
Quickly find Unicode symbols with SymbSearch
Need to enter a Unicode symbol on your PC? Then launch the Character Map, find what you need to the clipboard and copy it to the clipboard. Sounds easy, right? Until you try it.
The reality is the Character Map gives you hundreds of characters to examine, organised in a way which doesn’t always match their purpose, and displayed in such a small font that you’ll barely be able to see some of them at all.
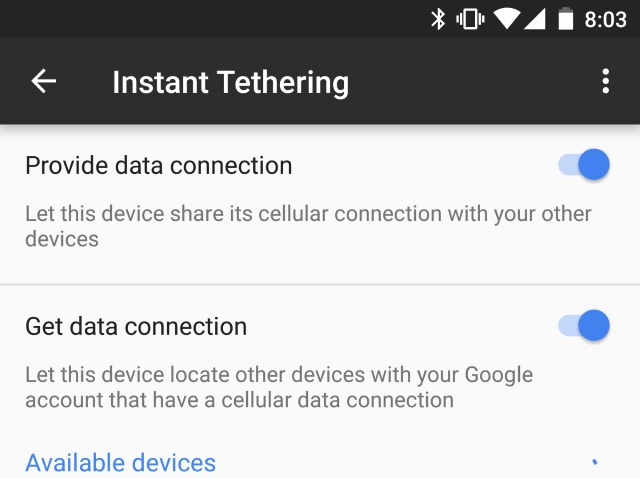
Simplified connection sharing comes to Android with Instant Tethering
Take your phone with you wherever you go, and you can use it to get your laptop online thanks to the wonder of tethering. This seemingly simple technological marvel is a delight for people working away from the home or office, and Google is now making things easier than ever with Instant Tethering.
The new feature is rolling out to some Android devices now, and it takes the 'hard work' out of creating a hotspot with your phone to which your other devices can connect. As the name suggests, the aim is to make the connection instantly.

What's the best Linux distro for you?
When it comes to desktop operating systems, there are three main camps into which people fall: Windows, Mac and Linux. In the case of the latter camp things can be confusing because there are endless distros to choose from -- but which is best?
The beauty of Linux is that it can be tweaked and tailored in so many ways. This means that while the plethora of choice can seem overwhelming, it is also possible to find the perfect distro for just about any scenario. To help you make the right choice, here's a helpful list of the best distros to look out for in 2017.

Tips for adopting a DevOps approach
Today businesses are working in more agile and digitally connected ways. What’s more in the case of new software development projects, DevOps is a buzzword that chimes with this sentiment. But what does it mean and how should we view it? Is it a job role? Is it a team? A product? A vision?
Quite simply, DevOps is a mind-set. When companies choose to expand development across the organization they are driving collaboration. This adds powerful value back to enterprise leaders, who have the interests of the customer at heart. What makes it a mind-set is that its success depends on a combination of people and behavior changes.

How to set up a manual threat intelligence lifecycle program
Threat intelligence is a popular topic in security circles these days. Many organizations are now using a threat feed that comes bundled with some other security product, such as McAfee’s GTI or IBM’s X-Force feeds. Lots of products, notably SIEMs, have added support for some sort of integration with specific threat intelligence feeds or more generic imports via STIX/TAXII. With many now hoping to take advantage of the large number of open source and free intelligence feeds available. Some are even investing in commercial intelligence feeds.
However, as many organizations quickly discover, without effective management of the threat intelligence lifecycle, making effective use of this valuable information is nearly impossible. Today, an organization has two choices for managing threat intelligence, these are to deploy a threat intelligence management platform, or a manual in-house management program. The steps required to set up a manual threat intelligence lifecycle program will be outlined below for those who prefer this approach.

Santa brought you an iPhone 7? Here's what to do first
Despite planning to stick with my iPhone 6s for another year, I ended up upgrading to the iPhone 7, and I’m pleased that I did. If you were lucky enough to get an iPhone 7 for Christmas, or an iPhone 7 Plus for that matter, you’re no doubt going to be as happy with the latest Apple smartphone as I am.
Getting started is straightforward, as once the phone is turned on you’ll be walked through the set up process, how to configure the Touch ID fingerprint scanner, and set up a PIN. Once you've set up the basics, it's time to explore what you can do with your new device.

