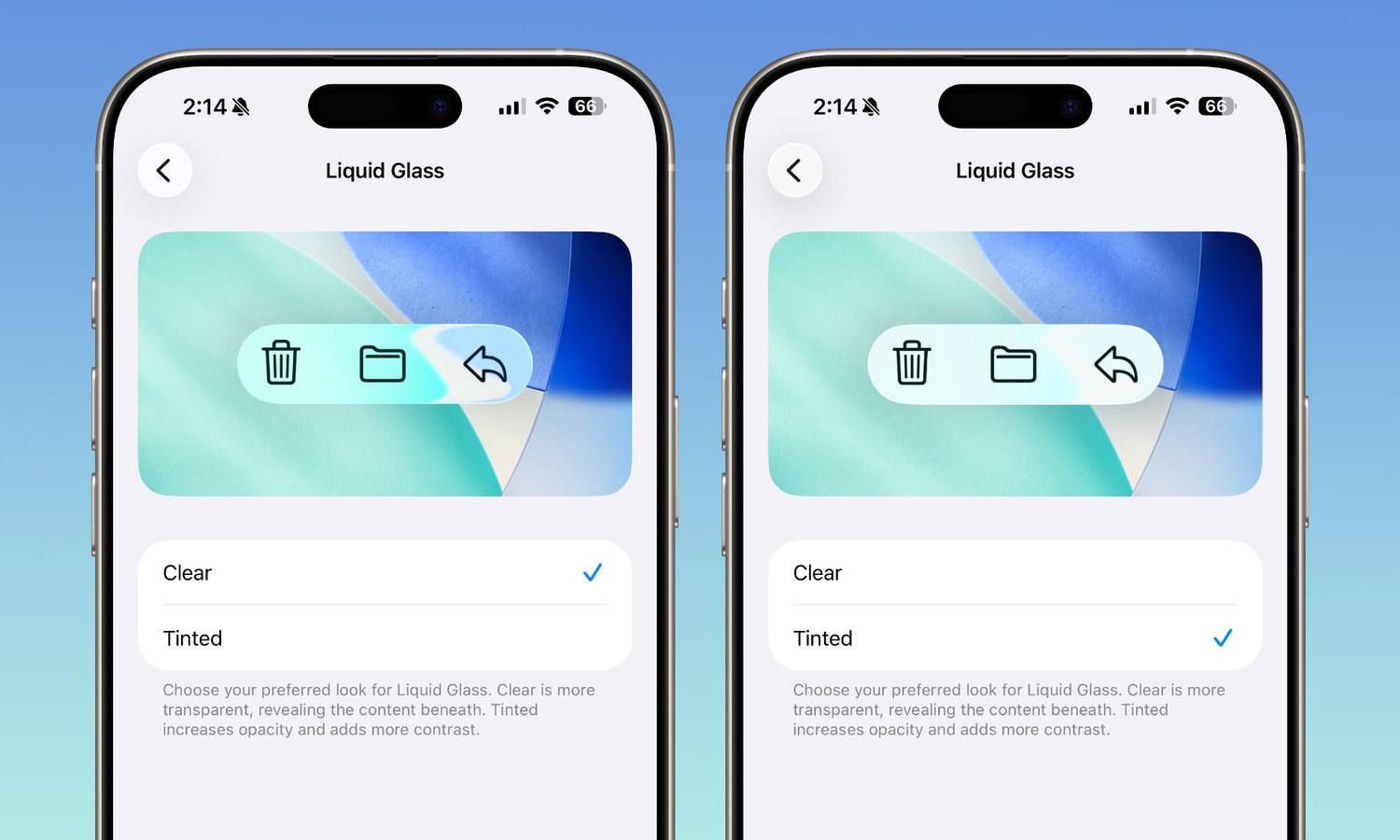
Apple decides to let users control Liquid Glass transparency
Any major visual change to software is likely to result in a mixed reaction – this is certainly true of the Liquid Glass transparency effect Apple introduced into its desktop and mobile operating system recently.
Apple is a company that prides itself on producing designs that balance beauty with utility, so it was probably surprised when users complained about Liquid Glass. Not willing to give in entirely and allow users to switch the effect off completely, Apple has relented a little, introducing controls to change the intensity of the look.
