Get 'Digital Marketing All-In-One For Dummies, 2nd Edition' (worth $24) for FREE

With more than 800 content-packed pages, Digital Marketing All-in-One For Dummies is the most comprehensive tool for marketers looking to beef up their online presence.
In this edition, you’ll learn the latest trends in digital marketing strategies, including brand new insight on how to incorporate artificial intelligence into your marketing plans. You’ll also get the latest information on how to manage your customers’ experiences, create exceptional marketing content, get help from influencers, and leverage social accounts for more followers and greater profits.
How the .ai domain is benefiting cybercriminals (and a small Caribbean island)
Google is using AI in Waze to deliver crash history alerts about dangerous roads
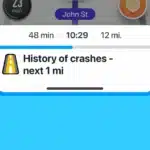
With so much focus on Google Maps as a navigation tool, it is easy to forget that Google also owns Waze and that this app is often home to far more exciting and useful features.
Demonstrating this, Google has just announced a new feature for Waze that is partly AI-powered, partly community driven; Crash History Alerts. This road safety feature is very much what it sounds like -- a warning system that lets users know about potentially dangerous, crash-prone roads based on historical data.
The rise of mobile app overlay attacks and how to defend against them [Q&A]

A major new threat has made its presence felt in the last few months. Cybercriminals have expanded the use of screen spoofing or overlay attacks from web applications to trusted mobile apps.
What’s more, the availability of as-a-service technology has lowered the threshold for attacks. We spoke to Dr. Klaus Schenk, SVP security and threat research at Verimatrix, to learn more about how these attacks work and what can be done to guard against them.
Google is making it easier to get the best prices and find discount codes
Google is introducing new tools in both Chrome and Google search that should help to make online shopping a little cheaper. With the holiday season just around the corner and shoppers eager to save money, the timing is ideal.
Chrome users are gaining access to a new feature that will seek out discount codes much like services such as Honey. There is also a new section landing in search results that makes it easier to track down products that are on sale.
elementary OS 8 Linux distribution roadmap revealed

As someone who has kept a close eye on the evolution of Linux distributions, I find the development journey of elementary OS particularly fascinating. With the next major release, elementary OS 8, on the horizon, the anticipation within the Linux community is palpable, and for good reason. The developers have shared the planned roadmap for the operating system.
The roadmap for elementary OS 8, while not tied to a fixed release date, suggests a release window post-April 2024, following the Ubuntu 24.04 LTS launch. The elementary team's philosophy is quality over haste, which means they will release OS 8 only when it meets their stringent standards. This meticulous approach is what endears users to elementary OS, as it often translates to a polished and stable computing experience.
NETGEAR launches MS108TUP 8-Port Multi-Gigabit (2.5G) Ethernet Ultra60 PoE++ Smart Switch

NETGEAR has broadened its product offerings tailored to small and mid-sized businesses with the introduction of the MS108TUP Smart Switch. The MS108TUP stands out with its Multi-Gigabit (2.5G) Ethernet ports and PoE++ support, ensuring that various devices operate at optimal performance levels without a hitch.
The MS108TUP joins forces with other NETGEAR products such as the PR60X Pro Router and the Pro WiFi Access Points. Managed via the Insight cloud platform, this lineup facilitates a cohesive network ecosystem that’s both scalable and user-friendly, particularly for businesses lacking on-site IT support.
Fedora Linux 39 launches with GNOME 45

Twenty years after the debut of Fedora Core 1, Fedora Project commemorates this milestone with the release of Fedora Linux 39 (available here). This iteration brings forward a suite of enhancements and updates that solidify its stance as a versatile operating system for a multitude of platforms. At the heart of Fedora Workstation 39 is GNOME 45, which promises not only improved performance but a slew of user experience refinements.
GNOME 45 introduces new widgets and a redesigned Image Viewer application, boosting both aesthetics and functionality. The desktop environment has become more informative with a dynamic workspace indicator, giving users a clear view of their virtual desktop landscape. A new camera activity indicator, alongside the pre-existing privacy features, now notifies users when their camera is accessed.
Organizations turn to GenAI to combat downtime

Downtime-producing incidents such as application outages and service degradation are putting organizations at risk of losing up to $499,999 per hour on average, so it's no surprise they're turning to AI to help their responses.
A new State of DevOps Automation and AI report from Transposit shows 84.5 percent of respondents either believe AI can significantly streamline their incident management processes and improve overall efficiency or are excited about the opportunities AI presents for automating certain aspects of incident management.
Unauthorized apps put businesses at risk

The risks from shadow and unauthorized apps have been known for years, but new research from Armis finds employees of 67 percent of UK organizations are introducing risk to the business by downloading applications and software onto assets without the knowledge or management of IT or security teams.
In addition the study, carried out by Vanson Bourne, finds 39 percent of enterprises admit to feeling challenged by increasingly complicated regulations and governance requirements.
Social media security issues pose threat to election campaigns

A new report from access management platform Cerby highlights the critical need for best practices for businesses and political leaders to secure their accounts as the November 2024 US elections quickly approach.
Researchers analyzed social media platforms Facebook, Twitter (X), Instagram, TikTok, and YouTube across six key security parameters. The report provides detailed insights into gaps in their support for enterprise-grade authentication and authorization.
Proton VPN rolls out new Linux app

Many people choose to browse the internet using a VPN because it offers a number of benefits including privacy and safety, and this is true whatever operating system you use.
With the launch of an all new app for Linux, Proton VPN is offering users of the open source OS greater functionality and a more intuitive interface. The Proton VPN Linux app natively supports Proton VPN's core security and privacy features.
HyperX launches Clutch Gladiate RGB Gaming Controller for Xbox and PC

HyperX has unveiled its latest product -- the Clutch Gladiate RGB Gaming Controller. This new wired controller is not just a treat for the eyes with its transparent design and customizable full-body RGB lighting but also a precision controller designed to enhance the gaming experience for Xbox users.
Sean Peralta, HyperX's Director of Product Management, emphasizes that the Clutch Gladiate RGB is "crafted to provide players with an immersive gaming experience and extensive customization options." Peralta adds that the controller is, "Designed to cater to every gamer's unique preferences and style, it gives gamers complete control and elevates their gameplay to new heights."
TCL's eye-friendly NXTPAPER 11 Android tablet now available for purchase

In an era where digital screens are as ubiquitous as the air we breathe, TCL Mobile is stepping up with a compelling proposition -- a tablet that's easy on the eyes without sacrificing performance. Enter the NXTPAPER 11, now hitting the digital shelves of TCL.com at a wallet-friendly $229.99.
TCL's NXTPAPER technology isn't just another incremental upgrade; it's a thoughtful response to our ever-increasing screen time. The NXTPAPER 11 tablet significantly cuts down harmful blue light exposure by up to 61 percent, a boon for the digital workforce and binge-watchers alike. With a matte finish and textured surface, this device ditches the glossy sheen of traditional tablets for an e-reader-like experience that's less taxing on the eyes.
IT pros worry about Kubernetes security

A new survey of 800 security and IT leaders from large organizations shows 76 percent of security and IT pros believe we are heading towards a cloud reckoning in terms of costs and security.
The study from Venafi finds that 84 percent believe Kubernetes will soon be the main platform used to develop all applications. But, three-quarters worry that the speed and complexity of Kubernetes and containers is creating new security blind spots.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




