
Windows' market share declined 17 percent in the past 10 years
These days you no longer need to stick with Microsoft's Windows operating system if you don't want to. There are some excellent Linux distributions you can run instead, like Ubuntu or Linux Lite, or macOS if you opt to switch to Apple hardware. You can even use iPads or Android tablets as laptop alternatives if you prefer.
In 2013, Microsoft Windows accounted for over 90 percent of the total desktop operating system market, but that figure has dropped significantly in the past decade in the face of increased competition.

Deepfakes and crypto scams are on the rise
The first quarter of 2022 has seen a rise in cybercriminals deceiving victims through new deepfakes and crypto scams to gain access to their financial or personal information.
The latest quarterly Consumer Cyber Safety Pulse Report from Norton Labs reveals deepfakes -- computer-generated images and videos -- are on the rise and being utilized by bad actors to spread disinformation.

2022 Call for Code Global Challenge aims to get developers focused on green solutions
Supported by IBM, The Linux Foundation and the UNHCHR, the 2022 Call for Code Global Challenge wants to bring together developers and problem solvers to use open innovation to help accelerate sustainability and combat climate change.
Now in its fifth year, Call for Code has galvanized a community of more than a half million developers, students, and problem solvers from 180 nations to design cutting-edge open source-powered hybrid cloud and AI solutions that can tackle some of the world's most pressing issues.

IT leaders think security is lagging behind current threats
New research from Vectra AI reveals that 74 percent of respondents experienced a significant cybersecurity event in the past year.
The study surveyed 1,800 global IT security decision-makers at companies with over 1,000 employees and finds that 92 percent of respondents say that they had felt increased pressure to keep their organization safe from cyberattacks over the past year.
What's needed to improve trust in AI?
Digital technology company, Kainos, along with award-winning slow news organization, Tortoise, has produced a report looking at how business leaders should respond to challenges around trust in AI.
Through interviews with twenty international AI experts -- from companies including Accenture, The Alan Turing Institute, and UNESCO -- the report identifies three guiding principles to improve trust in AI.

Zoom is slashing the length of free 1-on-1 meetings from May
Zoom is a service that huge numbers of businesses and individuals have come to rely on during the COVID pandemic and associated lockdowns. For people working on a one-to-one basis -- such as therapists and coaches -- the fact that free meetings involving two participants were not subject to the same limitations as larger meetings is a major bonus. But this is about to change.
At the moment, if you want to use Zoom for free, there is a 40-minute limit on meetings involving three or more participants. Free one-on-one sessions have a 30-hour limit. The company has been busy emailing free users advising them that the 40-minute limit will also apply to free meetings with two participants. The result? As well as confusion and annoyance, people are now seeking out free Zoom alternatives.

Musk takeover of Twitter sparks heated debate
News that Elon Musk has succeeded in his bid to buy Twitter has, as you might expect, triggered a range of reaction. From rejoicing in some quarters to wailing and gnashing of teeth in others.
The debate rages on the platform itself as well as in the wider media. We've put together a range of views.

Microsoft releases KB5012643 update for Windows 11 to fix app button problems and more
Microsoft has released a big new update for Windows 11 that addresses a number of issues with the operating system. Key changes included in this update include fixes for various problems with video subtitles.
With the KB5012643 update, Microsoft has also introduced a change that means the temperature is now displayed on top of the weather icon on the taskbar. Other features of the update include improvements for servicing the Secure Boot, and a fix for a memory leak.

