
40 million individuals exposed in healthcare data breaches
Despite an overall decline in the number of healthcare data breaches, the first half of this year has seen a record number of individuals have their information exposed.
The latest Healthcare Data Cyber Breach Report from security-as-a-service provider Critical Insight shows individual records compromised in data breaches increased by 31 percent in the first half of 2023 compared to the second half of 2022.

IBM launches generative AI tool to help modernize mainframe software
Many large enterprises still rely on mainframes, but the use of legacy technology can hold back modernization and digital transformation efforts.
To help organizations progress their modernization plans, IBM is launching watsonx Code Assistant for Z, a new generative AI-assisted product that will help enable faster translation of COBOL to Java on IBM Z systems and enhance developer productivity on the platform.

Microsoft is willing to make massive cloud concessions to gain UK approval for Activision Blizzard deal
Microsoft's attempt to acquire Activision Blizzard has been a long, drawn-out affair with a seemingly endless series of obstacles along the way. Now the company has indicated a willingness to make major concessions as it submits a revised deal for approval.
Facing regulator opposition to the deal in the UK so far, Microsoft's latest proposal to the CMA (Competitions and Markets Authority) includes an offer to sell cloud gaming rights to Ubisoft.
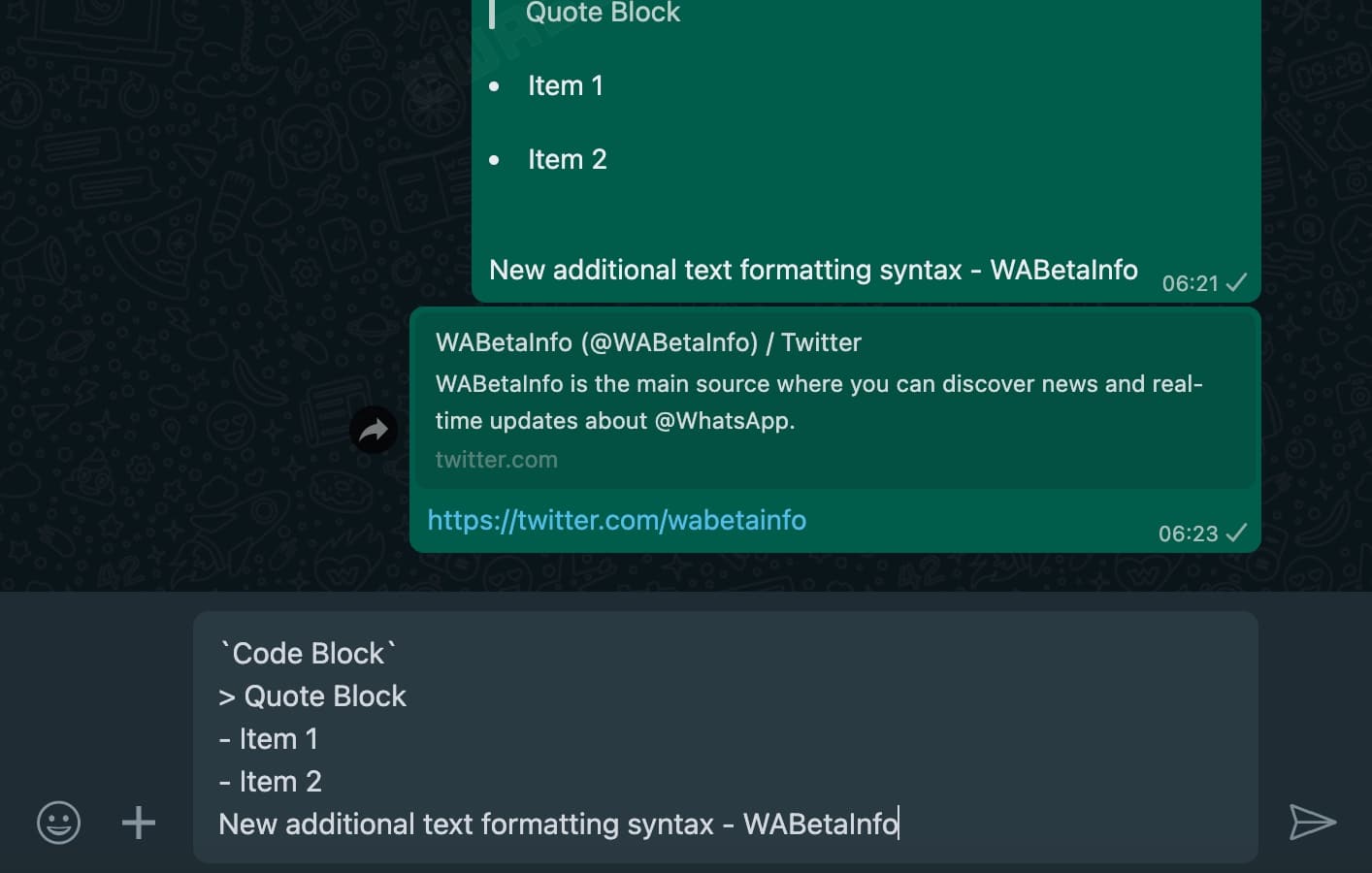
WhatsApp is finally getting more text formatting tools
Although WhatsApp leads the way in many regards, there are plenty of areas in which it is lagging behind. The text formatting options in the message app are incredibly limited, for instance, but this is about to change.
The Meta-owned app is finally being given more formatting tools. The update means that WhatsApp users will no longer be limited to using bold, italics and strikethrough, and the need to find workarounds for the lack of common formatting options will soon be eliminated.

