
Microsoft says the rollout of Windows 11 upgrades is way ahead of schedule
When Chief Product Officer of Windows and Devices at Microsoft, Panos Panay, wrote about "a new era of the PC", he revealed some of what we can expect from Windows 11 in the future. But his blog post also shed light on just how the operating system has been received by users.
Panay reveals the impressive statistic that Windows 11 upgrades have been taken up by users at twice the rate of Windows 10 upgrades. Satisfaction levels are said to be high, and as a result Microsoft is well ahead of its mid-2022 target for the rollout of Windows 11.
Celebrate African-American history with Apple Watch Black Unity Braided Solo Loop
African-American history is American history. The USA would not exist as it is today without the contributions made by countless black people -- that is a fact. And so, every February, we all collectively celebrate Black History Month by recognizing many great Black Americans such as Harriet Tubman, George Washington Carver, and Barack Obama to name just a few.
Today, Apple announces a new product designed to let consumers show their love and respect for black people. You see, the Apple Watch Black Unity Braided Solo Loop is a beautiful new watch band that uses colors from the Pan-African flag and looks quite stylish.

The apps section of the Microsoft Store is still a dumpster fire
In a new blog post in which he discussed a number of things, including the (near) future of Windows 11, Panos Panay, Chief Product Officer, Windows + Devices talked about how the new operating system is driving 3x more traffic to the newly redesigned Microsoft Store.
"We’re energized by the feedback from both our customers and partners about the new Microsoft Store" he said. But hmm... Perhaps he needs to step out from his bubble and see what Windows customers are really saying about it.

Admins struggle to keep users safe in a post-COVID world
A new survey of 600 IT admins finds almost a third say that their biggest challenge is keeping users secure, while 67 percent say they are stuck in a daily grind of provisioning services and apps, managing user identities, dealing with employees who have ignored best IT practices, and helping onboard new staff.
The study from Remotely also finds 28 percent say ensuring the tools remote IT teams have access to are as good or better than the ones they have on site is the problem teams struggle with the most. Following closely are: remaining as productive as they were in the office, collaboration among the sysadmin / IT admin team, and tracking their own performance.

Microsoft reveals what's next for Windows 11
Let’s be honest here. Windows 11 has the makings of being a good operating system, but it’s not there yet. Some of the features that Microsoft touted in its original presentation -- such as native support for Android apps -- aren’t even available yet.
However, Microsoft today addresses what’s coming next for the new OS and you won’t have long to wait to try out the new features and functionality.

Hackers continue to target zero-day vulnerabilities
Unpatched vulnerabilities remain the most prominent attack vectors exploited by ransomware groups, according to a new report.
The study by Ivanti, produced in conjunction with Cyber Security Works, shows 65 new vulnerabilities tied to ransomware last year, representing a 29 percent growth compared to the previous year and bringing the total number of vulnerabilities associated with ransomware to 288.

Google launches Topics API to replace tracking cookies, and kills off controversial FLoC
Ever since Google first announced Federated Learning of Cohorts (FLoC), it was controversial. So hated was FLoC that the likes of WordPress said the ad-targeting technology should be seen as a security concern, and DuckDuckGo took steps to block it.
Now Google has announced that FLoC is dead. On top of this, the company has a replacement waiting in the wings -- Topics API for Privacy Sandbox. The feedback from the trials of FLoC have proved instrumental in the development of Topics and its delivery of interest-based ads.

Through a glass darkly: Nike sues Lululemon over mirror
In my bio below you'll see a picture of me sporting my new digital camouflage Lululemon Surge Warm Half-Zip that had arrived the night before writing this. Inside the box was a card trying to sell me something called Lululemon Mirror. The image on the card was very similar to what Lululemon has on their site (see image at the top).
My first reaction was "This looks like something Nike would make. I wonder if it'll claim to own the IP rights."

Over three-quarters of container images have high risk vulnerabilities
A new report from container and cloud security company Sysdig finds that 75 percent of images contain patchable vulnerabilities of 'high' or 'critical' severity. In addition 85 percent of container images that run in production contain at least one patchable vulnerability.
Looking at the issues in more detail, 73 percent of cloud accounts contain exposed S3 buckets and 36 percent of all existing S3 buckets are open to public access.

