
Auslogics unveils Driver Updater
Australian utilities developer Auslogics has released Driver Updater, a commercial tool which can update all your PC drivers with a click.
If you’ve tried anything similar, the program’s core abilities won’t surprise you. Launch a scan and any outdated drivers are quickly listed, along with the dates and times of the latest version. You’re then able to update all your drivers, or just a select few.

iPhone 6 and 6 Plus set sales record, but, hey, Apple can sell 4 million of anything
Are you one of the 4 million? That's the number of iPhone and iPhone 6 Plus pre-orders during the first 24 hours, according to Apple. We don't have comparative number for iPhone 5s and 5c, as Apple gave a three-day figure of 9 million last year. But in September 2012, iPhone 5 topped 2 million the first day.
In one of the funnier Hitler parody videos, the dictator says: "If Apple sold Jony Ive's gym sweat, millions would also buy that!" (Ive is Apple's chief designer.) The point: Apple can sell millions of anything. CEO Tim Cook brags "record sales" -- and they're nothing to snicker about -- but would you expect anything less?

Comcast could cut off customers who use the Tor browser
Last week there were net neutrality protests from a number of big names in the online world. This week there is controversy courtesy of Comcast -- described by DeepDotWeb as "the most hated company in America" -- as the firm apparently declares war on Tor.
The web browser -- one favored by those concerned about their privacy -- has been branded "illegal" by Comcast according to DeepDotWeb and customer reports appearing on the /r/darknetmarkets subreddit (reddit itself having banned subreddits associated with the Fappening). Customers are reporting having been warned that use of Tor is against Comcast's term of use and could result in a termination of service.

IT professionals not confident they can prevent cyber attacks
Despite the number of high profile attacks in recent months, many organizations are still lacking confidence in their ability to prevent a cyber attack or data breach.
These are the findings of a new survey from risk consultancy firm Protiviti which also shows that companies aren't properly preparing for crises and often don’t have adequate core data policies.

Microsoft buys Minecraft, reasons are uncertain
There's no denying Minecraft is a wildly popular game that many people, both old and young, enjoy. It's also multi-platform, making it extremely profitable and available to many customers. Perhaps that's why Microsoft has announced it has purchased the franchise.
It's hard to say the motive behind this move -- the game does run on Xbox and Windows, of course -- but how does the software giant hope to recoup the money? After all, $2.5 billion is an awful lot to recover from.

Moto G (2014): The same, but different [Review]
What's in a name? A smartphone by any other name would still make calls and texts, right? Not according to Motorola it won't. The Moto G was Motorola's best-selling phone to date, despite its budget status. So in a not-so-subtle attempt to recreate that handsets' success, what has Motorola called its successor? The Moto G of course.
No "Moto G 2" or "Moto G+" or "Moto G 2nd generation" moniker here, the 2014 edition of the Moto G has swanned in as an out-and-out replacement of its older brother that boasts some seriously upgraded specs.

The life of Steve Jobs, in an infographic
Walter Isaacson's Steve Jobs is a superb biography of the late, great co-founder, chairman, and CEO of Apple, but at 592 pages it’s a bit of a hefty tome.
If you’re interested in Jobs’ life, but don’t have the time, or inclination, to read the full book, there’s always the forthcoming film adapted by Aaron Sorkin to look forward to, or -- if you just want a super quick guide -- there’s this excellent infographic.

Over three-quarters of mobile apps will fail security tests by 2015
New research by analysts at Gartner shows that more than 75 percent of mobile apps are set to fail basic security tests by 2015.
This is a particular worry for enterprises as employees may download software from app stores. These apps offer minimal or no security assurances but are able to access sensitive business data and violate company security policy.

Flipboard for Windows Phone: It's coming, damn it!
I remember it like it was yesterday: when Lumia 1020 was unveiled, Microsoft and Nokia were very happy to announce that Flipboard would "soon" be coming to Windows Phone. That was in mid-July 2013. Fast forward to today and the app is still not available. "Soon" has a certain urgency to it, which, for some strange reason, always seems to be missing in its association with Windows Phone.
Microsoft and Nokia could have jumped the gun more than a year ago by touting that the app would arrive shortly after Lumia 1020's announcement, and Flipboard could have inadvertently delayed the launch since. No matter, "soon" sure ain't soon. Regardless, Flipboard is still on its way as its public listing on Windows Phone Store implies. This is one of the major missing titles; the sooner it is available the better for the platform.

Many UK iPhone 6 pre-orders cancelled after Phones 4u enters administration
Would-be iPhone 6 and iPhone 6 Plus owners are currently wondering whether or not they will receive the handsets they pre-ordered after Phones 4u went into administration.
On Sunday, the beleaguered retailer threw in the towel after EE decided not to renew contracts. While Phones 4u has said that it will honor orders that have been placed and dispatched, but indicated that orders that are yet to be sent out -- which will include many iPhone 6 orders -- will be canceled, and refunds issued.

