
deepin Linux 25 Preview challenges Windows 11 with stunning design and security from China
deepin 25 preview is now available here, offering a glimpse into a beautifully designed and highly secure Linux-based operating system that challenges Windows 11. Developed in China, deepin demonstrates how open source software can unite global communities and deliver innovation that transcends borders. While some might be wary of software made in China, there’s no need for concern -- deepin is largely open source, transparent, and a reminder that collaboration across nations fosters progress.
It’s important to note that this is a pre-release version, and users should expect potential bugs and incomplete features. Deepin’s development team recommends the preview version for those with technical expertise and advises against using it in production environments. Beginners are encouraged to stick with the stable deepin 23 release until deepin 25 is finalized.

How much power does your AI use? Most businesses don't know
According to new research only 13 percent of businesses are monitoring their AI’s energy consumption despite escalating power demands.
The study from SambaNova Systems gathered responses from 2,012 business leaders (1,004 in Europe and 1,008 in the US) finds that 49.8 percent are concerned about the energy and efficiency challenges posed by AI.

Supply chain 'butterfly effects' what are they and how do you navigate them? [Q&A]
The world is a pretty unstable place at the moment, which can lead to problems when it comes to making decisions on whether to invest in new technologies -- particularly in the context of a rapidly changing landscape for supply chains.
We spoke to Jonathan Barrett, CEO of Kallikor, to discuss how a new generation of AI-powered digital twin technology can help businesses to anticipate changes brought about by events outside their control, and adopt efficiency-driving technologies, such as robotics and automation, with confidence.
TikTok, AliExpress, Temu and more hit with GDPR complaints over unlawful data transfers to China
Austria-based data protection and privacy advocating NGO noyb (none of your business) has filed a series of complaints against AliExpress, SHEIN, Temu, TikTok, WeChat, and Xiaomi for violating European general data protection regulation (GDPR).
The six firms stand accused of unlawfully transferring user data to China. In its complaints, noyb says that “given that China is an authoritarian surveillance state, companies can’t realistically shield EU users’ data from access by the Chinese government”.
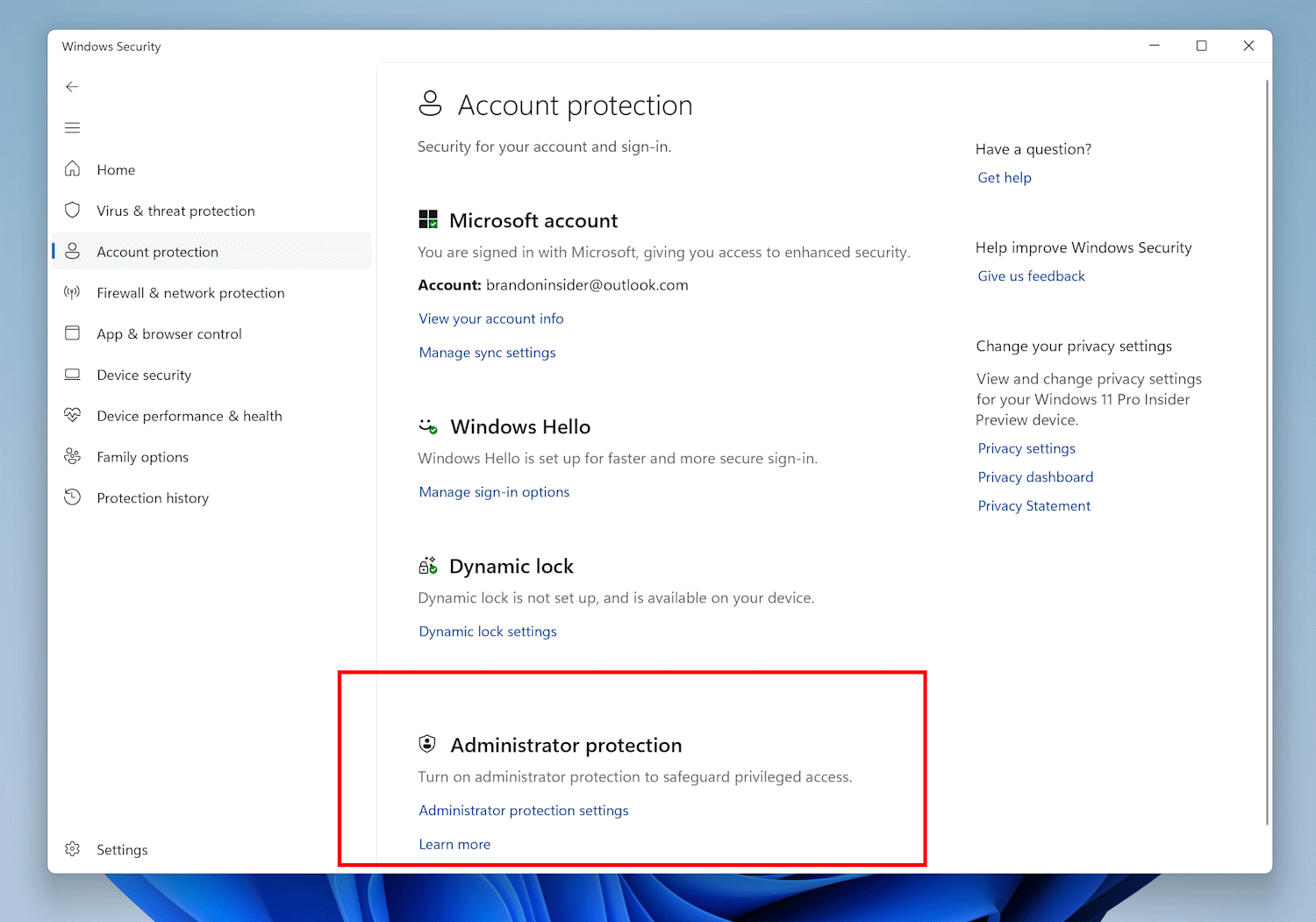
Microsoft rolls out administrator protection feature to some Windows 11 users to boost security
Microsoft has been testing a new Windows 11 security feature called “administrator protection” for a few months, and now the company has rolled it out to more users to try out.
Currently available to Windows Insiders who are beta testing preview builds of the operating system, the new security feature introduces important new protections by only assigning standard user permissions to administrator accounts. Authentication prompts appear when higher privileges are needed to complete a task.

