
Illuminate your Windows 11 experience with Dynamic Lighting
As technology continues to evolve, so do the ways in which we interact with our devices. The integration of "Red, Green, Blue" (RGB) lights within various gadgets has opened up a realm of personalization, allowing users to create unique environments that extend beyond the screen. Microsoft has recognized this trend and with its latest feature update, unleashes the power of Dynamic Lighting on Windows 11.
The Dynamic Lighting feature in Windows 11 embodies a step towards a more unified and interactive user experience. It finally grants users the liberty to control their RGB devices right from the Windows Settings -- something many of us have been waiting for. This means you can now extend your Windows accent color to the devices around you, synchronize RGB effects across devices from different brands, and have finer control over how apps manage your device’s lights.
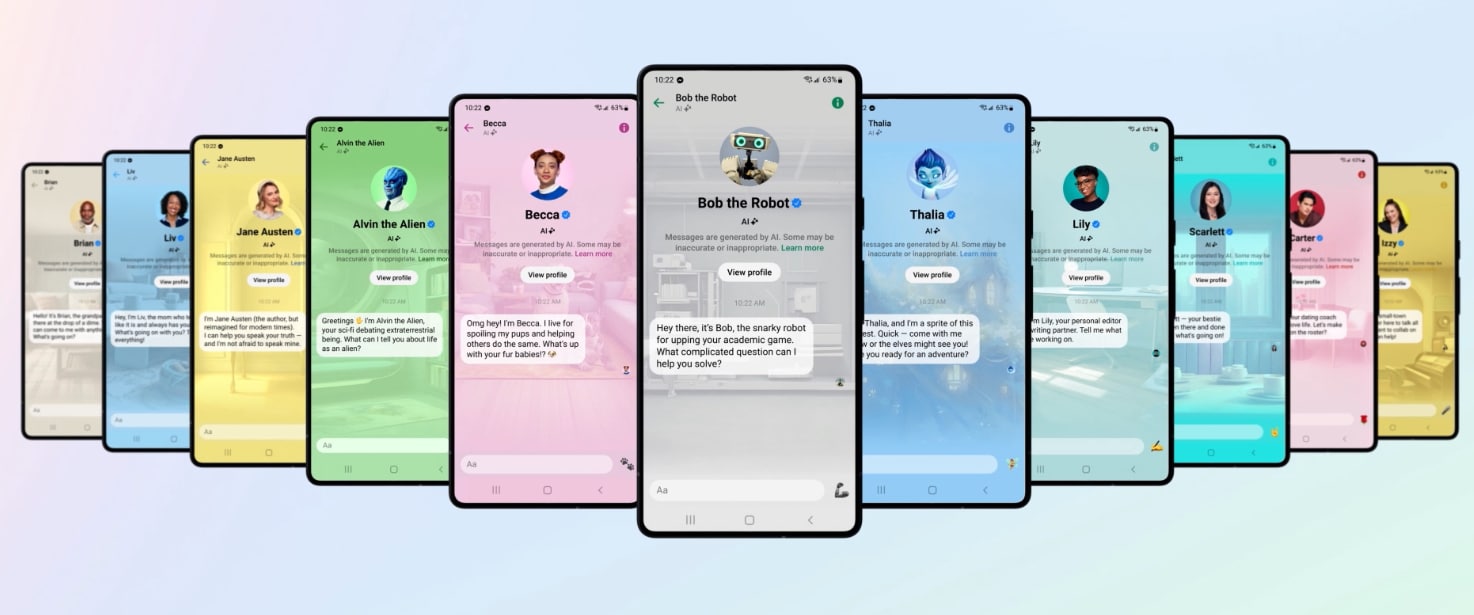
Meta uses AI to bring stickers and celebrity chat buddies to its apps
Today, at the Connect event, Meta unveiled a promising suite of AI experiences sprucing up its family of apps and devices, charting a thrilling course towards more personalized and interactive digital realms. The announcements encompass AI stickers, a new conversational assistant named Meta AI, 28 additional AIs with distinctive personalities, and tools for creators and developers to craft their own AI entities.
Starting with the whimsical, Meta is rolling out AI stickers that breathe fresh energy into your chats and stories. Emu, Meta's image generation model, along with technology from Llama 2, morphs simple text prompts into a variety of high-quality, bespoke stickers. This feature, soon to grace WhatsApp, Messenger, Instagram, and Facebook Stories, is a delightful way to augment digital expressions.

