
Intel surpasses 500 AI models on Core Ultra processors
Today, Intel announced it has successfully optimized over 500 AI models to run on the new Intel Core Ultra processors. These AI-friendly PC chips are equipped with capabilities that enhance AI experiences, provide immersive graphics, and optimize battery life.
This milestone highlights Intel's dedication to advancing client AI through significant investments in AI transformation, framework optimizations, and robust AI tools like the OpenVINO toolkit. The array of 500 models, deployable across CPU, GPU, and NPU, spans various sources such as the OpenVINO Model Zoo, Hugging Face, ONNX Model Zoo, and PyTorch. These models encompass a wide range of local AI inferencing applications, including large language models, diffusion, super resolution, object detection, image classification, segmentation, and computer vision.

A technical overview of Cisco IoT: Routing and switching
The topical area of Cisco’s IoT (Internet of Things) offerings includes assorted types of wireless networking, and they consist of widely disparate requirements in different use cases such as “industrial networking.”
At recent partner training courses and presentations, Cisco summarized its product applications to various market niches. The following article offers a compiled summary of Cisco's IoT products, describing how they might be used and pinpointing why tech decision-makers should care about specific features.

Raycon launches upgraded Everyday Earbuds
Raycon has unveiled an updated version of its Everyday Earbuds. The new enhancements include Active Noise Cancellation (ANC), multipoint connectivity, and a quick charge function, building on the success that attracted over 2.5 million customers to the original model.
Ray Lee, co-founder and CEO of Raycon, emphasized the importance of customer feedback in developing the upgraded product. “The original Everyday Earbuds made technology accessible and user-friendly,” Lee said. “Our customers’ enthusiastic support and suggestions inspired these new features, such as ANC and improved device connectivity, which they were eager to see.”

Data privacy requests surge since 2021
A new report shows 246 percent boost in privacy requests since 2021 as consumers seek to clear personal data online.
The report from DataGrail shows Data Subject Requests (DSRs) -- formal requests made to a company by a person to access, delete or request not to sell/share the personal data that the company holds on them -- increased by 32 percent from 2022 to 2023.

New solution helps enterprises demonstrate security and compliance
As numbers and severity of third-party breaches grow, companies are scrutinizing not just how they handle data, but how their vendors do as well. Trust management platform Vanta is launching a new addition to its Trust Center to allow enterprises to automate security questionnaires
Questionnaire Automation in Trust Centers uses Vanta AI to save time by generating suggested responses for security teams to review and approve, rather than starting from scratch each time. This will make it easier for enterprises to proactively and reactively demonstrate their security and compliance.

Philips launches Evnia 49M2C8900 49-inch QD OLED curved gaming monitor
Philips has launched the Evnia 49M2C8900, a 49-inch curved gaming monitor. At the core of this display is the cutting-edge QD OLED panel that merges the benefits of self-luminous OLED displays with quantum dot technology. This combination delivers superior contrast, deeper blacks, and vivid colors.
The monitor’s 49-inch screen, with a 32:9 aspect ratio and a 5120x1440 dual QHD resolution, offers expansive, sharp visuals. The 1800R curvature of the screen envelopes the user, providing an unparalleled immersive gaming experience.

New solution uses AI to target spam and phishing
Since the launch of ChatGPT there has been a surge in the number of phishing emails as AI makes it easier to create convincing lures.
Email security specialist SlashNext is fighting AI with AI thanks to the launch of a new generative AI large language model (LLM) to deliver accuracy and precision in spam detection, with claimed near-zero false positive rates.

Get 'Microsoft Excel Dashboards & Reports For Dummies, 4th Edition' (worth $24) for FREE
Beneath the seemingly endless rows and columns of cells, the latest version of Microsoft Excel boasts an astonishing variety of features and capabilities. But how do you go about tapping into some of that power without spending all of your days becoming a spreadsheet guru?
It’s easy. You grab a copy of the newest edition of Microsoft Excel Dashboards & Reports For Dummies and get ready to blow the pants off your next presentation audience!

VNC is the hacker's favorite remote desktop tool
Virtual Network Computing (VNC) is the remote desktop tool most targeted by attacks, accounting for 98 percent of the traffic across all remote desktop-specific ports.
This finding comes from Barracuda which has released a new Threat Spotlight report looking at the most common tools, associated ports, and the ways in which attackers can, and do, gain access.

The human challenges of dealing with security alert backlogs [Q&A]
Most security teams experience some level of alert overload, struggling to prioritize the issues demanding immediate attention from those that are less pressing. This can lead to a backlog of problems to be dealt with and consequent stress on team members.
We talked to Yoav Nathaniel, CEO and co-founder of Silk Security, about why alert backlog is a people problem rather than a technological problem and how IT and security teams can overcome this challenge.

