
Enterprises increase reliance on public key infrastructures
A new report released by data protection company Thales and the Ponemon Institute shows that the use of cloud services and the IoT has led to greater dependence on public key infrastructures (PKIs) in today's businesses.
The survey of more than 5,000 companies across 11 countries shows that PKIs -- used to create, distribute, store, and revoke digital certificates and manage public-key encryption -- are increasingly relied on to support applications.

SoftPerfect’s World Route is a simple visual traceroute
Australian developer SoftPerfect has shipped World Route 1.0, a free for Windows (commercial for Mac) visual traceroute which plots your internet traffic on a world map.
The package is built for simplicity. Type your destination domain or IP address in a box, press Enter and the program begins listing the IP address and geographic location of each hop. Once it’s done, the route is drawn over a Google-sourced map, and some summary stats list the total distance of all hops and their round-trip time.

UK bans Apple Watch from cabinet meetings
In an attempt to block foreign hackers from compromising the devices of British politicians to access sensitive information, Apple Watches have been banned from use during official cabinet meetings.
The UK's prime minister Theresa May has informed elected ministers that just as mobile phones are not allowed, high-end smartwatches will no longer be permitted as they pose a security risk. An inside source informed The Telegraph that "The Russians are trying to hack everything".

Samsung orders the global shutdown of both sales and exchanges of Galaxy Note7
Sigh. The Galaxy Note7. What should have been a wildly popular and successful smartphone has become synonymous with failure, and fodder for jokes. As everyone knows, the phone has been exploding and catching fire, creating serious risk for consumers.
The phone was eventually recalled and replaced, although that process was bungled by Samsung -- there was much confusion. Not to mention, there was criticism that the recall was not initially an official one. With the issues seemingly in the rear view mirror, the scandal was over, right? Wrong. Now, the replacement models are reportedly exploding too. Enough is apparently enough. Following rumors that production of the phone was being ceased, today, Samsung orders the global shutdown of both sales and exchanges of Galaxy Note7.

Kingston IronKey D300 USB Flash Drive has FIPS 140-2 Level 3 256-bit AES-XTS hardware encryption
Flash drives are less popular nowadays thanks to cloud storage. While the cloud offers convenience, there is extra control and security when local storage is used. Remember folks, when you leverage the cloud, you open yourself up to deficiencies of a third-party company -- a mass data breach could expose your secret files. For a business in particular, this could mean the loss of important information, or the leak of confidential information. Your company's reputation could be tarnished as a result.
If you are more comfortable using USB flash drives for storing and transmitting data, encryption is a must -- hardware being the best. Today, Kingston unveils the IronKey D300 USB Flash Drive. To secure your data, it uses FIPS 140-2 Level 3, 256-bit AES-XTS hardware encryption. There is also a "managed" version of the drive which allows companies to impose its requirements on employee-used drives.

Consumers don't want to use more apps due to security concerns
The fact that people are afraid to use more apps because of security reasons is costing the UK economy billions. To be more precise, £2.5 billion this year, £3.2 billion the next.
This is according to a new report by Rackspace, which says that 36 percent of consumers are reluctant to use more apps for security reasons. Privacy is also a huge issue for 33 percent of consumers in general -- rising up to 37 percent among the older population.
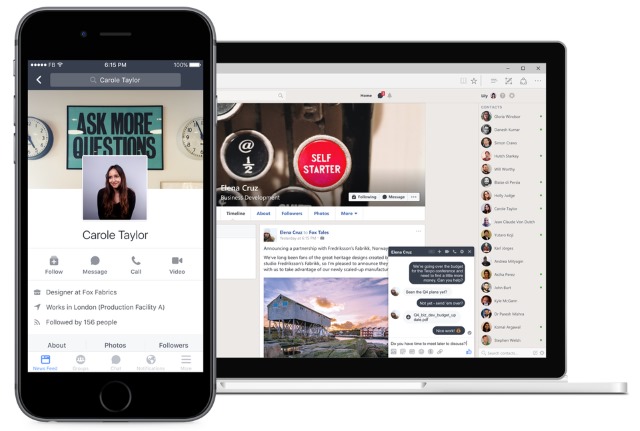
Workplace by Facebook exits beta, bringing social networking to the enterprise
You may not have heard of Workplace by Facebook, and that could be for one of two reasons. Firstly, it used to be known as Facebook at Work but, more importantly, it has been in closed beta for nearly two years.
Today, Facebook announces that Workplace is now available all over the world, giving enterprise users a way to stay connected with co-workers. Promising "the best of Facebook plus new features", Workplace can be used by any company or organization that feels a personalized, internal social network with messaging capabilities could be beneficial.

