
Data sovereignty, cloud and security [Q&A]
As more and more information is stored in the cloud, often with hyperscale providers, the issue of data sovereignty -- where the information resides and who can access it -- becomes increasingly crucial.
We spoke to Sergej Epp, CISO at Sysdig, and previously CISO at Palo Alto Networks, to explore the theme of data sovereignty, cloud and security.

Cloud infrastructure is becoming a barrier to growth
Research released today reveals that cloud infrastructure has become the second-largest expense for tech companies, following headcount; averaging 10 percent of revenue and increasing rapidly. What’s more nearly 90 percent of companies report that it's directly affecting profitability.
The study from Cloud Capital surveyed 100 CFOs and senior financial decision makers within SaaS and technology businesses of up to 1,000 employees across the US and UK.

File-sharing platforms not protecting against malicious content
Cybersecurity company Surfshark has reviewed popular file-sharing platforms and finds that the majority of them don’t scan your files for viruses, nor do they protect you from malicious software on their free plans.
Box and WeTransfer, which together have a total of 138 million registered users, do not scan for viruses on free plans but begin scanning files on paid plans. Dropbox, with 700 million registered users, does not offer scanning at all.

Red Hat announces Project Hummingbird to boost cloud-native development
Today’s IT leaders frequently face a critical trade-off between delivery speed and systems security. AI-assisted and -generated coding tools accelerate development cycles, but this speed can run counter to the realities of managing multi-faceted, complicated software components.
This seemingly leaves CIOs with two choices, moving at the speed of business while balancing potential production systems risks, or being overcautious to the point of losing to competitor’s innovations.

Governance failures disrupt cloud migration plans
Nearly 40 percent of organizations have experienced security or compliance incidents directly linked to governance gaps introduced during cloud migration according to a new report.
The study from Pathlock, based on responses from 620 enterprise IT, compliance, and security leaders, finds that in spite of the regulatory pressures many organizations face, with respondents operating under major regulations like SOX, GDPR, and others, governance is often treated as an afterthought.

More than half of IT leaders lack resources despite increasing budgets
Although 74 percent of IT leaders expect budgets to rise in 2026 more than half say they still lack the internal resources to fix issues quickly or drive innovation.
A new report from DataStrike also finds 60 percent of organizations now rely on MSPs to manage data infrastructure, more than double the rate reported last year. This highlights a growing dependence on external expertise as teams tackle modernization and technical debt.

Businesses at risk from boom in IoT devices
New research from Forescout Vedere Labs reveals that 65 percent of devices across organizations are no longer traditional IT. Of these 11 percent are network equipment, while 24 percent are part of the extended IoT, such as IoT, OT and IoMT.
Financial services (54 percent), healthcare (45 percent) and oil, gas and mining (40 percent) are the sectors that have the highest percentages of non-IT devices.

