Revolut Mobile lands in the UK with impressive roaming data
Fintech giant Revolut has started to roll out its own mobile network across the UK. Revolut Mobile is designed – like Revolut’s banking products – with travel in mind, including a generous roaming package as standard.
The network will use Vodafone’s infrastructure and a special introductory price is available for anyone who jumps on board early on. There is a waitlist in place, with the full launch due in January 2026.

Mobile security gaps revealed by BYOD and hybrid work
Organizations face massive mobile security vulnerabilities as they increasingly embrace BYOD and hybrid strategies. At the same time traditional mobile security tools are failing to mitigate these risks while also compromising employee privacy.
A new report from secure virtual mobile infrastructure firm Hypori, based on a survey of 1,000 global security, risk, mobility, and BYOD decision-makers, finds 92 percent of security and risk leaders are facing challenges in zero trust implementation.

Netflix quietly kills off casting from phones
To little fanfare, Netflix has made changes that make it harder to cast content from a phone to another device, such as a TV.
The general rule of thumb that now applies is that if a device has its own remote control, it will not be possible to cast to it. With this covering pretty much every television in existence, this is something that will affect a lot of people.

Mobile threats increase ahead of holiday shopping season
New research from the Zimperium zLabs team reveals a sharp rise in mobile threats tied to the holiday shopping season.
The report shows that mishing (mobile phishing) remains the most widespread and effective mobile attack vector. Smishing messages and fake delivery alerts impersonating trusted retail and logistics brands surged up to fourfold during the 2024 holiday shopping period, with attackers using urgency-driven messages like ‘Your package is delayed, click here’ to trick users into revealing credentials or downloading malicious apps.

One in four free mobile VPN apps fail privacy checks
Virtual Private Networks (VPNs) are trusted by millions to protect privacy, secure communications, and enable remote access on their mobile device. But what if the apps designed to safeguard your data are not secure?
Analysis by Zimperium zLabs of 800 free VPN apps for both Android and iOS reveals that the threat is real and widespread.

