YouTube creators hit by 'Microstopped' take down requests -- Microsoft already fixing it

Creating content for YouTube is actually very hard and takes a long time to edit and upload. Even a simple-looking unboxing video can take hours from start to finish -- sometimes longer if you cut yourself opening the box and have to treat a wound. It is very disappointing to have your content removed for copyright issues, when you haven't actually violated anything. Even worse, it can be an impossibility to successfully dispute the bogus claim.
Today, many YouTube content creators were inconvenienced and upset by take down requests from an apparently overzealous company called "Marketly", acting on Microsoft's behalf. You see, all of the videos were Windows related, but not all of the removals were warranted. Of course, like all controversies, it has already been given a name and hashtag of #Microstopped.
Is Microsoft trying to confuse users by having Bing look like Google?
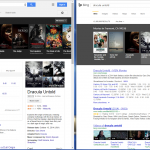
Microsoft has been tweaking Bing's design for a while now. The latest design makes it seem that it wants Bing to be indistinguishable from Google. If you have Bing as the default on your browser (or accidentally clicked a Microsoft prompt to do so), and are not very tech-savvy, you may not even realize that you're using Bing -- especially if you think any type of internet search is "Googling."
Notice how each have a minimalist search bar at the top with options for different searches at the bottom with "Web" highlighted with a colored bar.
Google releases hilarious Android 5.0 teaser video -- there can only be one L

A company's "cool-factor" can vary wildly, but one has not yet lost its magic -- Google. Sure, privacy advocates decry the search-giant's long reach into the lives of many, but that is what makes the company's products so endearing -- Google needs that data to know you. It is the customized and tailored experiences that create a bond between the user and Google.
The biggest bond, however, is Android; the mobile operating system has been wildly popular, bringing Linux to a user base that no one thought possible. People are fans of Android, unlike any other operating system before it. Hell, people collect plastic figures of the mascot; that is dedication. We should soon be experiencing the final version of Android 5.0, which will have an "L" code name. Will it be lollipop? Lemon meringue? Well, today Google releases a cool video, which has fun with the Android 5.0 name.
Security firms have created the next dot com bubble by 'scaring their customers'

There are too many security firms offering insufficient security. At least that's what Ilia Kolochenko, CEO and founder of High-Tech Bridge thinks. He points to the splitting of Symantec as proof that security companies are struggling, and suggests that the emergence of so many firms competing for attention is the start of a new dot com bubble that could burst at any moment.
Security is important to both home computer users and enterprise businesses. There is a huge amount of money to be made in the field, so it is perhaps little wonder that the number of companies muscling in on the market is on the increase. Kolochenko says that at the end of the century a lot of tech companies sprang up overnight and "most of these businesses were designed to create artificial problems or boost non-existent demand in order to make quick money. They didn't actually solve any real problems". There is a danger that the same could happen in the security world.
Google says American teens love voice search -- some use it in the bathroom

Google voice search is awesome; I use it every day in the car or at home. If I want to know the weather, I just ask and it tells me. It helps me find the phone numbers for my favorite pizzerias and Chinese food restaurants, and when I am lost, I just say "take me home" and it does!
Like I said, it is awesome, but apparently, teens are using it more than adults. According to a new Google study, 55 percent of teens in the USA are using voice search; these young people are often the barometers of the next big thing. The search giant should be elated that this important demographic is embracing voice search; however, the study does not only include Google, but also Apple's Siri and Microsoft's Cortana.
Yovo: Snapchat plus screenshot protection

If you’d like to share personal photos, but only briefly, then a service like SnapShot can help. Images are visible for only a set period of time before they disappear forever. (In theory, anyway.)
Yovo for iOS is based around the same idea. Take an image, add a caption or blur, set an expiry time and select your recipients. But it also includes "D-fence", a clever technology which prevents users taking clear screenshots.
Public cloud security flaws: who’s viewing your files?