Implementing runtime security for the cloud [Q&A]
Cloud-native platforms are built for speed with ephemeral workloads, rapid deployments, and plenty of third-party app dependencies.
This poses a real challenge to the deployment of runtime security tools. We talked to Bob Tinker, founder and CEO of BlueRock.io, to discuss how organizations can protect their cloud systems effectively.
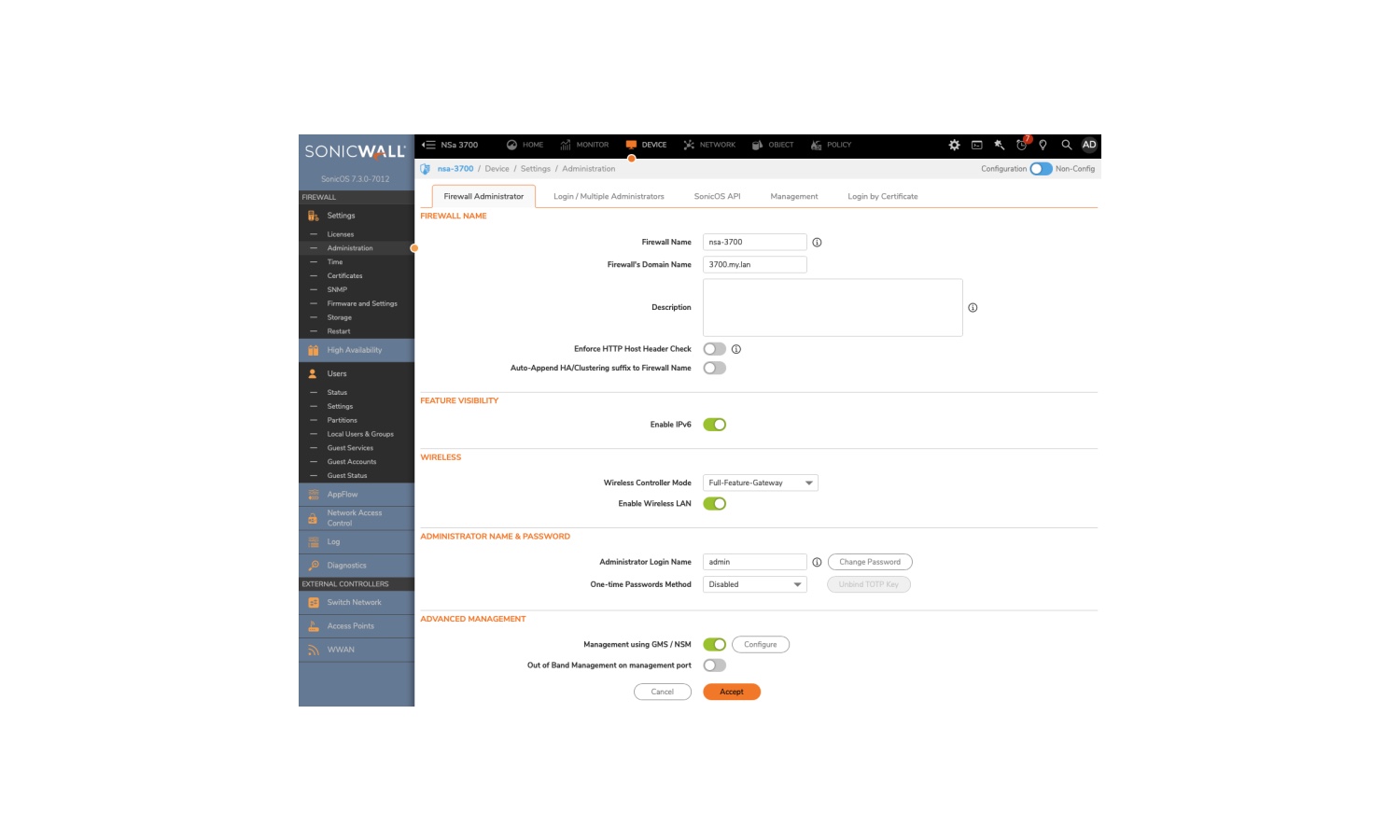
SonicWall warns its cloud backup service users to reset credential after security incident
Following a previously acknowledged security breach last month, SonicWall has published an updated bulletin to customers having investigated the incident. The company says that it is now aware that an “unauthorized party accessed firewall configuration backup files for all customers who have used SonicWall’s cloud backup service”.
SonicWall has also published an extensive document to help customers with “containment, remediation and monitoring”. This includes advising everyone to reset various passwords.
90 percent of organizations face attacks involving lateral movement
A new report from Illumio, based on a survey of over 1,100 IT and cybersecurity decision makers, finds that almost 90 percent of leaders have detected a security incident involving lateral movement within the past 12 months.
Each incident involving lateral movement resulted in a global average of over seven hours of downtime. Alert fatigue, along with limited and fragmented visibility, especially across hybrid environments, are two of the top challenges to detecting lateral movement.

Why the cybersecurity industry needs to be more accessible [Q&A]
The proliferation of different cybersecurity tools has created an operational crisis for organizations, with companies struggling to manage an increasing array of defensive technologies.
Organizations today are forced to juggle multiple tools, each with unique UI, costs, and maintenance headaches. They’re also often not able to buy the tools they need, because they are either too expensive or don't exist in the specific capacity they need.

Younger generations embrace the mainframe
Large enterprises have always relied on mainframe computing but with the rise of technologies like the cloud and AI many have predicted that those days are numbered.
Software solutions company BMC has released the results of its 20th annual BMC mainframe survey, which finds that in fact positive perception of the mainframe has reached an all-time high of 97 percent, highlighting that the mainframe remains a vibrant and growing platform.

