
2023 Call for Code winners announced
The sixth annual Call for Code Challenge launched back in February with a focus on developing AI-powered technology projects that address sustainability to help fight climate change.
Today sees IBM, United Nations Human Rights, and the Linux Foundation announce the winners in the challenge's three categories -- Developer, University, and Independent Software Vendor/Startup.

Wikipedia reveals its most popular articles of 2023
Wikipedia, the world's largest free online encyclopedia, has unveiled the most popular articles of 2023. The list provides a unique snapshot of the global events, personalities, and trends that captured the world's attention throughout the year.
The data, released by the Wikimedia Foundation, reveals a diverse range of topics that were most sought after by the site's billions of users worldwide.

SOUNDPEATS GoFree2 open-ear wireless headphones get HUGE launch discount
Just in time for Christmas shopping, SOUNDPEATS today launches its newest product: the GoFree2 headphones. These have an open-ear design; a feature that enables users to immerse themselves in their favorite music while maintaining awareness of their surroundings. This design is beneficial for safety-conscious users who want to enjoy their tunes without being cut off from the world around them.
At the heart of the GoFree2 are its 16.2mm dynamic drivers, complemented by advanced low-frequency enhancement technology. These components work together to produce a sound that promises to not only be crisp and detailed, but also rich in bass. You can expect a dynamic audio experience.
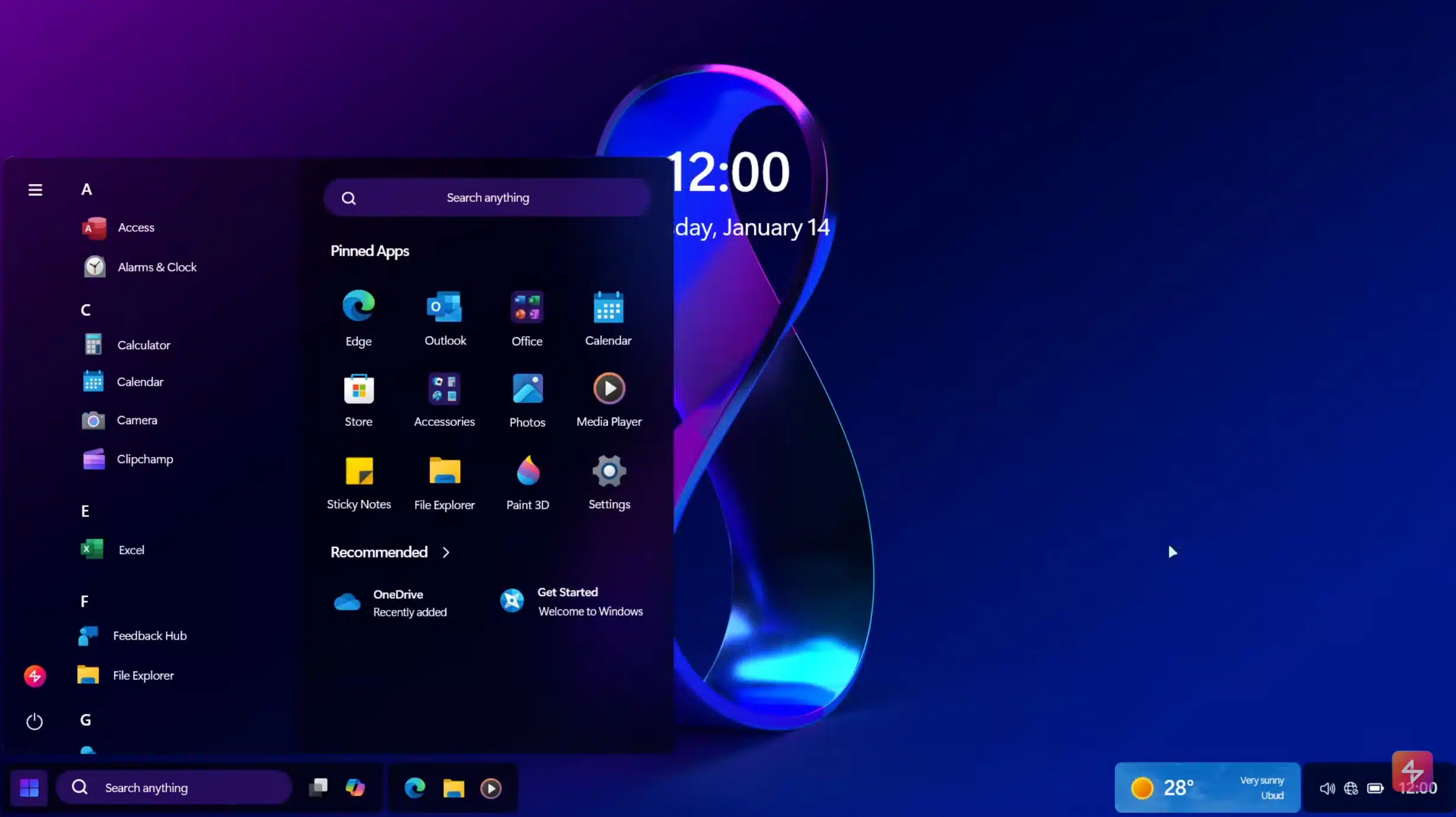
Watch Windows 12 (2024) being installed
There's been a lot of talk about Windows 12, Microsoft's inevitable successor to Windows 11. Most recently, my colleague Sofia Wyciślik-Wilson reported that Microsoft plans to release the new operating system in June 2024, to ride the AI PC wave.
Two months ago, Intel let slip about Microsoft’s 'Windows refresh' plans, believed to refer to Windows 12. If you’re wondering what the new OS might look like, we have an idea.