Brits warned of scams ahead of emergency alert test
This Sunday, September 7th, the UK will test its emergency alert system, sending a message that will cause 4G and 5G mobile phones and tablets to emit a loud siren sound and vibrate for about 10 seconds.
But Marc Porcar, CEO of QR Code Generator, is warning that fraudsters are likely to exploit the upcoming government test, particularly targeting elderly and vulnerable people who may be confused by the alerts.
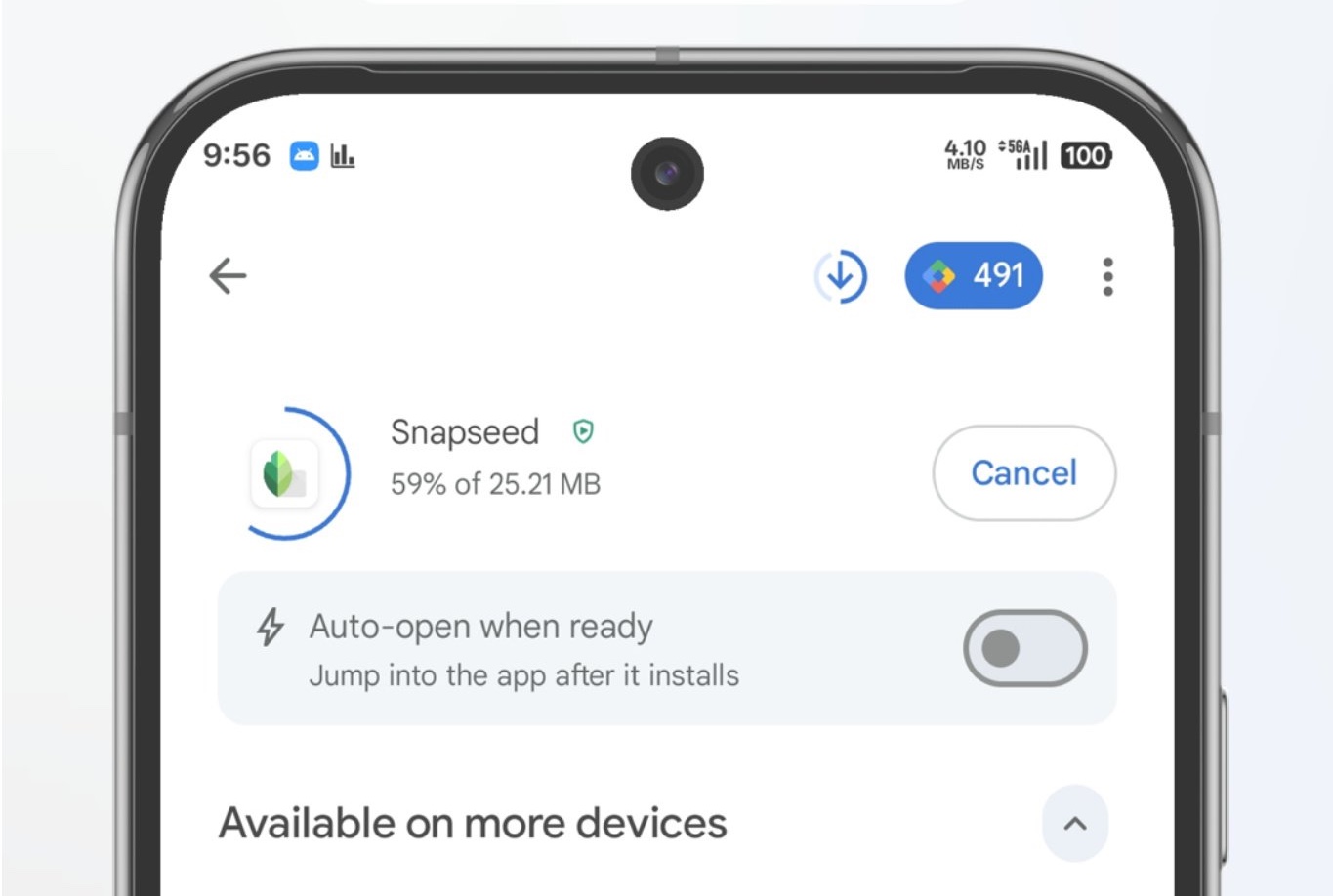
Your Android phone will soon be able to auto-open apps when installation completes
When you install an app, the chances are that you’re going to want to fire up straight away. To help with this, Google is in the process of rolling out a handy auto-open feature to Android users.
If this sounds familiar, that is because it is something Google was spotted working on back in the second half of last year. You would have been forgiven for thinking that the company had forgotten about it, but the auto-open toggle is back.
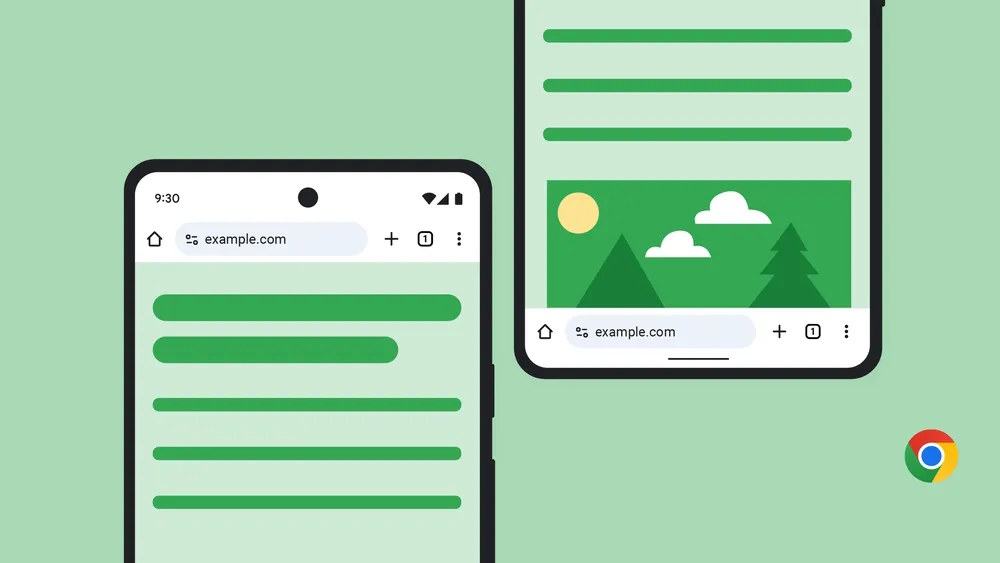
Google Chrome address bar – are you a top or a bottom?
Across all platforms, Google Chrome remains one of the most popular – if not the most popular – web browser. But while the desktop version of the software is versatile, customizable and flexible, the same cannot be said of the mobile apps.
And this is why an announcement made by Google several weeks ago caused a flurry of excitement. On the face of things, the news that it would be possible to move the address bar from its familiar position at the top of the browser may not seem huge, but now that it is rolling out, it is becoming clear that it is actually pretty significant for Android users.