Apple decides to disable its broken AI-powered news summaries
While Apple was excited to roll out news summaries powered by artificial intelligence, the reception has been somewhat muted because of some serious issues. The Apple Intelligence notification summaries were found to be sharing misleading or incorrect news headlines.
The BBC and other news outlets complained that their names were being used to spread misinformation, and Apple responded by promising an update to the service. For now, though, the company seems have to changed its mind, opting instead to simply disable notification summaries.

Traeger unveils Woodridge Series with app-connected grills for tech-savvy cooks
Traeger, a well-known name in wood-pellet grilling, is introducing the Woodridge Series, a new lineup of grills designed for every level of outdoor cooking enthusiast. The series includes three models -- Woodridge, Woodridge Pro, and Woodridge Elite -- each offering a range of features to make grilling more efficient and enjoyable. These new grills aim to combine convenience and innovation, bringing a touch of sizzle to backyard cooking routines. And yes, they all include smartphone app support, so you can grill smarter, not harder.
The Woodridge Series is designed to handle multiple cooking methods, including grilling, smoking, baking, roasting, and even braising. Each model features a durable, modern design and Traeger’s WiFIRE technology, which connects the grill to the Traeger App. This integration allows users to monitor temperatures, adjust settings, and access recipes remotely, making it easier to achieve consistently great results.

Nintendo Switch 2 announced but I’ll wait until homebrew is possible
Nintendo has officially announced the Nintendo Switch 2, set to launch in 2025. With promises of exclusive games, enhanced hardware, and backward compatibility with most Nintendo Switch titles, the new console is sure to attract attention. However, for some gamers, including myself, the real question is how easily the system will support homebrew development.
The original Nintendo Switch became iconic not just for its innovative design but for how quickly the homebrew community embraced it. Unlocking the system to run custom software, emulators, and other non-official programs was surprisingly easy. This ability allowed users to customize their consoles and experience gaming in a whole new way. For many, the possibility of running homebrew made the system even more appealing.

