
Microsoft releases emergency patch for Windows 10 BitLocker recovery problems
The release of the KB5058379 update for Windows 10 earlier this month resulted in frustration for many Windows 10 users. People with devices with Intel Trusted Execution Technology (TXT) enabled on 10th generation or later Intel vPro processors were hit with BitLocker recovery problems.
It took Microsoft a little while to acknowledge the issue, but now the company has issued an out-of-band patch in the form of the KB5061768 update.
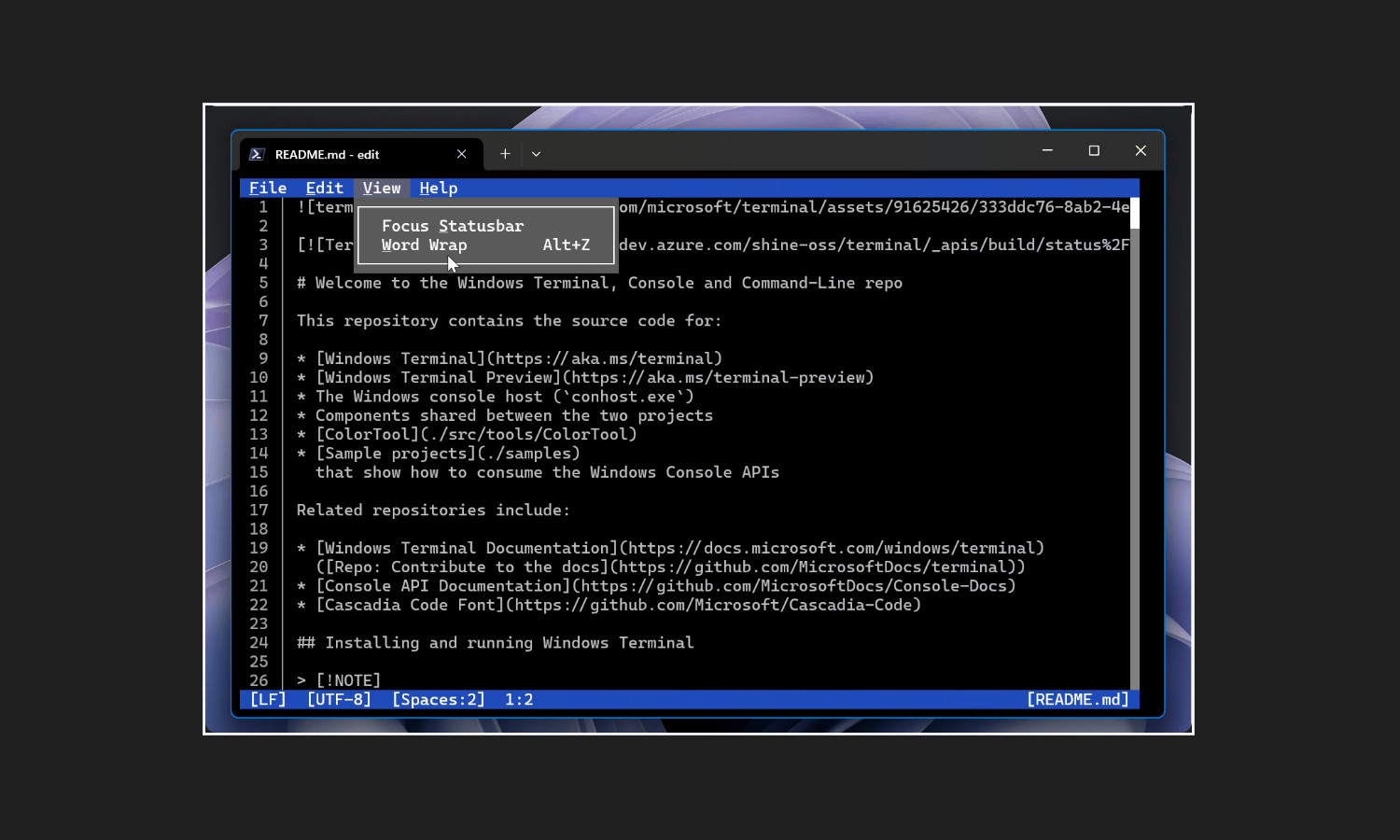
Microsoft launches Edit, its new open-source command line text editor
Microsoft Build is usually about cutting edge development, but sometimes there are nods to the past. And this is precisely what is happening with the company’s new text editor.
Named -- uninspiringly -- Edit, this text editor is not only open-source, but it is a command line tool. While clearly not something that will be of interest to the majority of Windows 11 users, it is something that has strong developer appeal.

