
Millennials want to share personal data -- but not for free
Sharing for the sake of it won't suffice among millennials, a new study has shown. But if there are certain benefits to be had, well, that is now a completely different story. Business intelligence company SAS, together with research agency Future Foundation, came to these conclusions after extensive research.
It says millennials, which it also calls "Data Generation" (16 - 34 year-olds), expect a "hyper-personalized service from brands". They are willing to use their personal information as bargaining chips to get a better experience from businesses.

When is stupidity fraud?
Next month I return from my first—and hopefully last—summer sabbatical. I resume writing with a question for you: "When is stupidity fraud?" I ask because someone is using my gmail address to sign up for a humungous number of newsletters and websites. At first, I presumed someone trolled me. But that no longer appears to be the case. This guy, presumably living in North Carolina, either uses my address randomly to hide his identity, or he mistypes one that is similar. Given many of the services are for an unidentified widower looking for love, I assume the latter.
Behind my question are real concerns about identity and privacy that do not just apply to me. The email address gives me the ability to change the passwords and even cancel accounts—both of which I have done, treating his misuse of my email address as identity theft and violations of my privacy; after years of careful cultivation that reduced spam, crap is on the rise as this misuse spreads my gmail identity across dating and discount sites and sex webcams. Who knows on what mailing lists it will appear next.

New law requires IMDB to respect actors' privacy and remove ages on request
If you've ever got into an argument about the age of an actor, or you've just been curious about how old someone is, you may well have hit IMDB to find out. But starting next year, the Internet Movie Database will have to comply with requests to remove age details from profiles after the state of California passed a new anti-discrimination law.
The bill, AB-1687, requires that all sites that have paid subscriptions that allow people to post resumes and other information respect requests to remove information relating to age -- or just not post this information in the first place. Welcomed by some, the new legislation has also been criticised for being a violation of free speech.
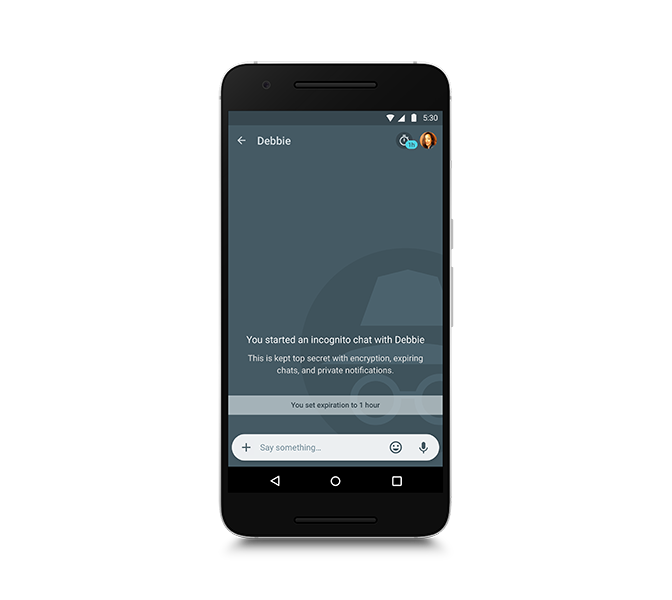
Google's new chat app Allo is a privacy nightmare
Four months ago, Google announced two new communication apps: Duo, for video calling, and Allo, for traditional WhatsApp-style messaging. Duo arrived for Android and iOS a month ago, while Allo is available from today.
While Allo is a good looking app, it has some big privacy issues that users need to be aware of.

Time to learn Pig Latin, your devices are listening
While it’s convenient to turn lights on, lock doors, check humidity levels and monitor energy use in your home with your smartphone, those conveniences come at a cost; even something as seemingly harmless as monitoring calorie burn with a connected device can lead to a breach. Billion dollar companies are having a hard time shielding themselves against hackers, insider threats and data leakage, let alone a single device in your home.
When you register devices and tie them to your email account and address you are opening that information up to be invaded. Additionally, fitness trackers are revealing whether you have met your goals, coffee pots are recording how quickly you go through your favorite brew and thermostats are recording what time of day you are home. All of this information is valuable to companies because it can be sold to other businesses that can customize ads to fit the data you are inadvertently feeding them. Even the FTC has expressed concerns over what the Internet of Things will mean for the future of privacy and security.

GCHQ plans Great British Firewall to protect web users
The UK's cyber intelligence agency GCHQ is planning what has been labelled a 'Great British Firewall' to protect individuals and companies against cyber attacks.
The idea emerged in a speech delivered by the head of GCHQ's national cybersecurity centre, Ciaran Martin, at the Billington Cyber Security Summit in Washington DC.

Adblock Plus introduces new platform to increase Acceptable Ads’ transparency
It has been difficult to ignore the issue of online ads recently. Facebook’s approach to ads has been in the news in particular, but the battle between advertisers and ad blockers is one that has rumbled on for some time -- and looks set to continue to do so. At the forefront of ad blocking is Adblock Plus, and the company has just announced a new ad platform that aims to deliver ads that will not irritate internet users too much.
Acceptable Ads is an idea that has been bounced around for a while now, but today it has been relaunched as a completely new platform -- the Acceptable Ads Platform, funnily enough. It has two primary directives: to increase the transparency of Acceptable Ads, and to provide website creators with easy access to a database of pre-whitelisted ads that they can use to monetize their sites.

