
Securing the cloud: Lessons learned from 2023 and what it means for 2024
The global cloud computing market is expanding rapidly and reaching new milestones every year. According to recent data, the market is projected to grow from USD 626.4 billion in 2023 to USD 1,266.4 billion by 2028 at a Compound Annual Growth Rate (CAGR) of 15.1 percent during the forecasted period.
The industry's rapid financial growth is also driving new technological advancements. With this, the dynamic and innovative nature of cloud technology brings new security vulnerabilities and risks, thereby every year increasing the number of malicious incidents. According to the 2023 Thales Cloud Security Study, more than a third (39 percent) of businesses experienced a data breach in their cloud environment last year, an increase from the 35 percent reported in 2022. The leading targets for hackers were Software as a Service (SaaS) applications (38 percent) and cloud-based storage (36 percent).

Online casino security: How to protect your data
The iGaming industry has made leaps and bounds since the days when online casinos were plagued by terrible graphics and slow interfaces. The massive growth in smartphone technology has filtered down to most major online industries and had an amazing effect on their quality.
There are now countless online casinos to choose from and players have an ever-growing selection of games to choose from. However, the thrill of being able to gamble for real money comes with the ever-present risk of data breaches. Here's how to protect your data while still enjoying your favorite online casinos.

The future is now: Advancements in biometric security
Originating in the late 19th century, biometrics has come far from its forensic beginnings to become a key player in today's tech landscape. What started as a tool for crime scene investigation now unlocks our phones and customizes our digital interactions.
This article zeroes in on the latest strides in biometric technology, exploring how these innovations shape various industries and our daily lives, while also addressing privacy and accuracy concerns.

Will Artificial Intelligence power online trading solutions in the future?
Artificial Intelligence (AI) has become a buzzword in various industries and the world of online trading is no exception. With its ability to analyze vast amounts of data and make predictions, AI has the potential to revolutionize the way we trade online. Or maybe that's not the case at all. The point in fact is that AI has been integrated into various systems across numerous different industries already.
However, using AI in the financial market, especially, in trading stocks, bonds, cryptocurrencies and other assets is up to debate. After all, is using AI's machine learning and predictive analysis considered cheating? How is it any different when investors rely on informer insights and leaked documents? The software is just better at processing data than human is.

Get 'Information Security Handbook -- Second Edition' (worth $35.99) for FREE
Information Security Handbook is a practical guide that’ll empower you to take effective actions in securing your organization’s assets.
Whether you are an experienced security professional seeking to refine your skills or someone new to the field looking to build a strong foundation, this book is designed to meet you where you are and guide you toward improving your understanding of information security.

AI and security: It is complicated but it doesn't need to be
AI is growing in popularity and this trend is only set to continue. This is supported by Gartner which states that approximately 80 percent of enterprises will have used generative artificial intelligence (GenAI) application programming interfaces (APIs) or models by 2026. However, AI is a broad and ubiquitous term, and, in many instances, it covers a range of technologies.
Nevertheless, AI presents breakthroughs in the ability to process logic differently which is attracting attention from businesses and consumers alike who are experimenting with various forms of AI today. At the same time, this technology is attracting similar attention from threat actors who are realising that it could be a weakness in a company’s security while it could also be a tool that helps companies to identify these weaknesses and address them.

Microsoft kicks off 2024 by releasing KB5034123 update for Windows 11 adding new lock screen options, security fixes and more
Microsoft has released its first batch of cumulative security updates of 2024, including the KB5034123 update for Windows 11. While the security fixes are a good reason for installing this particular update, there are plenty of other enticements too.
The KB5034123 update addresses various non-security issues including Wi-Fi connectivity problems and a bug that caused Windows to shut down. The update also ushers in new lock screen options thanks to the addition of a "richer weather experience" complete with dynamic, interactive weather updates.

2024 technology advancements in endpoint security
Cybercrime and data breaches have escalated to alarming levels, with the global estimated cost of cybercrime in the cybersecurity market reaching over $8 Trillion in 2023. Projected to rise by an additional $5.7 trillion (+69.94 percent) by 2028, the urgency for advanced endpoint security solutions has never been more apparent.
Cybercrime and data breaches have become some of the most significant threats individuals and organizations face in the modern business world. As technology continually advances, so do the methods employed by cybercriminals to exploit it. As a result, endpoint security solutions have become a vital tool for businesses and individuals seeking to protect their devices and sensitive data from harm.

Don't risk falling behind when it comes to cloud security
Cloud investment is central to staying competitive in modern business. Gartner estimated that global end-user cloud investment reached nearly $600 billion this year and forecasts a 20 percent increase in spending in 2024. But as investment in and reliance on the cloud increases, so must investment in cloud security.
Expanding cloud usage means an expanding attack surface for threat actors to target. Research from Vanson Bourne, commissioned by Illumio, found that nearly half (47 percent) of all security breaches now start in the cloud.