MSI unveils new handhelds and laptops in massive Computex 2025 showcase
At Computex 2025, MSI definitely is not playing it safe. The company clearly came to Taipei ready to shake things up with fresh handheld gaming devices, artistic laptop designs, and a growing relationship with Mercedes-AMG. From lacquered laptops to performance-packed portables, MSI’s lineup is truly exciting.
The Prestige 13 AI+ Ukiyo-e Edition might be the most striking device on display. It features real Japanese Yamanaka lacquer, crafted in partnership with OKADAYA, and uses the famous “The Great Wave off Kanagawa” artwork as a design centerpiece.

Sesame Street is coming to Netflix but PBS will thankfully still offer it for free
If you’ve got a toddler at home, chances are Sesame Street is already part of your daily routine. Whether it’s Elmo giggling or Cookie Monster teaching patience through snack-based wisdom, the show has long been a lifeline for tired parents and an educational joyride for kids. So the news that Sesame Street is coming to Netflix later this year should sound like a win -- and it mostly is.
Netflix will be home to Season 56 of the show, complete with a refreshed format and plenty of returning fan favorites. Kids can look forward to new segments like Cookie Monster’s Cookie Cart and Abby’s magical fairy garden, all wrapped up in a new 11-minute story-driven episode structure. It’s a smart move that might make the show even more engaging for younger viewers with shorter attention spans.