Millions of unsecured Wi-Fi networks are putting data at risk
New threat intelligence from Zimperium reveals over five million unsecured public Wi-Fi networks have been detected globally since the beginning of 2025, with a staggering 33 percent of users still connecting to these open networks, putting enterprise data at risk in the process.
“Mobile devices are now a primary gateway to corporate data, but during travel, they’re also the most vulnerable,” says Kern Smith, VP of global solutions at Zimperium. “Unsecured Wi-Fi, phishing disguised as travel alerts, and risky sideloaded apps are creating an ideal attack surface for cybercriminals -- especially in peak travel months.”

Over half of employees fall for mobile phishing scams
A new report shows that security leaders have false confidence in their capabilities and employees when it comes to mobile security. While 96 percent are confident their employees can spot a phishing attempt, 58 percent have reported incidents where employees fell victim to executive impersonation scams via text message.
The study from Lookout, of more than 700 security leaders globally, underscores a critical need for organizations to rethink their cybersecurity strategies, particularly around the human-risk factors for social-engineering attacks.

Why we need to focus on mobile device security [Q&A]
When getting a new smartphone most people focus on features and pricing, while security tends to be overlooked. But as we access the internet more using mobile devices, protecting users' personal information, transactions, and digital identities is vital.
We talked to Tom Tovar, CEO of Appdome, to discuss why mobile security should be at the forefront of consumer and media conversations and why it's currently being neglected.
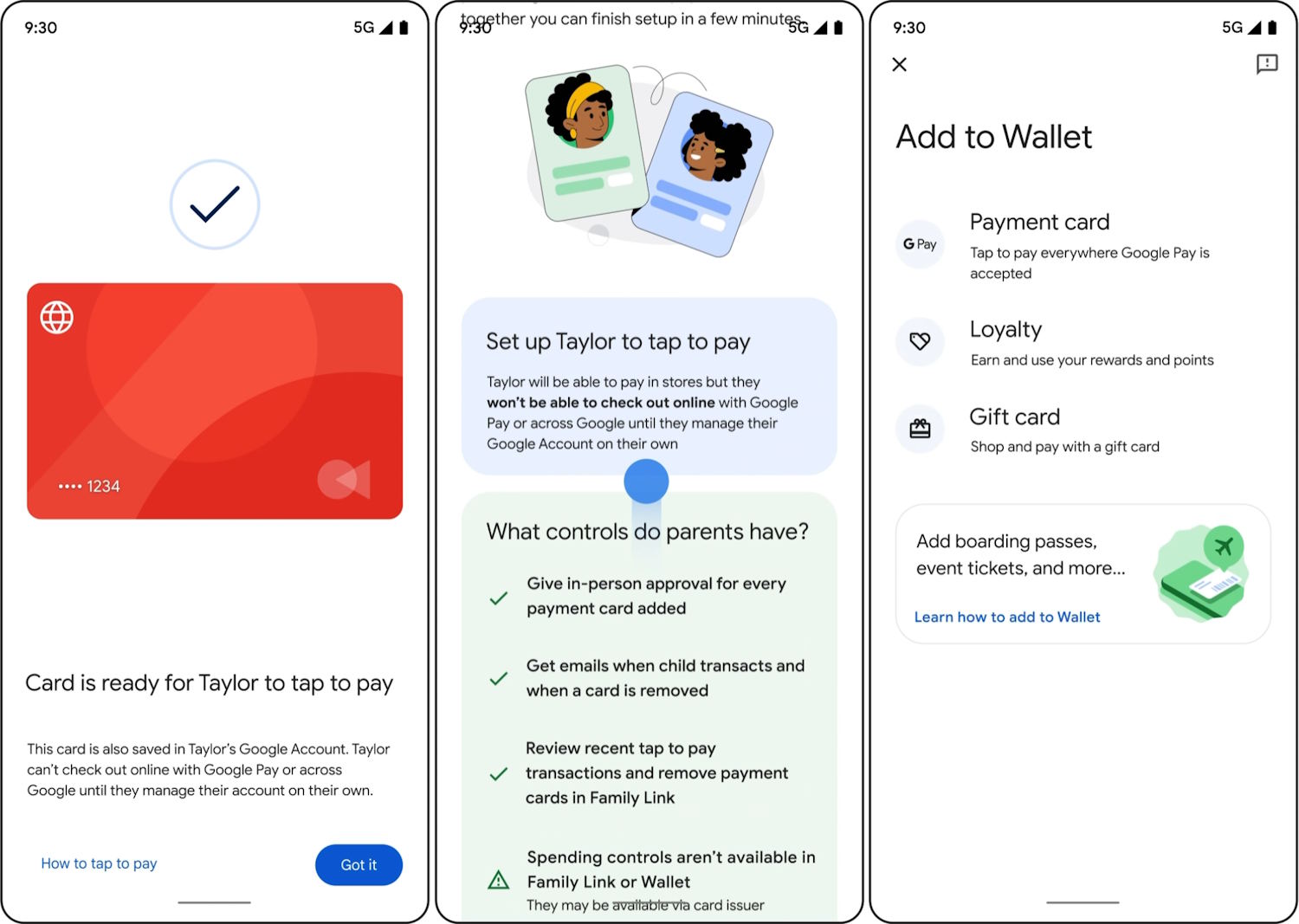
Google Wallet update means kids can now use digital payments and store their passes
Google is rolling out a significant update to Google Wallet that opens up the digital wallet to children.
The update enables children to not only make digital payments and use tap-to-pay, but also to store a range of passes, cards and tickets in one place. The consent of a parent or guardian is required to add a child’s card to Google Wallet, and there are comprehensive supervision tools available.