Microsoft finally confirms Windows bug that renames printers and forcibly installs the HP Smart app
If you have noticed that Windows suddenly thinks you have an HP LaserJet M101-M106, you are not alone. The same is true if you've spotted that the HP Smart app has installed itself on your computer.
These are issues that have been affecting users of Windows 10 and Windows 11 for a little while, but Microsoft has only just acknowledged that a problem exists.

Kensington launches SD5800T Thunderbolt 4 and USB4 Quad Video Docking Station
Kensington has launched the SD5800T Thunderbolt 4 and USB4 Quad Video Docking Station, which can support up to four 4K monitors simultaneously. It offers a zero-footprint mounting option and integrated lock slots for added security. The dock, which can be oriented horizontally or vertically, features up to 98W of power delivery.
In terms of monitor support, the SD5800T provides dual HDMI and DisplayPort (DP) ports, accommodating various setups. This includes quad 4K @ 60Hz or single 8K @ 60Hz with DSC enabled on Windows laptops, and dual 6K @ 60Hz on certain MacBook models.

Cisco launches AI security assistant for enterprises
As cyberattacks continue to evolve so defenses need to change to keep up. In many cases that means adopting AI.
Enterprise networking and security company Cisco is the latest to embrace this with launch of Cisco AI Assistant for Security.

Network security is ripe for automation -- except when it isn't [Q&A]
According to one analyst estimate, the market for network automation tools will grow nearly 23 percent annually from 2022-2030.
While many IT professionals are familiar with automation of business processes, they are likely less familiar with its applications in network operations (NetOps) and security. As automation technology is maturing, organizations are using network automation solutions to transform their core workflows, including troubleshooting, change management and network security, for more efficient and effective network operations.

Microsoft opens up Extended Security Updates to consumers so everyone can pay for Windows 10 support
With support for Windows 10 coming to an end in under two years, Microsoft has been trying to encourage everyone to upgrade to Windows 11. The reality is that this is not something that all Windows 10 users want to do, and it is not possible for many because of hardware requirements.
Now Microsoft has relented. The company has made a somewhat surprising move in giving all Windows 10 users the chance to pay for Extended Security Updates (ESU) when Windows 10 reaches end of service. Until now, the ESU program has only been available to larger organizations and enterprise customers. In opening it up to home users, Microsoft is effectively admitting that it foresees large numbers of people continuing to stick with Windows 10 -- so the company has decided to try to profit from this fact.

Micron unveils 3500 SSD
Today, Micron unveils the 3500 NVMe solid state drive. This SSD leverages 232-layer NAND to meet the demanding requirements of business applications, scientific computing, high-end gaming, and content creation.
The 3500 SSD will be available in an M.2 form factor and offered in capacities of 512GB, 1TB, and 2TB. The drive features the Micron 3D TLC NAND Flash and operates on the PCIe Gen4 x4 interface with NVMe 2.0c.

Multicloud by design: Making a cloud environment that truly works
We all know the saying: you can’t have it all. The same applies to the cloud providers -- a single one cannot give and be everything you need.
Increasingly we are seeing customers demand higher standards from their cloud services in an effort to reduce savings and security risks, as well as enhance their flexibility. In a landscape that is always changing, many sectors are feeling the need to keep up with technology or even try to be one step ahead of it. To meet these complex requirements, companies may want to look a little wider than their single cloud provider set-up and into the world of multicloud.

Microsoft Bing's new Deep Search feature uses AI to 'disambiguate' complex search queries
Microsoft is introducing AI into most of its products and services, and its search engine, Bing, is one of the tools that benefits the most from this addition.
Today, the search giant takes things a step further still, with the introduction of a new AI-powered feature in Bing called, Deep Search. This addition aims to provide more relevant and comprehensive answers to complex search queries, boosting the existing web search rather than replacing it.

Get 'Mastering Windows 365' (worth $39.99) for FREE
Written by experts from the Windows 365 product group and a seasoned Microsoft MVP, this book offers a unique perspective on the features, functionality, and best practices of Windows 365.
Drawing from their extensive professional experience and insight, the authors provide invaluable knowledge for those eager to learn about the next generation of cloud computing.
AI and automation are top enterprise priorities
According to a new report from Digitate 90 percent of IT decision-makers plan to deploy more automation, including AI, in the next 12 months.
Based on a survey of 601 US-based IT decision-makers in organizations with more than 1,000 employees and conducted with Sapio Research, the study finds 26 percent of respondents plan to implement machine-operated tasks that require limited human input or fully transition to autonomous systems in the next five years.

AIDA64 Extreme Edition 7.0 unveils customizable toolbar and updated support for latest AMD and Intel chipsets
Budapest-based FinalWire Ltd has released a major new version of its Windows diagnostic and benchmarking tool with the release of AIDA64 Extreme Edition 7.00 and AIDA64 Business Edition 7.00.
The landmark release is marked with a revamped user interface offering configurable toolbar. Users can navigate the various parts of the program using the left-hand pane, with sections spanning hardware, software and OS.



