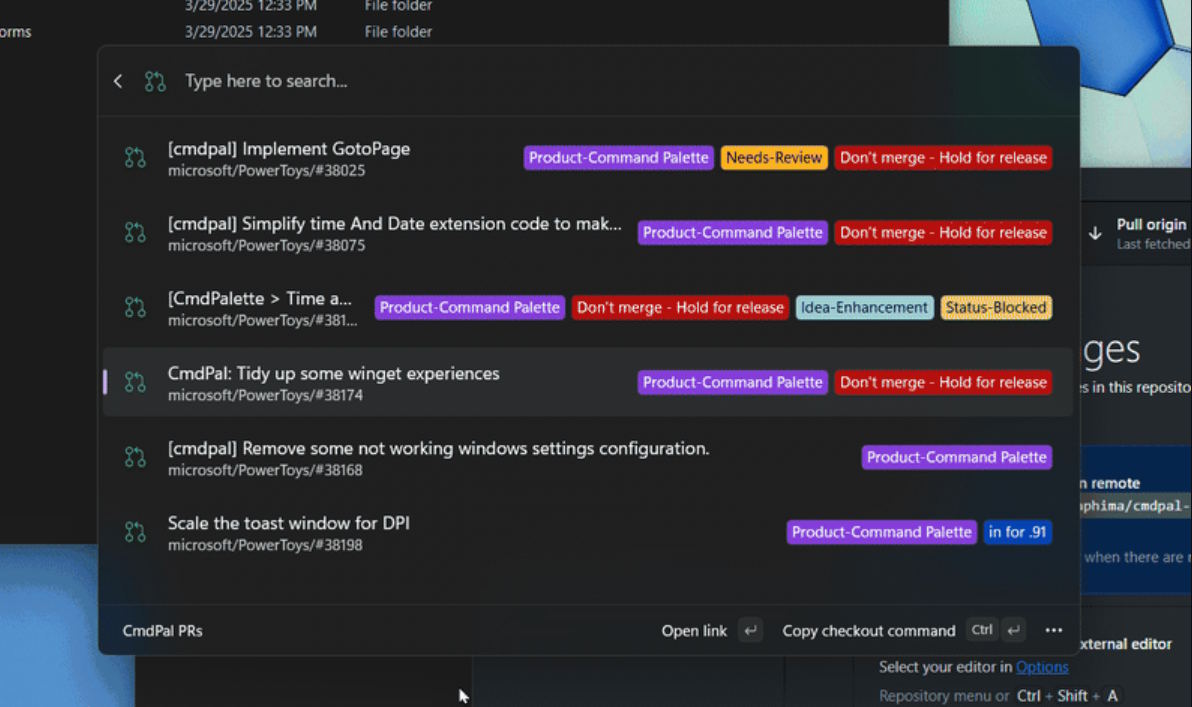
PowerToys v0.90.0 is here… and it’s a big release with a great new launcher module
We are, slowly but surely, making our way towards the release of PowerToys v1.0.0 -- but in the meantime we have the 0.x.x releases to enjoy. Microsoft has just pushed out PowerToys v.0.9.0, and it is an impressive update this time around.
Just a couple of weeks after we talked about the Command Palette module that was being worked on, this “PowerToys Run on crack” has landed. This is far from being the only change in PowerToys v0.9.0, though. In addition to a raft of bug fixes and tweaks, there are also new features for Peek, New+, and more.
Microsoft is making Copilot+ experiences available to more systems, and that’s great news for accessibility
When talking about AI in general -- including Copilot -- the focus tends to be on the impressive time-saving capabilities and futuristic features. What is often overlooked is the potential for artificial intelligence to improve accessibility.
But this is exactly what Microsoft is doing with the features it has for Copilot+ PCs. And now the company has made many of the Copilot+ experiences available to a wider range of processors, so systems with AMD Ryzen AI 300 series, Intel Core Ultra 200V and Snapdragon X Series chips can feel the benefits. There are huge advances in accessibility to be explored.

Amazfit Bip 6 smartwatch is a cheaper Apple Watch alternative with AMOLED screen and AI fitness coaching
If you’ve been eyeing an Apple Watch but don’t want to drop hundreds of dollars on your wrist (especially in this economy), Amazfit may have something worth considering. The newly released Bip 6 smartwatch delivers a bunch of smart features, health tracking tools, and a bright AMOLED display -- all for just $79.99. Yeah, folks, you read that right!
This watch isn’t trying to be flashy or overcomplicated. It’s built to get the job done without becoming a nuisance to use. The Bip 6 sports a 1.97-inch AMOLED screen that hits 2,000 nits of brightness, so you won’t be squinting at it in the sun. The body is aluminum alloy, it’s water resistant up to 5 ATM, and Amazfit says you’ll get about two weeks of battery life on a charge. An Apple Watch, meanwhile, pretty much needs to be charged daily… annoying.

