
Microsoft takes us on a nostalgia-fueled trip through time
Microsoft has a long and illustrious/checkered history (delete as applicable), and if you’ve worked with computers over the years you’ll have used many of the company’s ever-evolving software and hardware.
In a new video, Microsoft takes us through time, starting on April 26 1983 and going right through to today, showcasing just how much things have changed over the years.

Acknowledging 'poor' drivers can break Windows 10, Microsoft tweaks update schedule and gives partners new powers
Updates for Windows 10 proved more than a little problematic last year, but it wasn't just Microsoft's own updates for the operating system that caused issues -- driver updates were often a headache for users too.
A confidential company document has now been published that details how Microsoft plans to deal with the problem. There are two key lines of attack: changing the release schedule for drivers that require Microsoft approval so they do not coincide with Windows updates, and giving hardware partners the option of requesting a block on feature upgrades that cause problems.

New Year's resolutions go digital as people vow to cut screen time
If you haven't made or broken any New Year's resolutions yet, here are some you might like to try. Research from Kaspersky indicates that 40 percent of people plan to change their digital lifestyle in 2020 with most aiming to reduce the time they spend with their gadgets.
The research shows 42.3 percent would make a digital New Year's resolution for 2020 rather than something more traditional.
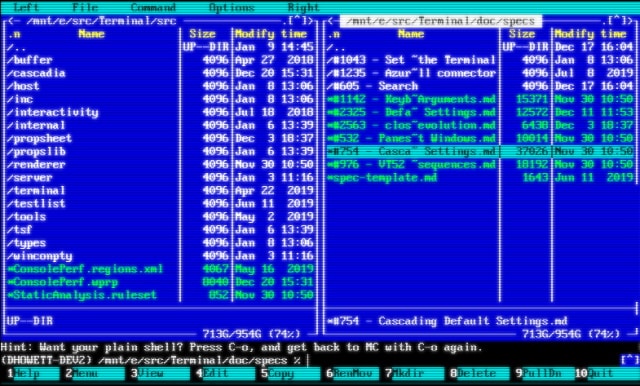
Microsoft is giving Windows Terminal a retro look with CRT effects
Updates are usually released to introduce new features and take things forwards, but with the next update to Windows Terminal Microsoft is taking inspiration from the past.
Due for release next week, the updated version of Windows Terminal will include experimental retro-style CRT effects. What does this mean in practice? It means using the old school PxPlus IBM VGA8 font and CRT-style scan lines; pointless, but a nice bit of fun. Of course, there are also other things to look forward to in this update.