Linux Mint Debian Edition 6 is released with a troubling lack of new features
Today marks the release of Debian 12-based LMDE 6, codenamed "Faye." This new release brings with it a host of information regarding installation, locked root account procedures, and more. However, there is a growing concern about the apparent lack of new features announced.
Despite sharing some known issues and tips, there are absolutely no new features announced in the release notes. And so, there is a legitimate worry: what new does LMDE 6 bring to the table? While stability and reliability are core to the Debian base, users look forward to fresh and innovative features with each new release. This anticipation is tinged with disappointment as the details of LMDE 6 emerge without a showcase of novel functionalities.
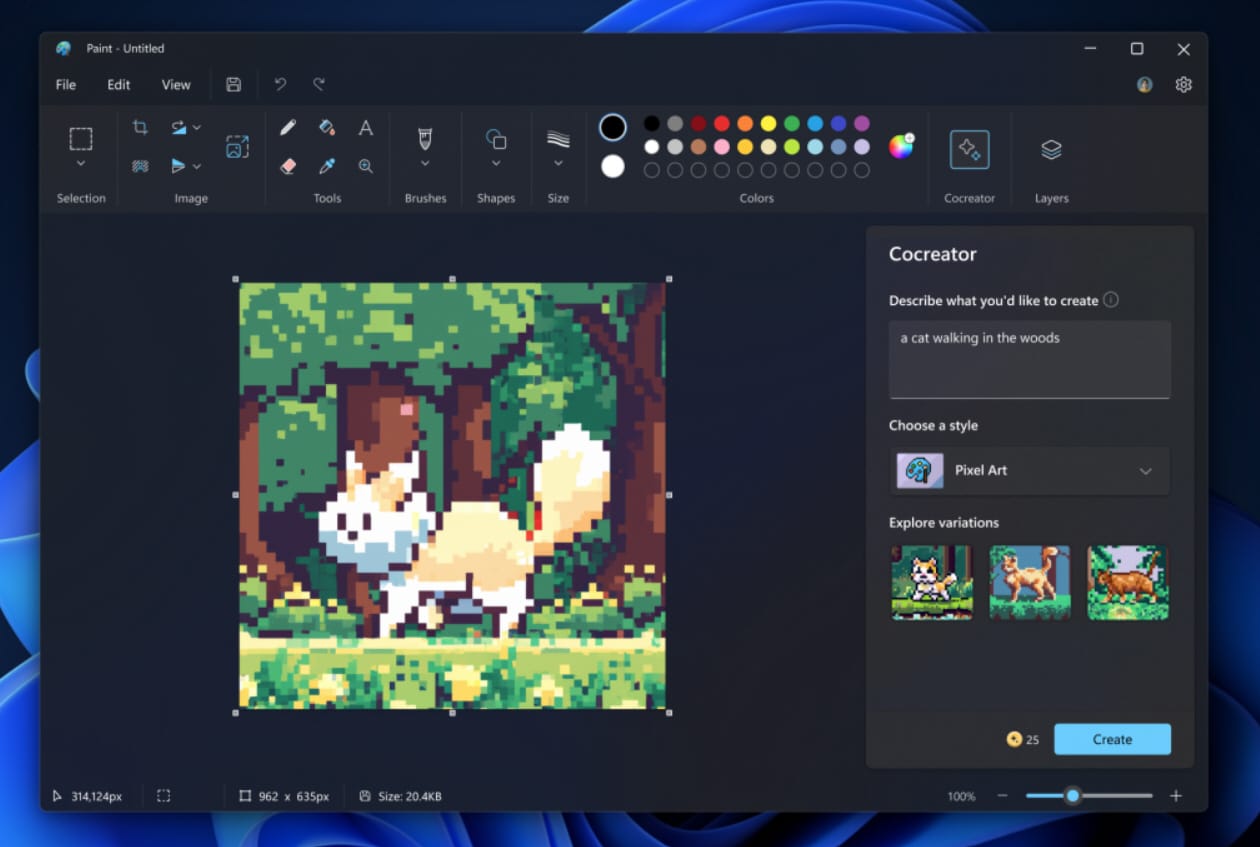
Microsoft begins rolling out its major Paint update, with AI-powered Paint Cocreator
Following on from yesterday’s Windows 11 update which saw the arrival of the AI-powered Copilot, Microsoft has today released a major update to its venerable Paint app.
The highlight of this new build is Paint Cocreator, an AI-powered feature that uses DALL-E technology to help users create stunning artwork simply by describing what they want in a few words.

Panos Panay's shift to Amazon could signal the death of Microsoft Surface
In a startling development, Panos Panay, the mind behind Microsoft’s Windows and Devices division, has officially jumped ship to Amazon. Yes, folks, the rumors were true. Amazon CEO Andy Jassy announced today that Panay will, in fact, be helming the Devices and Services business, replacing Dave Limp later this year.
While on the surface this seems like a significant win for Amazon, it might be worth pondering the implications of Panay’s exit from Microsoft. With nearly two decades at Microsoft, Panay’s sudden move raises eyebrows and stirs concerns regarding the internal dynamics at Microsoft.