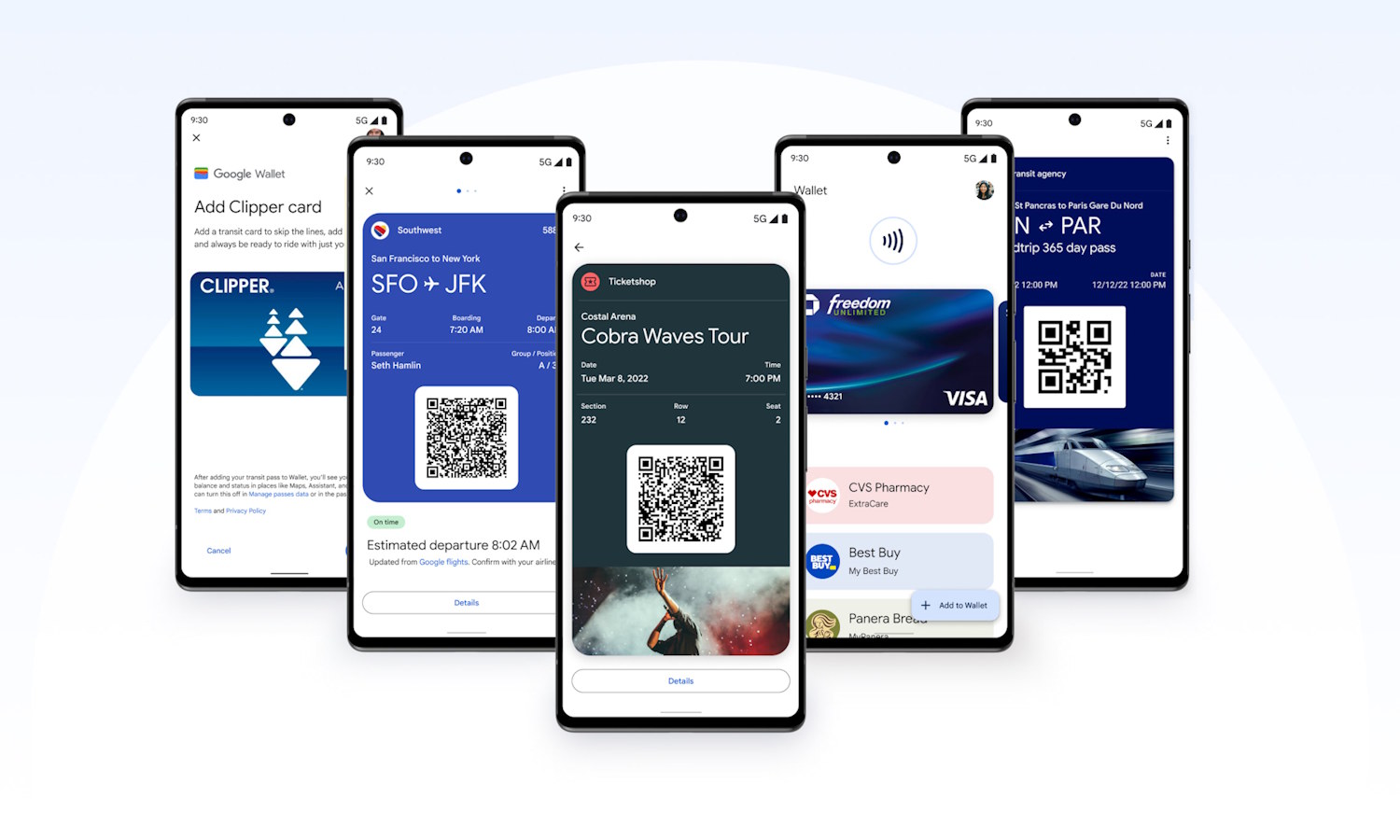
Google Wallet is getting a Live Updates feature for your tickets
Once you have embraced Google Wallet, it is hard to imagine living without it to help manage payment cards, tickets, loyalty cards and more. Thanks to a feature of Android 16, Google Wallet is gaining a handy Live Updates feature.
The addition comes as part of Google Wallet taking on the Material 3 Expressive redesign which also affects the likes of Google Maps. So just what can you expect from this change?