Santa brought you a Samsung Galaxy S7 or Galaxy S7 edge? Here's what to do first
If Santa brought you a Galaxy S7 or Galaxy S7 edge, you are in for a treat. Samsung's flagships are, without question, two of the best high-end smartphones available right now, featuring an amazing camera, a gorgeous display, fantastic performance, impressive battery life, powerful software, a waterproof rating, and a premium design. Impressive, indeed.
To help you get comfortable with your new Galaxy S7 or Galaxy S7 edge, we have prepared this guide with tips on how to get started, set it up and what accessories to buy. So, without further ado, here is what you need to know.

Santa brought you a OnePlus 3T? Here's what to do first
Consider yourself extremely lucky: Santa just brought you one of the hottest smartphones of the year. The OnePlus 3T is the latest and greatest in OnePlus' line of flagship killers, packing really powerful hardware, a nice, big screen, solid camera, lovely software and a sleek design. It is also terrific value for money, but, hey, who cares about that right now?
If you are like me, all you can think about is taking it out of the box, setting it up and starting to use it right away. Here is what you need to know.

Santa brought you an Apple Watch (first or second gen)? Here's what to do first
If you were lucky enough to receive an Apple Watch as a present this year, you’ll no doubt be keen to see what it offers, and what you can do with it.
To start you’ll need to pair it with an iPhone 5 or later, running the latest version of iOS. To do this, go to Settings > Bluetooth on your phone and make sure the feature is enabled.

Santa brought you an Amazon Fire TV with 4K Ultra HD? Here's what to do first
The Grand Tour, The Man in the High Castle, Transparent… just three good reasons why you might have opted for Amazon’s powerful, yet diminutive TV box. Plus of course, it’s also the gateway to loads more TV, movies, apps and games.
If you have a 4K TV, it’s great source of UHD content (Amazon’s original shows are available in that format) -- although you may want to skip paying $25.99 to watch a scaled-up Groundhog Day! Once you’ve excitedly opened the gift of a new Amazon Fire TV, here’s what to do next.

What does it take to be a successful bug hunter?
Hackers are having a moment. As high-profile breaches have become the norm over the last few years, more and more enterprise organizations have turned to bug bounty programs. As a result, the idea of hacking for good has finally begun to resonate with the general public. This rise in popularity has inspired many, from aspiring hackers to seasoned security professionals, to join the hunt and seek out bug bounty programs to "hack on".
As an information security professional by trade and a hacker by heart, I’ve had years of experience hacking for good. From my days as a penetration tester and security leadership roles at HP Fortify, Redspin and Citrix to hacking on bug bounty programs of all sizes, I have spent my life hacking for good -- much of this experience has been hacking on bug bounty programs.
How to install Windows 10 Creators Update Build 14986 on Oracle VirtualBox
Microsoft has released ISO image files for Windows 10 Build 14986, giving anyone a chance to try out the forthcoming Creators Update.
While you can install it on a PC, it’s not wise to have it as your daily driver. One of the best ways of trying it out risk free, is to run it in a virtualized environment, using VirtualBox.

How to protect your business against data breaches
According to the Crime Survey for England and Wales published this October by the UK's Office for National Statistics (ONS), the official crime rate all but doubled in the year ending June 2016 after the inclusion of online crime figures for the very first time. In fact, card fraud was cited as the most common crime in the UK. John Flatley, head of crime statistics and analysis at the ONS, stated that members of the public are now 20 times more likely to be a victim of fraud than of robbery.
The Numbers Are Soaring!

How to not get hacked
We found out last week that one billion Yahoo accounts were hacked in 2013, only a couple months after we learned about a separate hack, that took place in 2014, which compromised an additional 500 million accounts. Combine that with the 360 million compromised MySpace passwords, 117 million from LinkedIn, 65 million from Tumblr, and 32 million from Twitter, and you can almost guarantee that you or someone you know was affected by the mega-breaches announced in recent months.
Being as most people use the same password over and over, these breaches give hackers access to multiple accounts. In a proactive security screen this fall, Netflix found a number of users whose Netflix passwords were compromised as part of another company’s breach. These instances do not simply let attackers tweet on your behalf; they can affect all of your accounts. How many people use the same password for LinkedIn or Yahoo as they do for their corporate email? An unsettling number.

Fool Windows 10 into disabling automatic updates
Microsoft made Windows 10 updates mandatory in order to make sure all users are always on the latest version of the new OS, but if you’d rather choose if and when updates are installed -- perhaps to avoid falling foul of problem ones -- there are several options available to you.
We’ve previously looked at ways you can disable the update mechanism in Windows 10, including using the Windows 10 Updater Disabler, but Windows 10 Update Switch uses an interesting method to stop updates for as long as you’d like.
