
Reports that uTorrent silently installs Bitcoin crapware are... crap
Sometimes it's easy to be swayed by what's being written online. At the moment there are lots of stories creeping out about the iPad Pro and Apple Watch, none of which are founded in any fact whatsoever. Still, making stuff up, popping it in quotes and attributing it to an anonymous source is great fun, right?
It may be fun, but it's not really fair on the reader. Another story which popped up on my radar today was about uTorrent -- the popular BitTorrent client that's loved and hated in equal measure. Stories on Trusted Reviews, Engadget and the Verge suggest a Bitcoin mining tool called Epic Scale is installed without permission, and is a tricky blighter to remove. There's an easy way to find out; let's just install it.

Oracle: How about some adware to go with that new Java for Mac?
One of the things I -- and I assume a lot of fellow users -- like about using a Mac is that most OS X programs do not try to trick the user into installing adware. In fact, a lot of the programs I use do not even feature a typical setup, as they can be installed simply by copying them to the Applications folder. For someone coming from Windows, it may feel impossible to grasp at first -- yes, you can actually enjoy the install process. Wow!
Of course, there are developers who do not care about the experience their users have during and after the setup, so they bundle adware with their programs. Thankfully, on Macs it's easier to spot, but it's still something to look out for at times, especially if you wish to install Oracle's latest Java release.
Malware detection in 2014 doubles from 2013 -- 2015 could be even worse
A report from PandaLabs suggests that there were twice as many malware infections in 2014 compared to 2013 -- and China was the hardest hit. Globally, Europe was found to be the area with the lowest rate of infection, and Sweden topped the chart as the safest country. The UK found itself in fourth place with an infection rate of 22.14 percent.
There were certainly plenty of big name security issues throughout 2014. CryptoLocker was just one high-profile example of ransomware, and Trojans continue to be the most common form of infection, accounting for 70 percent of new malware. Viruses tend to be the most commonly known and feared form of infection, but these make up just 12.33 percent of new infections, and a mere 2.7 percent overall.

Yet more aggressive Android adware found on Google Play
Google Play is supposed to be the safe place to download Android apps from, but that’s increasingly not the case. Three weeks ago security firm Avast detailed how it had found three popular Android apps riddled with Adware in Google’s store.
Today Bitdefender reports that it has found ten Google Play apps that are packed with aggressive adware that can do all sorts of nasty things.

Microsoft Malware Protection Center helps take down Ramnit botnet
Ramnit, a botnet that infected millions of computers around the world, has been tamed, thanks in part to Microsoft Malware Protection Center. The takedown operation was a collaboration between Microsoft, Europol, Symantec and others, and it successfully stopped the malware which worked by disabling virus protection before stealing banking details and personal information from infected machines.
With an estimated 3.2 million computers infected globally, Ramnit has been used by cybercriminals the world over, but the majority of infections were found in Britain. The botnet was brought under control by shutting down several servers used by the group responsible for Ramnit.

Your Android device may be spying on you even when it's 'off'
Much is made of the "Android malware problem", but the truth is, there isn't a very bad problem. That does not mean there is no problem though. Visuses for Google's mobile platform do exist and some folks manage to let phones and tablets contract a virus. Now a new and interesting bug seems to be floating around.
According to security software maker AVG this latest malware comes with a unique feature -- it can spy on you when you think your device is shut off. It does so by mimicking the shutdown screen, but not actually powering off the handset.

Worldwide Equation Group hid undetectable spyware on hard drives
In a new twist to the on-going NSA story, security firm Kaspersky Lab has discovered that a threat actor of previously unknown complexity and sophistication has been embedding surveillance software on hard drives produced by a number of well-known manufacturers. With names such as Western Digital, Seagate and Toshiba mentioned, and the reach of the spy program stretching to dozens of countries, it's not clear quite how many people may be affected.
Although Kapersky does not go as far as naming the NSA, or even specifying which country is responsible for the advanced surveillance, it seems that the spying campaign is somehow related to Stuxnet -- the tool used by the NSA to attack Iran -- and the Flame group.

Kaspersky Lab says malware is used to steal millions of dollars from banks
However much money you have flowing through your bank account, you probably take measures to keep it secure. You protect your PIN, you use secure passwords for online banking, and ensure that your computer is free from keyloggers and malware. It's only right that you expect your bank to be similarly eagle-eyed about security... right?
A new report from security firm Kaspersky Lab shows that banks' security is not up to the standard that many would expect. In fact Kaspersky says that sophisticated malware has allowed criminals to help themselves to up to $1 billion. Has your bank been hit? The affected financial institutions are now aware of the attacks, but non-disclosure agreements and on-going investigations prevent them from being named.

