
A minute is a long time on the internet
Former British prime minister Harold Wilson famously once said, "A week is a long time in politics." Of course in the age of the internet things move faster still.
Research from advertising company N.Rich shows that in the online world an awful lot happens in just one minute.

Why data quality is essential to business success [Q&A]
Enterprises are increasingly reliant on data, but it's only really useful if its quality can be assured. With growing volumes though maintaining data quality and compliance is a big challenge.
We spoke to Rex Ahlstrom, chief strategy and technology officer at Syniti to find out how businesses can improve and maintain the quality of their data and how this can benefit them.
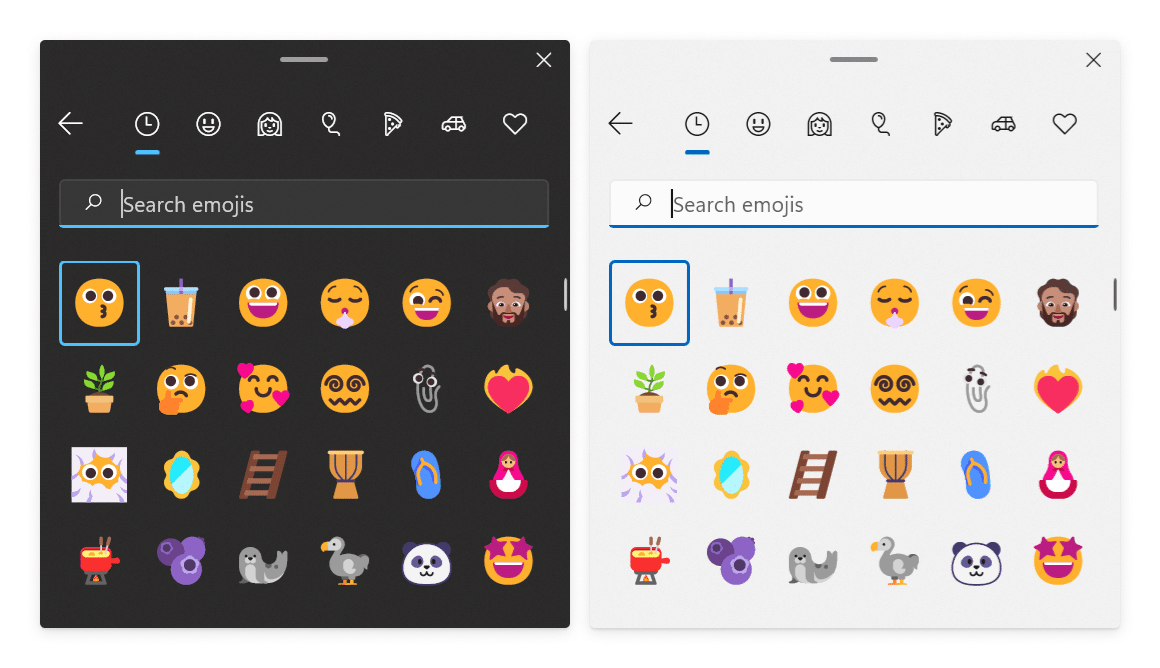
Microsoft releases Windows 11 Build 22478 with new Fluent-emoji
Microsoft rolled out the first update for Windows 11 earlier this week. Continuing the trend we saw with its Windows 10 patches, this one was designed to fix problems, but introduced new ones.
The company is hard at work on adding new features and improvements to its latest OS, and today releases Windows 11 Build 22478 to Insiders in the Dev Channel.

KLEVV unveils R1 and S1 USB-C SSDs
Solid state drives make wonderful internal boot drives for computers, but they are also great options for external storage too. Not only are they smaller than mechanical hard disk drives, but they use less power and are much quicker as well. Quite frankly, if you are someone that needs to transport data on a portable drive, you'd be crazy to still use HDD in 2021.
Today, KLEVV announces a pair of external solid state drives. Called "R1" and "S1," both drives connect using USB-C, but they can interface with USB-A ports too. While both SSDs are very fast, the S1 is faster than the R1. The former uses USB 3.2 Gen 2x2, while the latter relies on the slower USB 3.2 Gen 2.

How multi-cloud application delivery is impacting ecommerce providers as they prepare for major growth
Ecommerce continues to be one of the most fast-paced and competitive global industries, with industry-watchers estimating that online sales will constitute a fifth of all retail sales worldwide by the end of 2022. As vendors strive to capture their share of market growth, they need to offer exceptional customer experiences that build loyalty and repeat revenue. However, delivering omnichannel excellence puts considerable pressure on infrastructure as site traffic increases and consumer expectations rise.
At the same time, the sector is heavily targeted by cybercriminals seeking to disrupt, extort and damage online retail businesses. Consequently, striking a balance between operational efficiency, cost-control, security and customer satisfaction is a complex challenge.

Microsoft is shutting down LinkedIn… in China
Microsoft launched a Chinese version of LinkedIn in 2014, having weighed up the pros and cons of operating under the scrutiny -- and restrictions -- of the Chinese government.
Today, the software giant announces it is pulling the plug on LinkedIn there, citing a lack of success with the social aspects of the site, and the difficulties it faced with complying with the government’s many demands. Microsoft isn’t pulling out of China's blossoming business market entirely though -- rather it’s changing its focus.