Acer Predator X32 X2 and X27U X1 monitors bring QD-OLED to gamers with 240Hz refresh and 0.03ms response
Acer is giving gamers two new reasons to upgrade their setups -- the Predator X32 X2 and Predator X27U X1. These new monitors ditch the old LCD tech in favor of vibrant QD-OLED panels.
The Predator X32 X2 comes in at 31.5 inches and pushes out a crisp 3840x2160 resolution. But it’s not just about pixels -- this thing hits a wild 240Hz refresh rate with a 0.03ms response time. Thanks to AMD FreeSync Premium Pro, gameplay stays smooth even when things get hectic on screen.

World Backup Day -- your annual reminder that you need to look after your data
Today -- which of course you knew already -- is World Backup Day, an idea that began in 2011 as a reminder from a group of Reddit users who had seen too many people lose their important files. They deliberately picked the day before April Fool's to get across that you’d be a fool not to backup your data.
Although it started a bit of a joke it's become a useful reminder that backups are important and figures in the industry now see it as good for raising awareness. Here’s what some of them think.
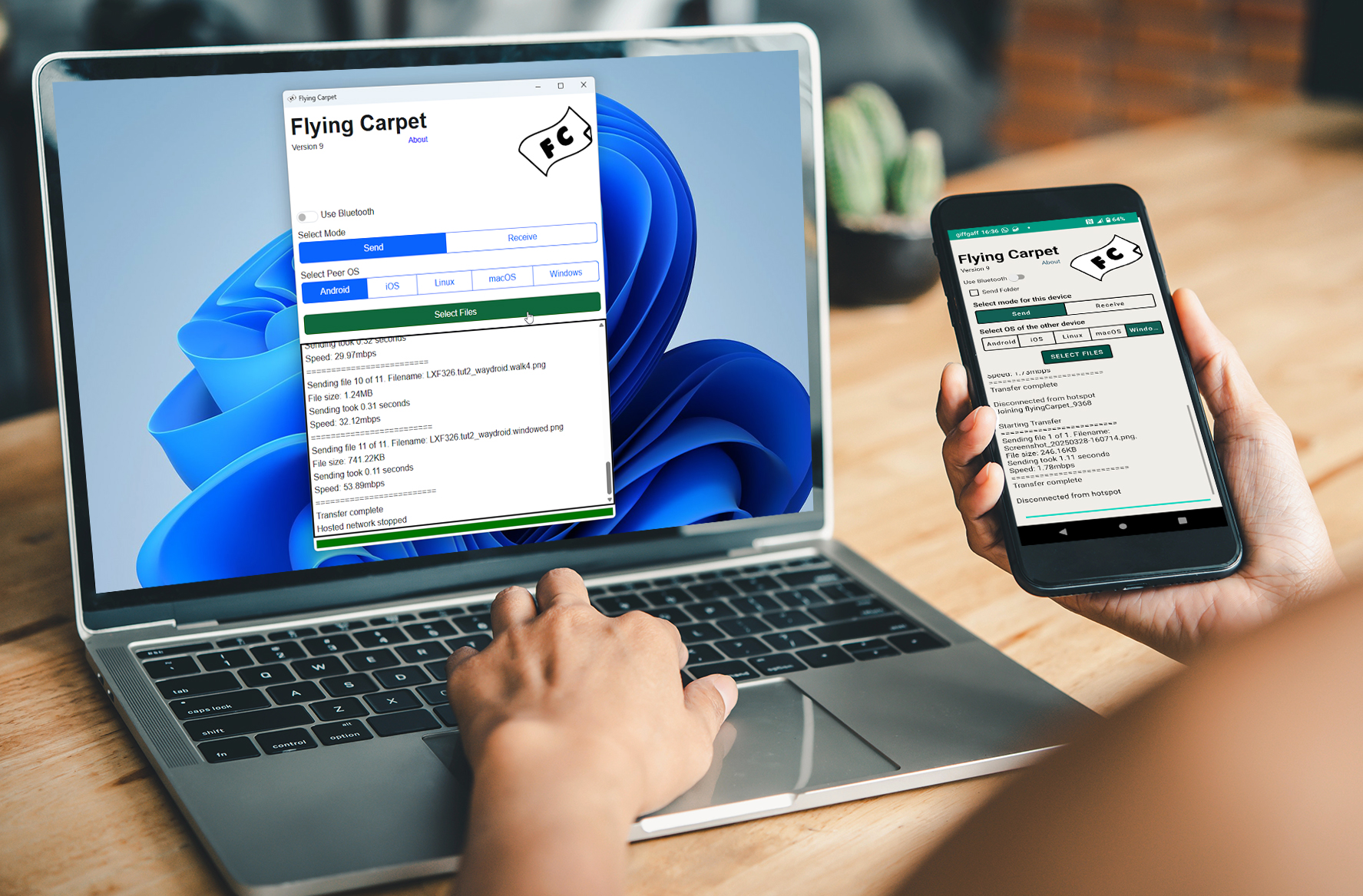
Flying Carpet 9.0 gives you AirDrop-like functionality across ALL your devices -- Windows, macOS, Linux, Android and iOS -- for free! Download it now
If you’re in dire need of quickly transferring a file between devices -- whether desktop to desktop, mobile to mobile or desktop to/from mobile -- then you’ll know the usual routine often involves transferring through an intermediary like a cloud or network folder or resorting to emailing or messaging yourself with the file as an attachment. Fiddly, time-consuming and often frustrating.
Apple’s AirDrop makes it easy to transfer files between Apple devices simply by bringing them into the same network, and now Flying Carpet 9.0 offers similar functionality across all major mobile and desktop platforms.

