Microsoft 365 Family licensing snafu causes a ‘Your subscription expired’ message

Microsoft has just found a new way to interfere with its customers’ productivity. While software updates are frequent culprits for downtime, some Microsoft 365 subscribers have been hit with a warning that their subscription has expired, leaving them unable to edit Office documents.
The issue affects Microsoft 365 Family users, many of whom have been locked out of their accounts despite having a valid subscription in place. The problems started yesterday and are still ongoing for some.
The devices that are exposing enterprises to risk

The enterprise device landscape is becoming much more complex and more dangerous, with the average device risk per industry increasing by 15 percent year-on-year.
A new report from Forescout highlights that network-connected devices, from traditional IT operating systems to specialized healthcare systems and OT machinery, are exposing organizations to damaging threats such as ransomware attacks and data exfiltration.
Lexar unveils 1TB PLAY PRO microSD Express card as Nintendo Switch 2 pricing and release date are revealed

Lexar has officially launched its PLAY PRO microSD Express card. This launch seems quite perfectly timed with today’s announcement of both the Nintendo Switch 2’s pricing and availability.
The PLAY PRO microSD Express card utilizes the SD 7.1 specification, which integrates both PCIe 3.0 and NVMe 1.3. The card can achieve read speeds up to 900MB/s and write speeds up to 600MB/s. These impressive speeds are particularly beneficial for gaming applications, as they can potentially reduce load times.
Microsoft is making Copilot+ experiences available to more systems, and that’s great news for accessibility
When talking about AI in general -- including Copilot -- the focus tends to be on the impressive time-saving capabilities and futuristic features. What is often overlooked is the potential for artificial intelligence to improve accessibility.
But this is exactly what Microsoft is doing with the features it has for Copilot+ PCs. And now the company has made many of the Copilot+ experiences available to a wider range of processors, so systems with AMD Ryzen AI 300 series, Intel Core Ultra 200V and Snapdragon X Series chips can feel the benefits. There are huge advances in accessibility to be explored.
Exploring the security risks underneath generative AI services

Artificial intelligence has claimed a huge share of the conversation over the past few years -- in the media, around boardroom tables, and even around dinner tables. While AI and its subset of machine learning (ML) have existed for decades, this recent surge in interest can be attributed to exciting advancements in generative AI, the class of AI that can create new text, images, and even videos. In the workplace, employees are turning to this technology to help them brainstorm ideas, research complex topics, kickstart writing projects, and more.
However, this increased adoption also comes with a slew of security challenges. For instance, what happens if an employee uses a generative AI service that hasn’t been vetted or authorized by their IT department? Or uploads sensitive content, like a product roadmap, into a service like ChatGPT or Microsoft Copilot? These are some of the many questions keeping security leaders up at night and prompting a need for more visibility and control over enterprise AI usage.
Microsoft accounts now have a sleek new sign in experience with a dark mode option

The next time you sign into your Microsoft account you may well be greeted by a new look. Microsoft has started the roll out of what it is calling a “new sign in experience” as the company uses its Fluent 2 design language to revamp the UI and UX. For better or worse, this is an attempt to create an “unmistakably Microsoft” look and feel.
The changes affect users of Windows, Xbox, Microsoft 365, and more, and Microsoft predicts that the majority of users will see the new look by the end of April. As part of the redesign, users are being given more choice; there is now a dark mode option.
Cloud collaboration platforms exploited in phishing attacks

Popular cloud collaboration and file sharing platforms like Adobe, DocuSign, Dropbox, Canva, and Zoho are being misused in phishing attacks due to their widespread adoption by businesses and individuals.
Research by Cofense finds 8.8 percent of all credential phishing campaigns in 2024 used these websites. Among campaigns exploiting these online document sites 79 percent of all cases containing the domains were credential phishing attacks.
Medical devices vulnerable to exploits and insecure connections

