To err is human, and that's what hackers are counting on

It's understandable if you've made thwarting ransomware your top cybersecurity priority for 2022. The number of successful ransomware attacks, which encrypt computers until victims pay the attackers to unlock their data, surged last year. Ransomware payments reported by banks and other financial institutions (PDF) totaled $590 million for the first six months of 2021, surpassing the $416 million for all of 2020.
When it comes to protecting your data center and endpoints (e.g., employees' laptops and mobile devices), ransomware should be top of mind. But when securing your cloud environments, don't worry about ransomware -- worry about the misconfigurations that lead to devastating data breaches.
Governing the ungovernable: Why cybersecurity must adapt to identity sprawl

You may remember the Colonial Pipeline ransomware attack. Launched in May of last year, DarkSide’s attack cost the Colonial Pipeline Company something on the order of $4.4 million dollars (though the FBI was able to claw some of that money back). The attack set the stage for President Biden’s Executive Order on cybersecurity, shut down pipeline production, and caused panic buying across the Southeast.
That’s how the Colonial Pipeline attack ended. It began far more simply: with hackers breaching the company’s networks through a virtual private network (VPN) account that was no longer actively in use.
Effective Contract Lifecycle Management (CLM) requires innovative, adaptable and knowledgeable solutions

As companies work to beat out the competition, taking a deeper look into contract management can be a driving force of success. When contracts accidentally expire or key milestones are missed, it can severely handicap business. Effective contract management improves workflow efficiency and leads to a more progressive and well-functioning organization.
Contract Lifecycle Management (CLM) is one of the fastest-growing and important innovations in business today. Spurred by the digital revolution advancing across virtually every key business sector, the CLM market is expected to grow over 13 percent annually for the next decade. But what is it, and why is it such an essential tool for businesses to utilize?
New solution helps guarantee electronic documents

Electronic documents are becoming more common in business, but this doesn't eliminate the risk of forgery or tampering.
UK-based Borderless Security is launching a new e-signature solution that makes use of blockchain technology to create a safe, secure and convenient solution for signing paperwork, contracts and legally binding documents.
What the UK's revised security guidelines mean for business [Q&A]

Changes to the UK government's Cyber Essentials security certification scheme come into force today. They include things like guidelines on remote working and hybrid approaches, rules for cloud service accounts -- such as deploying multi-factor authentication -- and speeding up critical patch deployments for critical and high severity vulnerabilities
We talked to Karl Alderton, technical account manager at security and compliance specialist Qualys to find out more about how these changes will affect businesses and what they need to do in response.
Reacting with confidence to a new Trojan horse cyber threat

It’s the sophisticated technology that enables the virtual assistant on your kitchen counter, the recommendation engines on your favorite streaming services, and so much more -- and there’s new evidence hackers can use it as a Trojan horse to deliver malware. Because this technology is increasingly embedded not just in your movie nights, but critical industries from healthcare to energy and banking, its newly understood vulnerability is grave news.
But do we tear it out by its roots? Isolate it? No. Artificial intelligence is too important for that -- particularly, ironically enough, in cybersecurity defense. We have no choice but to confront the Trojan horse gambit and block it.
6 IoT trends for 2022

The Internet of Things (IoT) has seen incredible growth in a relatively short period. Despite being fairly new, smart devices are everywhere in commercial and consumer circles, and they show no signs of stopping.
While the IoT’s growth may remain unchanged in 2022, it will shift and evolve. Here are six trends that will shape the IoT this year.
Microsoft seems to have changed its mind about killing off the Control Panel in Windows 11

Microsoft has been wielding its axe at the Control Panel in Windows for a while now, gradually migrating options to the Settings app. This is not something that has been universally welcomed by Windows 11 users, so a (slight) change of heart will come as welcome news for fans of the Control Panel.
While there are numerous settings that now have to be accessed through Settings, one Control Panel option has been given something of a reprieve. The applet in question is Network Connections (ncpa.cpl).
MINISFORUM launches AMD Ryzen-powered mini desktop PC running Manjaro Linux

When it comes to computers, there are two things that really get my motor running -- AMD processors and Linux-based operating systems. So when I learned MINISFORUM had begun selling a diminutive AMD Ryzen-powered desktop that comes with Manjaro Linux pre-installed, my heart skipped a beat. It is very exciting to see yet another computer being offered with Linux rather than Windows.
Called "DeskMini UM700," the mini Linux desktop PC is being offered in three configurations -- all powered by the very capable Ryzen 7 3750H APU -- with pricing starting at less than $500. In other words, the tiny computer isn't just capable, but affordable too.
Security is the top concern for CIOs and budgets are increasing

A new study from IDG Communications finds that more than half (57 percent) of CIOs surveyed indicate the need for security improvements as a top reason for increasing tech budgets this year.
This is followed by upgrading outdated IT infrastructure (48 percent) and investing in new skills and talent (48 percent). In addition, over three-quarters (76 percent) think their involvement with cybersecurity will increase over the next year, along with their involvement in data privacy and compliance (71 percent).
Best Windows apps this week
Four-hundred-seventy-four in a series. Welcome to this week's overview of the best apps, games and extensions released for Windows 10 and 11 on the Microsoft Store and elsewhere in the past seven days.
Microsoft released several out-of-bands patches this week that address VPN connection issues and other issues.
Insurance businesses targeted for customer details

Insurance companies exist to offer protection but they're increasingly having to protect themselves against a range of cyberattacks.
A new report from IntSights looks at the threats faced by insurance businesses and why they’ve become a particular problem in recent times.
Microsoft reveals the most dangerous, pointless and misunderstood group policies for Windows 11

There are a huge number of ways to customize, optimize and tweak Windows, some of which involve using third party utilities, while others rely on tools that are built into the operating system -- like Group Policy Editor.
System administrators have used group policies to implement a wide range of settings for a long time now, but there are some that should be avoided. Microsoft has shared information about some of the legacy group policies that should not be used; some because they have no effect at all, some because they have unwanted or unexpected side effects. Take a look through the list and see if you need to make any changes to the policies you have put in place.
Why enterprises need to take control of their cloud costs [Q&A]

Modern businesses are more than ever reliant on using the cloud, but it's easy to develop an 'out of sight out of mind' mentality to costs when systems are not hosted on site.
We spoke to Archera CEO Aran Khanna to find out about the challenges businesses face with cloud costs and how they can keep them under control.
DevToys is like an open-source Microsoft PowerToys for developers
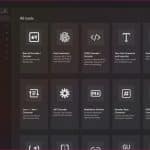
We have written about PowerToys quite a lot here on BetaNews. Microsoft has put a lot of work into building a useful collection of tools and utilities for Windows 11 users, and it is incredible to see each new addition and development.
PowerToys is aimed at power users looking to get more from their computers, and now there is a utilities collection designed with developers in mind. Described as a "Swiss Army knife for developers", DevToys comprises 14 outrageously useful tools and has just hit a major milestone.
BetaNews, your source for breaking tech news, reviews, and in-depth reporting since 1998.
© 1998-2025 BetaNews, Inc. All Rights Reserved. About Us - Privacy Policy - Cookie Policy - Sitemap.