Smaller businesses turn to messaging platforms to engage customers
The adoption of business messaging channels has increased by 53 percent in just one year, driven by AI agents and LLM-powered automation.
A report from respond.io shows small and medium-sized businesses are increasingly engaging customers through platforms like WhatsApp, TikTok, Instagram, and Facebook Messenger.

How AI is driving email phishing and how to beat the threat [Q&A]
Among all of the various forms of cyberattack phishing attempts delivered by email are still one of the most common.
What’s more AI is making these attacks more effective, because you can no longer rely on looking out for dodgy grammar or other signs that a message may not be what it seems.

Amazon Web Services outage takes down Duolingo, Snapchat, Roblox and other major sites
Serious issues with Amazon Web Services (AWS) have rendered a number of big-name apps and services inaccessible. The likes of Fortnite, Roblox, Duolingo, Ring and many more have been suffering as a result of the problems.
The issues first came to light thanks to spikes in reports to Downdetector, but Amazon Web Services has also acknowledged a series of errors. The problems affect multiple AWS services, and the severity of disruption is high.
WhatsApp is working on a new way to cut down on spam
Like email, SMS, and just about every other method of communication, WhatsApp suffers from spam. There are certainly things that can be done by users to stem the flow of spam that makes its way to their inboxes, but WhatsApp is also trying to help.
The platform has already introduced a system designed to automatically detect and block spam, but it is not perfect; no system is. And so, WhatsApp is trying another approach that will apply to businesses and individuals alike.

Google is retiring Privacy Sandbox
Privacy Sandbox was Google’s vision for replacing third-party cookies, but now the company is giving up and moving on from the idea. First launched six years ago, Privacy Sandbox suffered with low-adoption, and Google has gradually snuffed out various technologies relating to the system. Now it has taken things further.
Google says that “after evaluating ecosystem feedback about their expected value and in light of their low levels of adoption”, it has taken the decision to retire more Privacy Sandbox technologies. But this does not really paint a true picture of what is happening.
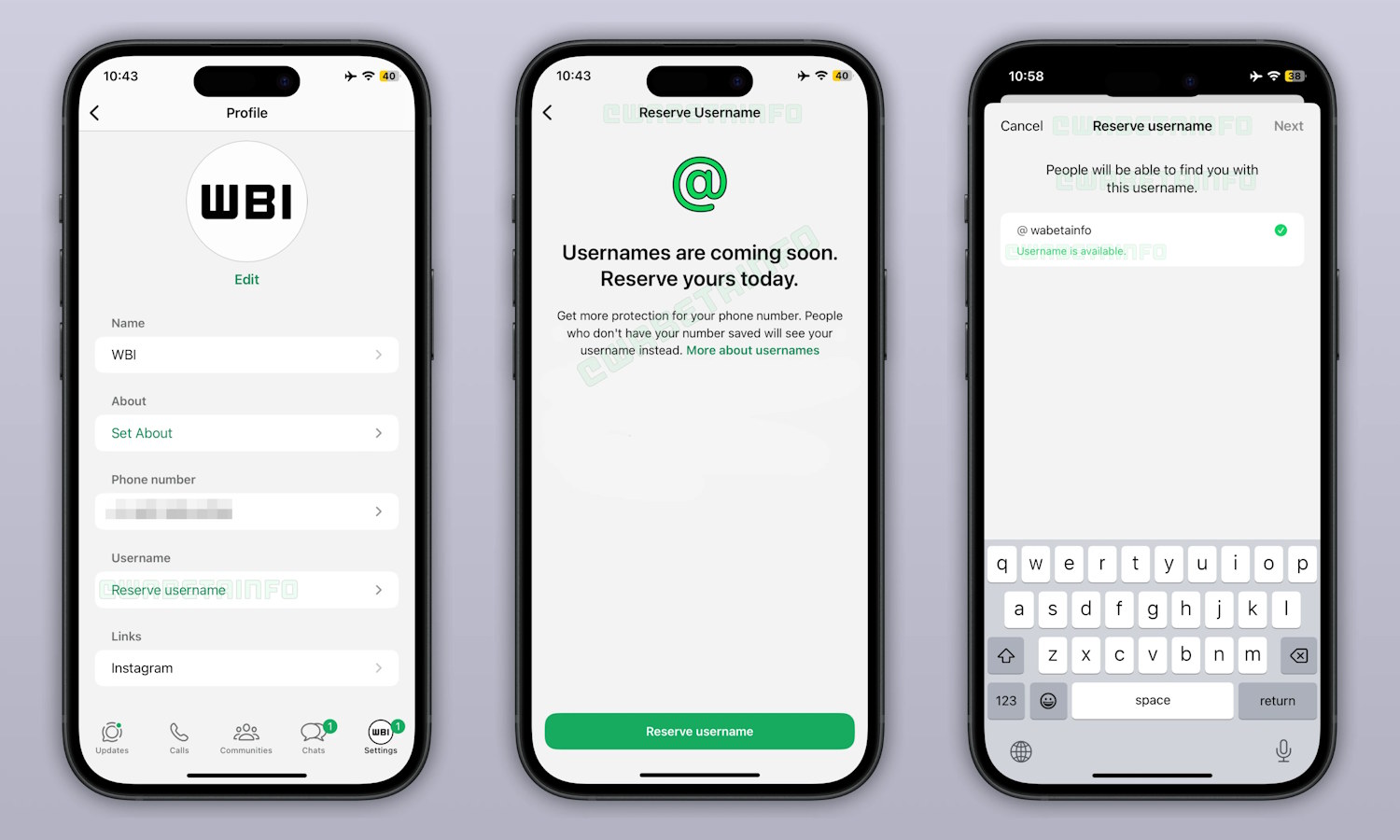
Get ready to reserve your WhatsApp username
It has been known for a little while that Meta has been working on a username system for WhatsApp. The popular messaging app is slightly unusual in not offering people a way to choose a username, but this is going to change at some point in the future.
Recent beta builds of the iOS and Android apps show that work is gathering paced, and the most recent development is a username reservation system. This will serve as a way for users to try to pre-select their preferred username even before the username system rolls out to everyone.
PowerToys update throws users into mode switching confusion
New versions of PowerToys are always eagerly received, especially when there are new utilities to explore. This was certainly the case with the release of PowerToys v0.95 last week, but in addition to the excitement there has also been confusion.
With PowerToys v.0.95, Microsoft added a new module called Light Switch. Designed to automatically switch Windows between Light Mode and Dark Mode, it is a tool that addressed an issue for many people. So where does the confusion come from? Light Switch is enabled by default.

