
CISOs watch out: The most effective cyber attacks never touch your company's firewall
When CISOs think about cybersecurity for their companies, there are certain expectations. Password protection, firewalls, and continuously training employees on the latest phishing scams, to name a few. And to be sure, cyber risks like these are as relevant as ever. The persisting problem is, cybersecurity is like any defense contest: the burden (and therefore the disadvantage) is on the defender. You have to win every time, whereas an attacker only has to win once to cause major damage.
Frustratingly, cyber criminals have shown time and time again that they are actually quite gifted at creative approaches, thinking outside the box, and combining advanced tech with old school techniques. For instance, a suspicious-looking form letter email is easy to spot and delete. However, by purchasing even a small amount of personal data from the dark web, a smart criminal can craft a phishing email with just enough familiarity so that its target will most likely open it without hesitation. With enough patience and photoshopping, a malicious actor can send customers a message from their favorite store that leads them to a spoofed website solely created to steal their credit card information. Increasingly today, these attacks targeting customers are more prevalent.

Windows 12 could be on the horizon as Intel lets slip Microsoft's 'Windows refresh' plans
Microsoft may be saying nothing about the release of Windows 12, but that's not stopping news slipping out about the successor to Windows 11. And thanks to information from Intel, it seems that 2024 is when we can expect to see a new Windows release.
The leak comes courtesy of David Zinsner -- Chief Financial Officer at Intel -- who confidently referred to "the Windows refresh" which he says is due to land next year. While his comments are not solid confirmation of the launch of Windows 12, it is a credible addition to the ever-growing pile of Windows rumors.

The 4 most important questions CIOs should be asking today
Although chief information officers have been at the forefront of enterprise digital transformation efforts for years, they are still too often reduced to the company’s "technology expert." Even if the reality is different, perception counts for a lot. It’s now time for CIOs to change that perception and evolve into more wide-ranging business strategists, enabling their IT departments to leverage their expertise for high-value business outcomes.
The good news is that most enterprise CIOs already have nimble, intelligent and scalable technology to facilitate that change. What’s needed is an approach that improves efficiency and increases productivity in ways that are directly tied to company goals. Here are four questions every CIO of a B2B enterprise should be asking as they seek to maintain the momentum of their digital transformation.

Staying safe online in 2023
As Cybersecurity Awareness Month celebrates its 20th anniversary this year, it's the perfect time to reflect on the strides we've made in security education and awareness. It’s also a chance to look ahead, combining education with the right technology to protect people at scale.
Two decades is a very long time on the internet -- there was no Facebook or YouTube in 2003. Now there are more than 500 times as many secure websites. Phishing was just beginning to catch on. Now phishing is widely reported to be a multi-billion-dollar problem, with millions of attacks detected and taken down each year. As the internet has evolved, so have cybercriminals.

Twenty years of software updates
In the beginning, software ran mostly on a smart server dumb terminal networked or entirely on a local machine. If there was a defect, it was that the given program wouldn’t run. Once desktops, laptops, mobile phones and even physical devices such as refrigerators started interconnecting via the internet, a software defect could open the device to an attack or shut down a life-critical system. The very real need to stay on top of software updates has been escalating every day.
In the early 2000s, when computer malware began as a few innocent viruses before morphing into full-on malevolent worms, the software giants such as Microsoft (but by no means limited to Microsoft) denied responsibility. There was significant push back with vendors saying that compromise was only possible in only a limited number of scenarios -- almost as though the end user was responsible. Increasingly, though, it became clear that maybe the software itself could be responsible for some of the malicious activity on the early internet. And maybe the software industry needed to take that seriously.

You can't avoid APIs, so you need to secure them
As APIs emerge as the unsung heroes behind modern software development for their ability to accelerate innovation and streamline processes, it’s no secret or even a surprise that API security is a lingering problem that the broader cybersecurity industry has yet to fully solve. Since abandoning the use of APIs is not a viable option, organizations need to focus on building strong AppSec programs that give the teams developing with APIs, the structure and tooling to ensure connections are secure and software deployed is safe.
To be most effective, organizations need to prioritize designing security best practices into development workflows from the beginning and by adopting secure-by-design based principles.

