Looking for that last minute Christmas gift? Save big in the Downloadcrew Software Store this Holiday Season!
In the realms of understatement, "2020 has been a hard year" rules supreme. No one needs a recap as to why, but as many of us continue to be subject to restrictions preventing us from getting out to the shops, coupled with well-publicized delays and disruption to mail services, getting Christmas sorted for our loved ones has been particularly challenging this year.
And that’s where we come in: if you’re stuck within a "stay at home" area, worried about missing the last post or looking for a last-minute gift, the Downloadcrew Software Store has you covered. You can order directly from our digital store and have the gift sent either to yourself or directly to your friend or family member -- it’ll arrive within minutes, even on Christmas Day!

Fraudulent eCommerce purchase values jump 70 percent over 2019
2020 has been a boom year for eCommerce, with average daily transaction volumes equal to 88 percent of the volume achieved during Black Friday weekend 2019 according to digital trust and safety specialist Sift.
It also finds the average attempted fraudulent purchase value has risen to over $700 from October through November 2020, a 70 percent year-on-year increase compared to the same period in 2019.
How the MITRE Shield can help organizations better address their adversaries [Q&A]
The MITRE ATT&CK framework is now used by many organizations to help them understand and counter threats. Less well known is the latest addition, MITRE Shield.
We spoke to Carolyn Crandall, chief deception officer and CMO at Attivo Networks to find out more about how this can be used along with MITRE ATT&CK to better address adversaries.

Pandemic accelerates moves to the cloud
The COVID-19 pandemic has been a major influence on spending and digital transformation plans in 2020 with many businesses speeding up plans to move to the cloud.
A new study from BillingPlatform of 300 CFOs and senior finance executives shows that this trend is likely to continue into 2021. Respondents named their three top priorities as investing in cloud-based technologies (42 percent), identifying ways to drive higher revenue through new products and services (41 percent) and reducing operating costs or capital investments (36 percent).

IBM helps businesses prepare for next generation encryption
IBM Security is launching a new service that allows companies to experiment with fully homomorphic encryption (FHE) -- an emerging technology that allows data to remain encrypted while being processed or analyzed in cloud or third-party environments.
IBM Security Homomorphic Encryption Services provide companies with education, expert support, and a testing environment to develop prototype applications that can take advantage of FHE.

The best password managers 2021
Using unique passwords is essential for keeping documents, data and accounts safe. However, it can be hard to remember them all.
Using password managers is the ideal solution for keeping everything organized. Now that the new year is nearly upon us, it’s time to take a look at the best password managers for 2021.

HBO Max finally comes to Roku, and The Matrix 4 is on the way
There are way too many streaming services nowadays. If you want to subscribe to them all, it will cost a small fortune. For instance, there is Netflix, Hulu, Disney+, and more. One of the newer services is HBO Max, which is already wildly popular. It will only gain in popularity, as several Warner Bros. movies will debut on the service simultaneously with theaters in 2021. This includes the highly anticipated Matrix 4.
With all of that said, HBO Max has not been available on Roku, which is absolutely tragic. After all, millions on households depend on Roku devices for their streaming services. Today this changes, however, as HBO Max finally comes to Roku. Woo-hoo!

Ubuntu-based Linux Mint 20.1 'Ulyssa' BETA is here with Cinnamon, MATE, and Xfce
Back in October, we told you that Linux Mint 20.1 would be named "Ulyssa." There was excitement about this version of the operating system, especially since the developers planned to release it around Christmas. Unfortunately, there was controversy and drama surrounding Ulyssa too, as we learned the Linux Mint developers were foolishly wasting resources on an IPTV player named "Hypnotix."
So here we are -- Christmas is fast approaching, and today, the Ubuntu-based Linux Mint 20.1 'Ulyssa' BETA finally becomes available for download. The pre-release operating system can be had with your choice of three excellent desktop environments -- Cinnamon, MATE, and Xfce.

On January 1 2021, many famous works including 'The Great Gatsby' by F. Scott Fitzgerald will enter the public domain
January 1 is not only New Year’s Day, but also Public Domain Day. This is the day where certain previously copyrighted works enter the public domain, allowing anyone to use or creatively reinterpret them without needing to seek permission or pay a fee.
In 2021, copyrighted works from 1925 will enter the US public domain, and the list of books, movies and songs included is an impressive one. The BBC has even stated that 1925 could well be the greatest year for books, ever.

Prioritizing AppSec and data governance in 2021
For many organizations, the immediate shift to remote work meant IT pros had to manage a hyper-accelerated, mass cloud migration coupled with large-scale SaaS platform rollouts. Daily users of Microsoft Teams, for example, rose from 75 million to 115 million in less than six months. Now that the first tidal wave of digital transformation has passed, IT and security teams should recalibrate and reprioritize application security and data governance in 2021 and beyond.
And while the pandemic has underscored major SaaS platform security concerns, including a rise in sophisticated cyber threats, research indicates many organizations still struggle with the fundamental tasks needed to secure the workforce -- both remote and on-prem. Here are three common mistakes and how to avoid them.

