
Will Linux Mint 20.3 'Una' make 2022 the fabled 'Year of Linux on the Desktop?'
Will Linux Mint 20.3 make 2022 the fabled "Year of Linux on the Desktop?" Absolutely not. However, that won't stop some fans of the Ubuntu-based operating system from making that prediction. While it won't dethrone Windows anytime soon, the release of a stable Linux Mint 20.3 is imminent.
You see, today, the Linux Mint developers share that version 20.3 of the operating system will be released this week! Sadly, the devs missed the Christmas 2021 deadline they previously shared -- a major disappointment. Oh well, users simply had more time to play with the Beta release. At least the wait for Linux Mint 20.3 -- code-named "Una" -- will be over soon.

Maintaining migration success: Pre-migration tips for moving Teams data
As our world grows increasingly digital, the importance of an effective virtual workplace becomes a greater priority for businesses everywhere. With many companies relying on remote workforces, tools like Microsoft Teams have become critical to enabling collaboration and engagement among remote employees. As a result, Teams adoption has skyrocketed. In July 2021, Microsoft reported 250 million monthly active users on Teams.
As corporations continue to leverage cloud-based solutions to enable remote work, the need to keep their digital environments secure and organized remains vital.
You can now give your Linux desktop a Windows 11-style 'Fluent' makeover
Windows 11 is far from perfect -- it’s still very early days for the new operating system after all -- but it sports an attractive, modern aesthetic thanks to the use of Microsoft’s Fluent Design System.
If you like the look of Windows 11, but prefer to use a Linux OS, you can now get the best of both worlds by applying a new 'Fluent' icon set.

Machine learning implemented by 68 percent of organizations
New research shows that 68 percent of chief technical officers (CTOs) have implemented machine learning at their company.
What's more the study, from software development company STX Next, reveals that 55 percent of businesses now employ at least one team member dedicated to AI/ML solutions, although only 15 percent have their own separate AI division.

Plugable UD-6950PDZ USB-C Triple 4K Docking Station has 3 HDMI and 3 DisplayPort video outputs
USB-C docking stations are a dime a dozen these days. There are so many on the market, it can be hard to get excited about new models. For one to stand out in the crowd, it has to be exceptional or offer functionality to make it special.
Well, folks, it seems Plugable has managed to announce a USB-C docking station that is legitimately exciting. Called "UD-6950PDZ," it supports up to three monitors running at 4K. While that is cool, it is not what makes it so special. Actually, the truly cool aspect is that it has six video outputs -- three HDMI and three DisplayPort. Only three of the six can be used at once, but by offering six ports, you can connect to three monitors using HDMI or DisplayPort without ever needing a dongle.
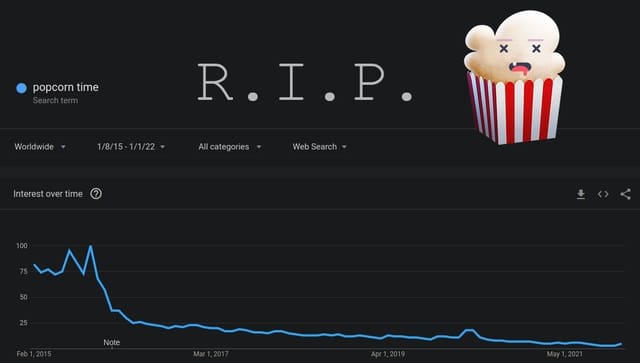
RIP Popcorn Time -- 'Netflix of piracy' is no more
There are many names associated with piracy, some old -- think of Kazaa and Limewire -- others more current -- such as the Pirate Bay and endless sites of its ilk. One of the most recent phenomena in the world of piracy has been sites that offer movies and TV shows to stream.
One of the biggest sites of this type is Popcorn Time… or at least it was. The site dubbed the "Netflix of piracy" has passed on, it has ceased to be, it has expired and gone to meet its maker. Popcorn Time is an ex-site. It is dead.

