
Puro Sound Labs launches JuniorJams Plus Bluetooth headphones for kids
Puro Sound Labs, known for its premium children’s headphones, has launched the JuniorJams Plus. Building on the success of the original JuniorJams, the new “Plus” variant introduces a USB-C connector and a new, eye-catching purple color option.
The JuniorJams Plus feature a sturdy aluminum headband and ultra-comfortable protein leather ear cushions, ensuring ease of wear while offering 87% ambient noise isolation. This allows kids to focus on their audio without external distractions.

AR/VR headset market experiences surge in Q4 2023
The augmented and virtual reality (AR/VR) headset market experienced a resurgence during the holiday season of 2023, defying previous trends. According to the latest data from the International Data Corporation (IDC), Q4 2023 saw a 130.4% year-over-year growth, signaling a shift in consumer interest and technological advancements.
This surge in the AR/VR market comes after a challenging year marked by macroeconomic uncertainties and a reliance on legacy products. The latter part of the year saw a shift in momentum, with new product launches and an easing of economic pressures contributing to the impressive Q4 performance.

SABRENT launches Rocket NANO V2 portable SSD
SABRENT has released the second generation of its popular Rocket NANO SSD. Designed to be compact, fast, and rugged, the NANO V2 is the perfect companion for videographers, photographers, and gamers on the go. Got a Steam Deck or iPhone 15 Pro? This could be the SSD for you!
With storage capacities up to 4TB, you can carry an extensive library of videos, photos, and files without feeling weighed down. The device's aluminum housing is not only attractive but also practical, offering resilience and protection for your data. An outer silicone sleeve further safeguards the SSD from drops and debris, making it an ideal choice for travel in challenging environments.

Microsoft is killing off Windows Subsystem for Android
If you are a Windows 11 user who fell in love with Windows Subsystem for Android, Microsoft has just delivered some bad news. The company is ending support for WSA.
Unlike Windows Subsystem for Linux, Windows Subsystem for Android failed to generate the mass appeal Microsoft was probably hoping for. This is likely partly because of the fact that while WSA makes it possible to run Android apps and games in Windows 11, it is limited to apps available via the Amazon App Store. The clock is now ticking for Windows Subsystem for Android
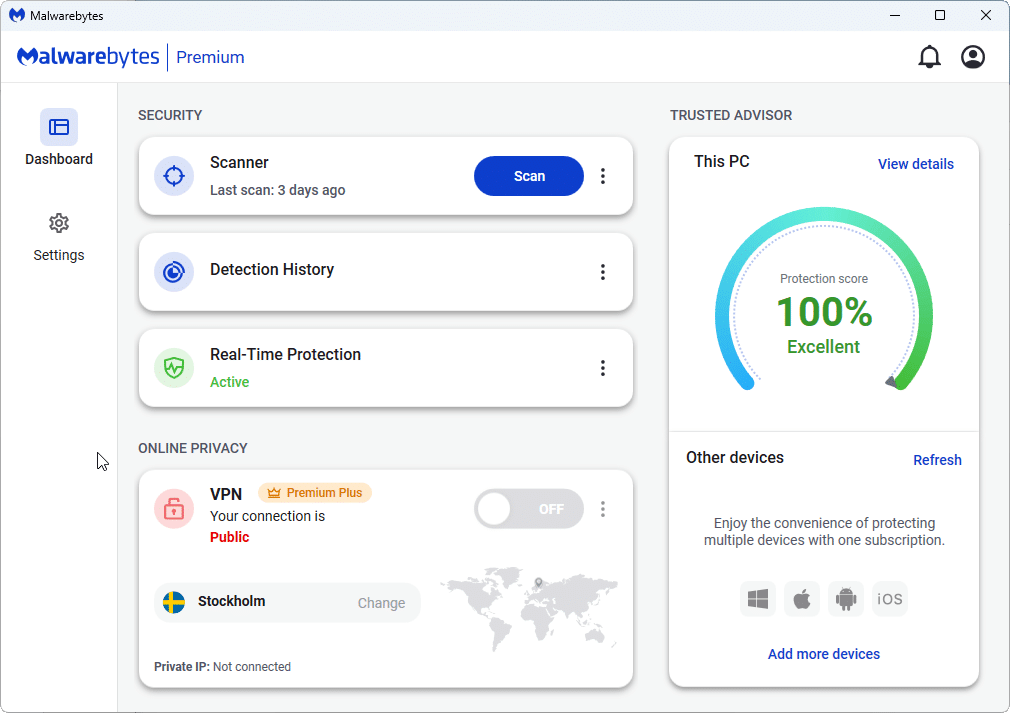
Malwarebytes 5.0 sneaks out, sporting modern new interface and Trusted Advisor
Malwarebytes is quietly rolling out a major new version of its eponymous anti-malware tool with the release of Malwarebytes 5.0. The tool is available in both free and premium versions for desktop and mobile.
MBAM 5.0 is released almost five years after version 4.0 made its bow in May 2019. Like its predecessor, the major change is a sleek new user interface, although this latest effort packs in improved navigation and user-friendliness to go with the modern look.

