
Lexar launches NQ780 and NM1090 PRO SSDs with blazing speeds for gamers and creative pros
Lexar is looking to shake up the solid state drive market with the debut of two new high-performance NVMe SSDs. The company has released the NQ780 PCIe 4.0 SSD and the Professional NM1090 PRO PCIe 5.0 SSD, both aimed at gamers, content creators, and anyone who demands fast storage. Even better, both drives are available for purchase on Amazon right now.
The NM1090 PRO stands out as the flagship option, pushing PCIe Gen 5 storage to impressive new heights. Depending on which capacity you choose, this SSD can hit read speeds up to 14,000MB/s and write speeds up to 13,000MB/s. The 2TB and 4TB models both offer up to 2100K IOPS for random reads, while random write speeds can reach as high as 1800K IOPS. Even the 1TB model holds its own with 14,000MB/s reads and 10,000MB/s writes. It’s built using a 6nm controller to help keep heat in check and performance stable.

Google reveals ZAPBench to predict brain activity in zebrafish and unlock new AI-powered neuroscience research
If we are lucky, Artificial intelligence might one day help scientists understand the human brain the same way language models predict the next word in a sentence. And now, that future is closer to becoming reality thanks to a new project from Google Research, Harvard University, and HHMI Janelia. You see, these teams have introduced the Zebrafish Activity Prediction Benchmark, better known as “ZAPBench,” which could help researchers create more accurate models for predicting brain activity.
ZAPBench isn’t just another dataset, folks. Actually, this new tool is based on two hours of brain recordings from larval zebrafish, capturing how roughly 70,000 neurons fired in response to different virtual reality scenarios. These tiny fish were shown various environmental changes, including shifting light patterns and moving water currents, while researchers recorded brain activity at an impressively detailed scale.

New Qualys tool aims to streamline enterprise compliance audits
Enterprises are grappling with an increasing compliance burden, subject to multiple frameworks and more regulatory mandates that stretch resources and drive-up costs.
Misconfigurations can further complicate things, often leading to non-compliance and regulatory penalties. Plus time-consuming tasks like auditing, reporting, and system remediation are prone to human error.

Crisis in 'digital dexterity' threatens AI investments
A new study shows that 92 percent of IT leaders believe the new era of digital transformation will increase digital friction and that less than half (47 percent) of employees have the requisite digital dexterity to adapt to technological changes.
The report from digital employee experience (DEX) specialist Nexthink, based on a survey of 1,100 IT decision makers worldwide, shows a further 88 percent expect workers to be daunted by new technologies such as generative AI.

Popular LLMs produce insecure code by default
A new study from Backslash Security looks at seven current versions of OpenAI's GPT, Anthropic's Claude and Google's Gemini to test the influence varying prompting techniques have on their ability to produce secure code.
Three tiers of prompting techniques, ranging from 'naive' to 'comprehensive,' were used to generate code for everyday use cases. Code output was measured by its resilience against 10 Common Weakness Enumeration (CWE) use cases. The results show that although secure code output success rises with prompt sophistication all LLMs generally produced insecure code by default.
O&O DiskImage 21 Premium Edition provides Windows home users with a comprehensive backup suite
Berlin-based O&O Software GmbH has unveiled a major new release -- and edition -- of its backup software for Windows. O&O DiskImage 21 Premium is a new entry into the DiskImage family, aimed firmly at home users.
The application, which can back up everything from individual files to entire drives, is relaunched with a brand new interface as well as several new features. As with previous releases, the app is sold with a lifetime license as opposed to a time-limited subscription.

Detectify improves app security testing with intelligent recommendations
Security teams know they need to test their main applications, but they often struggle to identify which other assets to cover. On average, organizations can miss testing nine out of 10 of their complex web apps.
Security testing platform Detectify is announcing the launch of its new Asset Classification and Scan Recommendations capabilities which enable organizations to easily identify and swiftly act on their complex web applications.

