Poor architecture documentation leads to project delays and security risks

Although 63 percent of organizations claim their architecture is integrated throughout development (from design to deployment and beyond), a new study shows more than half (56 percent) have documentation that doesn't match the architecture in production.
The research from vFunction shows the impact of this architecture disconnect has potentially resulted in project delays (53 percent), security or compliance challenges (50 percent), scalability limitations (46 percent), and reduced engineering team productivity (28 percent).
FastStone Image Viewer 8.0 is the free photo toolkit your PC needs -- download it now

Canadian developer FastStone Software has released Faststone Image Viewer 8.0, a major new release of its powerful -- and free for personal and non-commercial use -- image toolkit for Windows PCs.
Despite the name, FastStone Image Viewer is more than just a simple tool for viewing images. Users can view multiple files courtesy of its two-pane File Explorer interface, with the ability to view a folder full of images as a slideshow, complete with access to detailed file properties (including EXIF data).
Compliance is a major obstacle to data management strategies

A new survey of nearly 1,500 IT, engineering, and cybersecurity professionals worldwide reveals that 69 percent say maintaining data security and compliance is a top data management obstacle.
Not far behind is managing data volume and growth, cited by 67 percent. The research from Splunk shows 62 percent of respondents claim that difficulties with data management resulted in compliance failures.
67 percent of organizations report a rise in identity-based incidents

New research highlights the growing threat of identity-based attacks and looks at organizations ability to defend against them.
The study from Huntress shows 67 percent of organizations reported an increase in identity-based incidents over the past three years, with these attacks comprising more than 40 percent of security incidents for 35 percent of organizations in the past year alone.
Would you trust a robot lawyer?

A new survey for Robin AI reveals that while nearly one in three people would be open to letting a robot lawyer represent them in court, the vast majority would only do so if a human lawyer was overseeing the process.
The research carried out by Perspectus Global polled a sample of 4,152 people across the US and UK and finds that on average, respondents say they would need a 57 percent discount to choose an AI lawyer over a human.
Meta is promoting Threads by pestering users to cross-post to Instagram

Remember Threads? Meta’s most recent foray into social media caused something of a splash when it first emerged, but it quickly became just another platform. Seemingly worried that not enough people are using it, Meta is now using Instagram as a way of pushing Threads usage.
While Meta has said nothing about it in any form of announcement, existing Threads users have started to notice that they are being prompted to cross-post content to Instagram. The hope, presumably, is that Instagram users yet to try out Threads will be tempted into doing so.
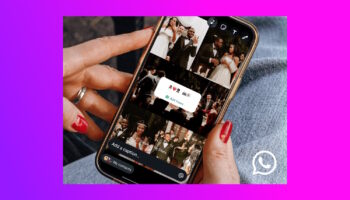
WhatsApp on the web is getting voice and video calling

Although WhatsApp is primarily seen as a mobile app -- which makes sense, as accounts are linked to a phone number -- the web client is also an excellent part of the family. The web-based version of WhatsApp has evolved and progressed impressively, but there remain areas in which it is found wanting.
A key example is the lack of support for placing voice or video calls from the WhatsApp web client -- but this is set to change.
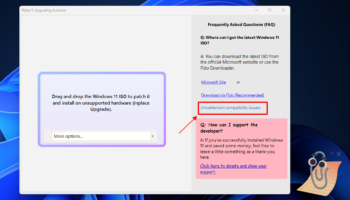
Microsoft will start charging for Windows Server hotpatch updates in two months

The arrival of hotpatch updates for Windows Server 2025 heralded a new era of keeping systems up-to-date and secure while keeping downtime to an absolute minimum. By eliminating the need for restarts after certain updates, systems can be patched while they are being used.
Hotpatching for Windows Server 2025 has been available in preview for a number of months now. It has been completely free of charge, but this is due to come to an end. Anyone who has fallen in love with the new approach will have to pay if they want to continue using it.
Kali Linux users warned that updates are likely to fail for a few days