Identifying hackers is harder than you think
One of the main reasons why hackers and other malicious actors are so hard to locate is not the fact they're really good at hiding their location -- it is because they're exceptional when it comes to faking things. They fake their locations, their working hours, language, infrastructure, toolkits -- even their own groups.
Hackers are going extreme lengths to make sure people looking for them are actually in for a wild goose chase. These conclusions were released by security researchers at Kaspersky Lab who tried to tackle the issue of misleading both victims and security researchers.

HP Elite x3 Windows 10 Mobile phone now available from Microsoft -- who will buy it?
Windows 10 Mobile is a virtually dead platform. True, Microsoft is still developing it, but there are so few active users, that it is totally irrelevant. It isn't a bad mobile operating system, but a lack of apps makes it a non-starter for many. Ultimately, there is no compelling reason to choose a device running it over, say, an iPhone 7.
Today, what looks to be the best Windows 10 Mobile smartphone ever -- the HP Elite x3 -- becomes available for purchase. It is only being sold directly from Microsoft in its retail locations or its online store. The big question, however, is who the heck will buy such an expensive phone without access to many popular apps? I mean, $800 is a significant chunk of change, am I right?

Consumers are 'overwhelmed' by the sheer number of security alerts
A new study has revealed that many consumers are suffering from "security fatigue" as a result of relentless cybersecurity warnings which have led to many of them failing to protect themselves online.
The study was conducted by the US National Institute of Standards and Technology (NIST), by conducting in-depth interviews with a wide cross-section of Americans between the ages of 20 and 60 living in rural and urban areas in both low and high-paying jobs.

GIGABYTE refreshes BRIX compact barebone PCs with 7th Gen Intel Kaby Lake processors
Size matters. Well, when it comes to computers, at least. Look, long gone are the days of having dedicated computer rooms where a family shares a single monstrous tower. With so many adults moving back home with their parents, houses and apartments are much more cramped, meaning fewer vacant rooms. True, a laptop can alleviate this, but so can a diminutive desktop. By taking up less space (some can even be VESA mounted to the rear of a monitor), a compact PC can allow a desk or table to serve other purposes than simply being home to a tower.
There are many choices in the compact PC market nowadays, such as the brilliant System76 Meerkat, or the new HP mini computers -- Wave and Slice. If you want a barebones system, however, GIGABYTE's BRIX line is a legit alternative to Intel's own NUC. Today, BRIX gets a refresh with all-new 7th Gen Intel 'Kaby Lake' Processors.

Milton is a minimalist painting tool with some smart tricks
Milton is a simple and straightforward painting tool which does its best to stay out of your way, but still has some unusual tricks of its own.
The core drawing tools are basic. Just one round brush, with color, size and opacity settings, and an eraser (or infinite undo) if you’ve made a mistake.

Trolls, sexters and doxxers could face prosecution for social media hate crimes
The UK's Crown Prosecution Service (CPS) has today published new social media guidelines that set out online offenses for which people could be prosecuted. Launched as part of Hate Crime Awareness Week, the guidance will be used to decide whether criminal proceedings should be brought against individuals.
Among the offenses outlined in the document is 'virtual mobbing' -- encouraging others to engage in online hate campaigns. The CPS points out that anyone doing this could face charges under the Serious Crime Act 2007. Also published today is the Public Policy Statements on Hate Crime which is due to be put to public consultation and will focus on hate crimes against disabled people, as well as attacks of a racial, religious, homophobic and transphobic nature.

Revenue management for telecommunications companies
According to the Communications Fraud Control Association (CFCA), network operators around the world lose around $38 billion annually to fraud and uncollected revenues. Currently the biggest threat to telecommunications service providers comes from loss of termination revenues.
Termination revenues come from when a network handles someone else’s call -- for example when someone on one network contacts someone on another -- or when you dial abroad. Telecommunications service providers naturally want to have a reward for handing on the call to the final recipient. Annual declines in revenue from termination in many countries are 10 percent or more.

Google Chrome 55 will drastically improve memory consumption
Google Chrome has received plenty of updates to make it lighter on resources, but it can still be a bit of a hog in certain areas. Its higher memory consumption remains a weak point, as you can easily notice on systems with a lower amount of RAM. However, an upcoming update is touted to greatly lower its footprint.
Google Chrome 55, which is expected to arrive in December, should improve the average memory consumption by up to 50 percent compared to the current release, version 53.



