
Remote desktop problems? Guess what? It’s probably because of another flaky update for Windows
Microsoft is, once again, using a Known Issue Rollback (KIR) to resolve a problem caused by yet another dodgy update for Windows. This time around, the issue sees Remote Desktop disconnecting and there is not yet a fix.
Just as with the recently fixed printer problems, the Remote Desktop issues are being caused by the January 2025 Windows preview update, but it is something that seems have been exacerbated by the March 2025 Windows security update.

If a Windows update made your printer act strangely, Microsoft has a fix for you
Recent updates for Windows 10 and Windows 11 had the peculiar side effect of causing printers to spew out random printouts. The culprits were the updates released back in January, although it took Microsoft a while to concede that there was a problem.
Having acknowledged the issue, Microsoft has finally produced a fix some two months after the problems emerged.
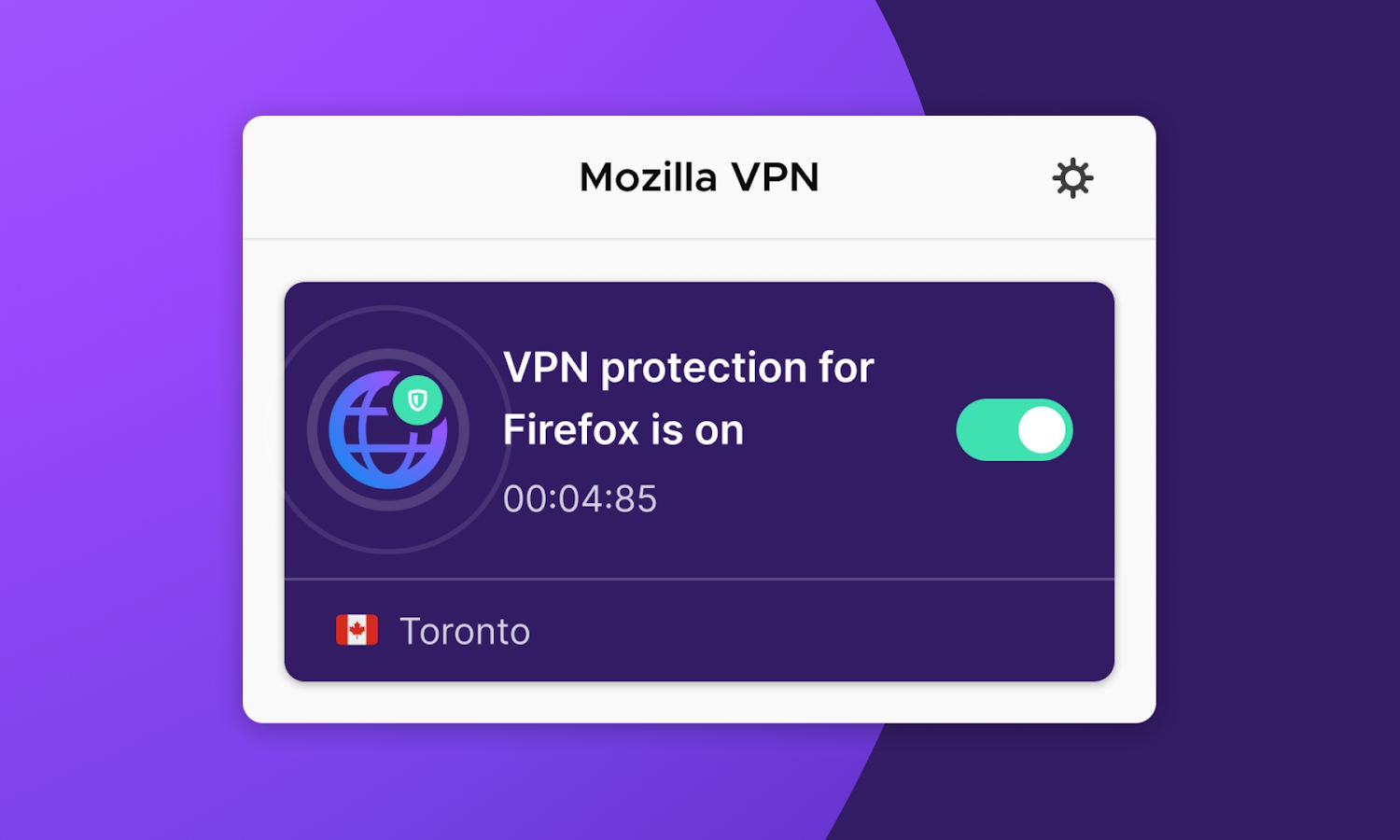
Firefox users have easy access to a powerful and customizable VPN with the Mozilla VPN extension
