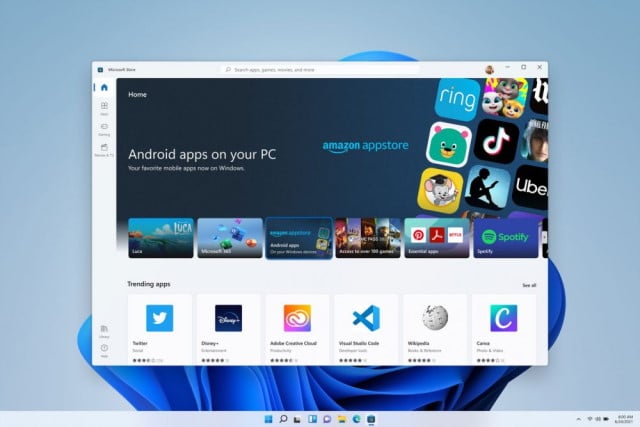
Windows 11's Android app support is not as disappointing as you might think
Microsoft has officially announced Windows 11, the dust has settled, and the excitement has died down a little. Now it's time to look at what we know is going to be included in the latest version of the operating system, rather than guessing and speculating as we have had to do up to now. And when we do this, there various reasons to be disappointed.
We always knew -- or at least suspected -- that Windows 11 was not going to be a major change from Windows 10. It has already been dismissed by some as being little more than a theme pack or service pack, but there are new features. One of the things that generated quite some interest is support for Android apps, but hearts then sank after learning that rather than Google Play, apps will need to come from the Amazon app store. But there is some great news...

What I'd like to see in the upcoming Sling app
I’ve mentioned before that I replaced my satellite service with Sling about six years ago. Since then it’s added a cloud DVR and recently upped the capacity of that to what I consider to finally be a reasonable amount of storage space. It’s also added quite a few more channels in that time. There have been app updates as well, some welcome and some not so much.
Now the service teases another update coming soon. A box popped up on my screen the other day announcing the change and promising an improved TV experience "soon".

Has your PC failed the Windows 11 upgrade check? This may help you make it compatible (for free)
The big reveal has been made: Windows 11 is coming later in the year, and it’ll be a free upgrade. So if you’ve been putting off the move to Windows 10, relax: you can buy or upgrade now, then upgrade again when the new OS becomes available.
Windows 11 offers more than a simple facelift over Windows 10 -- although at first glance you might think that many of the features announced yesterday amount to little more than windows dressing.

Mozilla launches new data sharing research platform
Data, as we know, has become a valuable commodity and that has thrown the privacy and transparency aspects of what information organizations hold about us into sharp relief.
Mozilla believes that we should have more control over our data and is launching a new platform to give people more choice over what data they share and with who, and allowing them to help with research projects.
Best Windows 10 apps this week
Four-hundred-forty-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft unveiled Windows 11 this week. The next version of Windows will be released later this year, and it will include new features such as support for Android apps, performance improvements, usability improvements, and Teams integration.
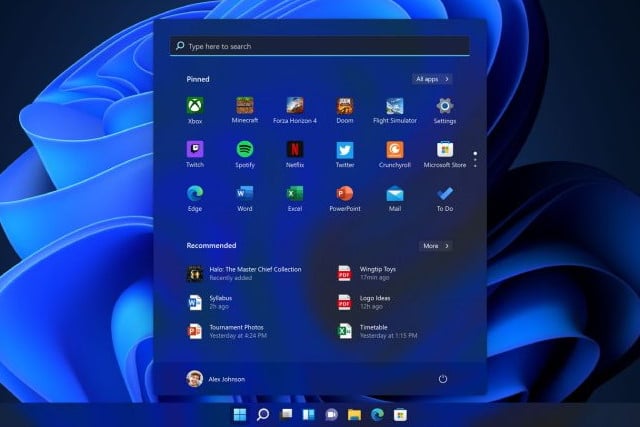
Want to move the Windows 11 taskbar? Tough! You can't
The taskbar has been a feature of Windows for many years now, and it is almost as iconic as the Start button. Traditionally it is placed at the bottom of the screen, but there has always been the option to move it to the top or sides if preferred. Not so with Windows 11.
Although the majority of people leave the taskbar where it is, the prevalence of widescreen and ultra-widescreen monitors has meant that it makes more and more sense to move it to the side to make better use of space. With Windows 11, however, Microsoft has taken the decision to lock the taskbar in place at the bottom of the screen.