Honor unveils Magic8 series, its first 'self-evolving AI' smartphones
Honor has launched its new Magic8 smartphone series in China, introducing a range of AI-driven features designed to improve imaging, performance, and everyday usability. And while the name might remind you of the fortune-telling toy of a similar name, Honor’s Magic8 is more interested in predicting your habits than your future.
The Magic8 and Magic8 Pro are what Honor describes, somewhat worryingly, as “Self-Evolving AI Devices.” That doesn’t mean they’ll become sentient over time while jammed in your pocket, but rather can learn from user behavior to automate everyday tasks and anticipate actions.

Microsoft is making every PC an AI PC with new Hey Copilot voice command
In what feels like something of a case of history repeating itself – Cortana, anyone? – Microsoft is furnishing Windows users with voice activated access to the operating system’s digital assistant.
While being able to call up the AI powers of Copilot by uttering Hey Copilot to your computer may not seem revolutionary, Microsoft has a different idea. The company says that it sees a “shift to conversational input [being] as transformative as the mouse and keyboard in terms of unlocking new capabilities on the PC for the broadest set of people.

OPPO announces global launch of Find X9 and Find X9 Pro smartphones with new camera system and larger batteries
OPPO will launch its new Find X9 and Find X9 Pro smartphones globally on October 28th, following their initial debut in China. The pair introduce upgraded imaging systems developed with Hasselblad, larger batteries, and OPPO’s latest ColorOS 16 software.
The two devices feature the Hasselblad Master Camera System powered by the company’s LUMO Image Engine, which combines optical tuning and computational processing for more accurate colors and improved low-light results. The Find X9 Pro adds a 200MP telephoto camera developed jointly with Hasselblad.

Forgotten your Google Account password? There are new recovery tools you can use
Getting locked out of an account because of a forgotten password can be a very troubling experience – and it is something that always seems to happen at the most stressful and inconvenient moments imaginable.
To help with this, Google has just announced a series of security related tools, including new account recovery options. Among these is the ability to create recovery contacts so you can “phone a friend” if you get locked out.