Get 'Mastering Linux Security and Hardening -- Third Edition' (worth $35.99) for FREE
The third edition of Mastering Linux Security and Hardening is an updated, comprehensive introduction to implementing the latest Linux security measures, using the latest versions of Ubuntu and AlmaLinux.
In this new edition, you will learn how to set up a practice lab, create user accounts with appropriate privilege levels, protect sensitive data with permissions settings and encryption, and configure a firewall with the newest firewall technologies.

Conquering disruption: How to build a more resilient business
From COVID-19, the energy crisis and widespread strikes, business continuity managers have been kept busy in the last few years. And the impact of these events, as well as ongoing threats like cyber attacks, mean that continuity planning is a regular topic on boardroom agendas.
Business resilience is now crucial to guaranteeing continuity and sustainable operations. In fact, according to PwC’s Global Crisis Survey 2023, 89 percent of organizations state business resilience as one of their key strategic priorities. But what are the key factors at play in building a more resilient organization?

Enterprises have ambitious plans for machine learning but the road isn't a smooth one
A new survey looks at how organizations find business value from machine learning (ML), how they plan to invest in the near term, and the challenges they expect to face in achieving their ambitious goals for getting new ML initiatives into production.
The study, conducted by NewtonX for Wallaroo.AI, asked asked chief data officers, chief analytics officers and leaders responsible for AI business outcomes in US private enterprises how they plan to invest in the near term and the challenges they expect to face in achieving their goals for getting new ML initiatives into production.

Xiaomi 13T Series Android smartphones have Leica cameras for professional-level photography
Xiaomi has unveiled its new 13T Series smartphones, made with the help of Leica to help customers take great photos. These phones aim to capture the classic Leica photo experience.
The Xiaomi 13T Series makes professional-level photography accessible. Both the Xiaomi 13T Pro and Xiaomi 13T have a triple camera setup with lenses made with Leica. This includes a 50MP wide angle and telephoto camera, and a 12MP ultra-wide-angle camera, suitable for panoramic shots and landscape photos. The cameras support high dynamic range shooting and have a wide color range for capturing detailed and vibrant photos.

Account takeover attacks surge by over 300 percent
Account takeover (ATO) attacks jumped a massive 354 percent year-on-year in Q2 2023 according to the latest quarterly Digital Trust and Safety Index from Sift.
Analysis across Sift's global network shows the fintech and food and beverage categories experienced especially large increases. ATO spiked 808 percent across fintech, hitting loyalty sites and crypto, and opening the gate to downstream payment fraud, while the food and beverage industry saw a 485 percent increase in ATO.

Why bad bots and open banking are creating opportunities for cybercriminals [Q&A]
We all know that bad bots are, well… Bad. But open banking is supposed to be good, giving consumers more control over their finances. Combine open banking and bad bots though and you have opened up a world of new threats to banks, customers, and their data.
We spoke to Alan Ryan, AVP for UK and Ireland at Imperva, about how open banking has created new opportunities for cybercriminals, and why the traditional siloed approach to security needs re-appraising.