Facing a riskier world: Get ahead of cyberattacks, rather than responding after the fact
Today’s complicated threat landscape leaves security teams grappling with new challenges on a scale never seen. Threat actors are more organized and efficient, leveraging a vast ecosystem of tools and services that cater to experts and beginners alike. In early March, the Cybersecurity and Infrastructure Security Agency (CISA) released an advisory warning of the resurgence of Royal ransomware with new compromise and encryption tactics used to target specific industries, including critical infrastructure, healthcare and education.
Cyberattacks are only increasing and growing more destructive, targeting supply chains, third-party software, and operational technology (OT). Gartner predicts that by 2025, threat actors will weaponize OT environments successfully to cause human casualties. This is happening at a time of increased technology adoption led by accelerated digital transformation efforts, hybrid work and the Industrial Internet of Things (IoT) boom, leaving security teams to manage an evolving and growing attack surface and multiplying vulnerabilities.
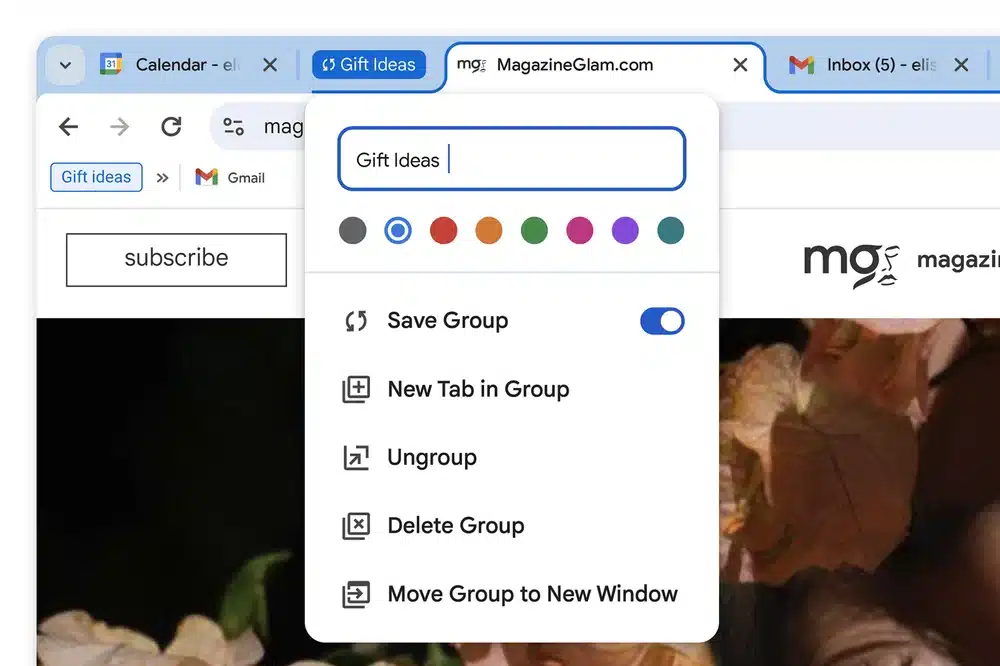
Google gives Chrome security, performance and functionality updates, with the promise of AI-feature in 2024
Google is in the process of rolling out a trio of important updates to Chrome, kicking off with an improvement to Safety Check. This security feature will now run automatically in the background, allowing for proactive alerts about security issues that need attention.
Other updates include improvements to tab groups that makes it possible to access them on other computers, and enhancements to Memory Saver. But the company also hints at big plans for 2024, with the promise of "smarter and more helpful features" powered its Gemini AI model.

Get 'Cyber Threat Intelligence' (worth $87) for FREE
Cyber Threat Intelligence introduces the history, terminology, and techniques to be applied within cyber security, offering an overview of the current state of cyberattacks and stimulating readers to consider their own issues from a threat intelligence point of view. The author takes a systematic, system-agnostic, and holistic view to generating, collecting, and applying threat intelligence.
The text covers the threat environment, malicious attacks, collecting, generating, and applying intelligence and attribution, as well as legal and ethical considerations.

Cybersecurity for SMEs: Seven steps to a Zero Trust approach
Never trust, verify everything! This is the premise on which the "Zero Trust" approach was founded. This model of cybersecurity involves implementing controls designed to ensure that only verified users can access company resources, and from similarly approved devices.
This strategy is increasingly being adopted in response to the challenges faced by small and medium-sized enterprises (SMEs), such as the continued evolution of hybrid working, the use of Bring Your Own Device (BYOD) and the increase and sophistication in cyber-attacks. Whereas previously SMEs thought they weren’t a target, now they are seen as the weaker link from a hackers’ perspective and increasingly they are falling victims to cyber attacks.

Web application security -- five ways to improve your approach
Web applications remain one of the most targeted areas for threat actors. According to Verizon’s Data Breach Investigations Report, web application attacks were behind 26 percent of all successful attacks during the twelve months covered. Yet while the methods for attacking web applications are well known and understood, as evidenced by the work that the Open Web Application Security Project (OWASP) has done on their Top Ten list over the years, many companies still find hardening their applications challenging.
Authorization and access control describe the biggest set of challenges identified by OWASP in their most recent Top 10 list (2021) -- three out of the top five issues were around broken authorization, while broken authentication and improper access to resources were also common problems. The OWASP Top 10 for 2021 also includes attacks that work on unrestricted access to sensitive business flows, which covers areas like creating fake accounts, and server side request forgery where APIs can send resources to the wrong locations.

Open to attack: The risks of open-source software attacks
Open-source software (OSS) is now so widely used that it is incredibly difficult to find an organization that doesn’t incorporate OSS in some form or another -- whether that be in a standalone open-source product, or more commonly, in the form of OSS packages. Though its usefulness cannot be doubted, the prevalence of this software is exactly what makes it a major target for cyber-attacks.
A prime example of this is Log4j, a popular logging utility used by scores of organizations for recording events such as status reports and errors. In a situation which came to be known as 'Log4shell', a zero-day vulnerability allowed threat actors to compromise systems using malicious code and take control all while remaining undetected. At the time, its impact was described as "enormous" and the implications of its implementation into countless commercial products underlined the inherent vulnerabilities of some open-source technologies when weak points are exposed.
