
Yes, Microsoft Cross Device Service is causing high CPU usage in Windows 11; no, there is no fix
If you have been experiencing higher than normal CPU usage in Windows 11 recently, you are certainly not alone. There is good and bad news.
The good news is twofold. Firstly, the cause of the issue has been identified by Microsoft, and secondly, it only affects Insider builds of Windows 11. The bad news, however, is that there is no fix available, and no indication of when this may change.

Linux-based postmarketOS v24.06 supports over 250 devices, taking on Google’s Android and Apple’s iOS
postmarketOS v24.06 is now available, targeting Linux enthusiasts who seek more control and flexibility on their devices. This release brings stability improvements and automated testing, though it may not yet match the polish of ChromeOS, Android, or iOS.
The appeal of running Linux on personal devices lies in the freedom it offers. postmarketOS does not require account setups, does not push cloud storage, avoids pre-installed bloatware, and does not follow privacy-invasive AI trends. Instead, it focuses on free software, user control, and extending device usability beyond the original vendor's support.

Your company needs a BEC policy and five other email security trends
Hardly a week goes by without news of another email-based attack via phishing or Business Email Compromise (BEC) scam. These types of attacks can cause a great deal of damage to infrastructure and an organization’s image, whether it is a large enterprise, a small-medium business (SMB) or even much smaller retailers. The FBI (Federal Bureau of Investigation) reports that the average financial loss per BEC attack is $125,000 and last year estimated the Business Email fraud industry to be valued at a whopping $50 billion.
These attacks are increasingly creative, and typically involve impersonation of someone such as the head of an organization or finance. If someone responds on behalf of the executive, they could unknowingly give away the keys to the kingdom, causing significant losses. With that in mind, let’s review some of the larger email security trends.

SparkyLinux 7.4 'Orion Belt' update rolls out: Here’s what's new
The much-anticipated update to Sparky 7, dubbed "Orion Belt," is officially here with its 7.4 version, and it's packed with updates and tweaks.
For those who might not know, Sparky 7 is built on the stable backbone of Debian 12 "Bookworm," ensuring a seamless and reliable experience for its users. This latest update, rolled out as a part of its regular quarterly cycle, brings us up to speed with the freshest developments from both Debian and Sparky’s own repositories.

Securing AI copilots is critical -- here's how
The use of AI copilots is already helping businesses save time and gain productivity. One recent study found that employees who gain proficiency using copilots saved 30 minutes a day, the equivalent of 10 hours a month, while the average employee saved 14 minutes a day, or nearly five hours each month.
AI copilots essentially allow people to interact with business productivity tools for greater efficiency. You can ask these tools questions, synchronize data and perform automated actions in an easier and better way. In the survey referenced above, 70 percent of users reported greater productivity while 68 percent said it improved the quality of their work. However, while the business benefits are significant, these copilots can also introduce new security risks that organizations must be aware of -- and have a plan for.

Get 'Cybersecurity Architect's Handbook' (worth $15) for FREE
Stepping into the role of a Cybersecurity Architect (CSA) is no mean feat, as it requires both upskilling and a fundamental shift in the way you view cybersecurity altogether.
Cybersecurity Architect’s Handbook is an all-encompassing guide, introducing the essential skills for aspiring CSAs, outlining a path for cybersecurity engineers and newcomers to evolve into architects, and sharing best practices to enhance the skills of existing CSAs.

ViewSonic unveils CDE92UW ultra-wide 92-inch 5K commercial display
ViewSonic has introduced the ultra-wide 92-inch CDE92UW commercial display. With its native 5K resolution, 21:9 aspect ratio, and high brightness levels, the CDE92UW is designed to maximize messaging and communication capabilities, ensuring seamless 24/7 operation. This display is ideal for corporate, educational, and retail environments, offering a dynamic and immersive solution that enhances visual experiences.
The ViewSonic CDE92UW offers premium visual content delivery with deeper immersion and precision, featuring a 33 percent increase in screen real estate compared to traditional 16:9 displays. This additional space is perfect for the Front Row layout in Microsoft Teams Rooms, allowing for more engaging and productive meetings. The display is built for performance and simplicity, equipped with an Octa-core SoC and Android 13, which facilitate efficient multitasking. A USB-C one-cable solution supports 100W power delivery, simplifying connectivity with external devices.