What value does Extended Detection and Response (XDR) bring to the cybersecurity market? [Q&A]
As organizations adapt to hybrid working models and modernize business practices, so too must cybersecurity programs.
We talked to Rupesh Chokshi, VP at AT&T Cybersecurity, to discuss key challenges and how XDR is becoming an important framework, helping organizations consolidate and improve security operations across the entire network, from endpoints to the cloud and beyond.

Get 'Business Writing For Dummies, 3rd Edition' ($15 value) FREE for a limited time
Do you wish you could write better? In today’s business world, good writing is key to success in just about every endeavor. Writing is how you connect with colleagues, supervisors, clients, partners, employees, and people you’ve never met. No wonder strong writers win the jobs, promotions and contracts.
Business Writing For Dummies shows you, from the ground up, how to create persuasive messages with the right content and language every time -- messages your readers will understand and act on.

Microsoft releases emergency KB5010196 and KB5010215 updates to fix serious remote desktop problems in Windows Server
Microsoft has issued an out-of-band update for Windows Server to address a problem with Remote Desktop that can prevent connections to a server.
There are two different updates available at the moment -- KB5010196 for Windows Server 2019, and KB5010215 for Windows Server 2012 R2 -- and Microsoft says that updates will be released for other affected platforms "in the coming days". As these are emergency, out-of-band updates, they are not currently available from Windows Update, and must instead be installed manually.

Linksys launches Hydra Pro 6 (MR5500) Dual-Band AX5400 Mesh Wi-Fi 6 Router
Wi-Fi 6 (802.11ax) used to be the future of wireless connectivity, but nowadays, it is the present. Yes, with more and more devices having Wi-Fi 6, now is the time to buy such a router if you haven't already. Look, with many of us spending more time at home nowadays -- including for work -- we all deserve to have a high-quality router, right?
Today, Linksys unveils its latest wireless router, and it is quite cute and stylish. Called "Hydra Pro 6" it supports Wi-Fi 6 and has a USB-A port on the rear for connecting a USB storage device. In other words, the router (SKU: MR5500) can pull double-duty as a makeshift NAS. Best of all, it has mesh support baked in, so you can set up a mesh network using other compatible Linksys products.
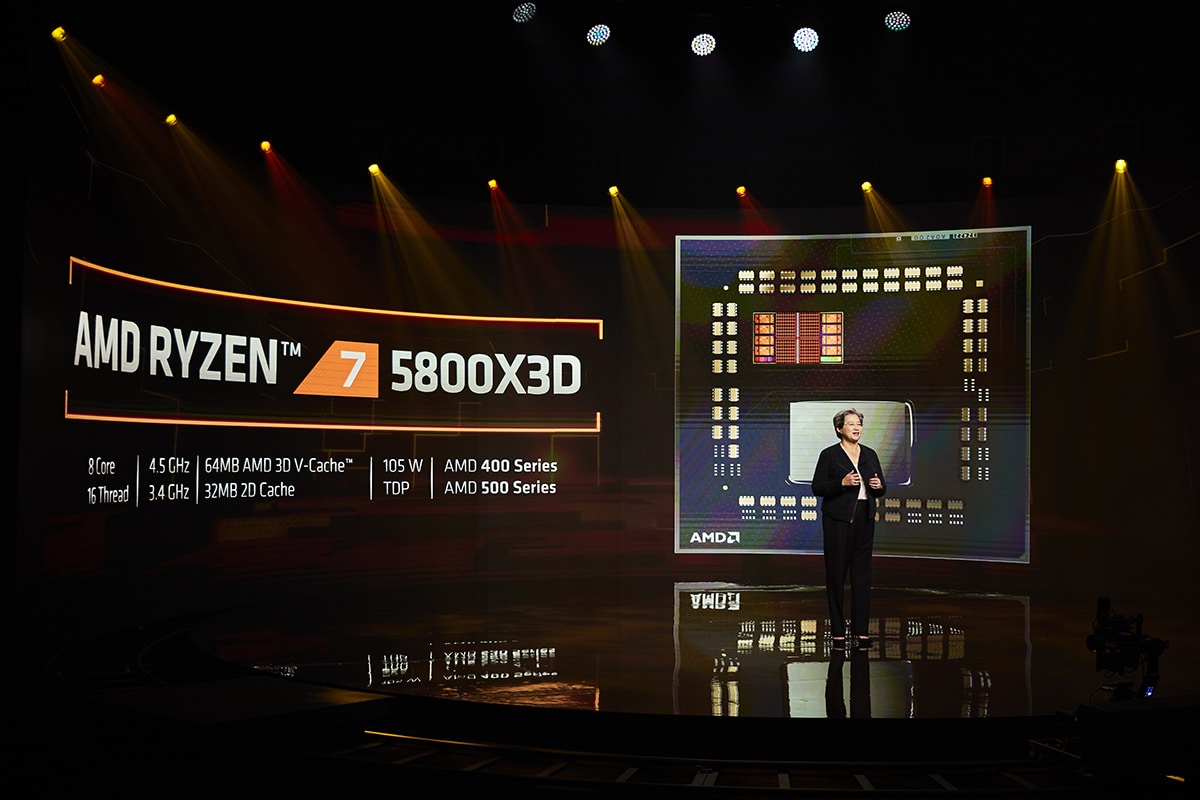
AMD announces 30 powerful new Ryzen and Radeon products for notebook and desktop PCs
The start of the new year is when most big hardware companies take the wraps off new and future products.
Today, at a Product Premiere livestream event, AMD President and CEO Dr. Lisa Su (and the AMD executive team) showed off over 30 new products, including the Ryzen 7 5800X3D desktop processor -- the first consumer PC processor to feature 3D-stacked chiplets to deliver a major boost in gaming performance.