Mobile-first phishing attacks surge as specific capabilities are targeted
As organizations increasingly rely on mobile devices for business operations, including multi-factor authentication and mobile-first applications, mobile phishing poses a severe risk to enterprise security.
New research from Zimperium's zLabs shows a surge in mobile-focused attacks, dubbed 'mishing', activity peaking in August 2024 with over 1,000 daily attack records. These attacks are specifically designed to evade desktop security measures, executing only on mobile devices.

Mobile intelligence APIs open up visibility into enterprise mobile security data
Mobile and cloud security company Lookout is launching new Mobile Intelligence APIs integrating critical security data from mobile devices into the solutions already in use by enterprise security teams -- those like SIEM, SOAR, and XDR.
This is aimed at allowing security teams to identify cross-platform attacks, risky trends or abnormalities, and potential risks.
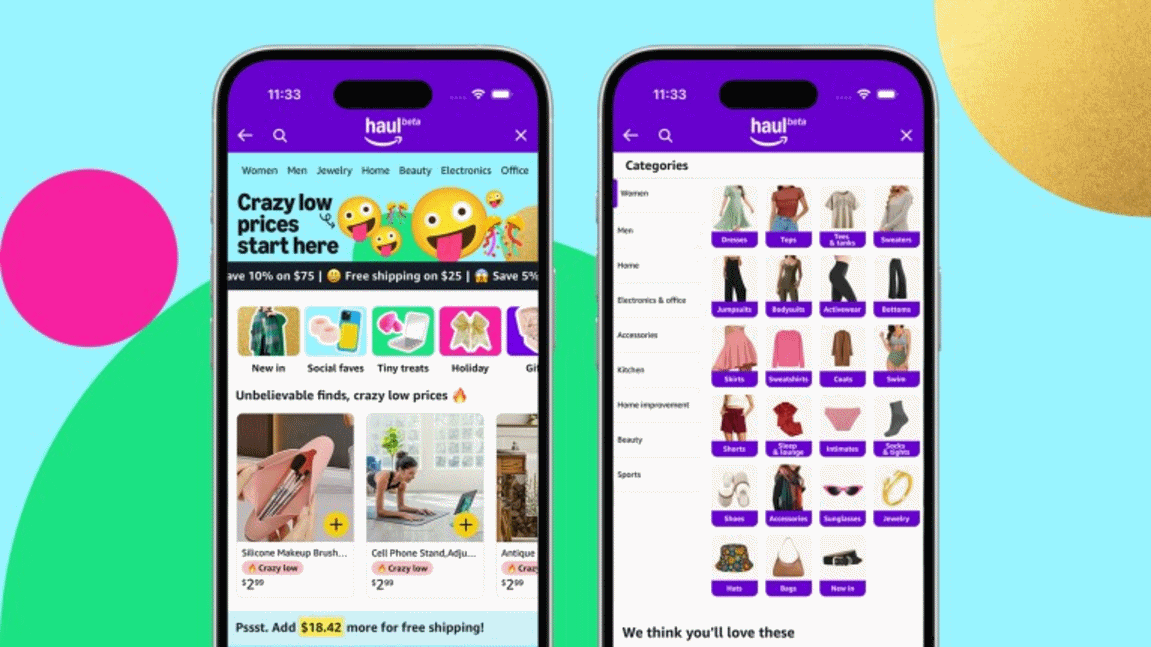
Amazon launches Amazon Haul in beta as a low-cost Temu alternative
Amazon may be one of the biggest names in online retail, but in recent years the likes of Temu has started to encroach on its territory by offering products at absurdly low prices.
Now Amazon has come up with a response. Amazon Haul is a new shopping experience that has launched in beta for US shoppers. Building on the Fulfillment by Amazon (FBA) service, Haul is home to “affordable fashion, home, lifestyle, electronics, and other products with ultra-low prices”. Most things are priced under $10, so what’s the catch?
