Delivering good search results is essential but hard to do

Whether you're trying to buy something or just looking for information, not being able to find what you want on a website is frustrating.
So it's not surprising that in a new survey of search practitioners from website search platform Lucidworks, 100 percent of respondents rank search relevance as being 'Highly Important'. What's more, 76 percent expect search relevance to become even more important in the future.
Only 15 percent of companies are ready for cyber threats

Just 15 percent of organizations globally have the 'Mature' level of readiness needed to be resilient against today's modern cybersecurity risks, according to Cisco's first-ever Cybersecurity Readiness Index.
More than half (55 percent) of companies globally fall into the Beginner (eight percent) or Formative (47 percent) stages, meaning they are performing below average on cybersecurity readiness.
Microsoft launches DALL-E-based, AI-powered Bing Image Creator
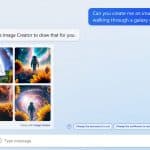
Continuing its AI push, Microsoft has announced Bing Image Creator. Powered by OpenAI's DALL-E, the tool can be used to generate images using artificial intelligence.
Microsoft says that Bing Image Creator will form part of Bing chat, and it will accept natural language prompts to create (just about) any sort of image you might want. The tool will also be made available in Microsoft Edge, making it -- the company is quick to highlight -- the first and only browser with an integrated AI-powered image generator.
Ransomware surges as threat actors get more aggressive

Ransomware and extortion actors are utilizing more aggressive tactics to pressure organizations, with harassment being involved 20 times more often than in 2021, according to a new report.
The study, from Palo Alto Networks' Unit 42 threat intelligence team, finds harassment is typically carried out via phone calls and emails targeting a specific individual, often in the C-suite, to pressure them into paying a ransom demand.
Windows 11 Moment 2 update is slowing SSDs and putting system boot times in slo-mo

While there was much interest and excitement surrounding the release of the Moment 2 update for Windows 11, seasoned users were bracing themselves for the inevitable problems to emerge. And emerge they have.
There are a growing number of complaints from people who have installed the update that their system boot times have massively increased. There are also serious issues with severely reduced SSD performance, leading to slow file transfers and poor overall performance.
Kingston announces overclockable FURY Renegade Pro DDR5 Registered DIMMs

If your server, desktop, or workstation can use DDR5 Registered DIMMs, today is your lucky day. You see, popular memory-maker Kingston has announced impressive new Renegade Pro DDR5 RDIMMs under its "Fury" line.
What makes these sticks particularly impressive is they can be overclocked. Kingston will be offering the FURY Renegade Pro DDR5 RDIMM kits in various speeds (4800MT/s, 5600MT/s, and 6000MT/s) and capacities (16GB, 32GB, 64GB, 128GB, and 256GB).
Veteran file hosting service Zippyshare to shut down at the end of the month

Although there are many file hosting services to choose from, Zippyshare is one of the better known, having been around since 2006.
Providing an easy, fuss-free way to store and share files, Zippyshare has a lot of fans, but it’s been struggling to make ends meet recently, despite still seeing around 45 million visits a month.
How to avoid fraud while remaining compliant

The financial technology (fintech) industry is a rapidly expanding web of innovation, but it is also becoming increasingly entangled by challenges posed by cybercriminals. These bad actors threaten both data security and regulatory compliance, which can result in heavy fines for noncompliance.
Such fines pose a significant risk for entrepreneurs seeking to quickly scale their operations, as they cannot afford to be bogged down by regulatory issues. Even established businesses find it challenging to navigate the complex layers of financial regulations, let alone startups.
ForgeRock launches password-free enterprise identity platform

People have been predicting the end of the password for a very long time, yet they still remain key to securing access to many systems.
Maybe the end is edging just a bit closer though as ForgeRock announces Enterprise Connect Passwordless, a new passwordless authentication solution that eliminates the need for users to interact with passwords inside large organizations.
Why a bigger budget isn't necessarily the key to good cybersecurity [Q&A]

Cyberattacks are expected to reach historic levels this year, in both volume and sophistication, yet many organizations are reducing their 2023 cybersecurity budgets.
We spoke to Steve Benton, VP of threat research at intelligence-driven cybersecurity specialist Anomali, to discover how a different approach might offer strong protection without breaking the bank.
Microsoft tests option to let you receive Windows 11 updates sooner

Microsoft is working on a new option for Windows 11 that will give users the ability to receive updates for the operating system faster. With the option enabled, there will be no need to wait until Patch Tuesday each month in order to get the latest bug fixes, or even new features.
It also means that there will be no need to manually hunt down the preview versions of updates Microsoft makes available. If this sounds interesting, it is possible to get on board and try out the early access feature right now.
Cloning voices: The opportunities, threats and needed safeguards

Microsoft recently made headlines by announcing it is working on a form of artificial intelligence (AI) called VALL-E that can clone voices from a three second audio clip. Imagine that now AI can have anyone’s voice say words without that individual actually speaking! Even more recently, Samsung announced that its software assistant, Bixby, can now clone users’ voices to answer calls. Specifically, Bixby now lets English speakers answer calls by typing a message which Bixby converts to audio and relays to the caller on their behalf.
Technologies like VALL-E and Bixby are bringing voice cloning to reality and have the potential to be industry game changers. The term voice cloning refers to the ability to use AI to build a digital copy of a person’s unique voice, including speech patterns, accents and voice inflection, by training an algorithm with a sample of a person’s speech. Once a voice model is created, plain text is all that’s needed to synthesize a person’s speech, capturing and mimicking the sound of an individual. In fact, many different types of voice cloning companies are now launching, making this technology much more accessible.
Microsoft Edge is getting an integrated crypto wallet
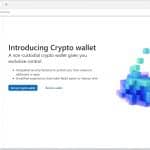
Microsoft is working to bring a cryptocurrency wallet feature to its Edge browser.
Known simply as "Crypto wallet" the feature is currently undergoing development and is being trialed on a test group of unknown size. Microsoft highlights the benefits of having the non-custodial wallet embedded in Edge, eliminating the need for a browser extension.
Microsoft is bringing huge changes to app pinning and app defaults in Windows 11
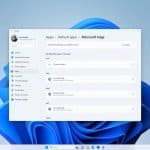
Microsoft has unveiled plans for what it is referring to as "a principled approach to app pinning and app defaults in Windows". The company has outlined sweeping changes that are coming to Windows 11 that will give users greater control over their computers.
The updates mean that the pinning of apps to the Start menu, desktop and taskbar will respect user choices, and adjusting the default apps used to open specific file types will be much easier. Microsoft says that the changes -- which are due to hit the Dev Channel soon before making their way to everyone else -- will also benefit developers.
New platform aims to deliver consumer insights without compromising privacy

The online world means that there is more information available about individuals than ever before. At the same time, however, there's growing concern around tracking and privacy.
A new SaaS platform launched this week by Qudo uses 'zero-party' data shared by consumers in anonymous online surveys, rather than rely on first- and third-party data collected via cookies.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.