Plugable announces USB-C DisplayPort 1.4 MST to Dual HDMI 2.0 Adapter
It is remarkable that as time marches on, laptops are actually losing ports. You'd think computers would get more useful over time, but actually, it is the opposite. Instead, notebook manufacturers are largely embracing USB-C, meaning customers have to buy dongles to regain the ports they need. This can be both a blessing and curse. As a positive, it looks better aesthetically and lessens the chance you will have outdated ports on your machine. On the negative side of this, not only do dongles and adapters cost money, but they are easily lost too. Sigh.
But hey -- at least we have companies such as Plugable producing affordable, high-quality dongles so our needs can be met. If you need to connect your laptop to multiple monitors, that company has a new adapter that should interest you. The USB-C DisplayPort 1.4 MST to Dual HDMI 2.0 Adapter can push two 4K monitors at 60Hz. This is important, as many similar adapters top out at 30Hz, leading to a very poor visual experience. Best of all, it is very inexpensive at under $40.
Best Windows 10 apps this week
Three-hundred-and-sixty-eight in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft released the first new build of the year 2020 to the Fast Ring channel. Since it is the first build after the Holiday period, it includes mostly bug fixes.
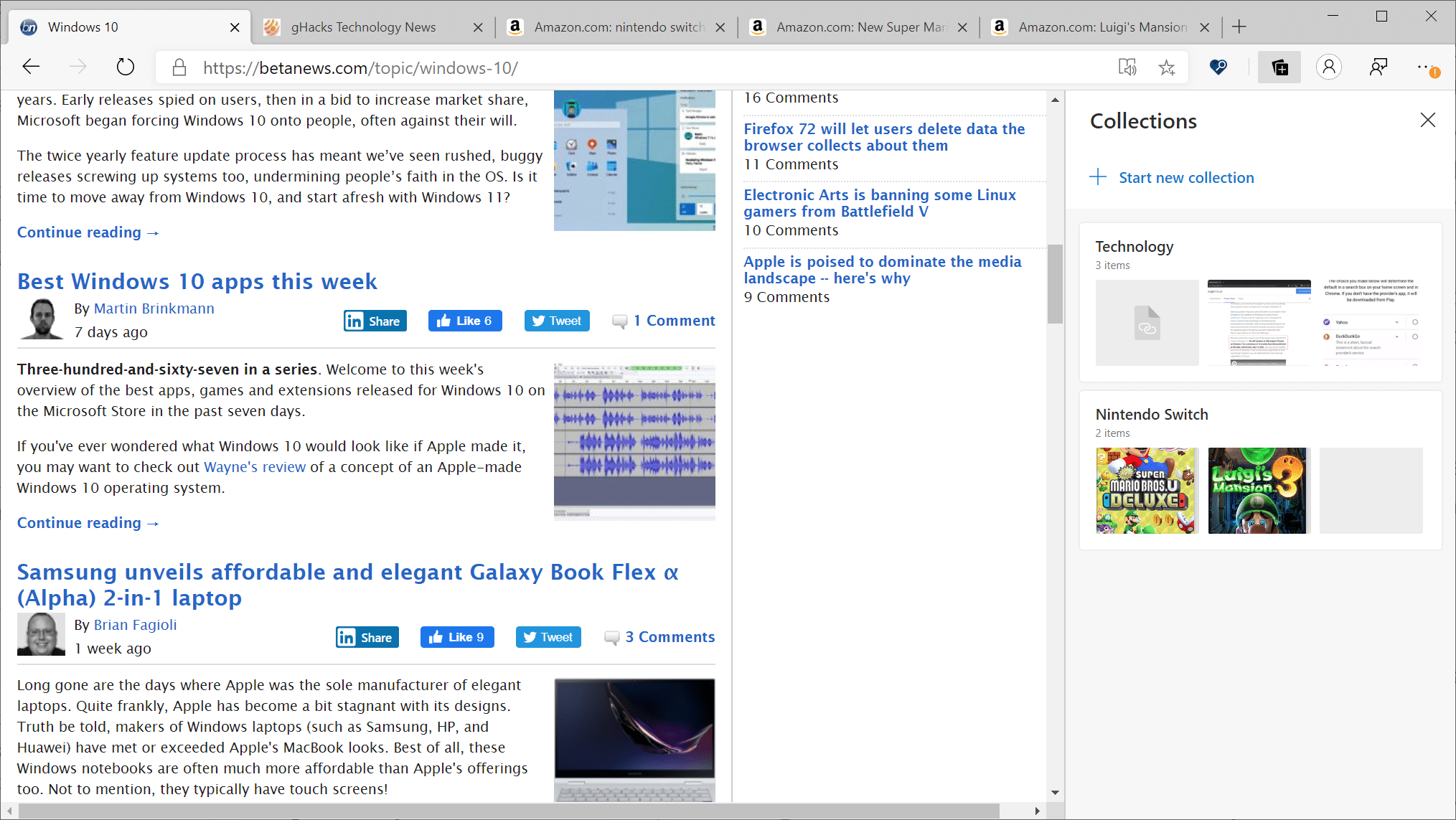
A look at new Microsoft Edge's Collections feature
The new Chromium-based Microsoft Edge web browser will be released on January 15, 2020 (a day after support ends for Microsoft's Windows 7 operating system) and Microsoft plans to provide it as an upgrade that will replace the classic version of Edge.
Since the new Edge is based on Chromium, it is clear that some things have changed. You can follow development of the new Edge here on BetaNews or on the official Edge Development blog.

Laplink makes it easy to switch to Windows 10 with its Windows 7 Migration Kit
It is now mere days until Microsoft stops supporting Windows 7. The company, as well as security experts, are keen to get as many users as possible onto Windows 10 so they do not find themselves in the position of not receiving updates.
For many people, though, the prospect of upgrading is daunting -- so Laplink is trying to help out. The company has announced the release of Windows 7 Migration Kit. Designed with both home and business users in mind, the software bundle includes PCmover Professional, DiskImage and SafeErase for a special, low price.