Zyxel Networks launches WiFi 6-enabled USG FLEX 100AX Firewall
Zyxel Networks has rolled out an impressive update to its lauded ZyWALL USG FLEX 100 firewall series, with the introduction of WiFi 6-enabled security firewalls. The newly announced USG FLEX 100AX Firewall not only supports WiFi 6 (802.11ax) for enhanced wired and wireless solutions but also guarantees comprehensive security for small- and medium-sized business networks.
This innovative firewall aligns with Zyxel's scalable Nebula Cloud Networking Solution, allowing for centralized security policy provisioning and distributed network management from a single dashboard. The USG FLEX 100AX, with WiFi 6 connectivity delivering speeds up to 1800 Mbps, promises robust VPN connectivity and advanced networking security features for various remote work locations, reducing the attack surface and inhibiting threat propagation.
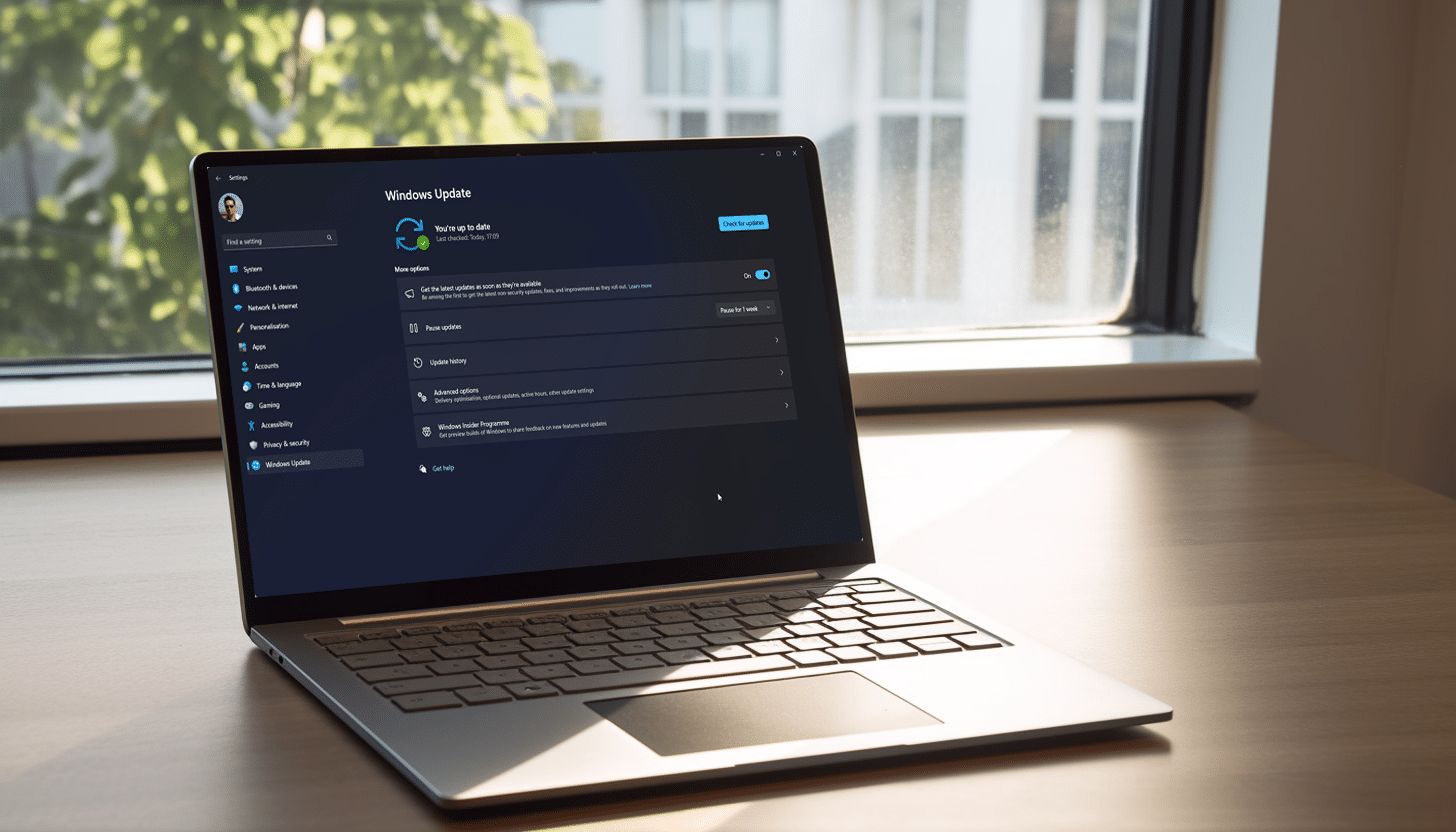
How to get the big Windows 11 update, with Copilot AI and other features
Today is a huge day for Windows 11 users, as it’s when Microsoft begins rolling out a major update for the new operating system, bringing the power of Copilot to Windows, as well as other new AI powered experiences to apps.
Provided you have a device running Windows 11 version 22H2, you can install these non-security updates -- there will be more than one -- as soon as they start to roll out.

The vital role of multi-factor authentication in your security stack
Stop me if you have heard this story before. A threat actor sends a crafty phishing email. An unsuspecting end user clicks a hyperlink in the email and enters their username and password, unknowingly providing those credentials to the threat actor. The threat actor then uses these credentials to gain access to all sorts of personal or company sensitive information. While this may be a "tale as old as time", it’s still happening today. Literally every day. According to the latest Verizon Data Breach Report, stolen credentials is still the primary way attackers gain access to organizations.
The fact is passwords continue to be a target for threat actors and are becoming increasingly vulnerable to attack. Threat actors leverage techniques like phishing campaigns, brute force attacks, information-stealing malware, and social engineering to gain access to user credentials. End users often contribute to the problem by using easily guessed passwords or reusing the same passwords across multiple accounts making a threat actor’s job easier. The bottom line is putting your data protection hopes into a single username and password is a foolish endeavor when the need for more robust authentication controls is evident.

Remote work creates extra challenges for network teams
The ongoing shift to hybrid and remote work environments has resulted in key changes to the roles and priorities of network administrators in order to address new connectivity challenges and prioritize and preserve a secure, productive end-user experience.
New research by Enterprise Management Associates (EMA) and Auvik shows 73 percent of network professionals reported an increase in workloads, either slightly or significantly, following the shift from traditional to hybrid work environments.


