
The new-look IObit Advanced SystemCare 14 can optimize your system using AI
IObit Advanced SystemCare is back with a big update that brings not only a new look, but also a number of new and improved tools, and also the addition of AI to automate the optimization of your computer.
The updated look is what you'll notice first about IObit Advanced SystemCare 14, but the latest version is about much more than a fresh coat of paint. As ever, there is a free version and a paid-for professional edition, and this time around the powerful Internet Boost tool is available to users of the free version.
Best Windows 10 apps this week
Four-hundred-and-nine in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 on the Microsoft Store in the past seven days.
Microsoft started the rollout of the Windows 10 October 2020 Update (Windows 10 20H2) this week. Check out how to grab an ISO image of the new version, and find out about all known issues here.

How to force Windows 10 to install blocked updates
Updates for Windows 10 are frequently problematic, causing a wide range of issues both large and small for users. Sometimes, Microsoft intervenes while it investigates problems, and puts a block on certain updates for systems and hardware configurations that are known to run into troubles with a particular release.
While this makes sense, many people prefer the idea of being in control of what they can and cannot install on their own computers. If you would like to get around one of these Microsoft-imposed compatibility holds/update blocks, here what you need to do.

What do Trump, Biden, COVID and your dog have in common?
They're all likely to be part of your password according to a new survey from security.org which asked 750 Americans to share their password strategies and security habits.
It reveals some worrying trends, 45 percent of Americans are using passwords that are eight characters or less, with only 15 percent using strong password generators.

SanDisk Ixpand Wireless Charger Sync creates local backups while charging
If you are like me, you charge your smartphone every night before bed. While some people still use old-school charging cables, many others -- including yours truly -- use a Qi wireless charger instead. I prefer this more modern option, as I can just drop my phone on the charging pad when I am exhausted -- no need to fiddle with plugging something in like a caveman.
Most Qi wireless chargers are pretty much all the same these days, but now, SanDisk has a new model that offers an incredibly useful feature. Called "Ixpand Wireless Charger Sync," the charging pad contains flash storage that allows the phone to automatically back up files locally while charging. How insanely cool is that?

Get 'Business Skills All-In-One For Dummies' ($22.99 value) FREE for a limited time
There are some things that will never go out of style, and good business skills are one of them. With the help of this informative book, you’ll learn how to wear multiple hats in the workplace no matter what comes your way -- without ever breaking a sweat.
Compiled from eight of the best Dummies books on business skills topics, Business Skills All-in-One For Dummies offers everything you need to hone your abilities and translate them into a bigger paycheck.

Ubuntu Linux 20.10 'Groovy Gorilla' is here with renewed Raspberry Pi focus
There are many Linux-based desktop operating systems these days. Some of them are great, while others range from mediocre to downright bad and unnecessary. When a new version of a Linux distro comes out, the Linux community takes notice, but largely, the world doesn't pay it any mind. That is, of course, unless it is Ubuntu.
Yes, Canonical's Ubuntu is undoubtedly the most well-known desktop Linux-based operating system, and when a new version becomes available, it is a very big deal -- even in the mainstream. This is despite that there is no real surprise in each release announcement -- they come twice a year, in April and October.

Researchers uncover botnet targeting decade-old CMS vulnerability
The results of a six-month investigation into a botnet that targets a vulnerability in content management systems have been released today by Imperva Research Labs.
The botnet known as 'KashmirBlack' first appeared around November 2019 and is still active. It's managed by a single command and control server and uses more than 60 servers -- mostly innocent surrogates -- as part of its infrastructure.

ESET launches updated consumer security range for Windows
Cybersecurity company ESET is launching new versions of its Windows consumer security products offering improved levels of protection.
ESET Internet Security, ESET NOD32 Antivirus and ESET Smart Security Premium get a wide range of security improvements covering malware detection, online banking, password security and smart home support.

Machine identity attacks grow more than 400 percent
The number of reported machine identity-related cyberattacks grew by 433 percent between 2018 and 2019, according to a new report from Venafi.
Between 2015 and 2019, the number of reported cyberattacks that used machine identities grew by more than 700 percent. Over the same period the number of vulnerabilities involving machine identities grew by 260 percent, increasing by 125 percent between 2018 and 2019.

New marketplace aims to promote transparency in AI and machine learning
The major challenges faced by businesses looking to implement AI and machine learning include transparency, bias, and quality of training data.
Swedish startup Unbiased is launching a new Data Marketplace on the Telos blockchain platform, aimed at providing privacy-centric and decentralized development tools to companies working with AI and Machine Learning applications.