AI use leads to new risks for data security
According to a new study, 89 percent of cybersecurity professionals agree that their company's sensitive data is increasingly vulnerable to new AI technologies.
The study of 700 respondents across cybersecurity roles, conducted by Vanson Bourne for Code42, also finds that 87 percent are concerned their employees may inadvertently expose sensitive data to competitors by inputting it into GenAI. In addition 87 percent are concerned their employees are not following their GenAI policy.

Security teams struggle to combat image-based and QR code attacks
Over 70 percent of respondents to a new survey say they feel their current security stack is highly effective against image-based and QR code phishing, however, 76 percent report being compromised by these types of attacks within the past year.
The study of 300 IT and security professionals across a variety of industries and geographies, from Osterman Research for IRONSCALES, shows almost 93 percent of IT and security professionals are aware of image-based phishing attacks targeting their organizations, and nearly 79 percent say the same about QR code attacks.

AIOps models deliver limited value say tech leaders
A new study reveals that 97 percent of technology leaders find traditional AIOps models deliver limited value, leaving teams unable to tackle data overload.
The global survey of 1,300 CIOs and technology leaders in large organizations, carried out for Dynatrace, also finds that 88 percent of organizations say the complexity of their technology stack has increased in the past 12 months, and 51 percent say it will continue to increase.
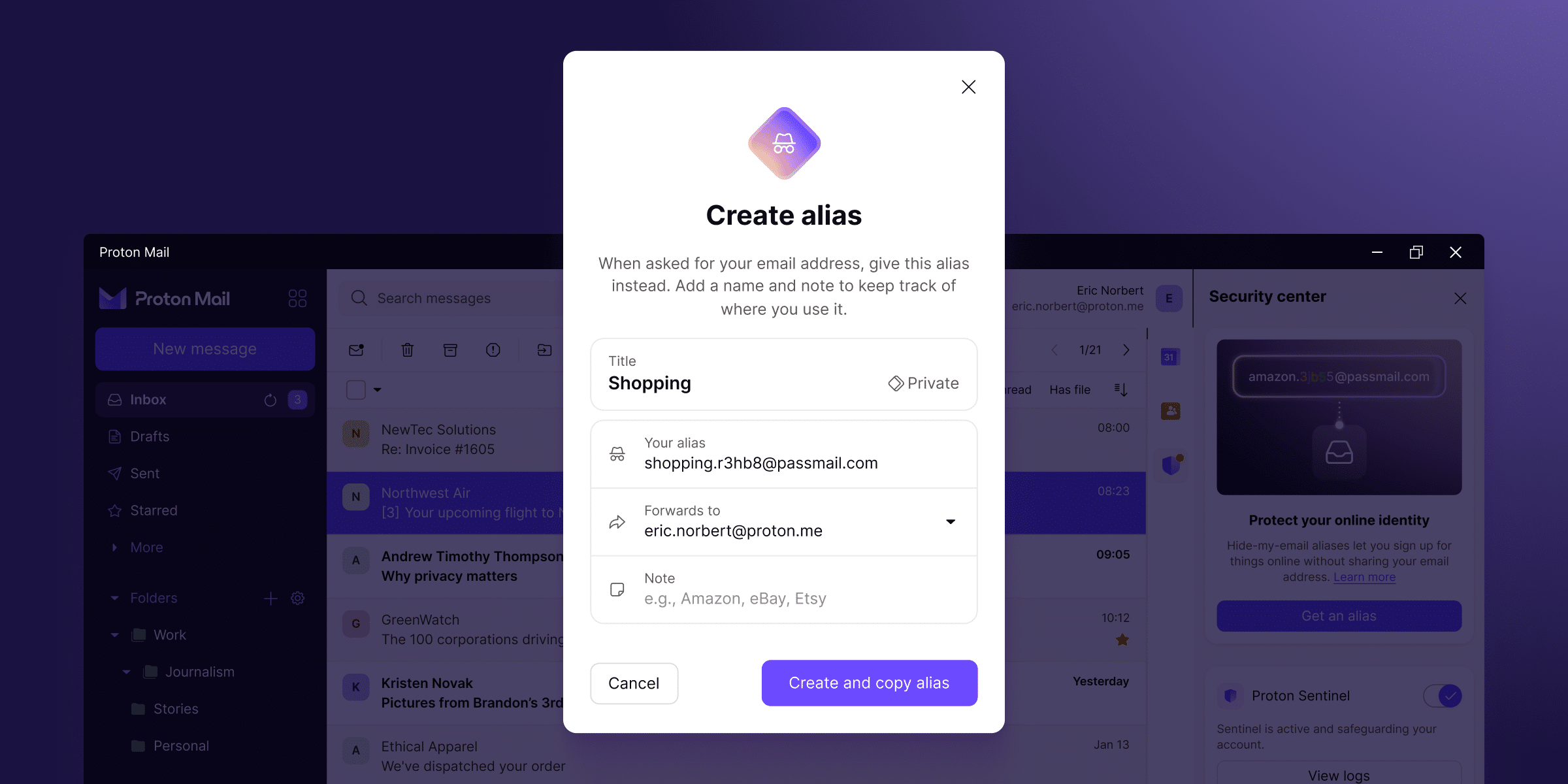
Proton Mail enhances user privacy with hide-my-email alias integration
Proton Mail, the popular email service known for its strong focus on both privacy and security, has integrated hide-my-email alias features directly into its web and desktop platforms. This move gives users more control over their online identity, setting Proton Mail apart from other email providers like Gmail.
The hide-my-email alias feature allows users to generate unique, random email addresses for use with apps, websites, and other digital services. This means that users can keep their personal email addresses private, reducing the risk of being targeted by malware, spam, or online trackers. If an alias is ever compromised, it can be easily deactivated without affecting the user's primary email address.

