
Microsoft implements a blanket ban on computer support ads on Bing
Microsoft is following in Google's footsteps and cleaning up the ads that can be displayed on its network. After Google announced that AdWords could no longer be used to push payday loans, Microsoft has decided to ban ads for computer support services from Bing.
What's interesting here is that Microsoft has taken an incredibly hard line and issued a complete blanket ban on all technical support ads -- no exceptions. The aim is to weed out fake support ads and scams, but it will also impact on legitimate services.

Barclays will introduce Android mobile payment service
UK bank Barclays has announced it will soon roll out its own contactless payment service for its Android-using customers in the country. All Barclays customers with an NFC-enabled Android smartphone will be able to pay for things the same way they pay with a contactless card.
For purchases of up to £30, all they need to do is tap their smartphone at the payment terminal, the same way they’d tap a contactless card. For purchases of up to £100, customers would need to tap in their PIN code.

Own a Raspberry Pi? You need to download this Raspbian Linux OS update -- here's what's new
No matter how great hardware is, you need software to make it have any value. After all, what good is a computer without an operating system? Who would want a powerful graphics card without drivers? A good computing experience is the successful marriage between hardware and software.
A great example of this is the Raspberry Pi. At first, the specs and diminutive size pull you in, but then you must ask, what can you do with it? You will need to install an operating system to get started, and one of the most popular is Raspbian. Today, that lightweight Linux distro gets a big update. There are some significant updates here, so trust me when I say you need to get it!
Alexa gets travel search with new Kayak integration
"Alexa, play Jeopardy". Many phrases uttered around here lately begin with "Alexa". Amazon's Echo can do an ever growing number of things from simply playing music to controlling home automation. Other tricks are always in the works from both Amazon and third-parties.
The latest "skill", as these things are called, is integration with travel giant Kayak. The company is announcing integration with all Amazon Echo devices, including Dot and Tap.
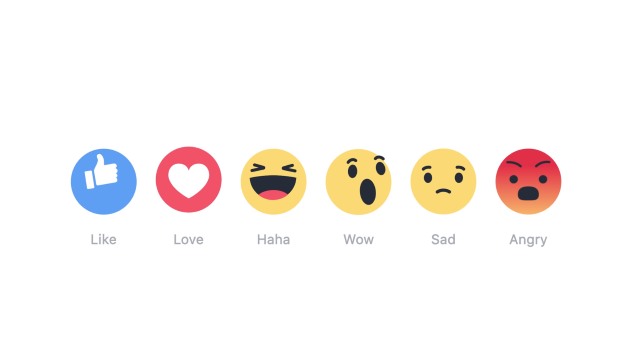
Belgian police warn that Facebook Reactions pose a serious privacy risk
Police in Belgium are warning people not to use Facebook Reactions because of the risk they pose to privacy. Introduced recently to supplement the iconic Like option, Reactions give Facebook users the chance to respond to content with Love, Haha, Wow, Sad, and Angry emoji.
But Belgian police have issued a 'Safe Browsing' warning advising that Facebook is using Reactions to gather information about social network users. Specifically, the police warn that in using Reactions to express emotions, users are giving Facebook the opportunity to build up a more detailed personal profile about them and use that information to deliver closely targeted advertising.

Windows 10 Mobile will get native fingerprint reader support
Fingerprint sensors are all the rage these days on premium smartphones. You will not find a new high-end device launching without one. Even mid-rangers and low-end handsets are starting to offer this feature. That is, as long as they are not running Windows.
Fingerprint sensors are found on Android handsets and iPhones, but not on Windows Phone or Windows 10 Mobile devices. That is, in part, because Microsoft has not implemented support for this feature in its operating system. However, that is soon about to change.

Is your hosting provider prepared for a DDoS attack?
Initially a fairly rudimental way to shut websites down, DDoS (Distributed Denial of Service) attacks have evolved into a complex and potentially catastrophic technique for cybercriminals to compromise valuable data.
With one survey of IT managers finding that the average cost of a DDoS attack was $40,000, it is imperative that businesses operating online recognize this threat and do something about it, which should start with your choice of hosting provider. One option is to switch from a shared hosting solution to a dedicated server, where your website can enjoy complete control over access and security. However, hosting providers and ISPs have a crucial part to play too.

Amazon's DSSTNE deep learning software now open source
Amazon has decided to follow in the footsteps of Google and other technology companies by open-sourcing its deep learning software.
The company has released its deep learning software DSSTNE (pronounced destiny) on GitHub under an open-source Apache license. Deep learning has gained a lot of traction in recent months and many tech companies are currently developing their own software to help teach computers.

UK ebook sales drop for the first time
It seems that our love affair with ebooks could be turning sour. For the first time since digital book sales were recorded, the number of ebooks sold in the UK dropped in 2015.
The drop could be partly explained by the fact that we seem to be reading less in recent years. While sales of printed books rose by 0.4 percent according to the Publishers Association, digital book sales declined by 1.6 percent.

IT pros too confident about detecting ongoing cyber-attacks
Endpoint detection and response company Tripwire and Dimensional Research conducted a research, and asked 763 IT professionals from various industries about their security practices, and if they felt confident they could detect an ongoing cyber-attack.
The two companies announced that the majority of IT experts felt overconfident in their abilities to detect an ongoing threat and remove an unauthorized device from their network.

Mark Zuckerberg wants to talk to conservatives about Facebook's trending news bias
After a delay of a few days, Facebook CEO Mark Zuckerberg has jumped to the defence of this social network and its handling of news. Following accusations that trending stories are manipulated to bury right wing news, Facebook has scrambled to play down suggestions of political bias -- something that will be increasingly important as the Trump and Clinton battle comes to a conclusion later in the year.
Zuckerberg felt compelled to respond to the accusations in a post on Facebook, reiterating the previous statement that there are "rigorous guidelines" in place that "do not permit the prioritization of one viewpoint over another or the suppression of political perspectives". He announced that a full investigation is to be carried out to ensure the integrity of Trending Topics, and says he'll be inviting "leading conservatives" to talk about the issue.

Best Windows apps this week
One-hundred and eighty in a series. Welcome to this week's overview of the best apps and games released for Windows 8.x and Windows 10 in the past seven days.
Starting this week, Microsoft Edge extensions are also included in the weekly series provided that they have a Windows Store listing.

Leaked documents show how Facebook manipulates trending news
Facebook has faced accusations of interfering with the headlines that appear in Trending Topics, censoring conservative stories. While admitting to a left wing bias in Silicon Valley, the social network has denied supressing the appearance of right wing news.
However, leaked internal documents show that there is a very structured and controlled process in place that sees employees -- rather than algorithms -- influencing the news that Facebook users see. The documents reveal that there is an editorial team in place, with stories being ranked and promoted by hand. Perhaps just as worrying is the revelation that a very small number of news sources are used by Facebook.

Save energy and extend battery life with Monitor Power Saver
Monitor Power Saver is a lightweight tool which can disable monitors automatically or on demand, saving energy and extending battery life. The surprisingly small download -- barely 100KB -- unzips to a single executable which runs on Windows XP or later.
Double-clicking its system tray icon displays a simple tabbed interface with various options.

Server virtualization market to reach $5.6 billion in 2016
New research from Gartner suggests that the worldwide server virtualization market is very close to reaching its peak.
In 2016, the x86 server virtualization market is expected to reach $5.6 billion. This is an increase of 5.7 percent compared to 2015. However, this growth is not attributed to new software licenses which have declined for the first time in more than a decade. Instead this increased growth has been driven by maintenance revenue which is a clear indication of how the software market has begun to rapidly mature.