AI-generated code could increase developer workload and add to risk
Artificial intelligence is supposed to make things easier, right? Not for developers it seems as AI-generated code is set to triple developer work within the next 12 months according to software delivery platform Harness.
This could also mean that organizations are exposed to a bigger 'blast radius' from software flaws that escape to production systems.

Think you could spot a deepfaked politician?
Given the quality of many politicians at the moment you might be forgiven for thinking that sometimes a deepfake would be an improvement.
But to be serious, a new study from Jumio of over 2,000 adults from across the UK finds that 60 percent are worried about the potential for AI and deepfakes to influence upcoming elections, and only 33 percent think they could easily spot a deepfake of a politician.
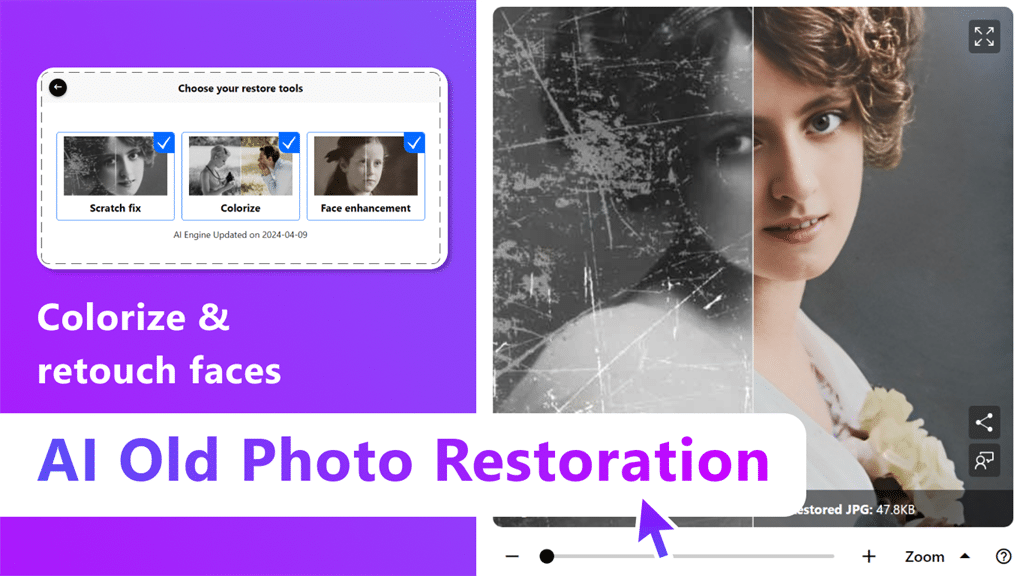
Best Windows apps this week
Five-hundred-and-ninety-nine in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft is changing the functionality of the controversial Recall AI feature to improve quality and security. It won't release the feature on June 18 to Copilot+ PCs, but plans to introduce it to the Windows Insider Platform first.