Say goodbye to Microsoft Windows 11 and hello to Nitrux Linux 3.9.1
Windows 11 offers a familiar environment for users, but it’s not without its share of frustrations, particularly regarding performance issues and resource consumption on older hardware. Microsoft's updates frequently add new problems while fixing old ones, which is another annoyance.
If you’ve been considering a switch from Windows 11, Nitrux is the perfect alternative. The Debian-based distribution, known for its focus on simplicity and performance, has just been updated to version 3.9.1, codenamed “mk.” This release includes new features and a series of updates and fixes aimed at improving the overall experience for both new and existing users.

What businesses miss when protecting their data [Q&A]
No business is immune from the threat of cyberattack, but when it comes to protecting their most critical and sensitive data many feel they are inadvertently helping attackers through the leaking information.
We spoke to Paul Laudanski, director of security research at Onapsis, to learn about the most common errors and how to guard against them,
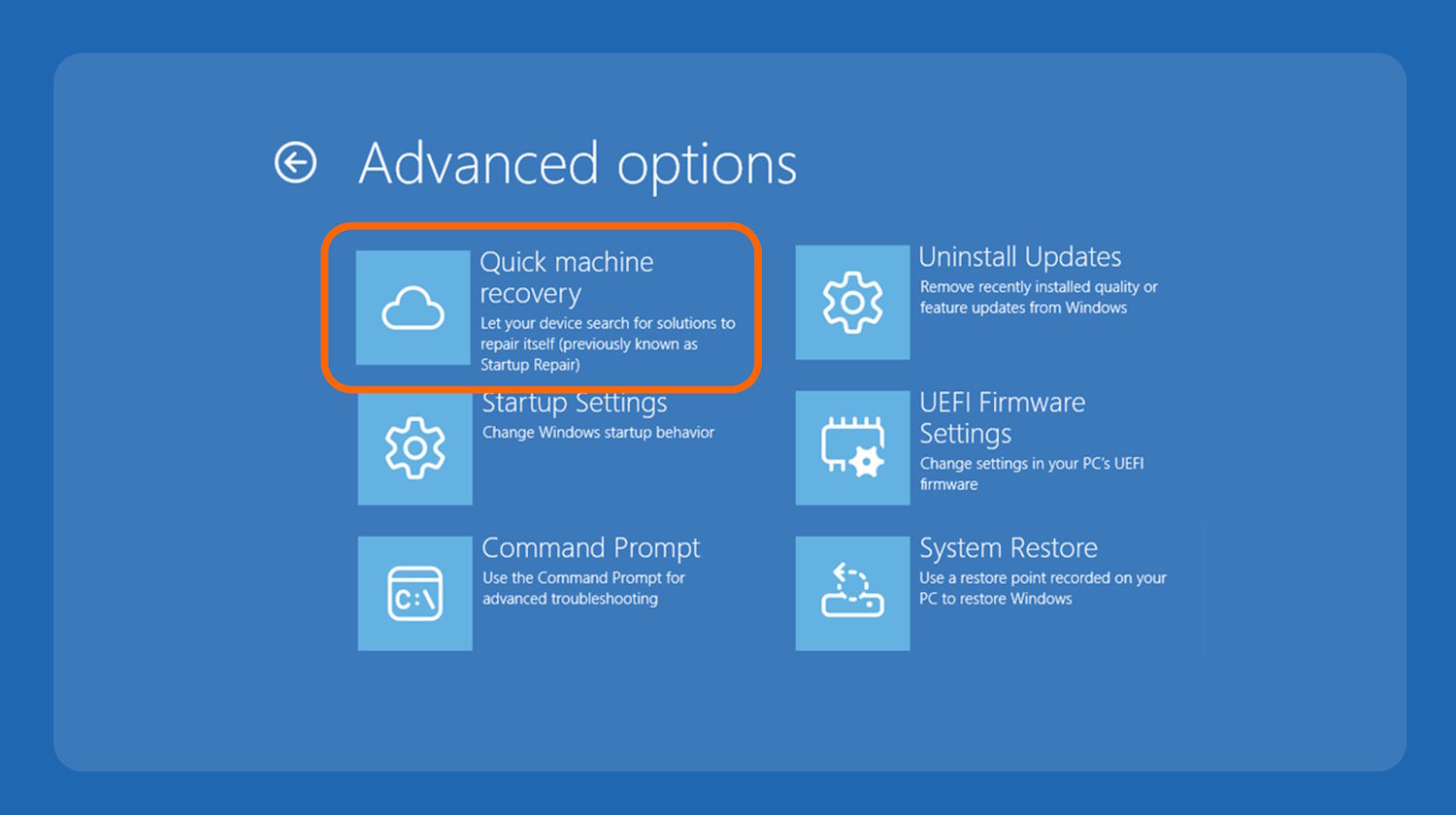
Microsoft launches Quick Machine Recovery to automatically fix your Windows 11 problems
When things go wrong with a Windows 11 device, downtime is not only frustrating but also expensive. In a bid to reduce the time lost to computer issues, Microsoft has launched Quick Machine Recovery, a new automated tool for addressing problems.
The tool is undergoing testing with Windows Insiders on the Beta Channel at the moment, so it probably won’t be long before it is promoted for general availability. Billed as a tool that “automatically detects, diagnoses, and resolves critical issues on your device”, Microsoft is looking to save users and sysadmins from having to delve into the Windows Recovery Environment.