Linux Mint 22.1 Xia frees your PC from the closed-source chains of proprietary software
Linux Mint 22.1, codenamed “Xia,” is finally available, offering three desktop environments -- Cinnamon, Xfce, and MATE. This long-term support release will receive updates through 2029.
Cinnamon is the flagship desktop environment of Linux Mint and is the primary focus of this release. Version 6.4 of Cinnamon introduces a refreshed visual design, complete with darker tones, smoother rounded elements, and modernized dialogs. Wayland compatibility has also been improved, ensuring better performance and usability on newer hardware. Enhanced features include redesigned system dialogs, refined multitasking options, and the new Night Light feature, which reduces blue light exposure to improve sleep quality and reduce eyestrain.

Data privacy in 2025: The resurgence of biometric security, a fleeting forecast for federal data privacy regulations, and the return of the wild west of AI
The transition from 2024 to 2025 brings a lot of uncertainty, speculation, and hopefully some optimism for the world of data privacy.
As technology continued to innovate, securing data grew more complex and consumers grew more concerned over how their information was being used. Regulatory changes are coming soon, with several states providing their own data privacy standards in anticipation of a shifting focus within the U.S. federal government, creating an important inflection point to set the tone for the future of data privacy and security.

Nearly half of UK financial businesses not ready for a date with DORA
The EU's Digital Operational Resilience Act (DORA) comes into force tomorrow (Jan 17th) but new research shows that 43 percent of the UK's financial organizations are set to miss the deadline for compliance, with 20 percent expecting to do so by at least four months.
Although the UK is outside the EU its strong financial ties with Europe mean firms operating in or interacting with EU markets will need to align with DORA standards to continue their business relationships.

Ransomware victim numbers hit an all-time high
The number of ransomware victims reached an all-time high with more than 1,600 in Q4 2024 alone according to the latest GuidePoint Research and Intelligence Team's (GRIT) annual Ransomware and Cyber Threat Report.
The number of attackers peaked too with a 40 percent year-on-year increase in active threat groups. GRIT identified more than 88 total active threat groups in 2024, including 40 newly observed adversaries.

Optimum 10 Pro is an upgraded version of Windows 10 with next-level performance, privacy and control
When Windows 10 first launched back in 2015, it sparked a major backlash for its aggressive data collection practices. Features like default telemetry settings and forced updates left many people feeling uncomfortable with the new OS. Microsoft eventually dialed back some of the most invasive elements, but the damage was done, and some users still worry about how much control the company has over their data.
Beyond privacy concerns, Windows 10 has also faced criticism for performance issues, especially on older hardware, and for limiting user control with automatic updates and a lack of flexibility in system customization. The good news is there is a solution.

Logitech launches Rally Camera Streamline Kit for flexible learning and workplace setups
Logitech has introduced the Rally Camera Streamline Kit, a USB Pan Tilt Zoom (PTZ) video solution aimed at supporting hybrid learning environments and modern workspaces. As educational institutions and workplaces continue to adapt to changing needs, the demand for easy-to-use, reliable lecture capture technology has grown. Designed around the Rally Camera, this kit offers simple installation, preset camera controls, and compatibility with popular collaboration platforms.
According to Michele Hermann, vice president and general manager of Logitech for Education, “PTZ cameras with speaker tracking for lecture capture are often overly complex and expensive, adding unnecessary hardware to standard USB AV setups while creating unpredictable and distracting experiences.”

AVerMedia announces ELITE GO GC313Pro and CORE GO GC313 for portable charging and connectivity
AVerMedia has introduced two new devices to its GO Series lineup: the ELITE GO GC313Pro Charging Capture and CORE GO GC313 Charging Dock. These products are designed to provide users with reliable charging solutions, video capabilities, and connectivity for a wide range of devices, catering to gamers, content creators, professionals, and students.
The ELITE GO GC313Pro includes a 1080p 60FPS HDMI video capture card, making it suitable for recording and streaming high-quality content. Its compact design incorporates docking features that allow it to function as a versatile 4-in-1 USB charging hub, enabling video output, data transfer, hardware expansion, and device charging. This device supports 4K60 HDMI output, providing the ability to connect to external monitors or TVs. With compatibility for Nintendo Switch, Steam Deck, ROG Ally, MacBook Air/Pro, iPads, iPhones, and more, it offers a flexible solution for various use cases.