Plugable announces 2.5 Gigabit USB-C Ethernet adapter for Windows, Mac, and Linux
While consumers seem to love thin and light laptops, there is one big downside to such svelte computers -- a lack of ports. You see, if a port is thicker than the body of the notebook, then it simply can't fit. While USB-A and USB-C ports are thin enough to be included on many laptops these days, there is one useful (yet thick) port that is being omitted -- Ethernet. Yes, the once-ubiquitous networking port is becoming increasingly more rare. This isn't a big deal for some consumers, as they will likely only ever use Wi-Fi. Some folks, however, still have either a want or need to connect to a network using a cable.
Thankfully, with dongles, you can add an Ethernet port to pretty much any computer these days. For the vast majority of consumers, a gigabyte dongle (such as this one that costs less than $20) is currently more than enough. But what if you have a desire to connect to a multi-gig network? In that case, there are faster dongles, such as this excellent USB-C 2.5G model from TRENDnet. Soon, there will be yet another such product on the market, this time from Plugable. What makes this USB-C 2.5G adapter so special is that it has an attached Type-A adapter.

US government-funded phones come with pre-installed malware
Researchers at Malwarebytes have uncovered malware pre-installed on phones offered under the US government-funded Lifeline Assistance program.
Assurance Wireless by Virgin Mobile offers the UMX U686CL phone as their most budget-friendly option at only $35 under the scheme. However, users are getting more than they bargained for. An app called Wireless Update is designed to update the phone's OS but can also install other apps without consent.

Plugable unveils 100W TBT3-UDZ Thunderbolt 3 and USB-C docking station
If you have a laptop with Thunderbolt 3, and you like to use the computer as a makeshift desktop, a docking station is a must-buy. Whether you own a Mac or Windows 10 notebook with TB3, one of these docks can transform your portable computer into a powerful and useful desk-based workstation. A single wire from the docking station to the computer will provide you with numerous ports, plus charging. It is immensely convenient to plug in one cable and immediately have access to a mouse, keyboard, large monitor, etc.
There are many Thunderbolt 3 and USB-C docks on the market these days, but thanks to the Intel Titan Ridge chipset, there are now models that can accommodate both of those connectivity options (such as this one from StarTech). Plugable has a new such model, and it looks incredible. It has one big feature that many other docks are lacking -- an SD card reader on the front. Taking it a step further, it even has a dedicated micro SD card port! That is very cool, as it means you can read the smaller card without the need of an adapter.

Why your business needs cyber risk insurance [Q&A]
Protecting against cyberattacks and guarding against technology failures is something that most businesses now do as a matter of course. But insuring against the risks is less common and could be leaving companies open to major losses.
We spoke to Jack Kudale, CEO of cyber insurance specialist Cowbell Cyber to find out more about cyber risk insurance and why it's increasingly being seen as an essential safeguard.

Samsung T7 Touch is a USB 3.2 Gen 2 SSD with integrated fingerprint reader
CES 2020 has been very exciting for those interested in data storage. Just yesterday, Western Digital unveiled a prototype 8TB portable SSD plus a diminutive 1TB flash drive with both USB-C and USB-A connectivity. Both of these drives should prove very popular with consumers -- if/when they hit stores.
Today, it is Samsung's turn to wow the data storage community. The company's latest SSD, called "T7 Touch," is an external drive that uses USB-C for connectivity and features USB 3.2 Gen 2 speeds. What makes it particularly interesting however, is its integrated fingerprint reader which is used for secure hardware encryption.

Microsoft releases Windows 10 Build 19541 to the Fast ring
The holidays are nothing but a distant memory now, and so it’s back to business as usual for Microsoft which has just released its first new Windows 10 build of 2020.
Fast ring Insiders are now receiving builds from future versions of the operating system, and new Build 19541 introduces some minor improvements.

Satechi launches 108W Pro USB-C PD Desktop Travel Charger
Just yesterday, Satechi launched a revolutionary charging mat that can charge multiple devices at once. While that is very convenient, not all people like wireless chargers. After all, wired charging still remains a faster option. Not to mention, it is still necessary for larger devices, such as laptops and tablets. And so, wired chargers are still very much relevant.
Today, Satechi launches a new product for those that prefer a wired charging experience. Called "108W Pro USB-C PD Desktop Travel Charger," it has a total of four USB ports -- two are USB-C, while the others are USB-A. It plugs into a standard wall power outlet, making it a great choice for both home and on-the-go charging. It can charge smartphones, tablets, laptops, and more.



