
Immigration officials allowed to hack phones of refugees and asylum seekers
The British government secretly rolled out powers that permitted the immigration officials to hack the mobile phones of asylum seekers and refugees, the Observer reveals. The Home Office has confirmed the hacking powers which have sparked outrage from privacy and human rights groups.
Since 2013, immigration officials have not only been permitted to hack into migrants' phones and computers, but also to install surveillance equipment in homes and detention centers. With concern about governmental plans for the snooper's charter and the privacy invasion this entails, claims that the powers are needed to "deal effectively with all immigration crime" are likely to fall on deaf ears.

Draft encryption bill could spell the end of privacy and security as we know it
Apple's battle with the FBI has focused the attention of the technology community on encryption. But while just about all of the big players in the tech world backed Apple's refusal to create a backdoor for the FBI into iOS, Congress has a very different idea about how encryption and governmental access to data should be handled. This is perfectly demonstrated by a new bill.
The draft version of the Compliance with Court Orders Act of 2016 -- penned by Senators Diane Feinstein and Richard Burr -- would essentially force all US companies to decrypt data they may have encrypted, or to provide backdoors when asked. It's a bill described variously as 'dangerous', 'encryption-weakening', and 'anti-security', and it starts off aggressivley in stating that "no person or entity is above the law". In effect, it renders the encryption put in place by the likes of WhatsApp completely pointless as, if the bill is passed, companies would have to decrypt data on demand.

WhatsApp's end-to-end encryption is not all it's cracked up to be
Just a few days ago, WhatsApp trumpeted the roll out of end-to-end encryption for its messaging service. The world rejoiced. With events such as the battle between Apple and the FBI turning attention to encryption, the announcement was well-timed to ride the crest of the wave. But it seems that for all of the bluster and bravado, the news about extra protection may not be quite as good as it seems.
Analysis of WhatsApp's privacy documentation reveals that the Facebook-owned company retains a huge amount of data about messages that are sent. If this all sounds familiar, it's because the retention of metadata is precisely what the NSA was (is?) up to, trawling web communications and upsetting Edward Snowden and privacy advocates around the world. WhatsApp's encryption and policies mean that those who are concerned about their privacy should not rest on their laurels.

The FBI vs Apple fight is not over
The recent furore between Apple and the FBI over access to the San Bernadino shooter’s iPhone brought privacy debates firmly into the public eye. Despite tech giants, politicians and privacy campaigners explaining the potential ramifications of the case, many people remained on the fence.
A recent survey by the Pew Research Centre found that the majority of Americans sided with the FBI and believe that Apple should have complied with its demands. I find this deeply concerning because it shows how easily our collective privacy could be eroded in the name of national security, and also how little most people seem to understand the encryption technologies which protect us all.

The doctor will lose your data now -- 1 in 5 doctors' mobile devices could be at high risk
More than 27 million Android devices running medical apps are likely to have high risk malware installed according to a new report.
The Mobile Threat Intelligence report from threat defense company Skycure is focused on healthcare and finds that doctors who use mobile devices to assist their day-to-day practice are exposed to network threats, and that these significantly increase over time.

Swipebuster: $4.99 is all it costs to see if your partner (or anyone you know) is using Tinder
Its developer -- who wishes to remain anonymous -- says that his website exists to educate people about the importance of privacy. But Swipebuster sells itself as a way for suspicious partners to check upon their other halves if they think they might be making use of Tinder to seek out some 'extracurricular activity'.
Swipebuster taps into the Tinder API to access publicly available data to see if a particular individual appears in the membership database. It’s perfect not only for confirming or denying worst fears, but also a valuable tool for a would-be blackmailer. For just $5, you can conduct three searches to see if people you know are using Tinder.

Full end-to-end encryption shows WhatsApp is serious about privacy
Encryption has been a hot topic for some time, but the battle between Apple and the FBI really brought it to the fore in recent weeks. In response to the FBI trying -- ultimately successfully -- to crack into the San Bernardino shooter's iPhone, WhatsApp was just one of the companies that promised to increase encryption.
Today the popular chat tool made good on its promise, enabling full end-to-end encryption; this means that calls, messages, photos, videos, files, voice messages, and group chats are all protected with end-to-end encryption. Importantly, this extra layer of security is enabled by default, leading WhatsApp to claim it is "a leader in protecting your private communication".