Mozilla commits to updating Firefox on Windows 10
Microsoft may have all but abandoned Windows 10, but this is not true of its users. There are still millions of Windows 10 systems in use around the world, causing security concerns for many. But not all software developers are turning their backs on Windows 10 – Mozilla included.
The company has announced that “Firefox will continue to support Windows 10 for the foreseeable future”.
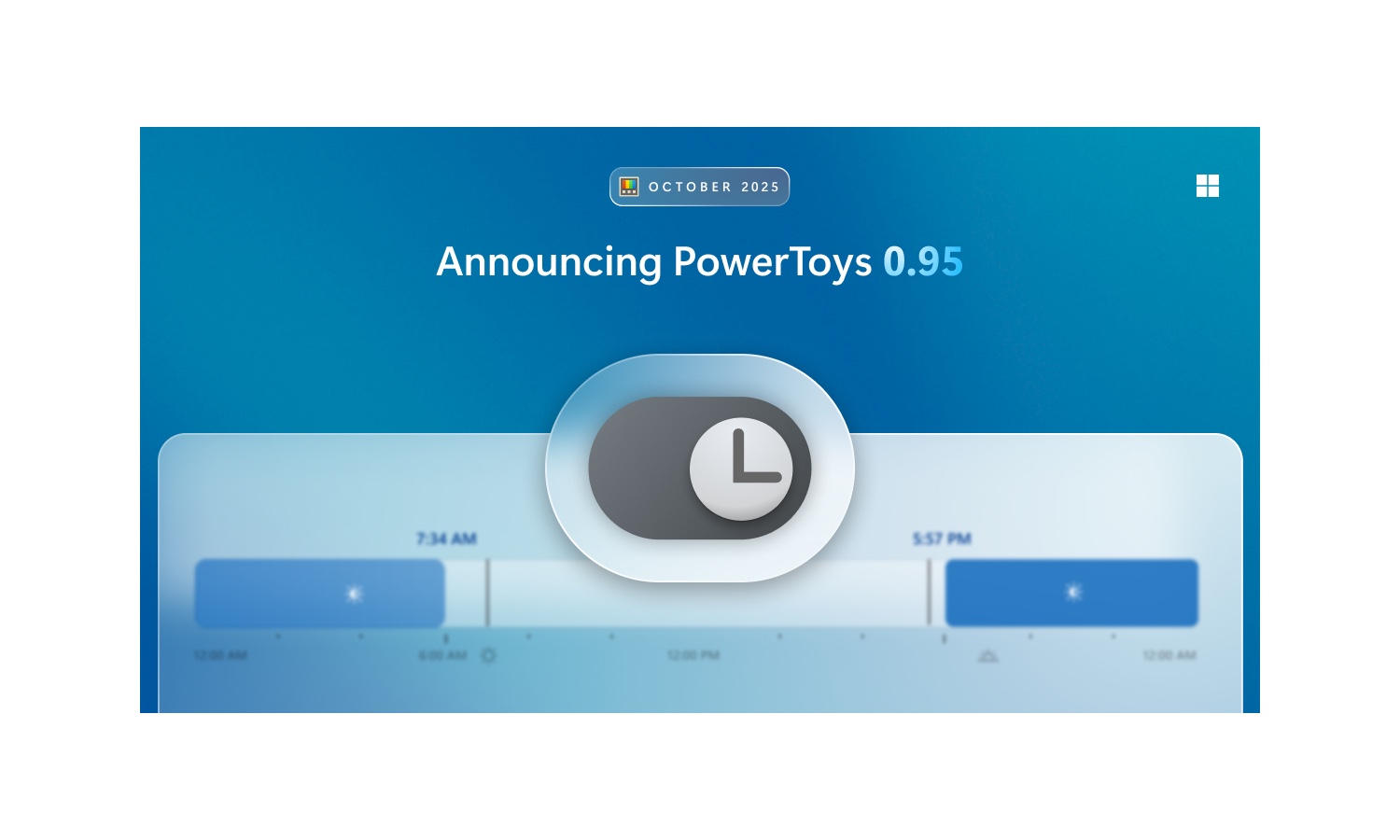
Microsoft releases PowerToys 0.95 with speed improvements and new Light Switch
Microsoft has unleashed PowerToys v0.95, and it is an impressive one. This is a release cycle which is billed as offering “new features, stability, optimization improvements, and automation”, and that’s very much what this particular release is about.
The first thing to ask about any new PowerToys release is whether there are any new modules. And this time around the answer is a resounding “yes”. In addition to a raft of changes, improvements and optimizations across the suite of utilities, there is also the new Light Switch module.