A new report from Claroty finds that 89 percent of healthcare organizations have medical devices vulnerable to ransomware-linked exploits and insecure internet connectivity.
Based on analysis of more than 2.25 million Internet of Medical Things (IoMT) devices and 647,000-plus OT devices across 351 healthcare organizations, the report finds 99 percent have at least one known exploited vulnerability (KEV) in their networks, while 78 percent of hospitals have OT devices with KEVs, including building management systems, power supplies, and temperature controls.
Discord rolls out a redesigned Game Overlay and desktop update to boost your PC gaming experience
Good news, fellow PC gamers -- Discord has finally refreshed the desktop experience and introduced a completely rebuilt Game Overlay. These new features are rolling out now.
The new Game Overlay is more than just a simple facelift -- it’s been entirely rebuilt from scratch. Instead of forcing the entire Discord app into your game window and draining system resources, the update introduces lightweight widgets you can move and resize based on how you play. Whether you’re deep into an FPS or strategizing in an RTS, you can now tailor the overlay to match the gameplay.
ExpressVPN finally brings GUI to its Linux app
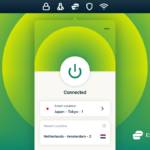
ExpressVPN has rolled out a much-needed update for Linux users, finally adding a graphical user interface (GUI) to its VPN app. Yes, folks, a GUI for Linux is only being rolled out in 2025! Better late than never, I suppose.
Until now, ExpressVPN users in Linux were stuck with a command-line interface (CLI), while Windows and macOS users enjoyed a more user-friendly experience. This update brings ExpressVPN more in line with competitors like Surfshark, which has long offered a Linux app with a GUI.
Over half of organizations experience incidents involving industrial control or operational tech

Over the past year, more than 50 percent of organizations have experienced at least one security incident involving ICS/OT systems. Among the top vulnerabilities exploited are internet-accessible devices (33 percent) and transient devices (27 percent), often used to bypass traditional defenses.
A new report from the SANS Institute, in partnership with OPSWAT, shows that while 55 percent of organizations reported increased ICS/OT cybersecurity budgets over the past two years, much of that investment remains heavily skewed toward technology, with limited focus on operational resilience.
Cricut Explore 4 and Maker 4 launch with faster speeds and lower prices -- perfect for stay-at-home moms

If you are a fan of crafts, you definitely have reason to be excited today. You see, Cricut is back with two new cutting machines designed to make crafting easier, faster, and even more affordable!
The Cricut Explore 4 and Cricut Maker 4 will be available starting tomorrow. These machines will appeal to stay-at-home moms (or stay-at-home dads for that matter) looking for a creative hobby or even a potential side hustle. With the ability to cut materials twice as fast as before, users can churn out custom vinyl decals, t-shirts, greeting cards, and more in record time. You'll be amazed by all the cool things you can make with it.
Install the KB5052093 update for Windows 11 to gain taskbar file sharing, Explorer improvements, and endless bug fixes

It's that time of the month when Microsoft releases preview versions of next month’s updates for Windows. For the eager -- and brave -- they provide a way to get early access to new features and options as well as fixes for problems.
Windows 11 users now have the KB5052093 update to download and install if they want to jump in ahead of Patch Tuesday, and this is a nice little update that not only patches a bunch of bugs, but adds a tasty selection of new bits and pieces. A highlight is the ability to use a single webcam in multiple apps.
99 percent of organizations experience API security issues

A surge in API adoption, driven by the need for organizations to modernize infrastructures and unlock new revenue streams, is contributing to the rise in API security risk according to a new report.
The study from Salt Security finds 99 percent of respondents encountered API security issues within the past 12 months and 55 percent slowed the rollout of a new application due to API security concerns.
86 percent of commercial codebases expose organizations to risk

Analysis of 965 commercial codebases across 16 industries during 2024 by Black Duck Software finds 86 percent contain open source software vulnerabilities and 81 percent high- or critical-risk vulnerabilities.
Black Duck's Open Source Security and Risk Analysis (OSSRA) report also shows that the number of open source files in an average application has tripled from around 5,300 in 2020 to more than 16,000 in 2024.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.