How to check if your PC can run Windows 11 right now
Following Microsoft's big event yesterday, PC users around the world are asking themselves "will my computer run Window 11?". Although many people have installed the leaked version of the operating system, most will be waiting for the official release later in the year.
Microsoft has already shared details of the minimum system requirements for Windows 11, but this is not information that everyone finds useful; many have been baffled by the TPM (Trusted Platform Modules) requirement, for instance. People are looking for a straight "yes" or "no" answer rather than having to check hardware specs. So, if you're wondering whether or not you need to buy a new PC to be able to enjoy everything that Windows 11 has to offer, here's how you can check right now using a special tool from Microsoft.
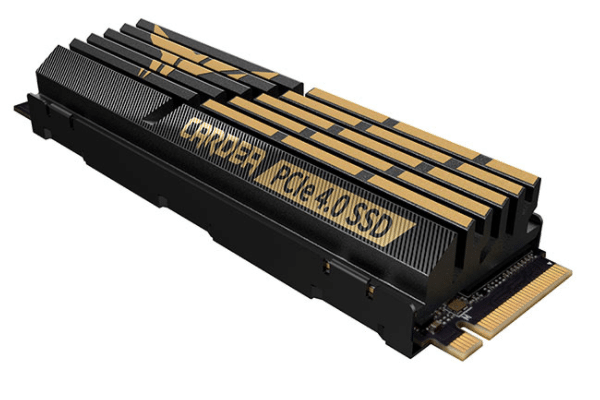
TEAMGROUP launches hardcore T-FORCE CARDEA Z44Q NVMe PCIe 4.0 SSD
If you have a cutting-edge PC with PCIe 4.0, you will probably want to get a compatible solid state drive to maximize your performance. True, PCIe 4.0 SSDs are largely for bragging rights and benchmarks -- you probably won't notice a difference in actual use -- but still, you might as well go for the best if the difference in price isn't totally obscene.
Today, TEAMGROUP unveils a new M.2 2280 NVMe PCIe 4.0 SSD. Called "T-FORCE CARDEA A440," this speedy gaming-focused SSD comes with interchangeable heatsinks -- a very unique cooling option. Essentially, you can opt for the giant aluminum heatsink if it fits in your computer, or the graphene heatsink if space is tight

Everything you need to know about Windows 11 in under 3 minutes
If you didn’t watch today's full Windows 11 reveal -- because you didn’t have the time, opportunity or inclination -- then you can catch up on what’s new here.
Of course, as they say, a picture paints a thousand words, and a video is even better when it comes to conveying information.

How to get the first Windows 11 Preview builds
Microsoft took the wraps off Windows 11 officially today, and as well as revealing the new OS will be a free upgrade from Windows 10, it also announced that it will be issuing the first test builds to Windows Insiders shortly.
If you’re already a Windows Insider that’s great news (if you’re not you can sign up here), but Windows 11 has updated hardware requirements and there may be other roadblocks that prevent you from testing out the new OS.