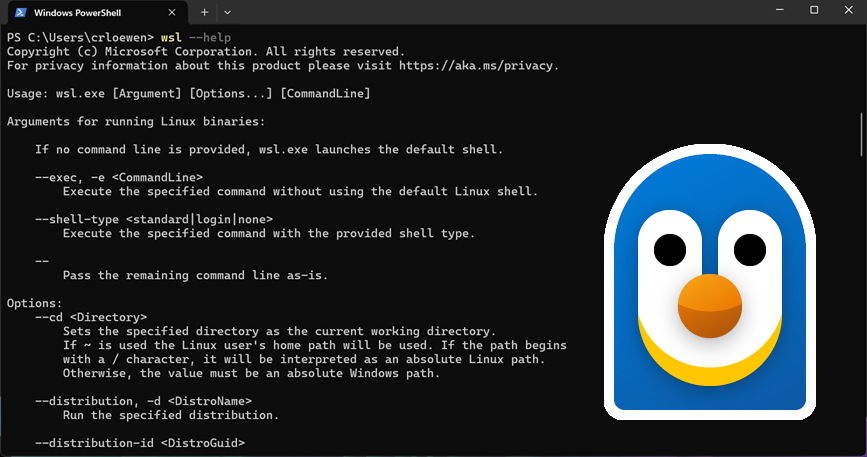
Microsoft open-sources WSL to give developers control over Linux on Windows
Well, it finally happened, folks. Microsoft has open-sourced the Windows Subsystem for Linux (WSL), giving developers full access to its code on GitHub! Yes, after nearly a decade of closed development and repeated requests from the community, the company has handed over the keys -- inviting coders to inspect, improve, and contribute to the very core of how Linux runs on Windows.
This isn’t some half-baked gesture, either. Microsoft has released the core WSL package (the components that power WSL 2) under an open source license. This includes command-line tools like wsl.exe, background services, init processes, networking daemons, and the Plan9-based file sharing system. You can now build WSL from source, fork it, or pitch in directly on GitHub.
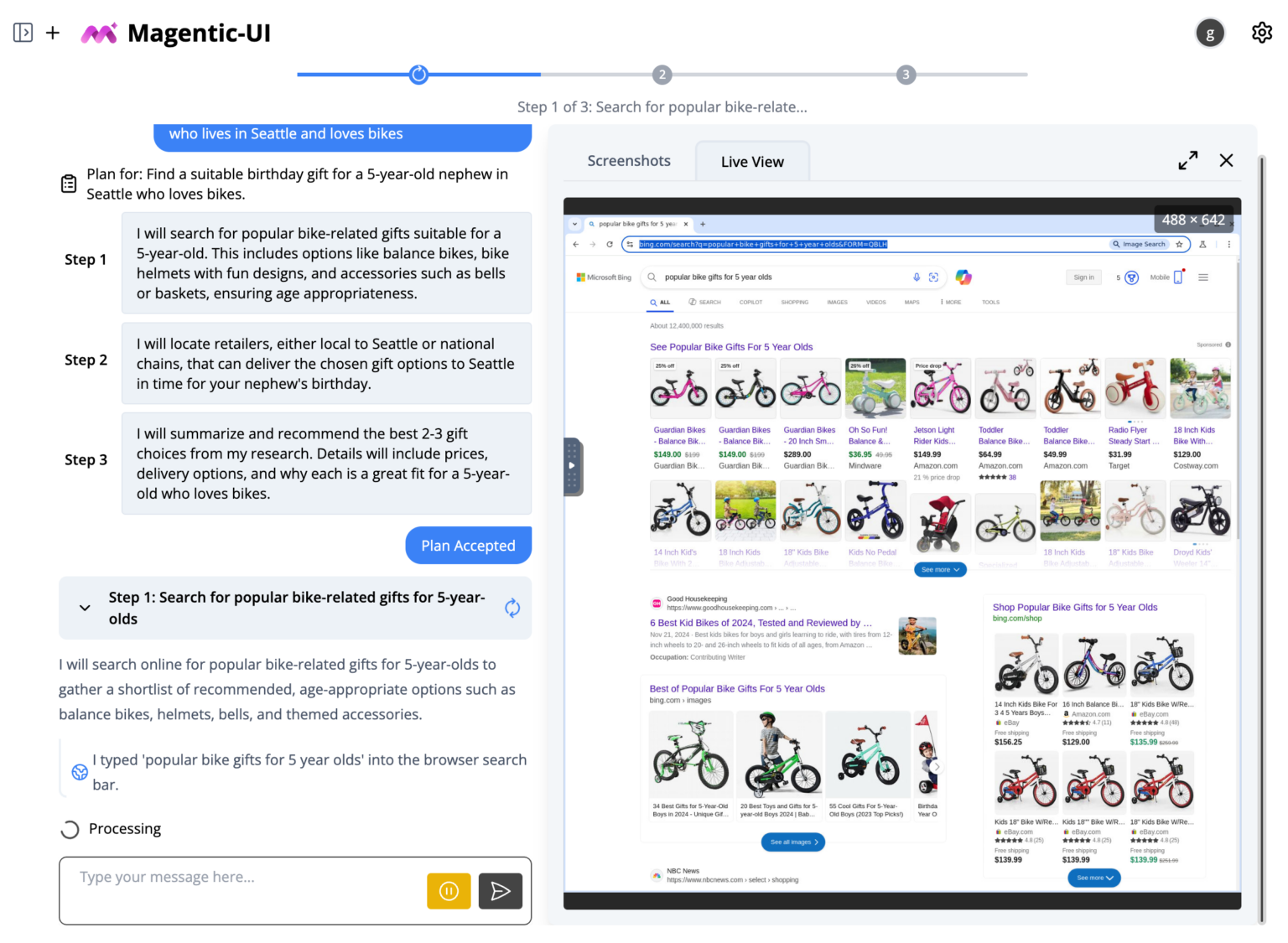
Microsoft Magentic-UI is an open source AI tool that lets humans stay in control
In a world full of AI agents seemingly trying to take control away, Microsoft has done something surprisingly refreshing -- it is handing the wheel back to the user.
With the launch of Magentic-UI, a new open source research prototype, Microsoft is inviting developers and researchers to explore a different kind of AI assistant. One that doesn’t just act on its own, but actually collaborates with people in a transparent, controllable way.

