
Why serverless platforms will unlock a new era of low-code development [Q&A]
As developers look for ways to improve productivity they're moving away from 'no-code' offerings and have their sights set on serverless platforms to help bolster their 'low-code' solutions.
Serverless platforms take tasks like managing application resilience, performance, security and compliance away from developers, allowing them to focus on functionality and innovation. We spoke to Briana Frank, VP of product at IBM Cloud to find out more about how serverless will unlock the next era of low-code.

Evolution of cloud data protection: Why your business needs a Data Command Center
Businesses face increasing hurdles when protecting sensitive data in today's complex digital, hybrid, and multi-cloud environments. The truth is that historically, data security has been the core challenge that enterprises have been aiming to tackle given the fact that data breaches have become increasingly common as attackers deploy more sophisticated techniques to cause extensive damage to companies, including monetary losses, reputational harm, and legal penalties.
In this context, deep and proactive data insights are required -- knowing where sensitive data resides or who has access to it is no longer a ‘nice-to-have,’ but a must. However, steps adopted to mitigate these challenges still have a lot to do with data security as a silo, while not necessarily as part of a broader understanding of how data is being used or how it needs to adhere to regulations across the entire organization, which usually comes as an afterthought.

Anomaly Detection: Four steps to avoiding unforeseen cloud costs
Data volumes are simultaneously exploding and migrating, making it difficult for businesses and their CIOs to both monitor and secure across their environments. With so many moving parts in the cloud, it can often run away with businesses because as it expands to handle the data that it’s given, so does its cost. This is both a blessing and a curse, as flexibility is a vital attribute of a successful business, but it means that unanticipated cloud costs are common and hard to track.
Anomalous, unexpected costs can crush businesses’ confidence in their budgets and forecasts, impact their burn rate and make it difficult to understand their wider spending patterns. Yet, despite this, many wait until their bill arrives before reacting. To avoid these unpleasant surprises, which can be caused by a repository error, crypto mining incident or simply because servers have been spun up and forgotten about, businesses can turn to Anomaly Detection tools with great success.

Understanding how on-premises system costs compare to cloud-based solutions
In today’s uncertain economic environment, understandably every purchase decision needs to be thoroughly analyzed and the cost to the business clearly understood. With so many organizations migrating to the cloud, it is important to understand not only the cost of migrating systems but also the longer-term costs.
IT managers must understand the main business driver(s) for moving their organization to the cloud, and those drivers need to be reconciled with business application requirements. Some applications will be CPU-intensive, others memory-intensive, while others are cost-sensitive. Likewise, understanding whether this is the best short and long-term solution for the business as well as the total cost of ownership (TCO) and predicted return on investment (RoI) is important.

Generative AI raises SaaS security worries
IT leaders are grappling with anxiety over the risks of generative AI despite continued confidence in their software-as-a-service (SaaS) security posture.
New data from Snow Software, which surveyed 1,000 IT leaders, finds 96 percent of respondents say they are still 'confident or very confident' in their organization's SaaS security measures, and yet, 'managing the security of SaaS applications' is the top challenge for IT leaders.

Identity management is top challenge for CISOs
Identity access management (IAM) is a key priority for enterprise security leaders according to the latest CISO Survival Guide, released today by Cisco along with Forgepoint, NightDragon, and Team8.
According to the guide 85 percent of IT decision-makers prioritize IAM investments more highly than other security solutions, while 23 percent of respondents report that user and device identity management is a top priority.
Google launches new service to eliminate virtual desktops
Google and Cameyo are launching a new service that will help organizations to save money and increase productivity by switching from Windows to ChromeOS devices while maintaining access to their Windows apps.
ChromeOS Virtual App Delivery with Cameyo gives organizations the ability to eliminate costly and insecure virtual desktops while still maintaining access to all of their applications. This is claimed to reduce total cost of ownership by 54 percent compared to virtual desktops, improve security, and deliver a better user experience.

Half of browser extensions pose a high risk to business
As businesses increasingly turn to SaaS applications in order to streamline their operations and facilitate hybrid working, a new report reveals the risks that can be posed to these apps by browser extensions.
The study from Spin.AI shows almost 51 percent of browser extensions pose a high risk to data stored in Google Workspace and Microsoft 365, and 44 percent pose a medium risk.

Microsoft is willing to make massive cloud concessions to gain UK approval for Activision Blizzard deal
Microsoft's attempt to acquire Activision Blizzard has been a long, drawn-out affair with a seemingly endless series of obstacles along the way. Now the company has indicated a willingness to make major concessions as it submits a revised deal for approval.
Facing regulator opposition to the deal in the UK so far, Microsoft's latest proposal to the CMA (Competitions and Markets Authority) includes an offer to sell cloud gaming rights to Ubisoft.

It's in the cloud somewhere... Three-quarters of enterprises don't know where their apps are
A new study reveals that 76 percent of enterprises don't have complete visibility into the access policies and applications across multiple cloud platforms, including which access policies exist, where applications are deployed, and who does and doesn't have access.
The report, from Strata Identity based on data from Osterman Research, shows the percentage of organizations using a single cloud identity provider (IDP) is down from 30 percent to 20 percent since last year. The other 80 percent are now using multiple IDPs to manage enterprise identity.

74 percent of cloud and web applications with PII are vulnerable to exploits
New research reveals a high proportion of vulnerable public cloud, mobile and web applications exposing sensitive data, including unsecured APIs and personal identifiable information (PII).
The study from CyCognito, based on analysis of 3.5 million assets across its enterprise customer base, finds 74 percent of assets with PII are vulnerable to at least one known major exploit, and one in 10 have at least one easily exploitable issue.