UK Digital marketing survives the pandemic but faces a skills crisis
In the face of lockdowns to control COVID-19 marketers have had to quickly adjust customer experience strategies and utilize new technologies and channels to engage with consumers.
A new report from digital experience company Acquia shows that many have done this successfully, with some 83 percent of UK brands seeing improved return on investment on marketing and customer experience technology over the past year.
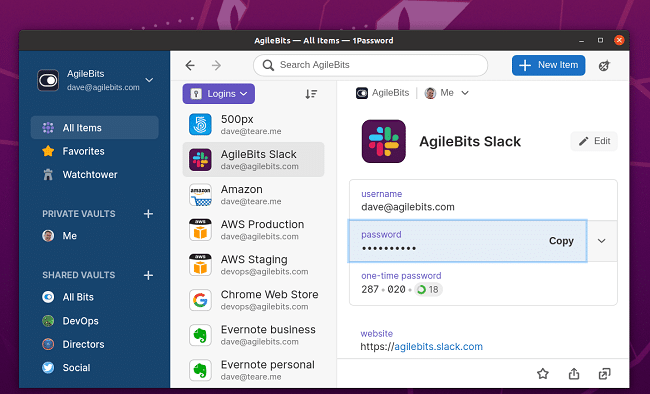
1Password for Linux Beta now available on Ubuntu, Mint, Manjaro, Fedora, and more
Back in August, we told you about some very exciting news -- 1Password had come to Linux... as a development preview. Yeah, it was a pre-beta release, but still, it was a huge win for the Linux community overall.
1Password is an extremely popular password management service, available for Mac, Windows, Android, and iOS/iPadOS. Bringing it to Linux makes the software truly cross-platform. Not to mention, it says a lot about the growing popularity of Linux that Agilebits found it beneficial to assign precious resources to its development.
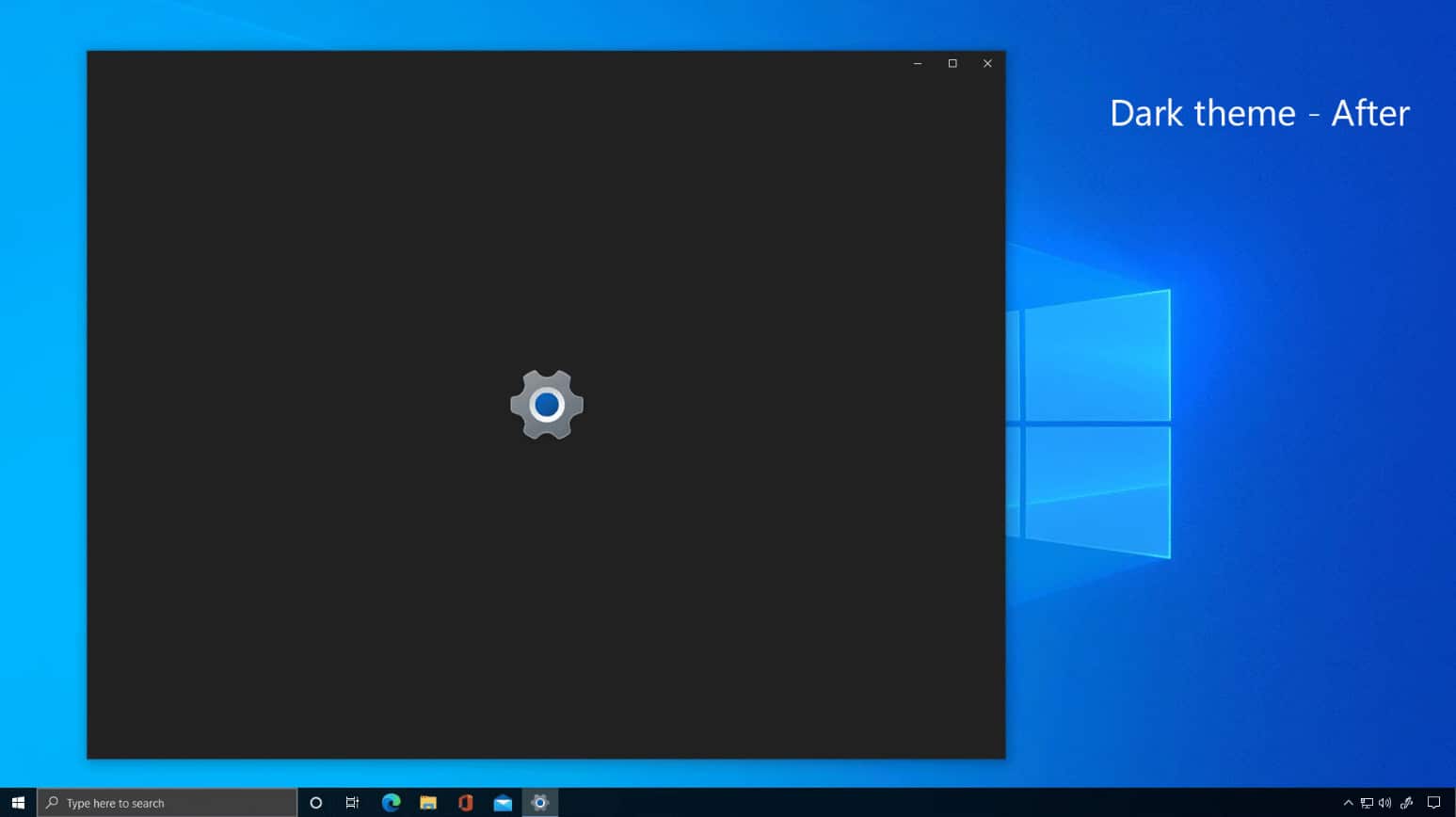
Microsoft releases Windows 10 Build 20241 with theme-aware splash screens for apps
Yesterday, Microsoft began rolling out the latest feature update for Windows 10. The long-awaited October 2020 Update -- or 20H2 if you prefer -- comes with a number of new features, such as improvements to Microsoft Edge, a refreshed Start menu, new Settings, and better notifications.
Today, the software giant releases a new Windows build for Insiders on the Dev Channel.

Acer unveils Chromebook Spin 513 laptop and Chromebox CXI4 desktop
Many people said it was impossible to bring desktop Linux to the mainstream, but guess what? Google did it. Yup, thanks to Chrome OS, there are countless people running Linux as their main desktop operating system every day. This is for home use, education, and business. During the pandemic, Chromebooks have been so popular that it can be hard to find one at a reasonable price.
Acer has long been a proponent of Chrome OS, and today, the much-respected company unveils two new machines -- the Chromebook Spin 513 laptop and Chromebox CXI4 desktop. The Spin 513 is a convertible, meaning it can pull double-duty as a tablet when folded. Since Chrome OS supports Android apps and Google Play, it is a very good tablet experience too. It is powered by an ARM processor, which seems to be the future of computing.