Hackers can now bypass Linux security thanks to terrifying new Curing rootkit
Most Linux users assume their security tools will catch bad actors before damage is done -- but sadly, new research suggests that confidence may be misplaced. You see, ARMO, the company behind Kubescape, has uncovered what could be one of the biggest blind spots in Linux security today. The company has released a working rootkit called “Curing” that uses io_uring, a feature built into the Linux kernel, to stealthily perform malicious activities without being caught by many of the detection solutions currently on the market.
At the heart of the issue is the heavy reliance on monitoring system calls, which has become the go-to method for many cybersecurity vendors. The problem? Attackers can completely sidestep these monitored calls by leaning on io_uring instead. This clever method could let bad actors quietly make network connections or tamper with files without triggering the usual alarms.

Half of security issues in Agentic AI code are API-related
A new report from API and AI security solutions company Wallarm finds that of around 4,700 security issues analyzed in Agentic AI projects, 49 percent were API-related, underscoring the inseparable nature of agent and API security.
The report also finds that over 1,000 issues in Agentic AI repositories remain unaddressed. 22 percent of reported security issues remain open too, with some lingering for 1,200-plus days, highlighting a critical gap between vulnerability discovery and remediation.
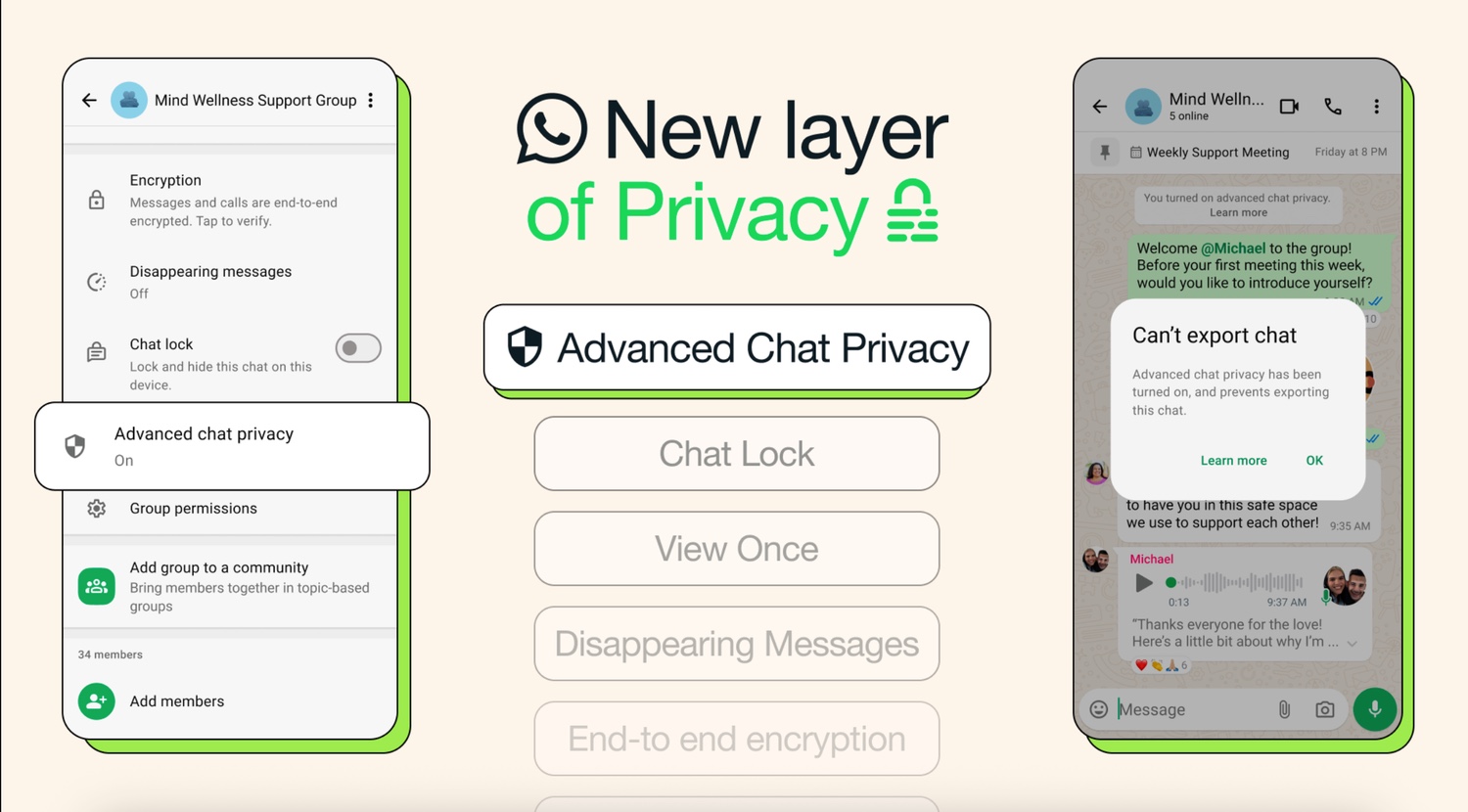
Your WhatsApp conversations have just been made much more secure thanks to the new Advanced Chat Privacy
There are lots of privacy and security features built into WhatsApp, but there have been a few oversights. Looking to remedy this, a new “privacy layer” called Advanced Chat Privacy provides powerful options.
The feature has been designed with those conversations that need to be kept private in mind. It gives the option of blocking anyone you are chatting to -- one-on-one or in a group -- from exporting chats. It’s a nice security boost, but it’s not infallible.