Mozilla is pushing its new VPN extension for Firefox as a way of simplifying the often confusing world of VPNs. Whether users are turning to a VPN for security, privacy, or to access content that’s only available in other countries, the Mozilla VPN extension is touted as a hassle-free option.
At the moment, the extension is only available for users of Firefox on Windows, but there are plans to release versions for Linux and macOS as well. Product manager for Mozilla VPN, Santiago Andrigo, explains what makes this VPN tool stand out from the crowd.
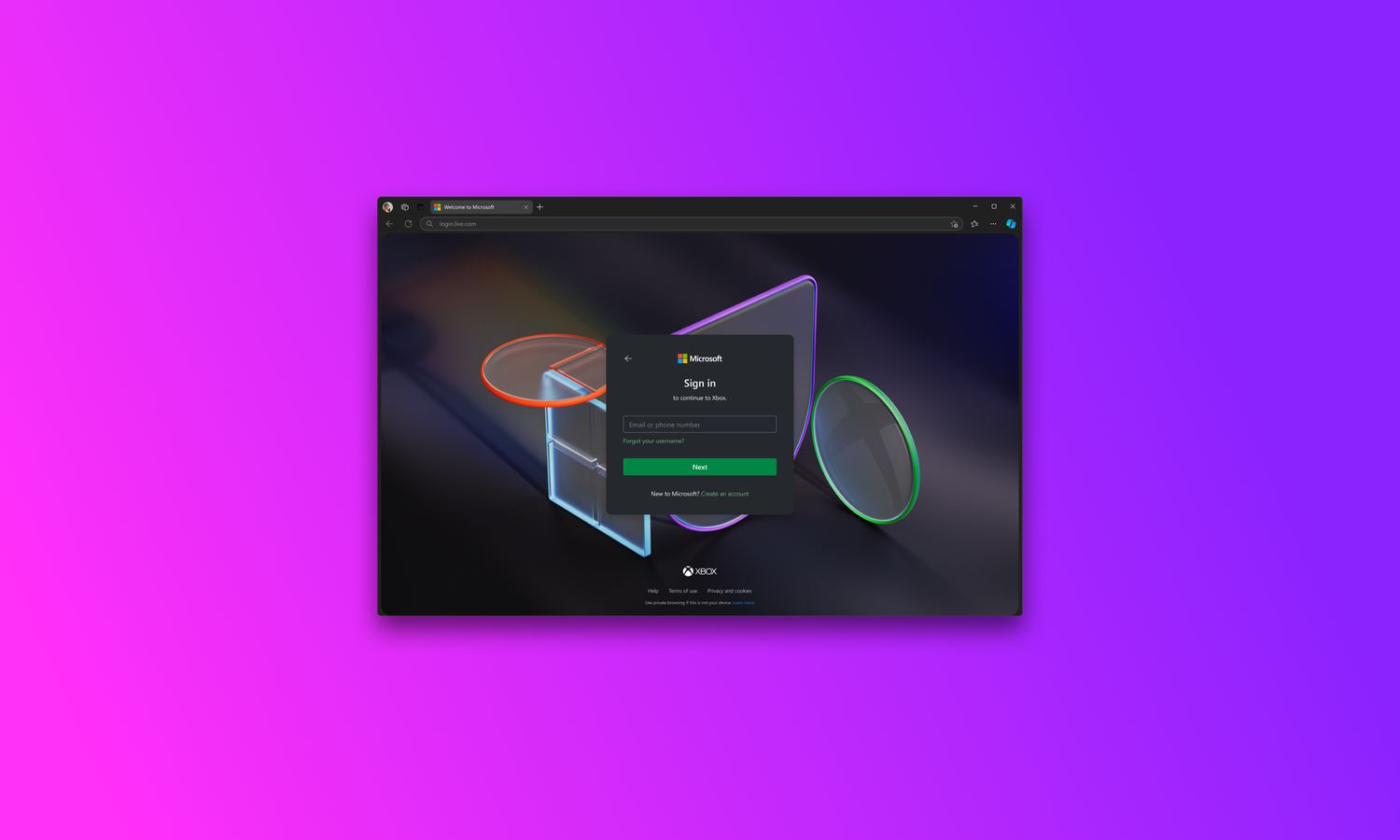
Microsoft accounts now have a sleek new sign in experience with a dark mode option
The next time you sign into your Microsoft account you may well be greeted by a new look. Microsoft has started the roll out of what it is calling a “new sign in experience” as the company uses its Fluent 2 design language to revamp the UI and UX. For better or worse, this is an attempt to create an “unmistakably Microsoft” look and feel.