Agentic AI might take years to transform security, but cyber defenders must prepare now
For the past two years, the world has been swept up in a rising tide of GenAI hype. The technology has evolved from a data science curiosity to a pervasive part of our everyday lives. ChatGPT alone has over 300 million weekly users worldwide -- and people use Large Language Models (LLMs) every day to generate text, images, music and more.
Despite GenAI’s widespread success, difficulty in developing robust applications that make use of trustworthy AI systems has proven difficult. This is most clear when noting the delta between consumer-facing GenAI applications relative to B2B integration of GenAI. But, with agentic AI this is about to change.
CachyOS March 2025 update adds new bootloader and updated hardware support to the Linux distribution
CachyOS is back with a fresh March 2025 release for the Linux distribution. The development team focused heavily on hardware support this time around, and it definitely shows. There’s a ton packed into this update, with improvements aimed at both desktop and handheld users.
Let’s start with something big: Limine. CachyOS now supports this bootloader, which works with both BIOS and UEFI setups. It even offers theming, similar to Grub. On top of that, if you’re using BTRFS as your filesystem, you’ll get automatic snapshot support right out of the box. That’s huge for anyone who wants an easy rollback option without extra configuration.
Exploring the security risks underneath generative AI services
Artificial intelligence has claimed a huge share of the conversation over the past few years -- in the media, around boardroom tables, and even around dinner tables. While AI and its subset of machine learning (ML) have existed for decades, this recent surge in interest can be attributed to exciting advancements in generative AI, the class of AI that can create new text, images, and even videos. In the workplace, employees are turning to this technology to help them brainstorm ideas, research complex topics, kickstart writing projects, and more.
However, this increased adoption also comes with a slew of security challenges. For instance, what happens if an employee uses a generative AI service that hasn’t been vetted or authorized by their IT department? Or uploads sensitive content, like a product roadmap, into a service like ChatGPT or Microsoft Copilot? These are some of the many questions keeping security leaders up at night and prompting a need for more visibility and control over enterprise AI usage.

This mechanical keyboard is just $10 on Amazon -- but you need to act fast!
Let’s be honest, folks -- most inexpensive keyboards aren’t worth the hassle. But every now and then, one pops up that actually makes you do a double take. That’s exactly what we’ve got here with the Newmen GM611. It’s a compact USB-C mechanical keyboard with a 60 percent layout, red switches, and rainbow LED lighting. And yes, it looks a lot more expensive than it is.
This thing isn’t just small for the sake of being small. The 60 percent layout trims the fat while keeping the essentials. It’s a great choice if you’re tight on space or just want a cleaner, simpler desk. But don’t think it’s lacking in features.

The hidden cost of legacy systems: How they hinder ROI and digital transformation
At this point in time, it is essential for one’s company to transform digitally in order to stay competitive and work efficiently. Most organizations will pour money into new modern technologies to heavily improve ROI and operational performance while ensuring they stay relevant in the new digital world. However, there is a barrier that stands in the way of achieving the maximum benefits: legacy systems.
Outdated and old software, hardware, and technologies continue to slow down any organization's positive transformation. To make matters worse, legacy systems tend to derail digital transformation initiatives, leading to additional expenses, hidden costs, and delays.