Behavior ID strengthens mobile and web security
Whether it's down to stolen credentials, weak passwords or bot-based attacks, the threat of an account takeover is one of the major worries for most users.
Mobile identity company TeleSign is launching Behavior ID, a new offering that enables web and mobile applications to measure and analyze a user's behavioral patterns to provide continuous authentication, even after the user has been verified with traditional security measures like passwords.
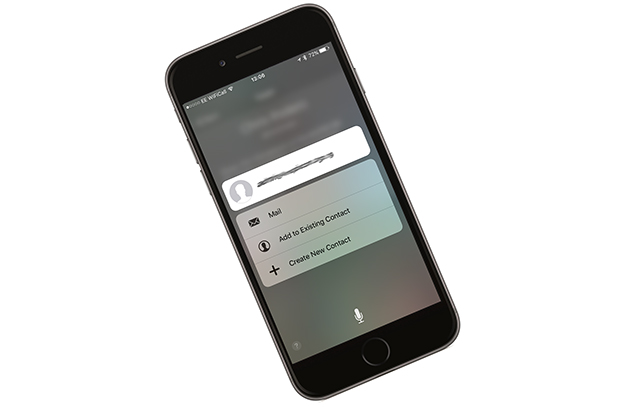
iPhone 6s security flaw lets anyone bypass the passcode and access contacts and photos
It might have taken the FBI quite some time to find a way to unlock a shooter's iPhone 5C, but it turns out to be trivially easy to access contacts and photos stored on the company’s newest flagship, the iPhone 6s.
The trick makes use of Siri and Twitter, and as the owner of a 6s I’ve been able to test this method myself, and can confirm not only that it works, but it’s very simple to implement.

93% of UK mobile users have their location tracked every day
Awareness of the privacy issues involved in using various devices and software has grown dramatically in recent years -- there can be few readers who do not know about the telemetry and privacy concerns surround Windows 10, for instance. But a new campaign by privacy-focused advocacy group Krowdthink aims to raise aware of the privacy implication of owning a mobile phone in the UK.
The 'Opt me out of Location' campaign aims to highlight the fact that nearly every single mobile phone owner in the UK (93 percent) has unwittingly signed up for a contract that permits their location to be tracked. More than this, the data collected allows providers to build up highly detailed customer profiles which Krowdthink warns leaves millions of users just one serious data breach away from having private data exposed to and abused by criminals.

Egypt bans Facebook Free Basics for NOT spying on users
In another blow for Mark Zuckerberg's free internet service, Facebook Free Basics has been banned in Egypt. The Egyptian government made the decision after Facebook refused to allow it to use the service to spy on users.
The shutdown comes just five months after Facebook Free Basics launched in Egypt, having proved controversial in other countries for contravening net neutrality rules. But Facebook's refusal to permit government surveillance of users means that the service has been banned this time for political reasons.

Apple responds to FBI iPhone hack, but questions remain
Yesterday, the FBI announced that it had managed to break into the San Bernardino shooter's iPhone sans help from Apple. The iPhone manufacturer will undoubtedly be pleased that the court case has come to an end without the company having to cave in and assist the agency.
In a statement, Apple said: "From the beginning, we objected to the FBI’s demand that Apple build a backdoor into the iPhone because we believed it was wrong and would set a dangerous precedent. As a result of the government’s dismissal, neither of these occurred. This case should never have been brought". But with the FBI's previous insistence that help from Apple was absolutely essential, some serious questions remain.
You could go to prison for sharing screenshots of Snapchat messages
The UK culture minister, Ed Vaizey, has warned that people who share screenshots of Snapchat messages without permission are breaking the law. Snapchat is characterized by its self-destructing messages that automatically delete after a short time.
The Conservative politician warned that anyone sharing screenshots of messages without consent could be sued and could face a prison sentence. If the content was of a sexual nature, it could result in a lengthier sentence.

Weakening encryption severely affects our privacy
When Apple recently refused to comply with a federal court order issued by the FBI to help it break into an iPhone 5c, belonging to one of the shooters in the San Bernardino incident, a US House Judiciary Committee hearing was held.
If a ruling is made in favor of the FBI, Apple will have to weaken the encryption of its iPhone operating system, allowing the FBI to gain access to data on any iPhone. Apple’s chief executive, Tim Cook described this as the "software equivalent of cancer".

20 percent of employees would sell their passwords
According to new research from identity management company SailPoint one in five employees would be willing to sell their work passwords to another organization, up from one in seven last year.
Of those who would sell their passwords, 44 percent would do it for less than $1,000, and some for less than $100. This is made worse by the fact that 65 percent admit to using a single password among applications and 32 percent share passwords with their co-workers.