Tech industry has become more inclusive but women still face barriers
The past decade has seen a concerted effort to improve opportunities for women in the technology sector, and 80 percent of female and 89 percent of male respondents to a new survey believe that it's now more welcoming.
However, a report out today from consulting company NTT DATA UK shows that 74 percent of women say they have had a negative experience at work because of their gender.

Enterprise asset management not keeping pace with pandemic changes
A new report from IT management specialist Flexera looks at how organizations have adapted their technology to meet the demands imposed by the pandemic.
It reveals information technology asset management (ITAM) trends relating to responsibilities and challenges introduced by the increased use of new IT environments such as software-as-a-service (SaaS), cloud and containers.

Hackers exploit zero day before enterprises can patch
Cybercriminals exploited the new CVE-2021-40444 remote code execution zero-day a week before the patch was issued on September 14, according to the latest report from HP Wolf Security.
Researchers also saw scripts that automated the creation of the exploit on Github on the 10th, making it easier for less-sophisticated attackers to use the exploit against vulnerable organisations.

Download Ubuntu Linux 21.10 Impish Indri
Is Ubuntu the best Linux-based operating system? That is a matter of opinion, but I would say no. While it is a great OS, there are other distributions that are arguably better. Is Ubuntu the most popular Linux distro? Not likely. These days, it isn't even in top five on DistroWatch.
With all of that said, new Ubuntu releases still seem to generate the most excitement in the Linux community. This is partly due to Ubuntu's name recognition, but also, there are many great distributions based on Ubuntu, such as Linux Mint, Pop!_OS, and elementary OS to name a few. Let us not forget the excellent official flavors of Ubuntu, such as the KDE Plasma-focused Kubuntu.

Be part of a cybersecurity world record attempt
It's Cybersecurity Awareness Month and also Serious Security Week. To mark these events, cybersecurity companies KnowBe4 and OneLogin are partnering with Security Serious in a bid to set a brand new Guinness World Record for the most views of a cyber security lesson video on YouTube in 24 hours.
The record attempt will take place starting today, October 14th at 11am EDT, (8am PDT, 4pm BST) and will see KnowBe4 and OneLogin provide a 45-minute training session that will be live-streamed via YouTube.

Boston Dynamics takes its dogs for a walk in DC
If you have a dog then you’ve likely been there with the 3AM trips outside regardless of weather -- rain, snow, bone-chilling cold. If the hound needs to go, you're going out -- after all, you don’t want the alternative.
There are other fun times, teething for instance. My current black lab cost me two pillows, a house plant and a vacuum cleaner cord. There’s food that needs to be kept out of reach... a lab can easily reach a kitchen counter, I learned early on.
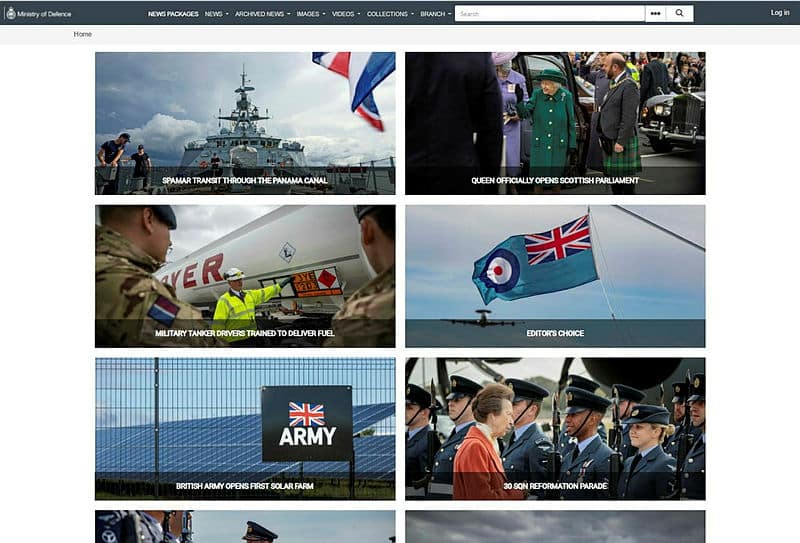
Defence Imagery is a new public image archive from the UK's Ministry of Defence
If you’re looking for military images and videos, there’s a new resource which offers over 5,000 videos and 10,000 images from the UK’s Ministry of Defence (MOD).
Created in conjunction with Norwegian software provider FotoWare, the new Defence Imagery site complies with the strict requirements laid out by the UK Government and makes it clear what you can and can't do with any content you download.

Industry leaders comment on Cybersecurity Awareness Month
Most things have a day or a week or a month nowadays, and as you're reading a tech news site it probably hasn't escaped your attention that October is Cybersecurity Awareness Month.
But just in case you missed it in all of the Windows 11 excitement, here's a round up of what some leading industry figures have to say on cybersecurity, and why we need to be aware of it.

Get 'Mastering Python for Networking and Security -- Second Edition' ($27.99 value) FREE for a limited time
It’s now more apparent than ever that security is a critical aspect of IT infrastructure, and that devastating data breaches can occur from simple network line hacks.
As shown in this book, combining the latest version of Python with an increased focus on network security can help you to level up your defenses against cyber attacks and cyber threats.