Employees sue Seagate over HR department's private data leak
After falling victim to a phishing scam in March, Seagate is now being sued by its own employees whose sensitive data was exposed in the leak.
The company's HR department was tricked into providing the operators of the phishing scheme with the personally identifiable information (PII) of 10,000 past and current employees and W-2 forms that include their Social Security numbers along with their wage, salary and tax information.

Microsoft opens UK datacenters for Office 365 and Azure
Microsoft has announced that local datacenters are now available in the UK to Office 365 and Azure customers. This enables companies dealing with UK-only customers to ensure that data remains within the country and fully complies with data protection and privacy laws.
Describing itself as the "first global cloud productivity provider" to offer UK residency for data, Microsoft says Azure and Office 365 are now generally available from multiple data center locations in the UK. It has already attracted the custom of the Ministry of Defence.

Microsoft gains support from Mozilla, EFF, Google and Apple in fight against US gagging orders
Microsoft is fighting the US Justice Department in an attempt to quash a law that prevents companies informing customers that the government is requesting their data. The technology giant has the backing of other tech companies as well as media outlets.
Amazon, Apple, Google, Fox News, Electronic Frontier Foundation and Mozilla are among those offering their support to Microsoft. The lawsuit says that blocking companies from keeping their customers informed is unconstitutional, and it comes at a time when tech companies in particular are keen to be as open and transparent as possible about government requests for data.
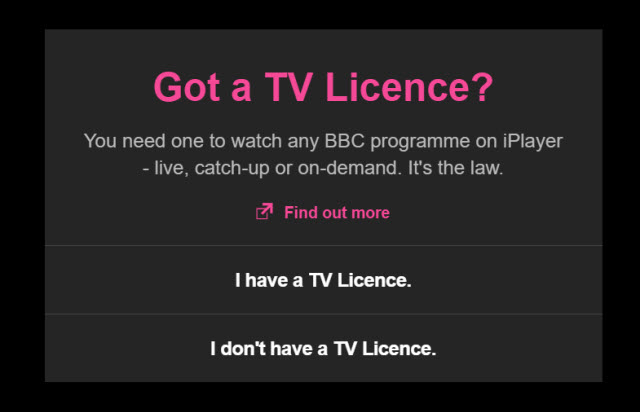
Now you need to buy a TV licence to watch BBC iPlayer, and privacy advocates are concerned
As of today, Thursday 1 September, if you stream any content from BBC iPlayer without owning a TV licence, you are breaking the law. But as with licences for televisions, it's not clear how -- or, indeed, if -- the BBC will be checking to see whether watchers have paid up or not.
If you fire up BBC iPlayer now, you'll be greeted by a nag screen that asks: "Got a TV licence? You need one to watch any BBC programme on iPlayer -- live, catch-up or on-demand. It's the law". Viewers need to click to indicate whether or not they have a licence, and of course there is nothing to stop people from lying. What is not known, though, is whether privacy-invading snooping will be used to perform licence checks.

Your personal data is worth less than $1
There's a new calculator online which will tell you exactly how much your digital data is worth. This tool, created by Totally Money, asks you to name the price for 13 different data types, including email address, health condition, or credit rating. After giving your price, the calculator then tells you the real price.
The whole project was basically designed to show people just how easy and cheap it is for companies to buy your personal data. Following the release of the calculator, the company also did a survey of 1,000 UK adult consumers. Forty percent of Facebook users, for example, didn’t know the social media giant sold their data to third parties.

Iran starts to roll out its own 'domestic internet'
Iran, much like China, is not a country that has the best reputation when it comes to granting citizens unfettered access to the internet. Now, a new initiative is underway, which sees the roll out of its own 'domestic internet', dubbed the National Information Network.
The country is rolling out its own national internet in a bid to provide affordable internet access to people, but there are concerns that there will be severe limits placed on online activity. Iran already blocks access to the likes of Facebook and Twitter, and a government-controlled internet, it is feared, could lead to a further erosion of privacy and individual control.
Opera sync servers hacked, usernames and passwords at risk
Opera Software is advising all users of the sync feature of its Opera browser to change their passwords following a security breach. Details are a little scant at the moment, but the company says that servers were breached earlier in the week and user data may have been compromised.
Opera Sync is used to synchronize user data between different computers but it is apparently used by under "0.5% of the total Opera user base". However, with a user base of 350 million this means that upwards of 1.7 million people could be affected.
Information Commissioner to investigate data sharing between WhatsApp and Facebook
WhatsApp's plans to share user data with Facebook are to be investigated by the Information Commissioner's Office (ICO) in the UK. The change in privacy policy goes against a previous public commitment not to share data in this way.
The ICO has the power to regulate how companies make use of data belonging to people located in the UK, even if the companies themselves are located elsewhere. A key concern is whether there will be compliance with data protection laws.
