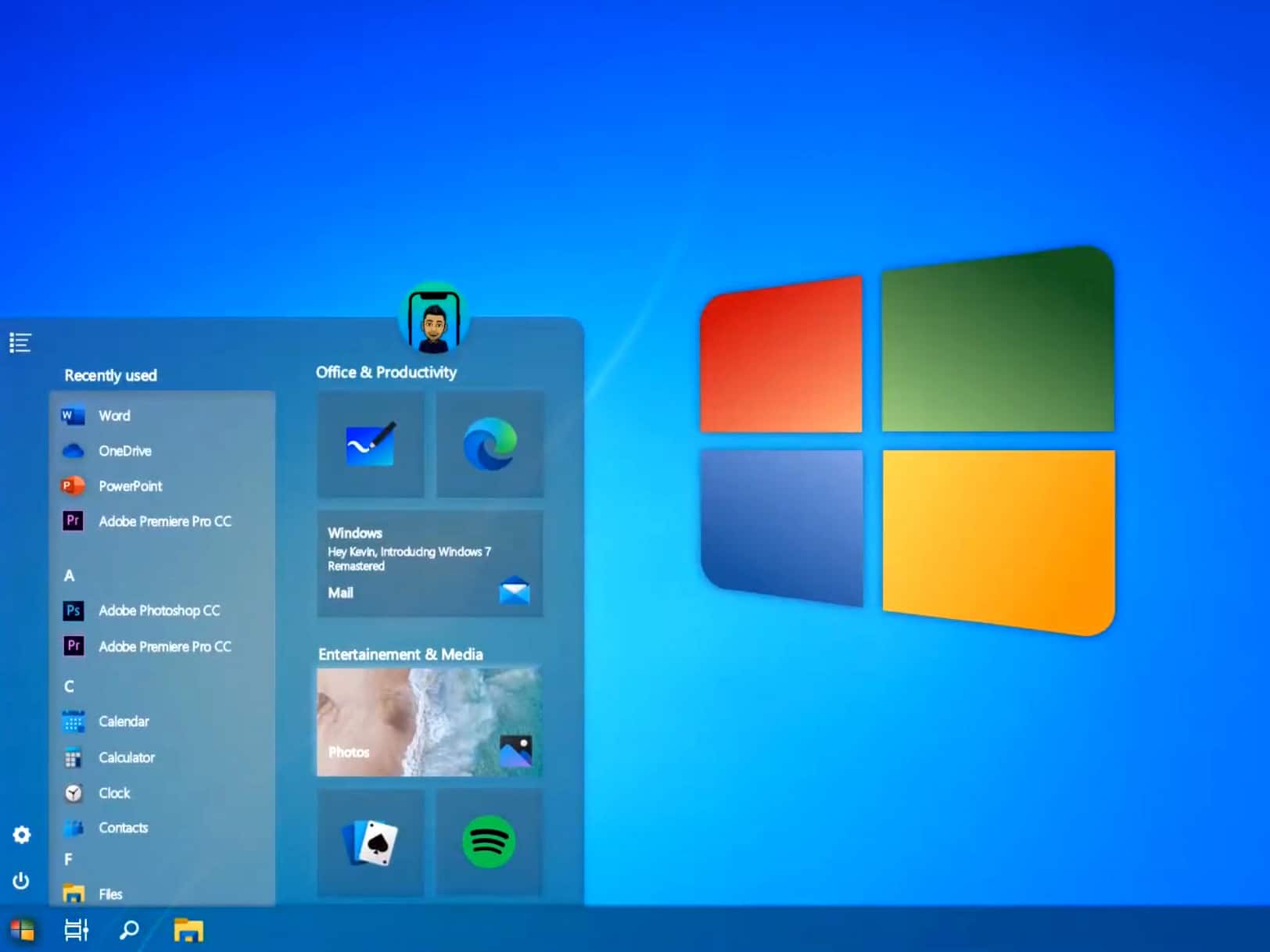
Windows 7 returns with the stunning 2020 Edition
Microsoft pulled the plug on Windows 7 five months ago, giving users a pretty stark choice -- switch to Windows 10, or stick with an aging operating system that the software giant is no longer supporting.
While the more sensible choice would be to upgrade to Windows 10, there are plenty of people who have avoided doing so for various reasons, not least that they just prefer how Windows 7 does things -- no Cortana, no forced Bing integration, no invasive telemetry…

New platform helps prevent data loss when employees leave
Around a third of employees take data with them when they leave a business according to email security firm Tessian.
In order to help companies understand and tackle the risks it's launching a new Human Layer Security (HLS) Intelligence platform to provide businesses with deeper insights into human layer security threats and the tools required to trend down the risk of accidental data loss, data exfiltration and advanced impersonation phishing attacks.

Microsoft publishes Windows Terminal 2.0 roadmap
Windows 10 is undeniably a graphic-based operating system, but there have always been various text-driven command line options too. With Microsoft increasingly embracing Linux, the arrival of Windows Terminal was pleasing if unsurprising.
The utility provides access to the Command Prompt, PowerShell and WSL (Windows Subsystem for Linux), and although version 1.0 has only just been released, Microsoft has already published it roadmap for Windows Terminal 2.0.

Sony PlayStation 5 has a revolutionary design, while Microsoft Xbox Series X looks tragically boring
Xbox Series X isn’t ugly. In fact, it looks rather cool. The problem, however, is the design of Microsoft’s upcoming video game console is tragically boring. It is literally a rectangular cuboid, showing very little effort was put into the design. Does the appearance of a console even matter? Actually, yes. Look, it is probably going into a living room or bedroom, so it will have a big impact on the room’s overall style.
Earlier today, Sony finally unveiled the upcoming PlayStation 5, and holy moly, it looks so much prettier than the Xbox Series X. The design is futuristic and iconic. Microsoft should be very worried that consumers will be turned off by the very conservative design of the Xbox Series X.