Get 'Take Control: The Career You Want, Where You Want' (worth $17) for FREE
The workscape has changed -- one of the most dramatic transformations of the past few years. Think about it. For so many people just starting their careers, working virtually is all they know. For everyone else who has had the remote option, work is no longer synonymous with a physical location.
In this push-pull world, that means navigating and negotiating between the flexibility and opportunity you want -- and the commitment and performance that organizations need. In other words, you need to take control.
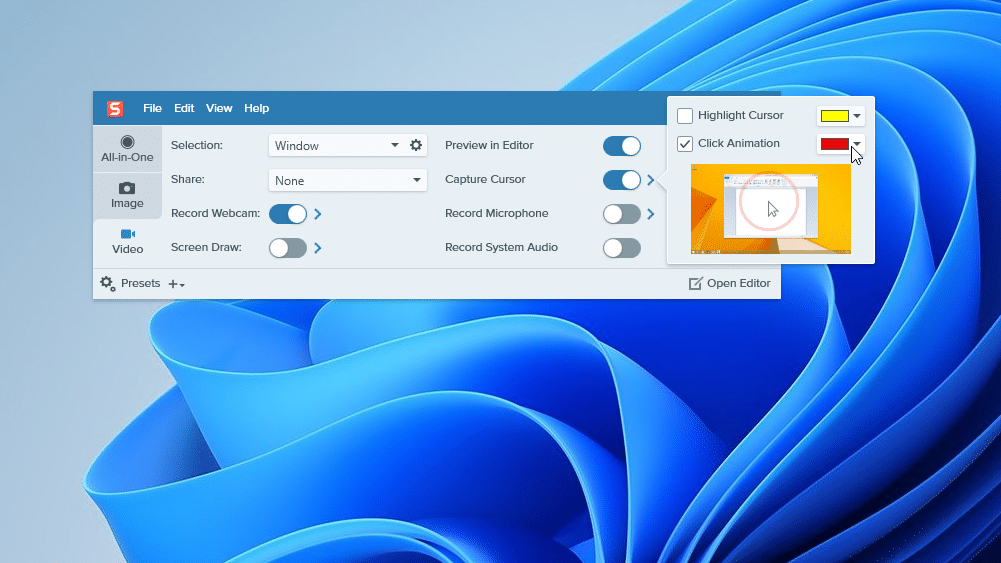
Snagit 2024 lets users combine video recordings, highlight cursor on-screen
Screen-capture specialist TechSmith has released Snagit 2024 for Windows and Mac, a major new version of its powerful screen-capture tool.
The 2024 build unveils the ability to add click animations and highlighted cursors, adds supports for combining video, and unveils a new starter theme alongside stamp collections.
Best Windows apps this week
Five-hundred-and-sixty-three in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Copilot is coming to all Windows 11 users next week. Microsoft has now admitted that Copilot is causing some issues, especially for Narrator users.

Cybersecurity Awareness Month turns 20
October, as you might have noticed, is Cybersecurity Awareness Month. Now in its 20th year, this aims to bring the public and private sectors to work together to raise awareness about the importance of cybersecurity.
As always industry experts are keen to use the event to offer views on the security landscape, here we round up some of their comments.

Meeting the challenges of API security [Q&A]
In today's increasingly digitally-centered organizations, the development of products, services, and solutions increasingly depends on the implementation of Application Programming Interfaces (APIs).
APIs have become the building blocks of modern business applications and are critical to digital transformation -- so much so that API security has become a boardroom issue.

Silicon Power unveils XPOWER XS80 PCIe Gen5 SSD
Silicon Power chose the stage of PAX at the Melbourne Convention and Exhibition Centre (MCEC) to unveil its newest solid state drive. Called “XPOWER XS80,” this PCIe Gen5 SSD marks a significant milestone in high-performance storage solutions tailored for gaming.
Harnessing the power of the latest PCIe Gen5 technology coupled with NVMe 2.0 support, and a 232-layer 3D NAND flash, the XS80 transcends the ordinary, offering a data transfer rate that is twice that of Gen4 and quadruple that of Gen3. This SSD is crafted to meet the demands of modern-day gaming, ensuring that gamers no longer have to compromise on performance.