Antivirus tools miss almost 70 percent of malware within the first hour
Threat protection company Damballa has released its latest State of Infections report for the fourth quarter of 2014 which highlights the limitations of a prevention-focused approach to security.
The report finds that within the first hour of submission, AV products missed nearly 70 percent of malware. Further, when rescanned to identify malware signatures, only 66 percent were identified after 24 hours, and after seven days the total was 72 percent. It took more than six months for AV products to create signatures for 100 percent of new malicious files.
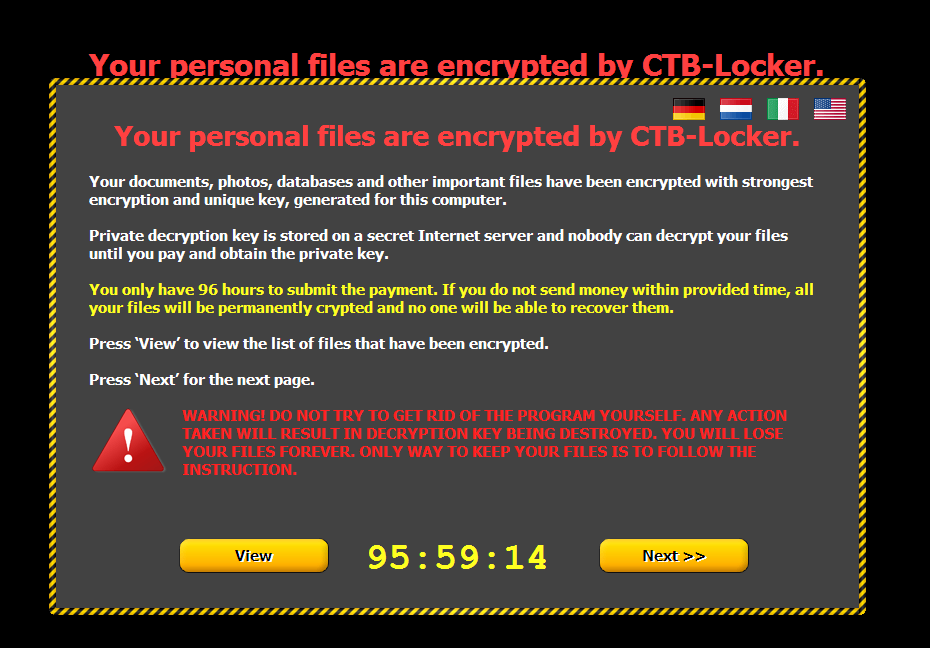
New ransomware is making the rounds via email
The "pay or lose your files" concept of ransomware seems to have taken off with hackers and crime syndicates, becoming the modern cyber equivalent of the mob shakedown. Sort of like paying "protection money".
Now a new ransomware variant has been spotted in the wild, spreading via email, just as previous ones had. The latest is being referred to by the catchy name of Trojan.DownLoad3.35539, and appears in a message as a ZIP file with hopes that unsuspecting recipients will launch it.

2015 -- the year automated malware protection and firewalls become worthless?
Whether you're a home or business user, one thing you've probably had drummed into you for years is the importance of virus protection, an effective firewall and malware guards. Well, as we start our journey into 2015 such security tools may not be anywhere near as effective as they used to be. Is it worth investing in them at all?
The suggestion isn’t that we should ditch firewalls and malware protection altogether -- that would be insanity. But security expert Ilia Kolochenko says that we need to rethink our reliance on automated security tools.

Facebook joins forces with ESET to fight malware for free
As part of an on-going battle against malware and abuse of the social network, Facebook has joined up with security firm ESET. The partnership follows on from the news back in May that Facebook was working with both Trend Micro and F-Secure to try to combat the threat of malware. The addition of ESET makes a trio of security partners, and Facebook has incorporated the company's technology into its own security systems.
Facebook hopes that by combining the power of F-Secure, Trend Micro and ESET, it should be possible to block the appearance of more malicious links from newsfeeds. The thinking is that adding more security providers will helps to catch even more malware without the need to rely on users having antimalware software installed.

Thousands of WordPress, Joomla and Drupal sites threatened by CryptoPHP backdoor
A large proportion of websites are built on a CMS rather than raw HTML. Three of the most common are WordPress, Joomla and Drupal, and security researchers at Fox-It warn that site administrators are at risk of being socially engineered into installing the CryptoPHP backdoor on their server.
Distributed through pirated themes and plugins, CryptoPHP's spread is thanks to the light-fingeredness of site admins. It was first detected in 2013 and is still actively spreading. The capabilities of the "well developed" backdoor include remote control of an infected server, and Blackhat SEO -- a form of illegal search engine optimization.

E-cigarettes can damage your PC's health
Using e-cigarettes, or vaping, is widely touted as being healthier for you than smoking tobacco, however, it may not be so healthy for your PC.
Many e-cigarettes offer a USB charging option but a story on social news site Reddit suggests that this is a potential source of malware attack. An executive's PC became infected after he'd recently given up smoking and the infection was traced to his e-cigarette charger.

Symantec uncovers Regin, a highly advanced stealth spying tool developed by a nation state
Security firm Symantec has released details of an advanced cyberespionage it has discovered. Called Regin, the backdoor Trojan is described as having a structure that "displays a degree of technical competence rarely seen". Symantec goes as far as saying that the levels of resources required to create such a highly advanced tool indicate that it was created by a nation state -- although there is no suggestion about who it might be.
The report says that Regin has already been used in mass surveillance programs not by but against government organizations. Symantec estimates that the tool may have been years in development, as it delivers multi-stage attacks, and great lengths are taken to hide each stage. The framework was designed to facilitate long-term surveillance, and the concealment techniques used make Regin difficult to fully understand.
