
Data intelligence is your new organizational North Star
There’s no shortage of data buzzwords: data quality, data governance, data management, data integration -- the list goes on.
Don't let the term "buzzword" fool you. These concepts aren't trivial -- they're tightly interwoven and all play a critical role in data-driven decision-making. For example, data quality is key to achieving a robust data governance strategy, and data integration is integral to the data management process. However, with so many considerations at play, it’s challenging for data leaders to prioritize hygiene across the organization. Until now. Enter data intelligence.

Guide for CTOs: How to elevate your DevOps journey
For Chief Technology Officers, spearheading a culture of innovation and forging a resilient DevOps infrastructure are paramount. These objectives, however, unfold over time through a deliberate journey of strategy, experimentation, and reflection. Establishing and nurturing DevOps processes is a pivotal part of this journey, requiring a comprehensive framework to ensure your team remains aligned with organizational goals.
The DevOps Maturity Model serves as a vital framework, guiding engineers and CTOs to precisely evaluate their position within the DevOps adoption continuum and critically review their ongoing initiatives. This roadmap is essential for improving performance, fostering a culture of continuous innovation, and ultimately achieving the desired outcomes.

Attackers exploit email forwarding rules to compromise accounts
Detections for malicious email forwarding rules have risen by nearly 600 percent in 2023, as adversaries compromised email accounts, redirected sensitive communications to archive folders and other places users are unlikely to look, and attempted to modify payroll or wire transfer destinations, re-routing money into the criminal’s account.
This is one of the findings in the latest Threat Detection Report from Red Canary. Half of the threats in top 10 leverage malvertising and/or SEO poisoning, occasionally leading to more serious payloads like ransomware precursors that could lead to a serious attack if not detected.

Flaws in ChatGPT extensions allowed access to sensitive data
New threat research from Salt Labs has uncovered critical security flaws within ChatGPT plugins, highlighting a new risk for enterprises.
Plugins provide AI chatbots like ChatGPT with access and permissions to perform tasks on behalf of users within third party websites. For example, committing code to GitHub repositories or retrieving data from an organization's Google Drives.

Humans represent the biggest security gap
According to a new report, 74 percent of all cyber breaches are caused by human factors, including errors, stolen credentials, misuse of access privileges, or social engineering.
More than two-thirds believe employees are putting the organization at risk through the misuse of email, oversharing company information on social media, and careless web browsing. This highlights the need for staff to receive better training on the risks.

Microsoft releases KB5035845 update for Windows 10, with security fixes, new Windows share features and more
Windows 10 users have a new security update to install in the form of the KB5035845 update. In addition to addressing a number of security issues, this mandatory update also kills the Windows Backup app for many people and introduces various other changes.
One of the most interesting additions to be found in the KB5035845 update are improvements to Windows share. There are also fixes for various issues in Windows 10 including Windows Hello problems.

Bridging the gap between development and security teams [Q&A]
Friction and lack of communication between development and security teams can lead to problems in software development and testing.
How can we bridge the gap between developer and security teams and help them see that they have common goals? We spoke to Scott Gerlach, CSO and co-founder of StackHawk, the company making web application and API security testing part of software delivery, to find out.

Microsoft releases KB5035853 security update for Windows 11 fixing 0x800F0922 error and more
Microsoft has released a new security update for Windows 11. KB5035853 is a mandatory update which not only addresses security issues, but also introduces changes to make Windows 11 compliant with new DMA legislation in Europe.
On top of this, the update fixes the 0x800F0922 error which many people started to experience back in February. The KB5035853 update also features various other changes and additions such as the arrival of support for the USB 80Gbps standard.

Sabrent Rocket 5 SSD lands on Amazon: A new era of PCIe 5.0 speed begins!
Are you ready for a game-changing upgrade to your computer's performance? Well, folks, Sabrent's highly anticipated Rocket 5 SSD is finally available on Amazon! Building on the success of the popular Rocket 4 Plus and Rocket 4 Plus-G, the Rocket 5 takes a giant leap forward with full PCIe 5.0 bandwidth, delivering astonishing transfer speeds of up to 14 GB/s.
Whether you're a gamer seeking seamless experiences or a professional working with large files and demanding applications, the Rocket 5 should supercharge your workflow. Its advanced performance is not just about speed; it's about transforming how you interact with your digital world.