Microsoft is treating Windows 10 users to more apps from Windows 11
Having already brought Windows 11's backup tool to Windows 10, Microsoft is porting more apps back to the older version of its operating system.
The latest Windows 11 app to be offered to Windows 10 users is the Photos app. But if you are wondering why Microsoft continues to eliminate reasons to upgrade from Windows 10 to Windows 11, the company has a few tricks up its sleeve.

GEEKOM Mini IT13: The world's first 13th gen Intel Core i9 mini PC
Today the tech world is being treated to new details about an upcoming computer from GEEKOM, one of the top providers of miniature PCs. The “Mini IT13,” as it is called, is a groundbreaking machine, as it is the first mini PC equipped with the 13th Gen Intel Core i9 processor.
Whether you're a professional seeking a reliable workstation, a creative looking for exceptional graphics performance, or a gamer craving unmatched power, the GEEKOM Mini IT13 should deliver on all fronts.

The (not so) secret behind successful DEI programs: build in diversity, equity and belonging, don't bolt it on
Why do organizations launch diversity, equity, and inclusion (DEI) programs? Simple: It's the right thing to do. Equity and inclusion are basic human rights. DEI is also better business. Multiple studies show companies highly rated for DEI enjoy superior employee engagement and belonging, EBIT margins, total shareholder return, revenue growth, and change agility.
DEI is clearly a slam-dunk must-have. In an HR context, DEI is the philosophical core of building and creating equal career development opportunities for all employees.
Bodhi Linux 7.0 challenges Microsoft Windows 11
The long-awaited Bodhi Linux 7.0 release has finally arrived, and it should make big waves in the open-source community. Built on the solid foundation of Ubuntu 22.04.2 LTS (Jammy Jellyfish), Bodhi 7.0 represents a significant evolution in the realm of Linux distributions. With a strong emphasis on improving user experience, performance, and maintaining its core values of minimalism and customization, this release aims to redefine what Linux can offer to its users.
In a world dominated by proprietary operating systems like Microsoft Windows, Bodhi Linux 7.0 emerges as a breath of fresh air, presenting itself as a compelling alternative. The release boasts an impressive array of enhancements and changes that cater to both newcomers and seasoned Linux enthusiasts.

It's in the cloud somewhere... Three-quarters of enterprises don't know where their apps are
A new study reveals that 76 percent of enterprises don't have complete visibility into the access policies and applications across multiple cloud platforms, including which access policies exist, where applications are deployed, and who does and doesn't have access.
The report, from Strata Identity based on data from Osterman Research, shows the percentage of organizations using a single cloud identity provider (IDP) is down from 30 percent to 20 percent since last year. The other 80 percent are now using multiple IDPs to manage enterprise identity.

Researchers feel overwhelmed by errm… research
A new study finds that 66 percent of researchers are overwhelmed by the quantity of published work they have to review.
The survey, by research platform Iris.ai, of 500 corporate R&D workers shows that 69 percent spend at least three hours a week reviewing research documents, with 19 percent of those spending over five hours. AI could help to address this problem but is not being widely used.

How the metaverse is set to change the way businesses communicate [Q&A]
Increased use of the metaverse and other immersive spaces using VR, AR and digital avatars, is going to change how businesses communicate with their customers.
In an increasingly globalized world part of the issue is how real time experience will cope with the use of different languages. This is expected to put real pressure on automated and machine translation services to deliver fast, accurate results.

Budgie 10.8 takes Linux desktop experience to new heights
Exciting news, y’all! Budgie 10.8 has landed, and the Linux desktop environment is packed with features that promise to transform how we interact with our desktops.
First off, the Budgie Menu has received quite the makeover. If you've ever scratched your head wondering why certain apps are in the 'Other' category, you're not alone. The team listened to feedback, and now, applications have found more fitting categories. Plus, there’s a nifty fix for non-Latin text crashes, thanks to a switch to C for the Application Indexer's fuzzy scoring function. And, let's say goodbye to the Utilities category; its apps have found a new home in System Tools.

From garage to global giant: The evolution of Apple
Apple Inc., the brainchild of Steve Jobs, Steve Wozniak, and Ronald Wayne, has transformed from a humble garage start-up into a global technology powerhouse since its inception on April 1, 1976. The trio's vision was to develop and sell personal computers, with their first offering being the Apple I, hand-built entirely by Wozniak and marketed by Jobs.
Introduced at the Homebrew Computer Club in Palo Alto, California, the Apple I marked the beginning of a technological revolution. Despite the company's modest beginnings, its vision was clear -- to bring an easy-to-use computer to the market. In 1977, Apple was incorporated without Wayne, who sold his share back to Jobs and Wozniak for $800. The same year, the company launched the Apple II at the West Coast Computer Faire, propelling Apple into the forefront of the burgeoning personal computer industry.

V-Color announces MANTA XPrism RGB DDR5 48GB (2x24GB) Memory Kit
Hey there, fellow tech nerds! So, V-Color's at it again, rolling out another piece of kit. This time, the company announces the MANTA XPrism RGB DDR5 48GB (2x24GB) Memory Kit. This RAM should be available here later this month. Pricing is not yet known, sadly. It comes in this SCC 2+2 setup and touts speeds that swing between 6200 to 6600.
V-Color has thrown in its patented RGB Filler Kit, which they say is perfect for Intel systems. They're also hyping up its Intel XMP 3.0 compatibility for smooth automatic overclocking. And guess what? They claim it'll play nice with some of the big motherboard names like ASUS and GIGABYTE.

Update WinRAR right now to patch high-severity security flaw
Users of the archiving utility WinRAR are being advised to update their software as soon as possible following the discovery of a serious Remote Code Execution vulnerability.
Tracked as CVE-2023-40477, the security flaw was discovered back in June and it allows malicious code to run when opening a RAR archive. Two months on, the issue has been fixed, but users of the software will have to ensure that they have the latest update installed to guarantee protection.