The changes affect users of Windows, Xbox, Microsoft 365, and more, and Microsoft predicts that the majority of users will see the new look by the end of April. As part of the redesign, users are being given more choice; there is now a dark mode option.
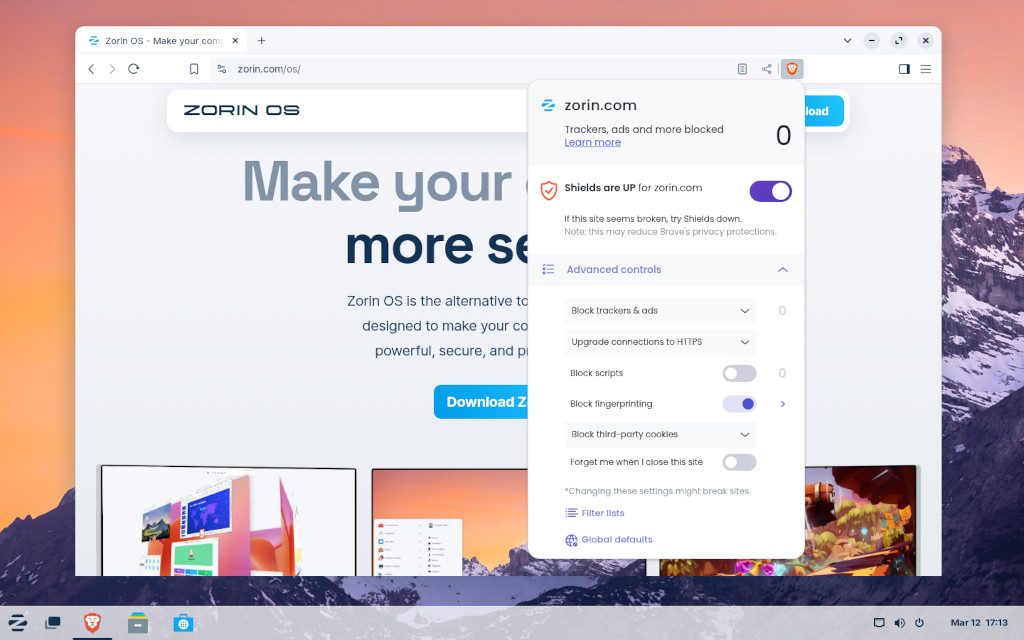
Zorin OS 17.3 brings Brave browser and better app support as perfect Windows 10 replacement
It’s time to celebrate, fellow Linux fans. Zorin OS 17.3 is officially available, and it couldn’t have come at a better time. With Microsoft ending support for Windows 10 in October, millions of perfectly good PCs are about to be left in the dust. If your computer doesn’t meet Windows 11’s ridiculous hardware requirements, don’t toss it in the trash just yet. Zorin OS 17.3 wants to give it a second chance.
This Linux-based operating system is built with simplicity, speed, and security in mind. It’s especially appealing to folks who are fed up with Microsoft but still want something familiar. With version 17.3, Zorin OS is doubling down on helping Windows users feel right at home, while also embracing the power and freedom of Linux.