Every major Linux distro has a PwnKit flaw that is easily exploited to gain root access
Linux-based operating systems are frequently touted as being far more secure than the likes of Windows or macOS. More secure they may be, but they are not completely infallible.
A great example of this is the recently discovered PwnKit vulnerability in the pkexec component of Polkit. The flaw can be exploited to gain root access to a system and it has been a security hole in pretty much all major Linux distros for over 12 years, including Debian, Fedora and Ubuntu.

Microsoft releases KB5009596 update for Windows 10 with new Sync Your Settings feature to simplify Windows 11 upgrades
Having released a preview of next month's updates for Windows 11, Microsoft has also done the same for Windows 10. With the release of KB5009596, the company has addressed an issue that prevented the Windows Subsystem for Linux 2 (WSL2) localhost relay from starting, as well as fixing a couple of audio problems.
This particular update also sees the addition of a reminder to Internet Explorer 11 users about the browser’s upcoming retirement. One of the more interesting additions that comes with the KB5009596 update is the new feature called Sync Your Settings which has been designed to make it easier to migrate to Windows 11.

Pathetic and predatory? Has Microsoft tried to use Windows 11 updates to sneakily switch people to Edge and Bing?
Microsoft is not exactly a stranger to -- how can we put this gently? -- slightly underhand tactics. And if complaints about recent updates for Windows 11 are anything to go by, this is not something that's changing any time soon.
According to reports, automatic updates for Windows 11 have been used to not only deliver security fixes, but also to change people's default web browser to Microsoft Edge. Some are also complaining that Bing.com loads every time Windows starts up. The behavior has led some to accuse Microsoft of being "very sneaky".

Microsoft releases KB5008353 update to fix audio and taskbar problems in Windows 11
We are coming to the end of the month and that means it is time for Microsoft to unleash the preview versions of the Windows updates that will be released on Patch Tuesday. As such, the company has released the KB5008353 update preview for Windows 11, addressing dozens of issues.
The list of changes, fixes and improvements included in this optional, non-security update is fairly lengthy, but there are some definite highlights. Among the most significant changes are fixes for problems with Bluetooth audio, as well as fixes for issues with Windows 11's taskbar that caused app icons to appear unnecessarily.
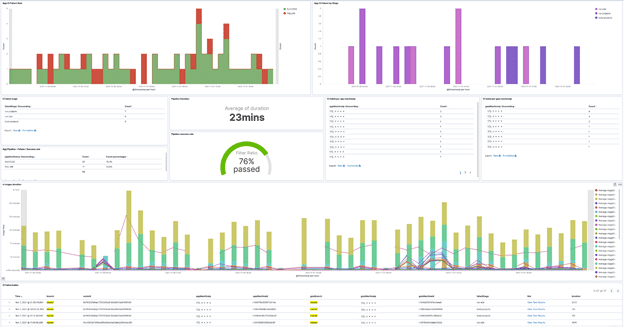
Overcoming observability challenges in the CI/CD Pipeline
When most companies monitor and analyze their software systems, they focus on the most obvious ones. But one essential service often slips through the cracks: the continuous integration/continuous delivery (CI/CD) pipeline. This poses three main observability challenges: pipeline investigation efficiency, pipeline performance, and the ability to access historical data.
Every time developers push out a new version, their pipeline run is triggered. A set of commands checks to make sure everything is valid, that the build process is all right, and that all tests have been passed. If everything checks out, the new service version is deployed to production.

Logitech G413 SE is an affordable mechanical keyboard for PC gamers
Should all PC gamers own a mechanical keyboard? No, not all of them. If they take their video games seriously, however, and they are focused on winning their competitive matches, such a keyboard can be a wise investment. These days, a quality mechanical offering can be had for under a hundred dollars, making it a no-brainer.
Today, Logitech announces its latest mechanical keyboard. Called "G413 SE," it will be offered in two variants -- a standard model with a number pad, and a tenkeyless (TKL) version without one. What I really love about this keyboard -- besides its affordable pricing -- is its subtle design. There is no wacky RGB lighting, instead using classy white backlighting. There are no gimmicks or nonsense either -- just a quality keyboard from a well-respected manufacturer.