System76 launches AMD Ryzen-powered 'Serval WS' portable Linux workstation
The year 2020 undoubtedly belongs to AMD. After trailing Intel for years in some areas, the company has finally leapfrogged the Pentium-maker. Between its Ryzen and Ryzen Threadripper processors, AMD owns the enthusiast desktop market. And that's not all -- the company's Ryzen 4000 Series Mobile Processors are impressing on laptops too. Hell, Linus Torvalds, the father of Linux, is now using a computer powered by AMD's Ryzen Threadripper 3970X.
Linux computer maker/seller System76 has been offering AMD processors in its Thelio desktop computers, but believe it or not, the company has never offered an AMD-powered laptop -- until now, that is. You see, starting today, you can buy a "Serval WS" powered by AMD. No, System76 is not offering mobile Ryzen chips in this laptop, but instead, desktop-class processors! As you can expect, this 15-inch portable Linux workstation is quite chunky and heavy as a result. With that said, it is simply impossible to cram this much power into a thin and light notebook.

Data analysts spend only half their time analyzing data
During the course of a typical workday, data analysts only spend half their time actually analyzing data according to a new study.
Conducted by Dimensional Research for Fivetran, the online survey of around 500 data professionals across five continents also shows 68 percent of the analysts who responded say they have ideas that would drive more profit for their organizations, but they lack time to implement them.

How hackers are targeting enterprises from the outside
In the past businesses have needed to worry about protecting their networks. But the expansion of internet use, cloud and as-a-service products means there are now more potential threats to worry about.
A new study from attack surface management specialist RiskIQ looks at the digital presence of organizations, where they lack visibility, and the pathways hackers are using to exploit these blind spots.

UK government invests in security by design
The UK government is announcing that it will provide £10 million ($12.5 million) over four years to develop groundbreaking cyber security technologies.
Nine grant winners have been revealed as the recipients in the government's Digital Security by Design program, which aims to help the tech infrastructure of UK organizations and digital devices be more resilient to cyber attacks.

Vivaldi 3.1 unveils new Notes Manager tool, customizable menus
Vivaldi Technologies has unveiled Vivaldi 3.1 for Windows, Mac and Linux. The release comes 48 hours after the first major update for Vivaldi for Android.
The desktop build unveils a major upgrade to its existing Notes feature in the form of a full-blown Notes Manager tool. The tool is now accessible via its own full-screen tab in the main browser window (click the link in the Start page or type vivaldi://notes/ into the browser’s address bar).

Windows 10 being upgraded to the May 2020 Update without user consent
Who can forget the bad old days when Microsoft decided it knew best and forced Windows 10 upgrades on users without their consent? Windows 7 owners who left their systems alone for any length of time often returned to find they’d been 'upgraded' to Windows 10.
Thankfully those days are behind us, and now when Microsoft rolls out a Windows 10 feature update that’s compatible with your system, you can choose when to install it. Except, that is, when Windows 10 goes rogue and installs the latest update without warning.

70 percent of security professionals say election infrastructure is at risk
A new survey of security professionals shows that 70 percent of respondents believe their governments can't adequately defend election infrastructure against domestic and international cyber attacks.
In addition the study, from machine identity protection company Venafi, finds that 75 percent believe the spread of disinformation is the greatest threat to election integrity.

Tweaking Windows 10 to remove features and lock down your privacy? You're violating Microsoft's copyrights
Although Windows 10 doesn’t spy on its users in the way it did when first launched, and people now have much greater control over their privacy settings, the truth is many users would prefer to tighten their control over the operating system further than Microsoft allows.
There are a number of great free third-party tools which let you boost your privacy and make various changes to the software, including removing annoying bundled software. That’s fine right? Not according to a lawsuit in which Microsoft says this is a breach of its license.

Logitech launches 2020 Design Collection of wireless mice
When it comes to product design, there are many paths to take. You can, of course, go for a basic and boring design, or opt for an elegant style. But what about fun? Playful and whimsical designs are not just for children -- adults can enjoy some funkiness too.
A great example of fun design comes from Logitech. Each year, it releases a collection of mobile wireless mice with playful exteriors. For 2020, the company is introducing the Design Collection for its M325C mouse. This year, the company has produced some truly colorful and fun styles of the non-Bluetooth and non-rechargeable wireless mouse.

You can watch today’s big PlayStation 5 reveal live here!
Between the pandemic and widespread police brutality, America is in deep trouble. As usual, however, the USA will ultimately survive and come out stronger as a result. Wisely, Sony decided to delay its big PlayStation 5 game-play reveal during the peak of protesting George Floyd's murder. Obviously, it would have been tone-deaf to discuss video games in the middle of a worldwide movement to fight against racial inequality and police brutality.
While the protests are still happening (racial inequality is arguably a forever-battle), Sony has decided enough time has passed, and it is time to reschedule the big PS5 event. Yes, we will finally get to witness some significant PlayStation 5 game footage later today at 4:00 PM Eastern Time. While not guaranteed to happen, many people are hoping Sony will also reveal the design of the PS5 console. Hey, we have already seen the revolutionary controller.

Internet Archive to close its National Emergency Library two weeks early following legal action
Three months ago, in response to the COVID-19 pandemic and resulting lockdown, the Internet Archive created a National Emergency Library with over 1.4 million books that you could borrow immediately.
By suspending waitlists for books in its lending library, the Internet Archive hoped to best serve the nation’s displaced learners. The plan at the time was to offer this Emergency Library "through June 30, 2020, or the end of the US national emergency, whichever is later".