Enabling zero trust for small and medium enterprises [Q&A]
The move towards zero trust has been one of the big security stories of 2020, driven by a switch to remote work, but so far it has been largely the preserve of bigger organizations.
Now though JumpCloud has added Conditional Access policies to its Directory Platform, enabling IT admins to adopt zero trust security from the same cloud platform that they use to manage and securely connect users to IT resources.
Windows 8 Remastered Edition is better than Windows 10
Microsoft took a big gamble with Windows 8. Back in 2012 the tech giant believed that touchscreens were the way we’d all be interacting with our devices, and so overhauled Windows to give it a touch-first design and a Start screen in place of the traditional Start menu -- which didn’t go down at all well with the Windows faithful.
Although the company relented and eventually added a Start menu and made various other user-requested tweaks, Windows 8 is viewed by many as one of the worst versions of Windows, which is a little unfair as it had much to recommend it.

New spyware seeks to blackmail Android and iOS users
Researchers at mobile device security company Lookout have uncovered a new strain of spyware targeting iOS and Android users in multiple Asian countries.
Called Goontact, it targets users lured to illicit sites and steals personal information stored on their mobile devices in order to carry out sextortion scams.

How to avoid getting caught in ransomware's crosshairs
Paying off a bad actor for successfully implementing ransomware into an organization is the enterprise equivalent of rewarding a bad child who vandalized a home with candy -- but unfortunately, many organizations often have no choice but to pay… and pay a lot.
Technology has enabled asymmetric attacks. In other words, one attacker can federate an attack across many organizations. The attacker needs to get the attack right once -- while the defenders (corporations, governments, hospitals, etc.) need to get their defense right every… single… time!
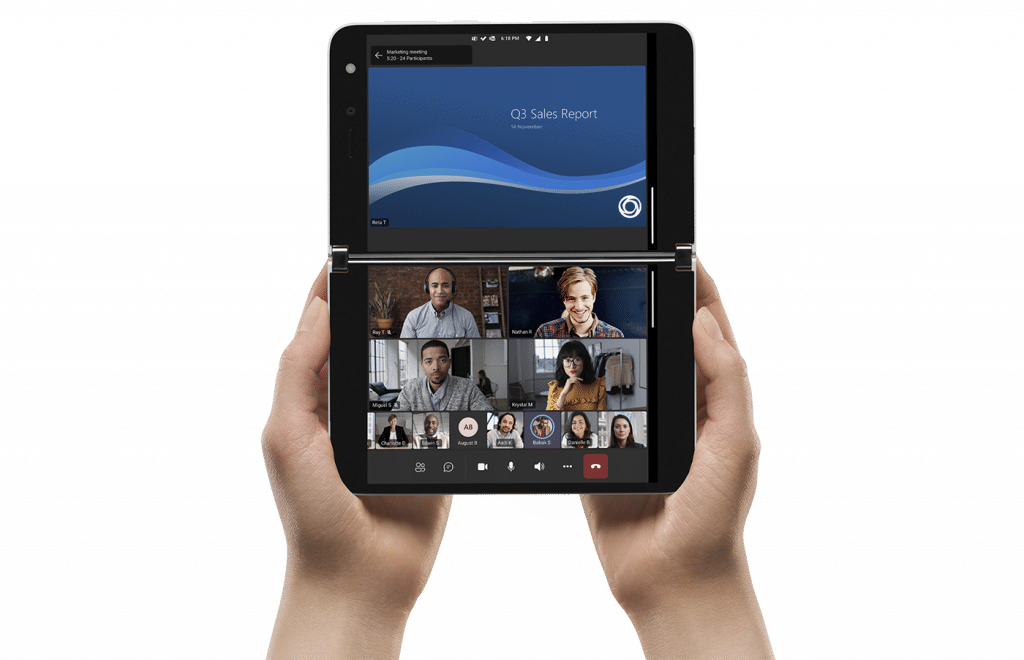
Microsoft foists the Surface Duo and its chunky bezels on more countries
The Surface Duo is a pretty cool device on paper. If you aren't familiar, Microsoft essentially connected two Android smartphones using innovative hinges. Why did the company do this? Well, the goal was productivity -- having two apps running simultaneously on two displays would be great for business use (and entertainment).
Unfortunately, Surface Duo doesn't just exist on paper -- it is an actual product. And for the most part, it has been panned by critics. Its software is reportedly buggy and the hardware durability is questionable -- the damn thing develops cracks. Its bezels are large and unsightly, making it look very outdated. There are reports that the camera is horrible too.