Confirmed: Elon Musk to acquire Twitter for $44 billion
We reported earlier today that Tesla and SpaceX tycoon Elon Musk looked poised to snap up Twitter, and now we have official confirmation that Twitter’s board has indeed agreed to the takeover.
The social network has entered into a definitive agreement to be acquired by an entity wholly owned by Musk for $54.20 per share in cash, with a transaction value of approximately $44 billion.
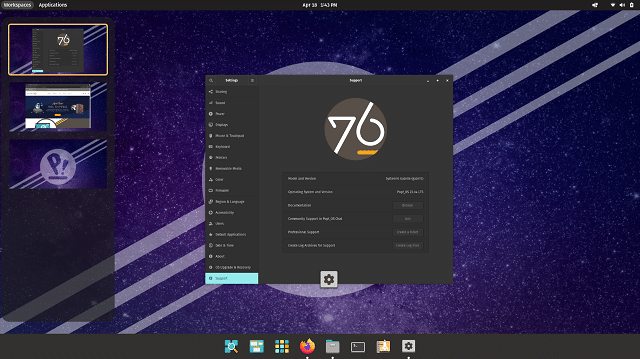
System76 takes Ubuntu Linux to the next level with Pop!_OS 22.04 LTS
Ubuntu is a great operating system -- and so are the many Linux distributions that are based on it. Quite frankly, you really can't go wrong by choosing any Ubuntu-based distro. With that said, there is one Ubuntu-based operating system in particular that really takes things to another level -- Pop!_OS by System76.
System76's operating system focuses more on the user experience, making it a superior desktop distribution compared to "regular" Ubuntu. Following the release of Ubuntu 22.04, today, Pop!_OS 22.04 becomes available as well, and yes, you should be excited. The distribution uses Linux kernel 5.16.19, Mesa 22, and the GNOME 42 desktop environment (with System76's COSMIC UX enhancements).

KB5012599 update is causing 0x8024200B and 0x800F0831 errors for some Windows 10 users
Earlier in the month, Microsoft released the KB5012599 update for various versions of Windows 10. The update fixed various issues including a Denial of Service vulnerability on Cluster Shared Volumes, but the patch also introduced problems of its own.
A number of people attempting to install KB5012599 report that they are running into problems, specially 0x800F0831 and 0x8024200B errors.

Musk about to snap up Twitter for $43 billion [Updated]
We reported two weeks ago that Tesla and SpaceX tycoon Elon Musk had put in a bid to buy Twitter, though it seemed at the time that the company’s board wasn’t too keen on the idea.
Fast forward to today and it seems that Musk's $43 billion offer is likely to be accepted. Financial site Bloomberg reports that a deal is close with negotiations in their final stages.

Linux Lite 6.0 RC1 is here with Google Chrome as new default web browser
Now that Ubuntu 22.04 has been released, we will start to see updates to all the Linux distributions that are based on Canonical's operating system. For instance, the first release candidate of Linux Lite 6.0, which is based on Ubuntu 22.04, is now available. If you aren't familiar, Linux Lite is very popular with those that are switching to Linux from Microsoft Windows.
Linux Lite 6.0 RC1 is notable for ditching Mozilla Firefox as the default web browser, and switching to Google Chrome 100 instead. The operating system currently uses Linux kernel 5.15.0-25 and the desktop environment Xfce 4.16.3. It comes with some excellent software pre-installed, such as GIMP 2.10.30, Thunderbird 91.7.0, VLC 3.0.16, and LibreOffice 7.2.6.2.

SaaS and what it can teach us about human behavior [Q&A]
Software-as-a-service has become increasingly popular and the market for it is still growing -- expected to reach $264 billion (£207 billion) by 2026.
SaaS sales are being driven by more companies continuing to digitize their operations in a post-COVID-19 world. We spoke to Paul Quigley, CEO and co-founder of predictive, real-time media monitoring platform NewsWhip, to discover how using SaaS can improve operations for a company, help grow the business, and even offer insights into human behavior.

Microsoft releases KB5012636 update to fix Windows freezing and improve Secure Boot
Microsoft has released a preview of a cumulative update for Windows 10. The KB5012636 update is a non-security update that addresses a number of issues and makes various quality improvements.
Among the issues fixed by the updates are a problem with Windows Defender Application Control that caused Windows to hang, and various remote desktop related problems. The update also improves the Secure Boot component of Windows.