These are the Windows 10 features Microsoft will be deprecating and removing from Windows 11
Although some people will view the newly announced Windows 11 as Windows 10.5, the truth is it’s a big change for Microsoft’s operating system.
Although Windows 11 will debut lots of new features, including widgets, Teams Chat and Android app support, some of the features and functionality you’re used to in Windows 10 may well be coming to an end. These are the key features that will be impacted.
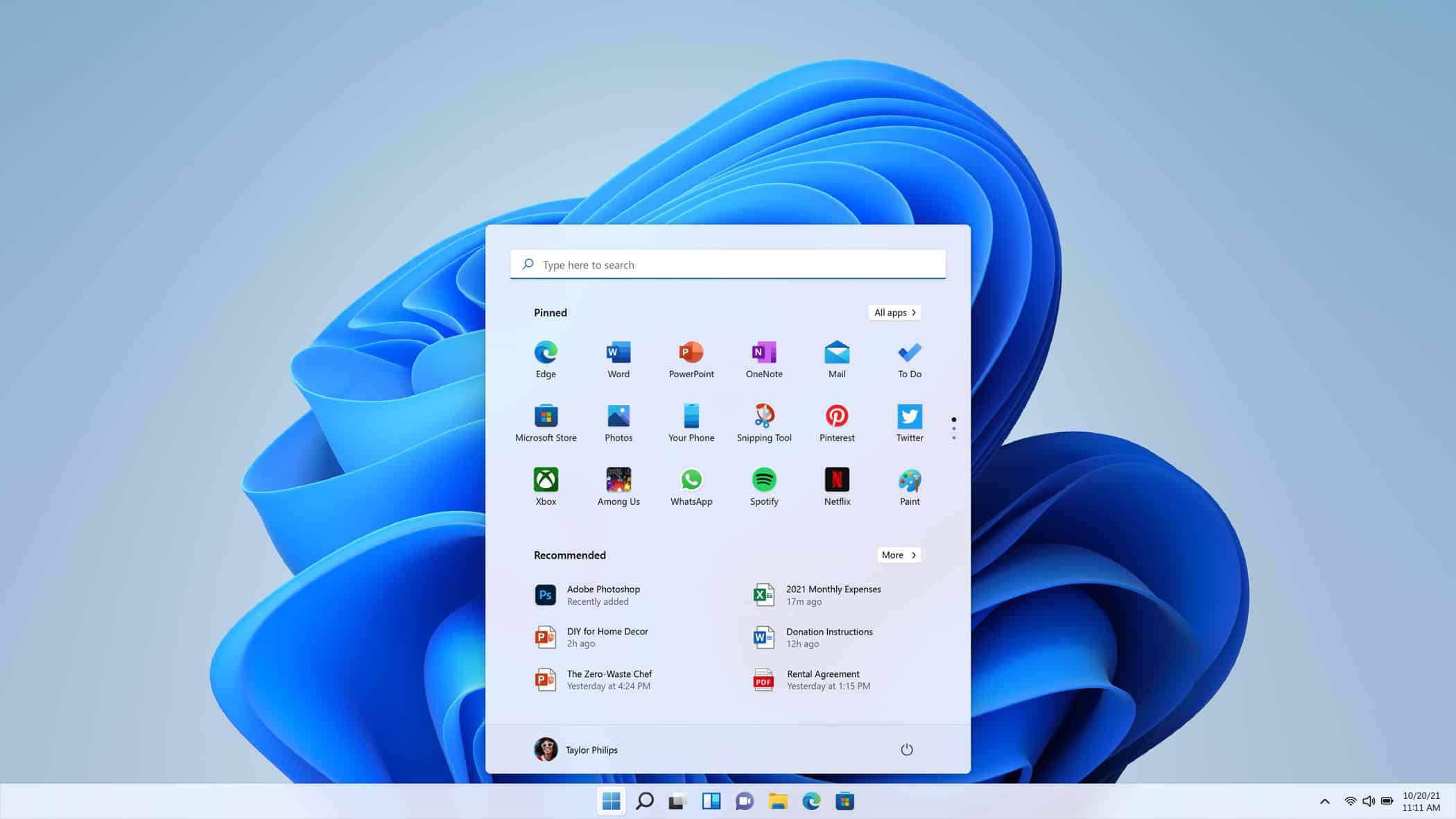
These are the updated hardware requirements for Windows 11
During its grand reveal of Windows 11 earlier today, Microsoft stressed that the new OS will run faster, and upgrades will be smaller and happen in the background.
If you’ve found Windows 10 to be a little sluggish at times, that might sound like great news to you, but Microsoft has updated the base hardware requirements for the new OS, so if your system is getting on a bit it may not be able to run it.
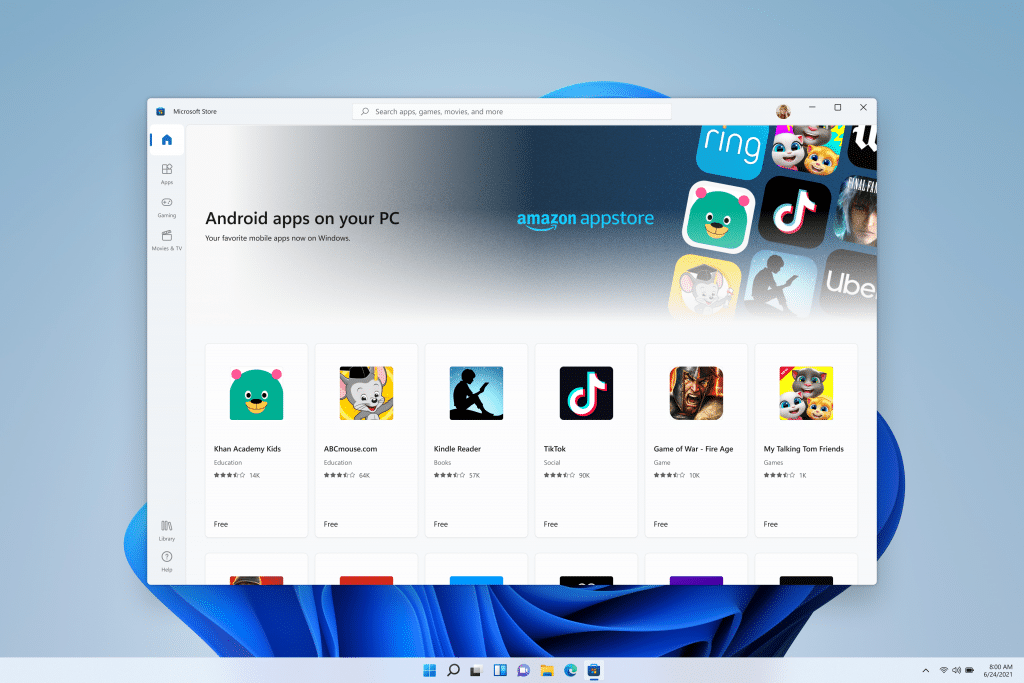
Windows 11 will support Android apps through the Amazon Appstore
Although the Windows 11 announcement introduced lots of new and exciting features coming to the new OS later in the year, perhaps the most jaw dropping was native support for Android apps.
Users will be able to find and download Android apps directly through the new and improved Microsoft Store, but you won’t be able to grab your favorites through Google Play as it isn’t supported.

Windows 11 will be a free upgrade for Windows 10 users
Today Microsoft took the wraps off what we can expect from its new operating system and it’s a lot. You can see what’s coming here.
The first builds of the new Windows 11 will begin making their way to Windows Insiders from next week, although it will be a while until we see the makings of a finished OS as general availability isn't expected until the end of the year. What we also learned from the announcement is the cost of the OS and the upgrade options.

Microsoft officially confirms Windows 11 with integrated Teams and support for Android apps
We’ve had teases and leaks already, but today at a special 'What's Next for Windows' event Microsoft officially confirmed the successor to Windows 10, and as expected it’s Windows 11.
The new operating system is based on the now cancelled Windows 10x design, but it’s much more than that. As you’ve have seen from the leaked screenshots, it has a centered taskbar and Start menu, rounded corners across the design, no live tiles, and web widgets for creators.