OWC Atlas FXR is the world's smallest Thunderbolt CFexpress card reader
Do photographers and videographers still use SD cards? Yes. In fact, I would guess that most do. However, the writing is on the wall, and the faster CFexpress Type B memory cards are obviously the future. Those with cutting-edge camera equipment are already enjoying the benefits of these superior cards.
The problem? Most computers, including the newest MacBook Pro laptops, do not come with integrated readers for these cards. And so, consumers must invest in external readers. Today, OWC unveils what it says is the "smallest Thunderbolt CFexpress card reader." Called "Atlas FXR," it connects using Thunderbolt 3/4 to provide insane speeds. It is also compatible with USB-C and comes with a USB-A adapter. In addition, the company is releasing its own line of CFexpress Type B memory cards called "Atlas Pro" and "Atlas Pro Ultra."

Pssst... Wanna buy a dead BlackBerry?
Online searches for 'Sell BlackBerry' rocketed 1,528 percent today as the company announced it would be ending support for the operating system used on its phones.
Analysis by VpnOverview shows interest in selling Blackberry phones is 16 times the daily average. Searches on Google for 'BlackBerry phones' were also up 590 percent.
Turn the Windows 11 taskbar into a macOS-style dock
Windows 11's centered taskbar isn’t for everyone, and it lacks many of the customization options we’re used to (although Microsoft promises these missing features are on their way).
Thankfully there are some third-party tools which can change the look and behavior of the taskbar.

EdgeDeflector alternative MSEdgeRedirect now redirects more content to your default browser
Microsoft has been quite aggressive in pushing its Edge browser, raising the hackles of many Windows users by ignoring default browser settings. The company's approach means that regardless of which web browser is set as default in Windows 10 and Windows 11, certain types of web content will always open in Edge.
The links of EdgeDeflector and similar tools popped up to intercept such links – such as clicking links in the News widget in Windows 11 – and force them to open in the default browser, but Microsoft has been busily trying to block such activity. One tool that continue to work is MSEdgeRedirect, and it has just been updated to make it even more useful.
