cloud appears to be paying off, with Microsoft's Intelligent Cloud business generating revenue of $6.3 billion. Overall, the company expects its entire annual cloud revenue to hit $9.4 billion, up from $8.2 billion.
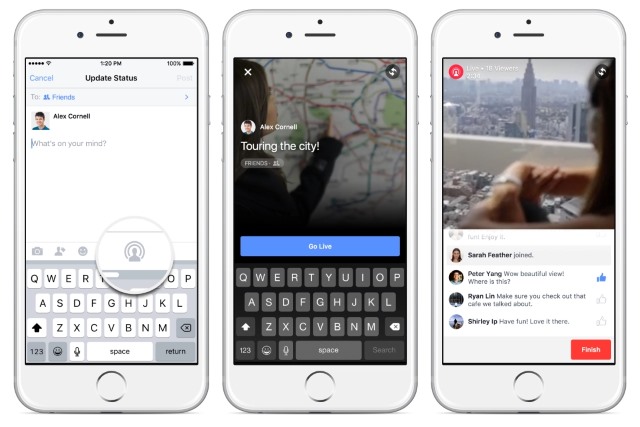
Live video streaming spreads to all mobile Facebook users
Lights! Camera! Action! Facebook is home to pictures, videos, comments, news, train-of-thought ramblings, and much more. Until recently, videos have been limited to those that have been pre-recorded, but that's about to change.
Facebook recently opened up the ability to share a live video stream to a limited number of people, and the social network is about to expand this. Starting today, live video sharing is being made available to US iPhone users, and it won't be long before the feature is available globally, and also to Android users.

Mount cloud storage as local drives with Mountain Duck
Iterate GmBh has shipped Mountain Duck 1.0, a smart tool which mounts remote volumes as local drives in Windows Explorer and the Mac’s Finder.
Based on the developer’s Cyberduck technology, Mountain Duck connects to FTP and SFTP servers, WebDAV, Amazon S3, Azure and OpenStack Swift storage.

Lenovo fixes SHAREit security flaw
Lenovo has issued updates to address a hard-coded password flaw and other security issues with its file sharing utility SHAREit.
Lenovo has addressed a serious flaw in its PC and Android versions of SHAREit, which enabled anyone on a LAN or wireless hotspot to potentially view and copy files from another computer or device running the SHAREit application. Though that was always the intention of the application -- to make file sharing painless -- it was probably not intended to be so open to anyone.

Bernie Sanders' campaign is right, Microsoft could hurt election -- open source is needed
When it comes to government agencies at all levels, and things like the voting process, I am a hardcore believer in open source being necessary. To truly know that votes are being counted correctly by machines, only open source would allow independent auditing. It will also help to prevent unknown backdoors in secure government computer systems.
Closed source technologies from companies like Microsoft could, in theory, contain backdoors or vulnerabilities that hackers and evildoers could exploit. Even worse, Microsoft or its employees could purposely alter voting software to influence outcomes. Am I saying the company is doing this? Not at all. But with closed source software, there is no way to know for sure. Now, Bernie Sanders' campaign is questioning Microsoft's technologies being used in Iowa Caucuses. You know what? They have a point.

How to ensure paper records comply with EU's new data protection regulation
At the end of last year, the European Parliament and Council reached an agreement on the General Data Protection Regulation (GDPR) proposed by the European Commission.
The new rules, which will come into force in early 2018, represent the greatest change to data protection legislation since the dawn of the Internet. They will affect any organization across the world that handles data of European origin.

Is your business wasting the software budget?
No matter how much money your company spends on software, it’s likely to spend less if your boss reads this article.
A new survey by American software company Flexera Software suggests that most companies are wasting their software budget, and the software they buy is often either underused or overused.