Get 'The Ultimate Linux Shell Scripting Guide' for FREE and save $35.99!
If you’re comfortable using the command line on Unix or Linux but haven’t fully explored Bash, this book is for you. It’s designed for programmers familiar with languages like Python, JavaScript, or PHP who want to make the most of shell scripting.
This isn’t just another theory-heavy book -- you’ll learn by doing. Each chapter builds on the last, taking you from shell basics to writing practical scripts that solve real-world problems. With nearly a hundred interactive labs, you’ll gain hands-on experience in automation, system administration, and troubleshooting.

IT teams, don't fall behind the AI curve
In the new age of AI, companies are looking for ways to integrate the groundbreaking technology cross-functionally to enhance efficiency, innovation and inform decision-making. Like any business department, IT teams are eager to learn how AI and automation can help alleviate more of the menial and burdensome tasks that consume large portions of their workday.
IT professionals are overworked, burnt out and feeling increasing pressure to do more with less. According to a recent survey of IT professionals, 78 percent reported that work stressors are preventing them from upskilling, and 44 percent said their workload is outweighing their ability to be productive. AI and automation can significantly help alleviate these burdens, but they must be implemented strategically and securely.

5 reasons customers are choosing a cybersecurity platform over point products
Cyber-attacks are becoming increasingly sophisticated and targeted, with the average number of weekly attacks per organization soaring to 1,673 in 2024 -- a 44 percent increase from 2023. In response, researchers and defenders are harnessing AI-powered analytics, anomaly detection and correlation engines to bolster security efforts. It’s an ongoing cat-and-mouse game that makes cyber compromise a question of when rather than if.
Effective defense hinges on resilience and minimizing the attack surface. However, many businesses are finding that traditional point-based solutions are leaving them with gaps in their security posture due to limited tools, skills or resources. There are five key factors that are leading organizations to look for a more sustainable and comprehensive platform-based approach.

Cloud collaboration platforms exploited in phishing attacks
Popular cloud collaboration and file sharing platforms like Adobe, DocuSign, Dropbox, Canva, and Zoho are being misused in phishing attacks due to their widespread adoption by businesses and individuals.
Research by Cofense finds 8.8 percent of all credential phishing campaigns in 2024 used these websites. Among campaigns exploiting these online document sites 79 percent of all cases containing the domains were credential phishing attacks.

Medical devices vulnerable to exploits and insecure connections
A new report from Claroty finds that 89 percent of healthcare organizations have medical devices vulnerable to ransomware-linked exploits and insecure internet connectivity.
Based on analysis of more than 2.25 million Internet of Medical Things (IoMT) devices and 647,000-plus OT devices across 351 healthcare organizations, the report finds 99 percent have at least one known exploited vulnerability (KEV) in their networks, while 78 percent of hospitals have OT devices with KEVs, including building management systems, power supplies, and temperature controls.

Bitcoin: Volatile or maturing? Why 2025's price swings might signal market evolution, not instability
The dramatic price changes of Bitcoin remain visible in the headlines during early 2025. Bitcoin experiences an upward trend after substantial institutional inflows while falling due to international regulatory news or global macroeconomic conditions.
Price volatility in the Bitcoin market leads traditional investors to perceive the cryptocurrency as a dangerous, unstable asset category. These fluctuations in price represent an emerging market that integrates into the fundamental structure of worldwide financial systems. For instance, Bitcoin price volatility operates as an essential element of an evolving asset class, which shows enhanced sensitivity to worldwide events and internal changes in the market.

0patch releases yet another free fix for yet another 0day vulnerability in Windows that Microsoft has not addressed
Security issues in Windows crop up with scary frequency, and most are fixed by Microsoft… eventually. But while the tech giant works out how to patch holes in its buggy operating system, there are -- thankfully -- others who are willing to do the fixing faster.
0patch is a familiar name. It is a firm that, on a subscription basis, provides support and security fixes for versions of Windows that Microsoft has abandoned. It also frequently releases free patches for security issues that Microsoft is yet to fix, and this has just happened again with a fix for a worrying SCF File NTLM hash disclosure 0day vulnerability.

Deepfakes and how to deal with them [Q&A]
With deepfakes getting more sophisticated and harder to detect both organizations and individuals are at risk of falling victim to fraud and phishing attempts.
We spoke to SURF Security CTO, Ziv Yankovitz, to learn more about the increasing threat of deepfakes and best practices that can be used to for combat attacks.

Ready or not, Microsoft is testing early builds of Windows 11 25H2 on users
No operating system is ever really finished, and this is certainly true of Windows 11. As well as the (very welcome) security fixes, Microsoft continues to make endless tweaks, changes and additions to the OS; now the company has just moved to the next big stage of development.
It may seem as though the most recent major update, Windows 11 24H2, has only just been released, but the company is already working away on Windows 11 25H2. What’s more, it’s available to try right now.

Forget Windows 11 and try AerynOS instead -- this new Linux distro just got a fresh ISO and powerful updates
The folks behind Serpent OS have completed their rebrand, and the result is something you must check out. Now called “AerynOS,” this Linux distribution just dropped a new ISO (AerynOS 2025.03) and it might soon be time to forget all about Windows 11. Seriously.
This isn’t some clunky science project or a quirky Linux offshoot that breaks every other week. AerynOS is shaping up to be a serious daily driver.