5G Fixed Wireless Access (FWA) -- entering a new era of connectivity
As the global marketplace becomes more competitive in response to customer demand, businesses must find alternative ways to deliver exceptional customer experiences. As budgets are tightening, companies are being scrutinized to new degrees for what they can deliver at a competitive price, with research conducted by Salesforce showing 60 percent of service professionals reporting higher customer expectations post-pandemic.
Should organizations fall short of these high expectations, customers are more than willing to look elsewhere. In fact, recent research from Emplifi found that 86 percent of consumers would leave a brand they trusted after only two poor customer experiences
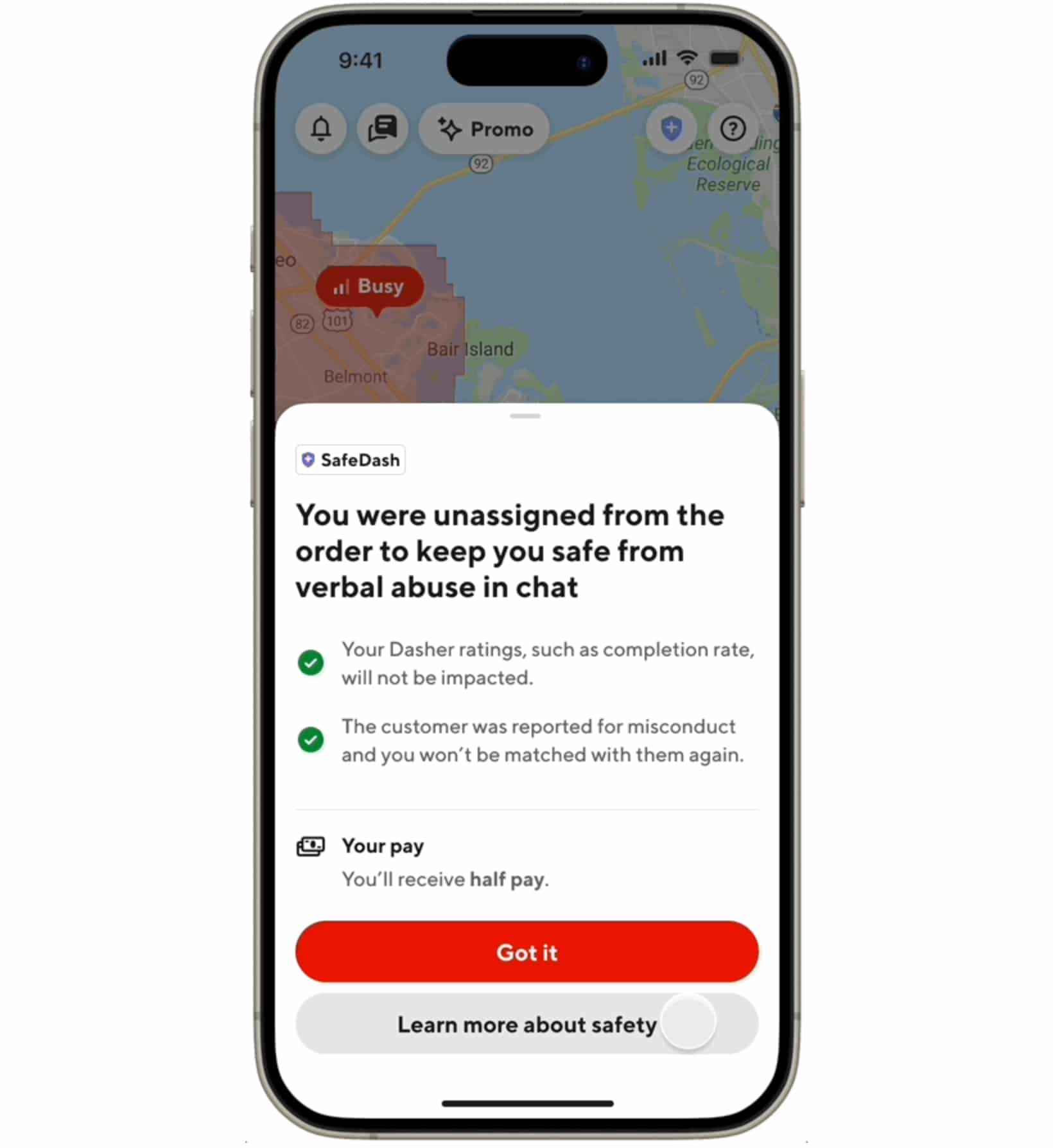
DoorDash introduces SafeChat+ to enhance platform safety with AI
DoorDash, the popular food delivery platform, is taking a big step forward to ensure both the safety and positive experiences of its users.
SafeChat+ is a new feature that leverages artificial intelligence to provide an even safer and better experience for everyone involved. SafeChat+ is designed to review in-app conversations and detect and prevent verbal abuse or harassment between consumers and Dashers.

Sabrent launches NT-25GA USB-C to 2.5 Gigabit Ethernet (2.5GbE) adapter for Windows, macOS and Linux
Today, Sabrent has launched its latest product -- the USB-C to 2.5 Gigabit Ethernet (2.5GbE) adapter (NT-25GA). This compact device is designed to provide a quick and easy way to add a high-speed Ethernet port to any USB-equipped system.
The Sabrent NT-25GA adapter supports impressive speeds of up to 2.5Gbps, making it ideal for handling large data transfers over distances of at least 100 meters using Cat5e or better cabling. It is fully backward compatible and comes with a range of standard features including Wake-On-LAN (WOL), UEFI PXE boot support for compatible systems, and more. For optimal performance, it is recommended to use the adapter with a USB 3.2 Gen 1x1 (5Gbps) port or faster.

Fake web traffic gets more sophisticated
Bots have been around for a long time, but they're now much more sophisticated, capable of mimicking human behavior, evading detection, and perpetrating a wide range of malicious activities.
A new report from CHEQ shows that latest bots are able to scrape data without permission, inflate engagement metrics, commit fraud, and compromise the security and integrity of websites, mobile apps, and APIs.

Centralizing observability saves businesses time and money
Observability is key to allowing organizations to manage their systems effectively, helping improve performance, cut workloads and save money.
Grafana has released its latest Obervability Survey, based on responses from over 300 industry practitioners which shows that 70 percent of teams are using four or more observability technologies.

NETGEAR launches Nighthawk CM3000 DOCSIS 3.1 high-speed cable modem
NETGEAR has officially launched the Nighthawk CM3000 DOCSIS 3.1 high-speed cable modem. Engineered with advanced mid/high-split technology, the CM3000 has the capability to deliver download speeds up to 2.5Gbps and upload speeds up to 1Gbps.
In a world where seamless connectivity is crucial for activities like gaming, video conferencing, and streaming, the CM3000 aims to provide lag-free and smooth experiences. With a significant increase in upload usage, as reported by OpenVault, the need for balanced upstream and downstream bandwidth has become more apparent. The CM3000 addresses this by offering upload speeds that are 2.5 times faster than its DOCSIS 3.1 predecessors.