Proton introduces emergency access to accounts
Imagine the scenario, you’re suddenly hospitalized or incapacitated following an accident but access to important information like insurance details is locked up in your computer and online accounts which no one else can access.
For this and other emergency situations Proton is launching an Emergency Access feature so that passwords and logins, documents and files will be recoverable by trusted individuals in case of an emergency.
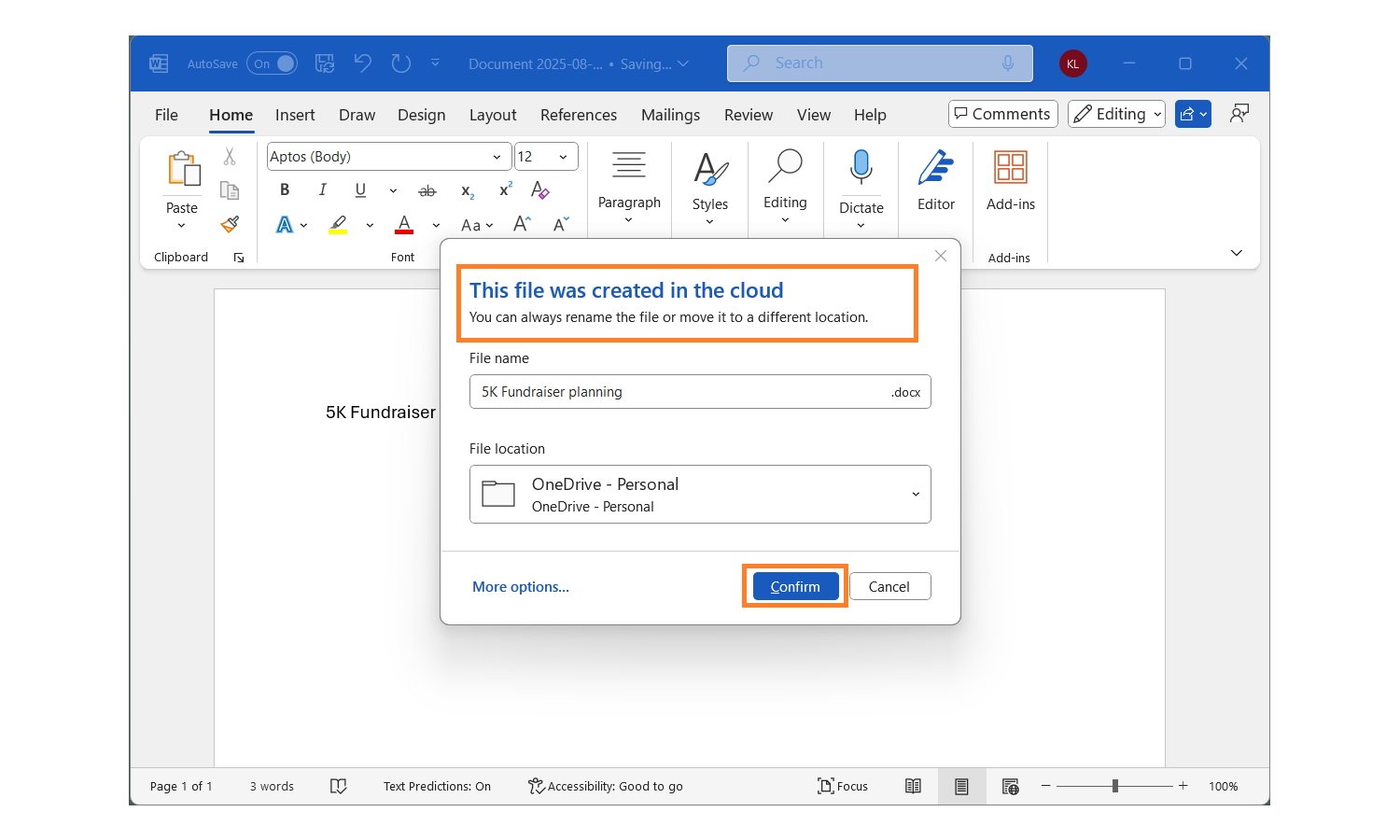
Microsoft now saves all Word files to the cloud by default
Anyone who has used Microsoft Word for a number of years will remember the times they have been saved by the autosave feature. The move to the cloud complicated things slightly meaning that many people lost files when Microsoft changed the way the feature worked.
Now the company has announced a significant change to Word that will help to dramatically reduce the risk of documents being lost by accident or because of something like a power outage or hardware failure. All Word documents are now saved to the cloud by default.
Google Drive simplifies video editing
Google Drive is home to every type of file imaginable, and a decent proportion of those files are videos. It is with this in mind that Google has decided to make it easier to edit videos which have been uploaded to its cloud storage service.
Rather than adding video editing tools directly into Google Drive, the company is instead making it easier to access the option to do so using Google Vids.