Managing the transition from DevOps to Platform Engineering
DevOps has historically been the dominant force in software development, explained by Pearl Zhu as being “for harnessing integration, interaction, and innovation.” With the increasing pressure on companies to keep pace in a rapidly evolving technological space, these capabilities are essential.
But this is changing. The standardization of DevOps into Platform Engineering demonstrates the efforts many organizations are going to make developers' lives easier and more productive. While not a new field, this transition represents an evolution in how we design, build, and deliver software.

Enhancing team harmony: Three strategies for integrating network and security solutions
In the fast-evolving landscape of cybersecurity, organizations face the challenge of maintaining operational efficiency while ensuring the security of network devices and firewalls. The increasing complexity, with factors such as cloud services, IoT devices, remote work, and legacy assets, has led to a growing list of potentially vulnerable devices. To address these issues, The Center for Internet Security (CIS) emphasizes the importance of inventory and control of enterprise and software assets.
Effective communication and coordination with the security team is often hindered by existing silos between IT and network teams, specifically network ops, network infrastructure, and network security. The lack of collaboration between teams can result in costly misfires, exposing organizations to cybersecurity threats.
Microsoft releases PowerToys v0.79.0 with amazing new shortcuts options in Keyboard Manager
It feels like it has been a while since there were any particularly dramatic changes or additions to PowerToys, but now Microsoft has just pushed out PowerToys v0.79.0.
The latest version of the essential utilities collection does not, unfortunately, gain any new modules this time around, but there are significant updates to existing tools. Chief among these are updates to Keyboard Manager that means, among other things, it is now possible to create a keyboard shortcut to launch a particular application.