Nearly 1 in 5 ransomware attacks results in a lawsuit
A new study from Comparitech finds that around a fifth of ransomware attacks in the US led to a lawsuit in 2023.
It shows that 355 lawsuits were filed following 3,002 ransomware attacks. Of these 228 have been completed and 134 were successful -- that is they led to a data breach settlement, resulted in the company being fined for failing to safeguard systems and/or data, or were settled out of court.
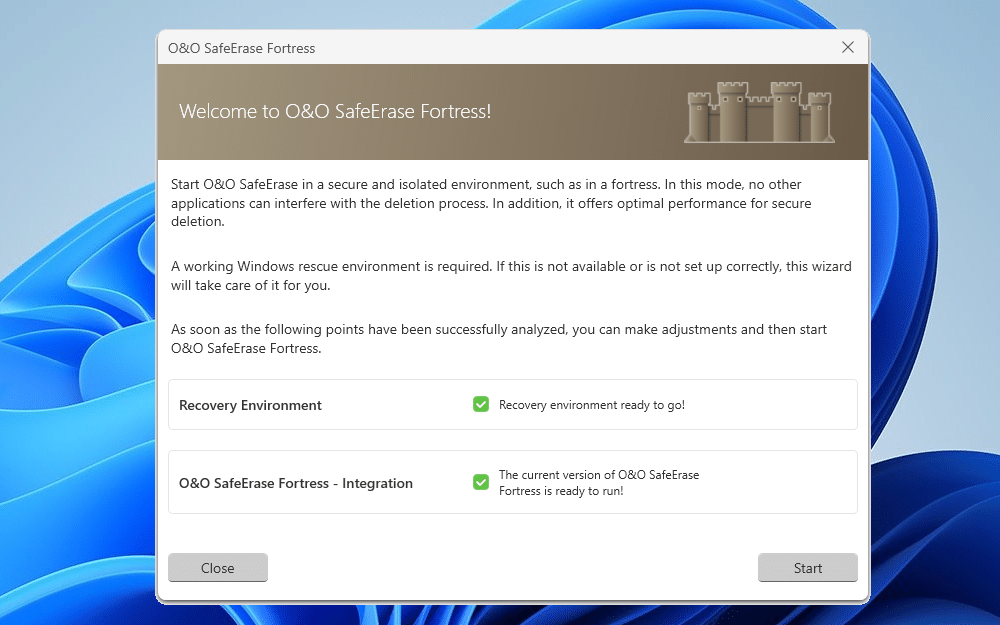
O&O SafeErase 19 unveils isolated Fortress environment, refreshed user interface
Berlin-based O&O Software GmbH has launched O&O SafeErase 19, a new release of its Windows data-shredding tool. Version 19 unveils a new feature -- Fortress Mode -- alongside a completely revised user interface.
When enabled, Fortress Mode provides O&O SafeErase with its own completely isolated Windows environment. The tool effectively "locks" the system, preventing other processes from accessing the user’s data. This ensures data shredding is safer while also speeding up the process.

Apple unveils Beats Solo Buds and Solo 4 headphones
Apple has unveiled an impressive expansion to its Beat product lineup with two new offerings: the Beats Solo Buds and Beats Solo 4 headphones.
The Beats Solo Buds are designed to provide big sound in a small package, featuring up to 18 hours of battery life, seamless pairing with both iOS and Android devices, and USB-C charging. Priced at $79.99, these earbuds are the smallest product yet from Beats, aimed at users seeking portability without compromising on quality. Available in June, the Solo Buds come in four colors: Matte Black, Storm Gray, Arctic Purple, and Transparent Red.

HighPoint launches Rocket 1608A PCIe Gen5 x16 to 8-M.2x4 NVMe Switch Add-In Card
HighPoint Technologies has launched the Rocket 1608A PCIe Gen5 x16 to 8-M.2x4 NVMe Switch Add-In Card (AIC), designed to optimize the performance of the latest Intel 600/700 and AMD X670E desktop platforms. This advanced AIC leverages the full x16 lanes of PCIe Gen5, achieving insane transfer speeds up to 56GB/s!
The Rocket 1608A model, officially named the Rocket 1608A PCIe Gen5 x16 to 8-M.2x4 NVMe Switch AIC, falls under the product category of PCIe Gen5 NVMe RAID AIC/Adapters. It features a PCIe 5.0 x16 bus interface and can accommodate eight NVMe ports, each with a dedicated PCIe 5.0 x4 channel. This AIC supports up to eight SSDs in the 2242, 2260, and 2280 form factors.

TUXEDO refreshes AMD Ryzen-powered Pulse 14 Linux laptop
TUXEDO Computers has unveiled the refreshed Pulse 14, an ultrabook that promises exceptional power efficiency and performance in a remarkably slim and lightweight form. With its partial aluminum chassis, weighing just 1.4 kg and measuring a mere 1.8 cm in thickness, this device is designed for users who want both portability and power.
The heart of the 4th-generation Pulse 14 is the AMD Ryzen 7 8845HS processor, fabricated using an advanced 4nm process. This 8-core, 16-thread CPU is not only powerful, but it is also highly energy-efficient with a Thermal Design Power (TDP) of just 54 watts. This efficiency is crucial in maximizing the battery life of the ultrabook, allowing up to 11 hours of video playback.