Autonomous AI agents aim to streamline enterprise development
The use of AI in software development can save valuable time completing routine tasks. But what if it could autonomously respond to events, implement changes, and submit code through standard pull requests?
This is what Zencoder is doing with the launch today of Autonomous Zen Agents for CI/CD, bringing groundbreaking AI automation directly into the software development infrastructure.

Docker introduces Hardened Images to boost supply chain security
Security of the enterprise software supply chain isn't solved with buzz or branding. It is solved with trust, scale, and seamless integration into real developer workflows.
To meet everyday software supply chain challenges Docker is launching Docker Hardened Images (DHI), a curated catalog of security-hardened, enterprise-grade container images.

Starburst platform updates boost enterprise AI initiatives
Updates to the Starburst data platform for apps and AI are designed to accelerate enterprise AI initiatives and support the transition to a future-ready data architecture built on a data lakehouse.
At the heart of these changes are Starburst AI Workflows, a purpose-built suite of capabilities that speed AI experimentation to production for enterprises. AI Workflows provides a link between vector-native search, metadata-driven context, and robust governance, all on an open data lakehouse architecture.

Why threat hunting is more vital than ever [Q&A]
The threat landscape is rapidly changing and businesses can no longer simply wait for an attack to be caught by traditional tools or decide how to respond after it occurs.
Mike Mitchell, VP of threat intelligence at Intel 471, has experienced the evolution of threat hunting first-hand as he's been in the industry for decades. We spoke to him to learn more.
Apple is giving macOS users a Magnifier app like iPhone and iPad in a massive accessibility drive
Later this year, Apple says, there is big things in store for accessibility. The company has pre-announced a large number of new tools and features that are coming to a number of its devices. One of the more intriguing is a new Magnifier app for macOS.
On the face of things, this is simply a macOS port of the existing iPhone and iPad app, but there is more to it than that. The app can work in conjunction with an iPhone to function as a loupe or magnifying glass. And this is just one of many accessibility options that are scheduled to roll out; there is also Apple’s Accessibility Nutrition Labels for the App Store.

X uses ‘robustness update’ to improve its flawed Community Notes system
Under a great deal of political pressure to do so, many social media platforms have opted to move away from using fact checking services. X and Facebook are among those to have adopted a “community notes” system that relies on crowd sourcing rather than third party companies.
Such systems have faced criticism because of the potential for manipulation, but these risks have been downplayed by social media firms. But now X has decided to take steps to improve its own Community Notes system to help detect suspicious activity that could be indicative of manipulation attempts.

OWC Thunderbolt 5 Dock features triple 8K display support and 140W charging
If you have a cluttered desktop full of dongles and adapters, OWC might just have your next upgrade. You see, the company has announced its brand-new Thunderbolt 5 Dock, and it’s looking like a an awesome tool for both professionals and home users. For instance, it allows you to connect up to three 8K displays (or two 6K screens on a Mac).
The dock supports Thunderbolt 5, 4, and 3, as well as USB4 and USB-C. So whether you’re using newer gear or hanging on to older devices, it’s got you covered. And with up to 140W of power delivery, it can keep even demanding laptops charged.

Toss Windows 11 in the trash and give Debian Linux 12.11 a try
Debian just got a fresh update with version 12.11, the eleventh point release for “bookworm.” You might be thinking, “How many point releases can one operating system have?” But unlike Windows 11, which can feel like it’s constantly changing things nobody asked for, Debian just quietly gets the job done, one steady release at a time.
This update isn’t a brand-new version, so you don’t need to toss your old installer or start over. Nope, folks, just run your regular updates, and you’ll get the latest security patches and bug fixes. Only new installations will actually require the creation of new media. For that you can grab an ISO here.

Microsoft confirms BitLocker recovery problems after Windows 10 update
Several days after users started to complain that a recent update for Windows 10 was causing them problems, Microsoft has acknowledged that there are issues with the KB5058379 update.
Many people reported the appearance of unexpected BitLocker recovery screens after installing the update on Patch Tuesday, and users were struggling to find commonalities between affected systems. Microsoft has now identified the cause and while it does not yet have a fix, it is “urgently working on a resolution”.



