Microsoft invites you to report malicious and phishing websites as it crowdsources security

Microsoft is opening itself up to submissions from the public, making it possible for people to provide information about malicious websites. A new page on the Windows Defender Security Intelligence (WDSI) website gives anyone the opportunity to pass on details of phishing sites and other malicious pages directly to Microsoft.
The WDSI portal is described by Microsoft as being in preview, so it's possible that what you see now may change over time.
Attackers impersonate bank emails to cash in on post-Equifax fears

In the wake of the recent breach at credit agency Equifax it's only natural that people are keeping a close eye on their bank statements and credit reports.
Of course the bad guys know this too and a new report by Barracuda Networks looks at an email attack that is impersonating a 'secure message' from financial institutions.
Phishing attacks reduce but more companies are targeted

Threat detection company RiskIQ has released the latest of its quarterly reports into threat trends, this one looking at phishing.
It finds that in the second quarter of 2017 there were 39,320 unique phishing domains, down from 45,025 back in the first quarter. However, there were 316 targeted phishing brands in Q2 -- up 15.7 percent from the 273 brands targeted in Q1.
Over one million phishing websites are created every month

Every month, almost 1.5 million new phishing websites are created. This is according to a new report by Webroot, showing just how big of an industry phishing really is.
The Webroot Quarterly Threat Trends Report says that 1.385 million new phishing sites are created every month. May was the busiest of them all, with 2.3 million sites created.
Office workers fall victim to phishing attacks despite training

Despite training and other efforts to combat the problem, phishing is still proving a remarkably effective tactic for cyber criminals according to a new report.
The study by cloud business applications company Intermedia shows that while 70 percent of office workers say that their organization regularly communicates with employees about cyber threats as a means of prevention, there are significant gaps between confidence and effectiveness.
Sophisticated phishing attacks target Office 365

With over 100 million monthly subscribers, it's not surprising that Office 365 is a popular target when it comes to attempting to steal credentials.
A new report from Barracuda Networks looks at how phishers are sending out authentic-looking emails purporting to be from Microsoft asking users to reactivate their accounts.
Phishing is the top threat faced by organizations

Both users and their endpoint devices are the primary target for cyber criminals with phishing being the most prevalent threat according to a new report.
The study from research and education specialist the SANS Institute finds security professionals rate phishing at 72 percent, spyware at 50 percent, ransomware at 49 percent, and Trojans at 47 percent as being the top threats today.
Cyber criminals target mortgage transactions as they phish for a big catch

Buying a house is the biggest purchase most people make, with large amounts of money involved it’s not surprising that these transactions are attractive to cyber criminals.
Security specialist Barracuda Networks has released an analysis of a recent mortgage spear phishing attempt where an attacker attempted to divert a payment.
Email scam is a growing problem for enterprises

Email phishing scams continue to strike a huge number of businesses, in spite of much more improved cyber-security policies, new research has revealed.
The latest Email Security Risk Assessment from Mimecast discovered that ambitious hackers are also increasingly targeting C-level executives and impersonating those in senior leadership positions in order to trick employees into transferring money or valuable IP data. The report found that there had been a 400 percent rise in so-called impersonation attacks in just the last three months of the year.
Gmail offers better malware and phishing protection for enterprises

Google has updated Gmail with a number of new security features aimed at businesses that require better protection against malware and phishing scams.
The company announced today that it is bringing early phishing detection to its email service by using machine learning along with click-time warnings for malicious links found in emails as well as unintended external reply warnings.
Phishers cash in on WannaCry attack

The UK's ActionFraud cyber crime reporting center is warning customers of BT’s internet services of a phishing scam claiming to protect against WannaCry-style attacks.
The emails claim that BT has launched preventative measures to protect data on an international scale and try to get recipients to click on a link to a 'security upgrade'.
Data breach at DocuSign leads to massive phishing campaign

E-signature and security firm DocuSign has confirmed a data breach in which attackers gained access to a database containing customer email addresses. The company says that no other data was revealed in the security breach, but it led to a large phishing campaign.
Attackers used the stolen email addresses to spam people with emails containing an infected Microsoft Word document. The company insists that its core service remains secure, but coming in the wake of the WannaCry ransomware attack, people around the world are on high alert.
Word vulnerability, Windows bug, and 'Trump's_Attack_on_Syria' document used in Sednit phishing attack

The Sednit group believed to have been involved in interference with the French election was also responsible for a phishing attack that used President Trump to lure in victims. Security firm ESET analyzed a phishing email with an attachment named Trump's_Attack_on_Syria_English.docx and found that it had the hallmarks of the well-known group.
The document was engineered to infect victims' computers with the Seduploader tool, and it did this by exploiting two vulnerabilities, one in Microsoft Word, and one in Windows. Sednit -- previously known as APT28, Fancy Bear, and Sofacy -- took advantage of a recently discovered Remote Code Execution vulnerability in Word (CVE-2017-0262) as well as a security hole in Windows (CVE-2017-0263) in executing the attack.
Google adds phishing protection to Gmail app on Android
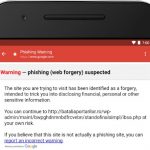
Gmail users will now be protected from phishing attacks on their Android phones thanks to a new update from Google. The company is rolling out a new security feature similar to that found in the web version of Gmail, warning people when an email contains a suspicious link.
For now, the update is only rolling out to Android users, and Google has not indicated whether it will make its way to iOS in due course or not. The update comes just shortly after a phishing scam emerged in which recipients were encouraged to click on a link to open files purporting to be stored on Google Docs.
Cyber squatters target UK bank domains

Part of the art of making a phishing attack successful is having a domain name that looks sufficiently similar to a legitimate one not to arouse suspicion in the target.
Research by threat intelligence specialist DomainTools has uncovered over 300 registered domains using the names of five of the UK's top high street banks.
Recent Headlines
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.