Roku reveals its own battery-powered smart home cameras with TV integration
Roku is going in a new direction with its latest smart home products, stepping away from the rebadged Wyze cameras it offered in the past. This time, the company is rolling out security cameras designed entirely in-house. The new Roku Battery Camera and Roku Battery Camera Plus promise easier installation, longer battery life, and deep integration with the Roku ecosystem.
These weather-resistant cameras are built to work indoors or outdoors, and because they run on rechargeable batteries, there’s no need to mess around with power cables. Roku also plans to offer a solar panel accessory, giving users the option to keep the batteries topped off without manual charging. According to the company, the standard Battery Camera can last up to six months per charge, while the Plus model could go as long as two years before needing to be recharged.

Making AI agents 'smarter' with connected data
The latest buzzy concept in the world of AI is now transcending its initial hype. Advances in Agentic AI are accelerating the development of autonomous business systems, building upon progress in machine learning. Acting as an independent ‘agent’, the technology can make informed decisions based on the multimodal data and algorithms they’re built on and then ‘learn’ from its experiences.
But even more excitingly, Agentic AI aims to execute tasks independently. It’s this ability to adapt, plan, and execute complex tasks without direct human intervention is what differentiates Agentic AI from its predecessors.

TCL D1 Fingerprint Smart Lock offers fast unlocking and local data storage for privacy-focused homeowners
If you’ve been thinking about upgrading your front door with a smart lock but don’t want your data floating around in the cloud, TCL may have the perfect solution. You see, the company has officially launched its D1 Fingerprint Smart Lock, a product designed to make home security both simple and private -- and yes, it is available to buy right now from Amazon for $89.99.
One of the big selling points is speed. The D1 uses a Swedish-made FPC fingerprint sensor with 508 DPI resolution, unlocking your door in just 0.3 seconds. TCL also worked an AI self-learning algorithm into the mix, which means the lock is supposed to get better at recognizing your fingerprint over time, even if your fingers are wet or dry.

Why auto-scaling is key to cost-effective cloud management
Today’s fast-paced digital businesses are dependent on scalable and adaptable public cloud infrastructures to keep up with the growing needs of their customers, with spending on global cloud infrastructure services predicted to increase by 19 percent this year. Faced with the constant challenge of how to optimise their cloud resources to avoid potential performance issues and unnecessary costs, the best prepared organizations must seek out tools to help achieve the most effective cloud management possible.
Auto-scaling is one such tool, designed to automatically adjust public cloud resources depending on real-time demand. It can help businesses keep their applications agile, responsive and available at the right level, so it is well worth considering its benefits.

Lenovo launches new ThinkPad laptops and workstations with Ryzen AI and Copilot+ for Windows 11
ThinkPad computers are absolutely legendary, and today Lenovo is expanding its lineup with a fresh batch of laptops and mobile workstations. The company has announced updates across several models, including the ThinkPad P14s Gen 6 AMD, ThinkPad P16s Gen 4 AMD, new L Series business laptops, and additional configurations for its X1 Aura Editions.
Leading the charge are the new ThinkPad P14s Gen 6 AMD and P16s Gen 4 AMD mobile workstations. These machines aim to offer a balance of power and portability, with the P14s weighing in at just over 3 pounds and measuring 16.13mm thin.