Security pros struggle with too many tools
New research by Keeper Security shows nearly half of security professionals (48 percent) say they favor standalone security solutions for specific issues.
But, this has resulted in security pros grappling with an average of 32 different security solutions in their tech stacks, and some managing hundreds of different security tools.
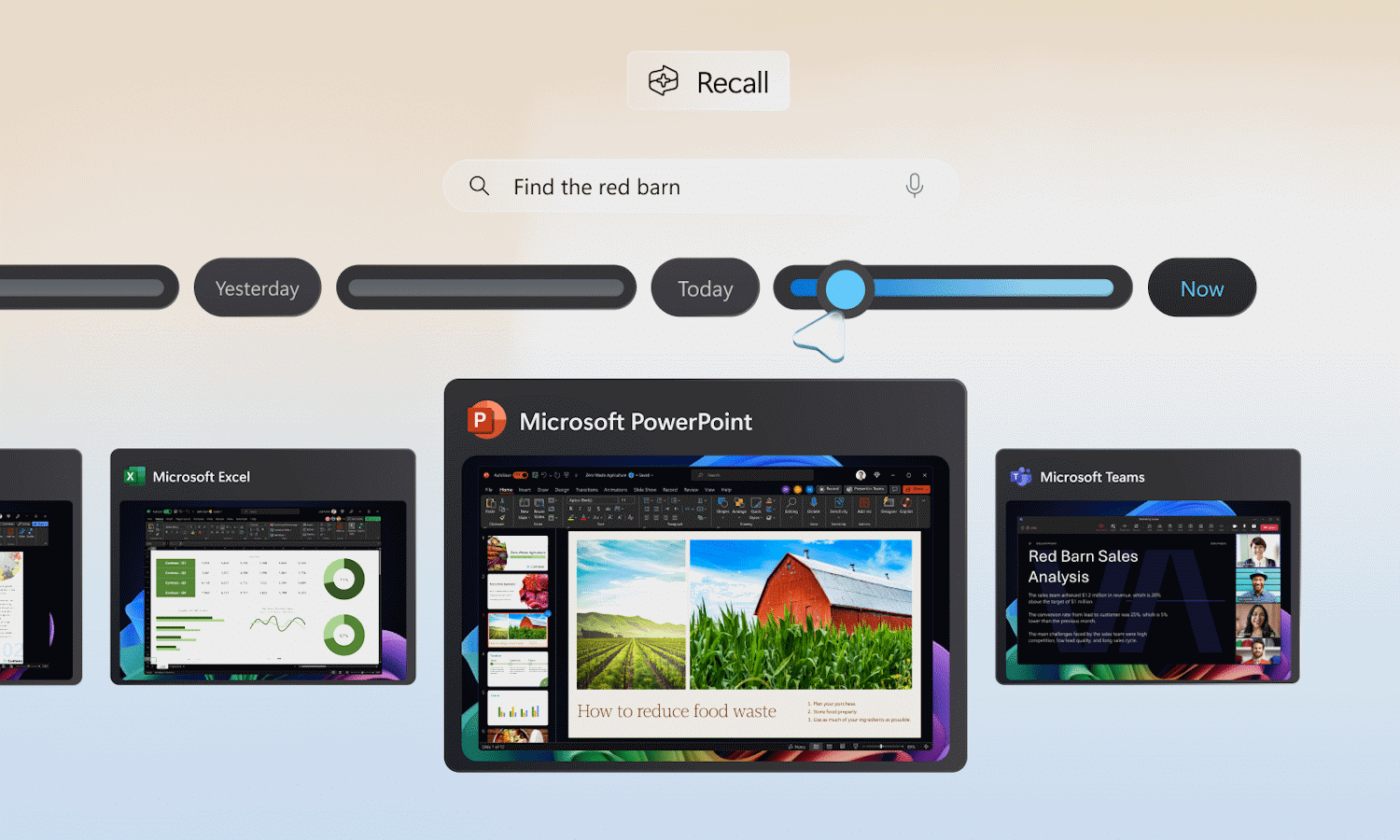
Microsoft postpones Recall so new Copilot+ PCs will launch without this flagship feature
Since it was first announced, the Recall feature for Copilot+ PC has been a major headache for Microsoft. The AI-powered feature has raised all manner of privacy concerns, and now the company has responded by putting the brakes on rolling it out.
Microsoft doesn't use words like "delay" or "postpone", of course. In an update to an earlier blog post about the rollout of the feature, the company now says: " We are adjusting the release model for Recall to leverage the expertise of the Windows Insider community to ensure the experience meets our high standards for quality and security".
How collaborative learning and conversational intelligence are changing AIOps [Q&A]
Artificial intelligence is changing the way that we work with computers and in particular collaborative learning (CL) and conversational intelligence (CI) are set to reshape AI-powered operations.