New tool helps IT teams measure their environmental footprint
All organizations are under pressure to make their operations greener and more sustainable. But sometimes it can be hard to accurately measure the impact of your operations, especially if you're relying on cloud services.
Nutanix is launching a new tool to help organizations understand how different factors can influence their environmental footprint by estimating annual power and emissions for various solutions and locations.

Sensitive data is exposed in over 30 percent of cloud assets
New analysis of more than 13 billion files stored in public cloud environments reveals that more than 30 percent of cloud data assets contain sensitive information.
The study by Dig Security shows personal identifiable information (PII) is the most common sensitive data type that organizations save. In a sample data set of a billion records, more than 10 million social security numbers were found -- the sixth most common type of sensitive information -- followed by almost three million credit card numbers, the seventh most common type.
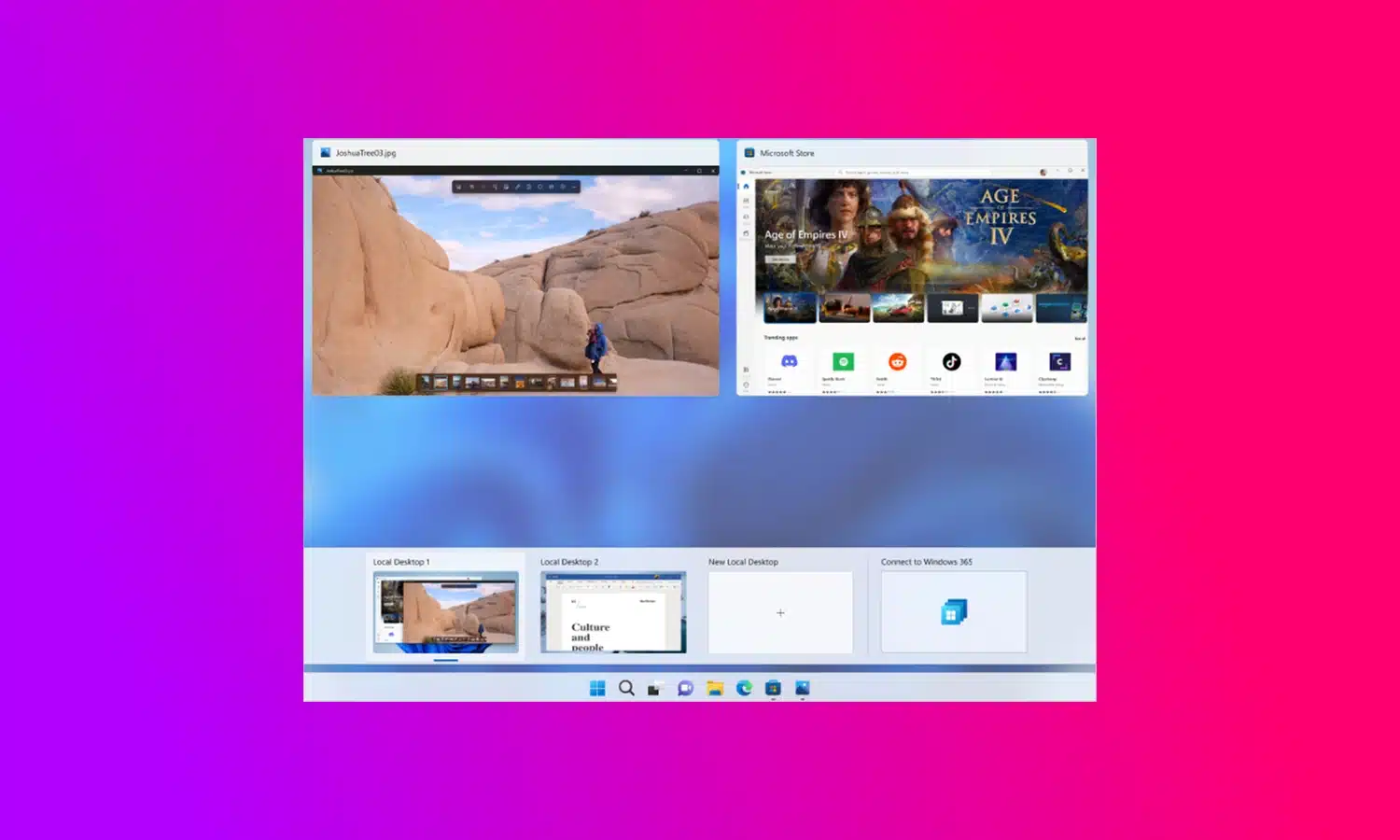
Microsoft releases Windows 365 Switch to simplify moving between a cloud PC and the desktop
Microsoft has announced the availability of the public preview of Windows 365 Switch. The utility makes it easy for Windows 11 users to jump between a Windows 365 Cloud PC and the local desktop.
The company highlights the benefits of the feature to BYOD scenarios, pointing to a seamless experience from within Windows 11 via the Task view feature. Using Windows 365 Switch, switching between a Cloud PC and a local desktop can be achieved with keyboard commands, as well as a mouse-click or a swipe gesture.

A clean bill of health: Harnessing data for precision healthcare
Unlike other industries, UK healthcare isn’t defined by how much revenue can be generated. Instead, success is measured in terms of achieving positive health outcomes for patients.
With new healthcare data available from a variety of sources -- such as wearables, clinical trials and biometric sensors -- healthcare is now driven as much by the promise of data processing and advanced analytics as it is by developing new and specialized drugs. So, how can healthcare professionals move faster, and gain actionable insights from the huge volumes of data they collect?