Google steps up its game in India with Android One
The increasing popularity of smartphones in emerging markets coupled with Google's desire to gain control over its open-source mobile operating system have resulted in Android One. It's a new program, designed with low-end devices in mind, that will see more consumers enjoying the benefits of a close-to-stock Android experience on inexpensive handsets. It's also Google's way of making sure that billions of first-time smartphone users will be exposed to its services and become long-term customers.
"If we look at how people are getting online and accessing information today, increasingly it’s through a smartphone", says Android and Chrome & Apps SVP Sundar Pichai. "While 1.75 billion people around the world already have a smartphone, the vast majority of the world’s population -- over five billion more -- do not. That means most people are only able to make simple voice calls, rather than connect with family through a live video chat, use mapping apps to find the closest hospital, or simply search the web. We want to bring these experiences to more people".
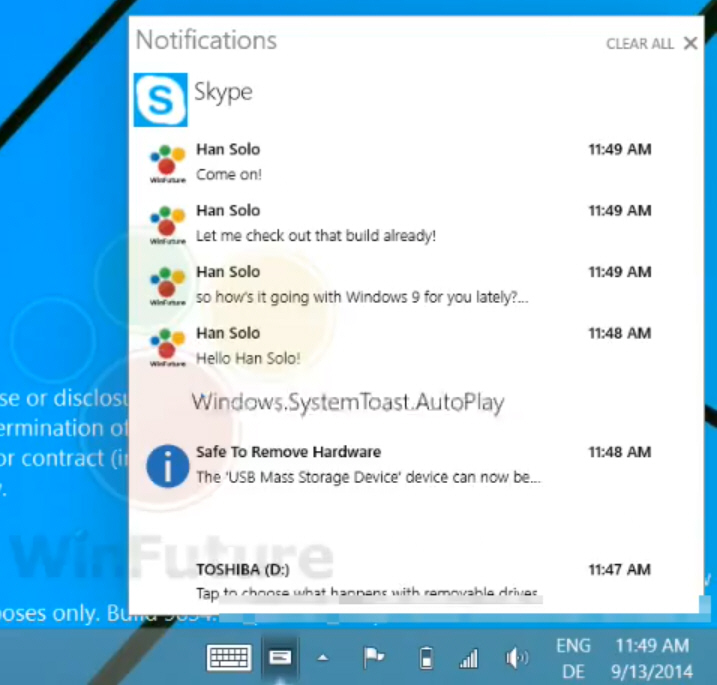
Take a look at Windows 9's new Notifications center
Last week, thanks to a series of leaked screenshots and videos from build 9834, courtesy of WinFuture.de, we got our first real look at the next version of Windows, including seeing the new Start menu and virtual desktops in action.
That’s not the only new feature being shown off however. In yet another new video we get to see the Notifications center which Microsoft is introducing.

How technology is changing football (or soccer) for the better
The use of technology in sports has historically been a contentious issue. "Video reviews will slow down the game" and "unfair advantage" are some of the complaints that get thrown at sporting bodies the world over when technology comes under scrutiny. Just look at the controversy with full-body swimsuits being banned in Olympic swimming. In this case records were broken, but so were rules.
Sport is big business. The latest European football transfer window only closed after £835 million ($1,356 million) was spent by British Premiership clubs. That's the highest spend ever seen within the league. Football clubs operate like any other business, meaning that cash flow and business documentation are vital processes. With so much money, hundreds of jobs and scrutiny from millions of fans worldwide reliant on actions on and off the pitch, things needs to run as smoothly as possible. That's why I believe that clubs need to embrace digital technology off the pitch. However, what about technology on it?

5 quick ways to speed up your Android smartphone
Remember the halcyon days of your HTC One/LG G3/Samsung Galaxy S5? How you ran your fingers across the screen and marveled as it transitioned smoothly between apps? You were together, taking on the world in ergonomic bliss.
Now though, with a few scratches to the screen and some scuff marks to the casing, your beloved phone has become sluggish and as you browse the web, your eyes guiltily move towards the gleaming fascias of the latest models.

Is Apple Watch out of time?
I am reluctant to criticize unreleased Apple Watch because my analysis about original iPad -- given before seeing it -- was wrong. That said, Android Wear, while seemingly sensible comparison that analysts, bloggers, and journalists make, isn't right. When put in perspective of next-generation wearables, I think Apple Watch should be compared to Google Glass.
Be honest. Which looks more innovative to you? The utility of something you see at eye level that provides real-time, location-based information is much greater than something that demands more responsive -- "Hey, Siri" -- interaction and turns the glance and fingers downward. Granted, Apple Watch delivers alerts, and you feel them, but your attention is always to look away.



