Failing to attract security experts may prove costly for businesses

A new report from Kaspersky Lab has found that large businesses that struggle to attract sufficiently skilled security experts end up paying up to three times more to recover from a cyber security incident.
The much talked-about skills gap in the security industry continues to cause problems for businesses, as increasing wages, a general shortage of expert availability and the need for more specialists are all prevalent.
New key hack exposes 100 million Volkswagen cars

Back in the day, people had to walk into a bank in order to rob it. They also had to walk into a car in order to steal it. Nowadays, people rob banks from the comfort of their home (or their parents’ basements), and it’s only a matter of time before they start hijacking cars the same way.
According to a couple of researchers, whose work has been covered by Wired recently, we’re already halfway there -- a new vulnerability has been found which allows hackers to remotely unlock 100 million Volkswagen cars.
Moon Express gets FAA 'approval' for Moon mission

Last week Moon Express, a contender for the Google Lunar X-Prize (GLXP), announced that the company had received interagency approval from the White House, Federal Aviation Administration (FAA), Department of State and other U.S. government agencies "for a maiden flight of its robotic spacecraft onto the Moon’s surface to make the first private landing on the Moon".
This heady announcement got a lot of press including this story I am linking to because it was in the New York Times, the USA’s so-called pape of record. If the Times writes "gets approval to put robotic lander on the Moon" it must be true. Only this story isn’t true. Yes, the FAA kinda-sorta gave Moon Express permission to land on the Moon. But by the same token, the FAA has no power to deny Moon Express -- or anyone -- the right to land on the Moon. It’s not in their jurisdiction.
Most smart car vulnerabilities can be easily exploited

Remember that cyber-experiment when a couple of hackers managed to take control over a speeding car in the middle of the highway?
Well, IOActive has published a study, entitled Commonalities in Vehicle Vulnerabilities, after three years of testing, and the results are quite scary.
Most businesses experience four monthly disruptions

Internet performance management company Dyn says businesses are still under a lot of disruptions, which severely hurts their internet performance, resulting in unsatisfied customers.
The company polled 100 IT senior IT leaders from enterprises across the United States, and released the results in a report titled "Constant Website Disruptions Demand a New Kind of Performance Management".
Polymail for Mac wants to provide a cross-platform email experience to die for

If you’re still looking for the perfect email experience on Mac and iOS, then Polymail, Inc may have something to fill the gap left by Mailbox’s unceremonious exit back in February. It’s just officially released Polymail for Mac 1.01 after around six months in beta.
Polymail for Mac joins existing iPad and iPhone client, Polymail for iOS 1.21, to provide a cross-platform email client for Apple fans.
What's the point of Twitter? Twitter explains...

Twitter is worried. It's worried that while it is a well-recognized brand, a disturbingly large number of people have no idea what Twitter is actually for. What is the point? Getting slightly meta, the company today explains its raison d'être and tries to clear up some common misconceptions.
'What misconceptions are there about Twitter?', you may well ask. That it is a social network. (It ain't.) That you have to use it every day. (Seriously?) As Twitter says, 'We realized we had some explaining and clarifying to do!'
Twitter expands its live video streaming of college sporting events

College sports is big business -- television, radio, merchandise, etc. While many Americans are fans of professional sports such as the NFL and NBA, not every state has such a team. What every state in the union does have, however, are college athletic programs. Believe it or not, in places like Florida where there are plenty of pro teams, many folks are more wild for the Gators or Seminoles than the Dolphins or Heat.
Today, Twitter announces a media partnership with the Silver Chalice-owned company "Campus Insiders". This deal will bring the live video steaming of more than 300 collegiate sporting events to the social network, bolstering its existing offerings.
Capture and explore network traffic with Microsoft Message Analyzer

Microsoft Message Analyzer is an expert-oriented tool for capturing, displaying and analyzing network traffic, file activity, Windows Events and device activities on Windows 7 or later systems.
This data may be filtered and presented in grids, charts, graphs, timelines and more. While the program is aimed at developers and system admins, if you’re comfortable with tools like Sysinternals Process Monitor then you could also find it handy.
Investigate suspect EXEs with Professional PE Explorer

Professional PE Explorer is a portable tool which allows investigating Windows executables including EXE files, SYS, DLL and more.
The download is so tiny you’ll wonder if it’s broken -- 78.1KB, really? -- but no, this is all you get. Unzip it and run PPEE.exe to get started.
Euclid Connect delivers personalized in-store experiences via Wi-Fi

Part of the reason for the success of online retailers is the ability to gather information on customers so that they can be targeted with appropriate offers.
Retail analytics and engagement specialist Euclid Analytics is launching a new platform that aims to give brick and mortar retailers some of the same advantages.
Mandelbrot Fractal is a pure JavaScript fractal explorer
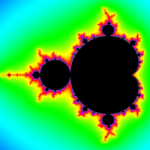
Mandelbrot Fractal is an open-source fractal generator with a difference: its spectacular images are produced using pure JavaScript, no external libraries or other oddball dependencies involved.
This makes for a very simple structure, essentially just an index.html with a supporting app.css and two .js files.
Ransomware victims pay less than they expect

If you’re a cyber-criminal looking to enter the ransomware game, but not sure how much money you should demand for the unlocking of a victim’s files, don’t worry. Kaspersky Lab has done the research for you.
The security firm, together with B2B International, says people value their smartphone data, on average, at $682. In 39 percent of cases, the figure exceeds $1,000. On the other hand, cyber-criminals which have managed to lock a victim’s device through ransomware, usually demand $300.
Enterprises leave vulnerable industrial control systems exposed online

Industrial control systems (ICS) are not supposed to be connected to the Internet, Kaspersky Lab says, as it opens a sea of opportunities for hackers. Such systems are run by energy, transportation, aerospace, oil and gas, chemicals, automotive and manufacturing, food and drink, governmental, financial and medical institutions, and should be, for the sake of security, run in a physically isolated environment.
However, Kaspersky Lab says that is not the case, and that it has found 13,698 ICS hosts exposed to the Internet, which very likely belong to large organizations. More than nine in ten (91.1 percent) host remotely-exploitable vulnerabilities, and 3.3 percent contain "critical and remotely executable vulnerabilities".
Skype for Business use on mobile expected to double by 2018
While Skype remains the most popular VoIP tool, the Skype for Business mobile client has been dogged by ongoing quality and technical issues that have slowed its rollout.
A new survey by Unify Square and Osterman Research finds that 30 percent of IT teams' total time spent troubleshooting the Skype platform is devoted to the mobile client.
Recent Headlines
Most Commented Stories
© 1998-2024 BetaNews, Inc. All Rights Reserved. Privacy Policy - Cookie Policy.