We talked to Dr. Maitreya Natu, chief data scientist at Digitate, to discover more about what this means both for businesses and for the role of operations professionals.
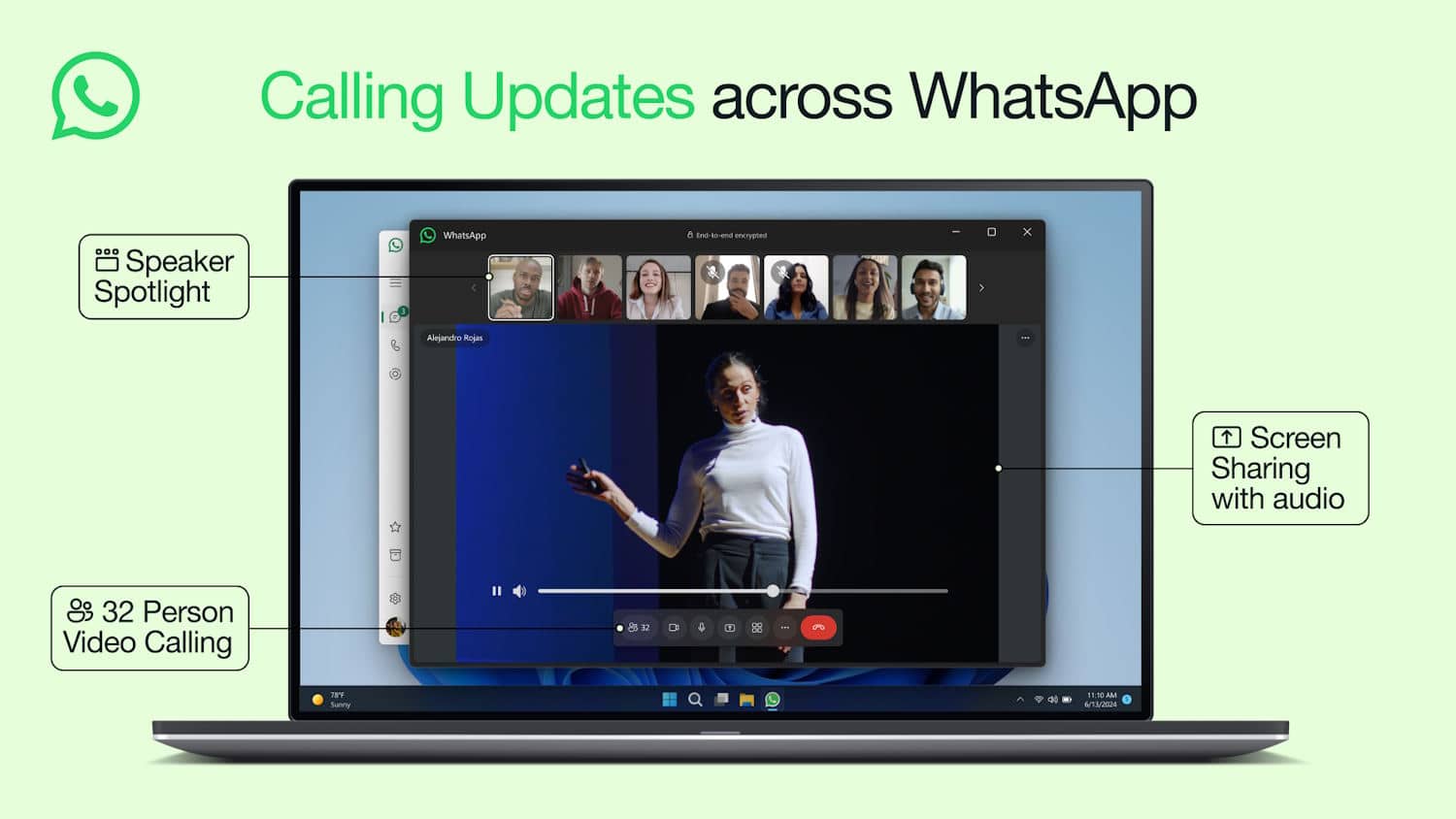
WhatsApp announces huge improvements to calling across all platforms
Whether you use WhatsApp on the desktop, or on your mobile device, there are a raft of changes and improvements coming to enhance the call experience.
Rolling out over the next few weeks, the changes include support for video calls with up to 32 people across all devices. There is also the arrival of sharing audio when screen sharing, and a switch to the new, more efficient codec means that you can expect higher call quality even when connectivity is poor.

TCL FLIP 3 helps Gen-Z unplug from social media and focus on real life
Do you find yourself staring at screens all day, spending too much time on social media or gaming when you should be engaging in real life? The new FLIP 3 from TCL Mobile might be the perfect device for you. Flip phones have become the latest trend for Gen-Z, especially for those who want to unplug and take a break from social media.
The TCL FLIP 3 is ideal for those wanting to spend more time enjoying life and less time tethered to a screen. It’s also a great starter phone for kids and teens whose parents want to limit their screen time and social media access.