Microsoft is giving click-free access to Copilot in Windows 11
It is no secret that Microsoft has jumped wholeheartedly onto the AI bandwagon, and its Copilot assistant is an important part of this.
Copilot is still in preview, but it has already undergone major work since it first appeared, and now Microsoft is trying to encourage people to use it by making it even easier to access. If clicking a mouse button has been standing between you and a fix of AI-powered assistance, you'll be pleased to hear that click-free access is rolling out to Windows 11 users.
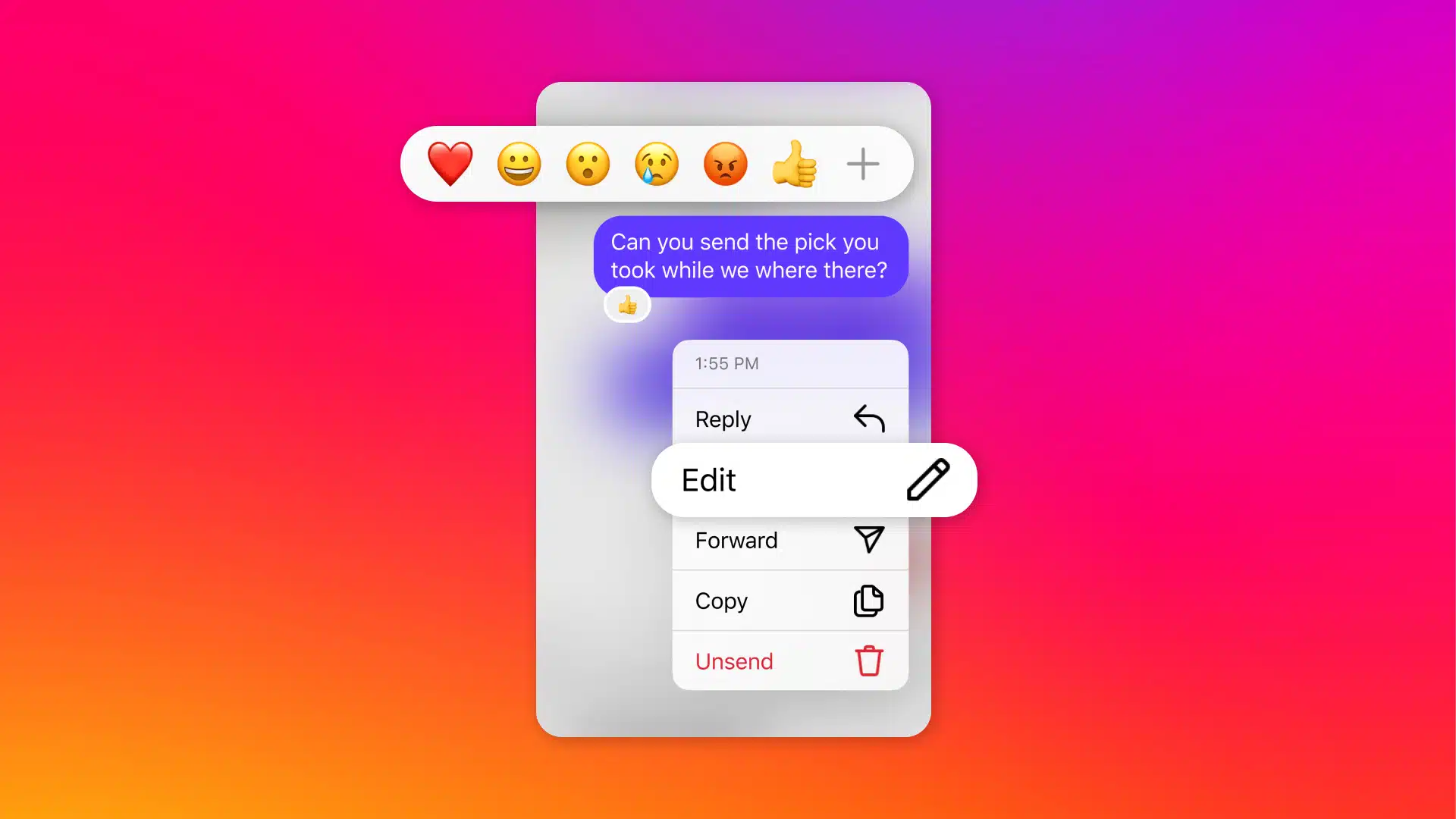
Now you can edit Instagram DMs, pin messages and more
Meta has announced a series of updates to Instagram, all of which are likely to be welcomed by users. Perhaps the most significant change is the option to edit the DMs you've sent, but there are other notable new features -- including disabling read receipts.
The latest round of Instagram updates also sees the introduction of a message pinning option that makes it easier to access keys one-on-one or group chats. On top of all this, reply options have been upgraded, new themes have been added, and more.

Zyxel Networks launches NWA130BE BE11000 Wi-Fi 7 Triple-Radio NebulaFlex Access Point
Zyxel Networks has launched the NWA130BE BE11000 Wi-Fi 7 Triple-Radio NebulaFlex Access Point. This new product offers an economical option for small- and medium-sized businesses (SMBs) that require the advantages of tri-band Wi-Fi 7 technology in a 2x2 access point format.
The NWA130BE is engineered for simple deployment and flexible management, allowing for operation as either a standalone or cloud-managed device. This feature makes it a suitable choice for SMBs looking to enhance their existing networks with the high speeds, low latency, and reliability provided by Wi-Fi 7 technology.