Secure cloud storage is a challenge facing many professionals today, especially small and mid-sized businesses. It’s clear that the cloud is going to stick around for a long time, and so everyone is looking for a way to get on board with it while still protecting their professional data.
But, the unfortunate truth about public cloud storage is that you can’t control who handles your data or how it is protected. If you choose the wrong service, your company files are exposed to the dangers of hackers, data leaks, seizure, and nosy cloud employees. It’s difficult to know who is looking at your data, but if you know the risks and costs that come with different services and cloud functions, you can better protect your privacy.
Organizations struggle to balance security with systems integration

Many organizations are failing to meet data security and governance requirements according to a new Ovum survey sponsored by data flow specialist Axway.
The results reveal that 23 percent have failed a security audit in the past three years and 17 percent lack confidence in their ability to pass one today. It also puts the average cost of a data breach at $350 per record.
SyncBack 7 adds cloud backup support

2BrightSparks has unveiled SyncBackSE 7 ($39.95) and SyncBackPro 7 ($54.95), a major update for its powerful backup and file sync application.
The Pro build now supports cloud backup to Dropbox, OneDrive, Google Drive, Box, and Glacier via S3.
Vertu unveils new smartphone for Bentley owners and enthusiasts

Most people who own expensive smartphones have the latest Apple iPhone, Samsung Galaxy S or Galaxy Note device, which, at launch, costs at least $650 off-contract. Even though they are unattainable to the average buyer, tens of millions of consumers can still afford to get them. And that creates a problem for the elitist one percenters of the world, who are faced with an unusual dilemma: own a smartphone that even their chauffeurs may afford or turn to a proper luxury device.
For those who can pay €12,500 for a smartphone and just so happen to be Bentley owners or enthusiasts, renowned luxury smartphone manufacturer Vertu has unveiled Vertu for Bentley. It is the first device to come out of the new five-year partnership with the high-end British car maker. Luckily, for that much money, it certainly is special.
Why hackers love the holiday season [Q&A]

Recent high profile security breaches involving retailers like Target and Neiman Marcus mean that people are increasingly aware they may be vulnerable when shopping online. Yet many don't fully understand the landscape that lies behind hacking and why it’s such a lucrative business.
With Christmas and its associated e-commerce peak fast approaching we spoke to Kelly Yee, Vice President of secure email provider Penango who has a wealth of security systems experience in both the public and private sectors. Here are her views on how hackers work and how we can guard against becoming victims over the holiday season.
Apple iPhone 6 Plus: Beautifully made, but expensive [Review]

Here it is, then, the iPhone 6 Plus. Apple's biggest handset to date, and a competitor for all those phablets that some people swear are the perfect device for them. It's big, it's bold, it's beautifully made. Does it do enough to justify its exorbitant price? My review sample came from Three in the UK, from whom you can get the iPhone 6 Plus in any of its three colors -- gold, silver or gray -- in its 16GB variant starting from £44 a month. At that price there's a £99 up-front price for the handset.
Other operators also sell it, of course, and if you want to go SIM free you are looking at £619/$749 for the 16GB version, £699/$849 for the 64GB and £789/$949 for the 128GB. That's a lot of money, and there are plenty of other large-screened handsets that will cost you much less.
Dropbox passwords held to ransom after third-party leak

Hackers claim to have stolen the login details of almost seven million Dropbox users. Having released a teaser file on Pastebin with details of around 400 accounts they’re offering to release more in exchange for a Bitcoin ransom.
Like the Snapchat photo leak it seems that this information has come from insecure third-party services rather than from Dropbox itself.
Firefox 33 reveals performance tweaks, search improvements, more robust session restore
Mozilla has released Firefox 33.0 FINAL for desktop, with Firefox for Android 33.0 due to follow in the coming days.
Like the previous release, the desktop build of Firefox 33 boasts no major new features, but its Android counterpart gains vastly improved tab management tools as well as the ability to send videos to both Chromecast and Roku devices.
Malwarebytes Anti-Malware improves multitasking, adds keyboard navigation support

Malwarebytes Corporation has released Malwarebytes Anti-Malware 2.03, a significant update for its anti-malware tool.
A new option to run scans at a lower priority (Settings > Advanced Settings > "Reduce priority…") may reduce their impact on other applications. This is a good idea in principle, although we noticed it had no effect whatsoever on our test system, with both process and I/O priorities remained stubbornly unchanged.
Most Commented Stories
© 1998-2025 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.




