
67 percent of organizations believe hackers can penetrate their network
Around two-thirds of executives and IT professionals responding to a new survey believe that hackers would be able to penetrate their networks.
The study from security and application delivery company Radware focused on global companies and reveals that at least 89 percent of respondents have experienced attacks against web applications or web servers of the past year.

Facebook hack update: Attackers did not use stolen tokens to access other sites and apps
Since the revelation that a "security issue" allowed hackers to steal access tokens to view people's Facebook accounts, the company has provided a further update about the incident. Facebook has already provided one update about the attack, but now the investigation has progressed and the social network is trying to offer reassurances to those who have understandable concerns about security.
The company says that the attackers did not access any apps that make use of Facebook Login, the system that makes it possible to sign into other accounts and services with Facebook credentials.

One in four cyberattacks targets ordinary users
While the majority of cyberattacks are aimed at businesses and other organizations, an increasing number are targeting ordinary users, according to the latest report from Positive Technologies.
The most attractive targets were personal data (30 percent) and credentials (22 percent), especially for online banking. To steal this data, attackers compromised a wide range of websites, including web stores, ticket vendors, and hotel booking services.

Behavioral analysis used to predict cybersecurity threats
Internet of Things security specialist ZitoVault has patented a new means of predicting upcoming cybersecurity events.
While most existing approaches only address the real-time detection of threats or anomalies based on a limited set of pre-established data points, ZitoVault's latest patent uses a new approach.

Financial services breaches triple since 2016
2018 has seen nearly three times as many breaches at financial services organizations as there were in 2016, according to a new report.
The study by cloud access security broker Bitglass finds there have been 103 breaches in this year’s report compared to just 37 two years ago.
Google is trying to make Chrome extensions safer with new Chrome Web Store review process and permission controls
Extensions are a great way to increase the capabilities of your web browser, but they can also be the source of problems. Malicious extensions can be a serious headache, and this is something that Chrome users know more than most. Now Google is looking to improve security.
The company has already promised that with Chrome 70 it is going to give users more privacy controls, and today it announced that this version of the browser will also introduce permission controls extensions. On top of this Google is introducing a new review process for extensions submitted to the Chrome Web Store, as well as placing a ban on extensions with obfuscated code.

Bigger isn't better when it comes to password security
A new study by LogMeIn, the company behind the LastPass password manager shows that size matters in password security, but not in the way that you might think.
Looking at anonymized data from over 43,000 companies, the study produced a security score and a password strength score for each. Businesses with fewer than 25 employees had the highest average security score of 50, but the average drops as company size increases.
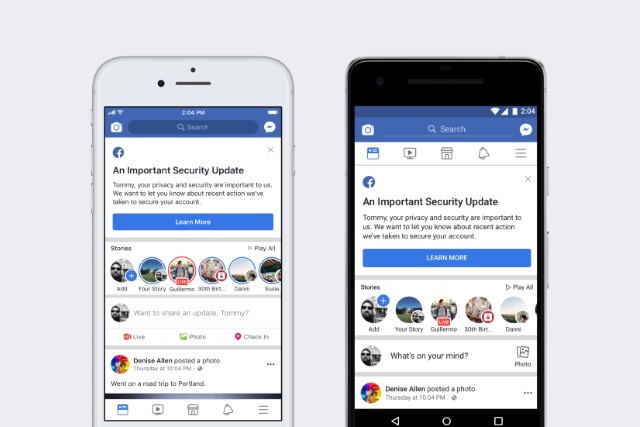
Facebook shares more details about its massive security breach -- after blocking people from sharing news about it
The Guardian was among many outlets to write about the huge Facebook vulnerability and attack reported yesterday, and people were understandably keen to share the story on the social network. However, many people found that they were unable to do.
Large numbers of Facebook users who tried to share the Guardian's story -- as well as one published by the Associated Press -- were greeted by a message informing them that the messages was spam and could not be posted. The matter has been addressed, but it led to complaints that Facebook was trying to hush up the story, and renewed calls to #DeleteFacebook. On its blog, Facebook's security team has also given more details about the "security issue" that happened earlier this week,

Facebook hack: 50 million users affected by site code flaw
Facebook has revealed that it discovered a security issue which could have exposed the accounts of 50 million people.
A vulnerability was discovered in Facebook's View As feature on Tuesday, September 25, but the company has not given too many details about how the flaw was exploited or by whom, but it has said that attackers were able to steal access tokens and access other people's accounts. Law enforcement agencies have been informed, and an investigation is under way.

ESET launches cloud-based security management solution for SMBs
Smaller businesses are not immune to cyber security threats, but they often don't have the budgets or staffing resources to deal with them.
To address this, endpoint security specialist ESET is launching a new cloud-based remote security management solution specifically designed for the IT security challenges faced by SMBs.

Security is developers' top concern for open source components
Developers rate security as their top concern when dealing with open source components, above integration and functionality, according to a new study.
The report from open source security and license compliance management company WhiteSource reveals that an average developer invests 15 hours a month dealing with open source security vulnerabilities, but only a small fraction of that time (25 percent) is devoted to actual remediation.

Schools should offer formal information security classes
Digital threats are evolving fast and that leads to increasing demand for security professionals to tackle them. A new report from AI-driven security company Lastline looks at how existing practitioners feel about education in their field.
Among the findings are that 85.5 percent of infosec professionals believe that US schools should offer more formal classes in the field.

Apple's Device Enrollment Program can leak sensitive information about devices and their owners
Security researchers have discovered an issue with the Device Enrollment Program used by Apple to allow organizations to manage their MacBooks and iPhones. Duo Security says that using nothing more than a serial number, it is possible to gain access to sensitive data about enrolled devices and their owners.
It is even possible to enroll new devices that can then access Wi-Fi passwords, VPN configurations and more. Apple was alerted to the issue way back in May, but has not done anything about it as the company does not regard it as a vulnerability.

The changing network security landscape
The adoption of the cloud and as-a-service delivery models means that the company network, which was once a closed environment, has now expanded into a range of other areas.
Alongside this expansion comes a new range of risks and a new study from cloud-delivered security specialist ProtectWise in conjunction with Osterman Research looks at the latest network security challenges and how they are being met.

Mozilla teams up with Have I Been Pwned to create data breach notification tool, Firefox Monitor
Mozilla has partnered with Troy Hunt -- the brain behind data compromise checking service Have I Been Pwned -- to create its own data breach notification service. Called Firefox Monitor, the free service lets users check if any of their email accounts or personal data have been involved in data breaches.
More than this, Firefox Monitor can also keep an eye out for future data breaches and notify those who have signed up whether their data has been affected.
