2020 mobile phishing trends

Phishing is nothing new, but the COVID-19 pandemic has seen an increase in attacks around the world as cybercriminals seek to exploit the opportunities offered.
Mobile security company Zimperium has produced an infographic looking at phishing trends with a particular emphasis on the mobile sector.
Careless scammers leave stolen passwords exposed online

Hackers responsible for a large-scale phishing campaign unintentionally left over a thousand sets of stolen log-in credentials accessible to the public via a simple Google search.
The error was uncovered by researchers at Check Point. and Otorio. The stolen credentials were stored in designated web pages on compromised servers.
Firmware attacks, sophisticated ransomware and ID fraud -- cybercrime predictions for 2021
Spammers get better at pretending to be banks

As always, spammers and cybercriminals seek to take advantage of the peak online shopping season covering Black Friday and the Christmas holidays.
The Bitdefender Antispam Lab has identified a series of campaigns impersonating online banking and financial organizations. In October six in 10 emails (58.84 percent) relating to the banking industry were fraudulent.
Parcel delivery phishing scams up 400 percent in November

Researchers at Check Point have seen a 400 percent increase in phishing scams using DHL, Amazon and FedEx branding to try to get people to part with information during the peak online shopping period.
Two weeks ago, Check Point researchers documented an 80 percent increase in malicious phishing campaigns targeting online shoppers with 'special offers.' The latest spike uses subject lines like 'track your shipment' and 'delivery problem.'
More than 5,000 Black Friday-related scam sites registered in November

While the holiday season is a peak time for retailers, it also represents an opportunity for cybercriminals. This is particularly true of 2020 when more people than ever are likely to be shopping online.
Research from Comparitech analyzed around 30 million websites registered this month to identify efforts by cybercriminals to trick consumers looking for holiday shopping deals.
Beware the 'Windows Update' that can install malware, steal your personal information, and encrypt your PC
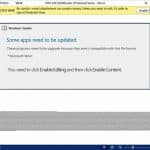
Emotet began life as a banking Trojan back in 2014 but has since evolved into something much worse -- a self-propagating platform that can deploy multiple exploits and spam campaigns.
The number one malware threat today, Emotet usually takes a break during the summer months while the developers behind it work to add new features and capabilities, and now it’s back with a new 'Windows Update' attachment.
Security breaches at a standstill but COVID-related attacks increase

The latest annual Cybersecurity Report Card from threat intelligence specialist DomainTools shows security breaches among those surveyed have remained essentially unchanged from last year's report at 16 percent.
Yet almost 60 percent of organizations detected a moderate to a dramatic increase in cyber attacks during and following the pandemic, which points to a rise in the overall breach prevention success rate.
Employees would rather be Mobile Mollies than Desktop Doras

More than 80 percent of global employees do not want to return to the office full-time, despite 30 percent claiming that being isolated from their team was the biggest hindrance to productivity during lockdown.
A new study from mobile-centric security platform MobileIron also uncovers some worrying views around security, with 33 percent considering it to be low priority.
Half of organizations experience remote work security incidents

Between March and July 2020, almost half of companies experienced a data breach or security incident according to a new report, and half of these were caused by phishing attacks.
The study from Tessian also reveals that 82 percent of IT leaders think their company is at greater risk of phishing attacks when employees are working away from the office.
Ransomware operators work together to maximize effectiveness of attacks

The numerous challenges of 2020 have proved to be fertile ground for ransomware attacks, with the number up by nine percent compared to the first quarter and by 59 percent compared to the second quarter of 2019.
The latest Threatscape report from Positive Technologies shows that 16 percent of phishing attacks took advantage of COVID-19 concerns, and there is also evidence that ransomware operators have started cooperating with each other.
Why vishing is the new phishing and how to guard against it [Q&A]

We're all familiar with the menace of phishing but, particularly following the recent Twitter attack, other methods of stealing credentials have been on the rise.
These include 'smishing' (phishing via SMS) and 'vishing' (phishing by voice call). We spoke to Ed Bishop, CTO at email security company Tessian to find out how businesses can identify vishing and smishing attacks, how the attacks work, and how companies can protect their employees.
Phishing attacks surge during the pandemic

In yet another example of cybercriminals exploiting world events, the frequency of phishing threats has risen considerably since the start of the pandemic, with companies experiencing an average of 1,185 attacks every month.
New research from GreatHorn reveals that more than half (53 percent) of over 300 IT professionals surveyed by Cybersecurity Insiders say they had witnessed an increase in phishing activity since the start of the COVID-19 pandemic.
New phishing attack tries to steal Office 365 credentials via Box

Researchers at cloud security platform Armorblox have uncovered a phishing attack that seeks to steal Office 365 login credentials.
So far, so predictable. The clever twist here though is that the initial page victims are taken to via the email link is hosted on cloud file sharing service Box, followed by a credential phishing page that resembles the Office 365 login portal.
Edison Mail gives iOS users added phishing protection
Phishing is a problem that shows no signs of going away and indeed the COVID-19 pandemic has seen a new raft of malware and fraudulent emails seeking to trick the unwary.
Edison Software is launching a new AI-based email security subscription plan that can be added to the Edison Mail iOS app to help combat the threat.
Recent Headlines
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.