Showing that it is not just Windows 11 that has issues with updates, Offensive Security has issued a warning that Kali Linux updates are likely to fail “in the coming days”.
The Linux distro has proved an important tool in penetration testing, acting as a valuable security tool for many users. The team behind Kali Linux says that “pretty much every Kali system out there will fail to update”, and it bears full responsibility: “This is not only you, this is for everyone, and this is entirely our fault”. But there is a solution.
Install 4MLinux 48.0 to breathe new life into your old computer
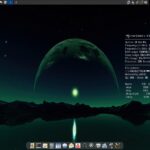
Let’s be honest, y’all -- it is pretty easy to feel overwhelmed by everything going on these days. Bad news seems to hit from every direction, leaving many people feeling helpless or anxious. But believe it or not, there is a simple, satisfying way to take back a little bit of control -- by breathing new life into an old computer with a refreshing Linux distribution such as 4MLinux.
You see, the new 4MLinux 48.0 series has officially been declared stable (download here), and it brings a whole lot to the table for such a lightweight operating system. Whether you want to write documents in LibreOffice 25.2 or GNOME Office (featuring AbiWord 3.0.5, GIMP 2.10.38, and Gnumeric 1.12.59), this little distro has you covered. Browsing the web is easy too, with both Firefox 137.0 and Chrome 135.0 ready to roll. Thunderbird 128.9 is there if you still prefer handling email the old-fashioned way.
Almost a quarter of HTML email attachments are malicious

When used legitimately, HTML attachments in emails enable organizations to share content, such as newsletters or invitations, that display properly when opened in an email client or web browser.
But a new report from Barracuda reveals that 23 percent of HTML attachments are malicious, making them the most weaponized text file type. Overall more than three-quarters of the malicious files detected overall were HTML, and 24 percent of email messages overall are now unwanted or malicious spam.
Mobile becomes the preferred route for attacks on enterprises

Mobile threats are no longer an emerging issue, they're here, rapidly evolving, and targeting the devices organizations depend on every day.
As employees use smartphones, laptops, and tablets to access sensitive data and systems, a new report from Zimperium zLabs shows attackers are increasingly exploiting these endpoints through mobile-first strategies that bypass traditional security defenses.
AI is challenging organizations to rethink cyber resilience

A new report from managed security services company LevelBlue reveals that organizations are forging ahead with AI innovations despite increased security concerns.
The report shows AI-powered attacks, such as deepfakes and synthetic identity attacks, are expected to rise in 2025, but many remain unprepared. The report finds that only 29 percent of executives say they are prepared for AI-powered threats, despite nearly half (42 percent) believing they will happen.
Winhance 4 transforms Microsoft Windows 11 (and Windows 10) into the bloat-free, faster operating system you need [Update]

The lukewarm reception to Windows 11 is clear from the wave of third-party tools built to fix it. One of the most recent is Crapfixer Rebirth Version, a utility that’s been around for about seven years (although it looks older), which has now been given a full refresh.
Winhance is another tool you’ll definitely be interested in. It can debloat and optimize Windows -- and keep it that way. Although it’s been designed for Windows 11 it works just fine on Windows 10. Winhance was originally a PowerShell GUI application, but version 4 is a standalone app that can be installed or uninstalled easily, and it also comes in a portable version, so there's no reason not to get started with it today.
The new role of behavioral biometrics in fraud prevention

Digital security is undergoing profound transformations catalyzed by the shortcomings of traditional authentication methods. Security strategies often force businesses to choose between robust defenses that frustrate users and seamless experiences that heighten vulnerability. Recently, behavioral biometrics -- using unique users’ digital interaction patterns -- has emerged to offer a compelling resolution to this longstanding challenge by providing continuous, invisible authentication based on unique human behaviors.
Behavioral biometrics can best be understood as digital body language. Like physical mannerisms, such as walking gait or vocal tone, users exhibit distinctive digital behaviors in interacting with their devices -- from typing rhythms and mouse trajectories to touchscreen pressures and even how devices are held. Behavioral biometrics captures and analyses these subtle distinctions to establish a unique digital fingerprint that fraudsters -- and their machinations -- find nearly impossible to replicate. By integrating behavioral biometrics into security and anti-fraud frameworks, organizations can attain a sophisticated balance between strong, proactive fraud postures and the frictionless user experiences that modern consumers expect.
Most Commented Stories
© 1998-2025 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.