v-color announces low-timing DDR5 memory kits
v-color Technology Inc has announced new DDR5 memory kits, aiming to make a mark in the gaming and overclocking space. The company’s latest offerings feature module capacities of 16GBx2 and 32GBx2, a Cache Latency (CL) of 26, with speeds ranging from 5600MHz to 5800MHz. This release is part of v-color’s attempt to cater to users seeking lower latency and moderate speed enhancements.
The new low-timing XSky series DDR5 memory kits come with different specifications including 32GB (2x16GB) DDR5 5600MHz CL26-36-36-76 1.4V, 32GB (2x16GB) DDR5 5800MHz CL26-36-36-76 1.4V, and 64GB (2x32GB) DDR5 5600MHz CL26-36-36-76 1.4V. These configurations are tailored for those who are keen on boosting their system’s performance.
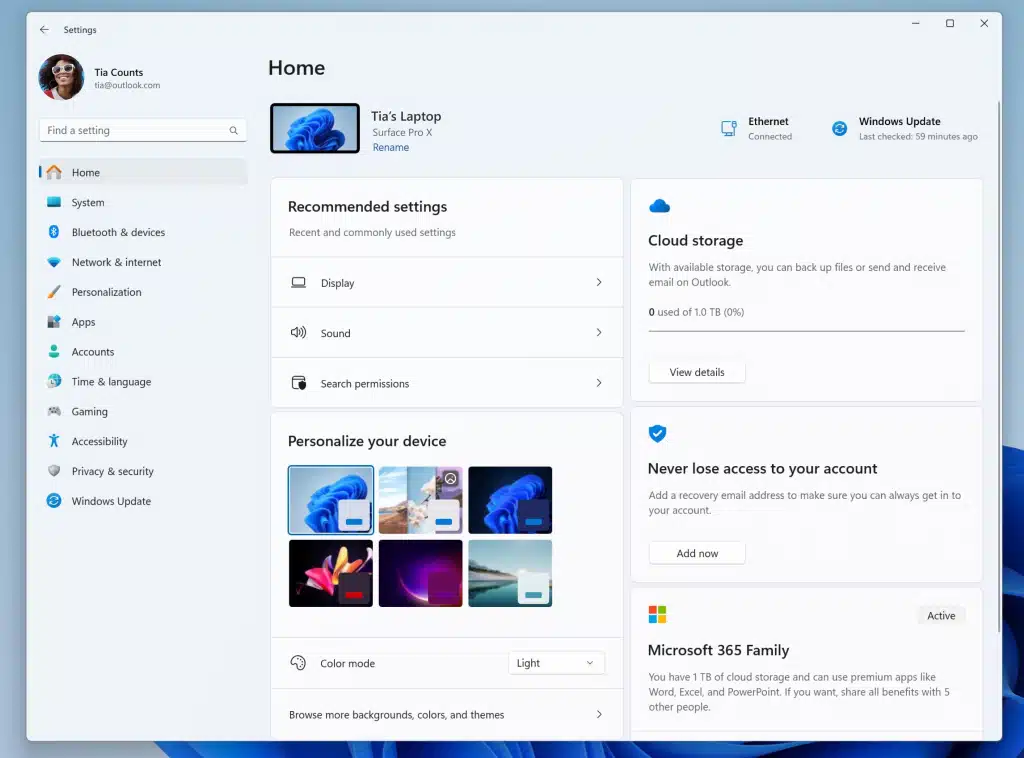
Microsoft releases experimental Windows 11 Build 25967 with new Settings homepage
Microsoft continues to add new features to Windows 11, and Windows Insiders in the Canary Channel get to try out some of the more experimental ones.
New in Build 25967, released today, is a redesigned homepage in Settings that offers a "dynamic and personalized experience". Microsoft says it provides an overview of your device, quick access to key settings, and helps manage your Microsoft account.

HyperX unveils three new products for gaming creators and streamers
Today, HyperX (the gaming peripherals division of HP) announces three new additions to its product lineup. Designed for both gaming creators and streamers, there is the HyperX Vision S Webcam, HyperX Audio Mixer Audio Interface, and the HyperX Caster -- a toolless spring-loaded microphone arm.
"We are excited to expand our portfolio of products and provide a more complete creator solution. The Vision S Webcam offers superb video quality and user-friendly features, and the Audio Mixer Audio Interface provides content creators with professional-grade sound. Since the listening experience for a content viewer is so important, we’ve added a volume meter to offer a quick and easy way to check input levels at any time. HyperX remains committed to enhancing the gaming and content creation experience, empowering users to unleash their full potential," says Sean Peralta, the company’s Director of Product Management.



