
Half of US mobile traffic will be scam calls by 2019
Unwanted and scam phone calls are an increasing problem. Analysis by call management company First Orion predicts that nearly half of all calls to mobile phones in the US will be fraudulent in 2019 unless the industry adopts and implements more effective call protection solutions.
Over the past year, First Orion's data shows a drastic increase in scam calls -- from 3.7 percent of total calls in 2017 to 29.2 percent in 2018 -- and that number is projected to reach 44.6 percent by early 2019.

Personal devices are a major threat to mobile IT environments
A new survey finds that 58 percent of respondents believe access to their network from non-corporate and personally owned devices such as laptops, desktops or mobile phones is the highest risk in managing remote users.
The study from trusted access specialist Duo Security shows that while the trend to remote working has created unmatched flexibility and helped organizations attract top talent globally, it has also introduced a major predicament for IT and security teams.

UBports Foundation releases Linux-based Ubuntu Touch OTA-4
Canonical once had an ambitious vision of making Ubuntu a dynamic operating system that would scale to desktop computers, tablets, and smartphones. Unfortunately, this goal was ultimately a failure -- the Ubuntu Touch plan was abandoned. Later, the much-maligned Unity environment was killed off. Why did it all fail? Quite simply, as Microsoft learned with Windows Phone, it is pretty much impossible to compete with Google and Apple in mobile. Android and iOS are just too mature and too good. Ubuntu Touch had no real chance due to a lack of apps and device support.
For those that still own devices compatible with Ubuntu Touch, all is not lost. You see, the UBports Foundation has picked up development. Today, the foundation releases version OTA-4, which is based on Ubuntu 16.04 LTS. It is chock-full of improvements, but unfortunately, despite the "OTA" name, you apparently cannot upgrade over the air.

How technology is changing the way we work
As millennials now become the largest component of the workforce, and as the freelance or 'gig' economy grows, expectations around technology in the workplace are changing.
Cloud communications and collaboration firm Intermedia has produced a report looking at how companies can utilize technology to foster a more collaborative, productive, and accessible workplace, and at the same time help attract and retain top talent.

Ookla: T-Mobile is fastest mobile internet carrier in USA, Minneapolis is speediest city
Mobile internet speeds are blazing fast these days thanks to 4G LTE, and they are about to get even faster with the impending roll-out of 5G. Not all carriers are created equally, however. In a new study by Ookla -- of Speedtest.net fame -- it is discovered that T-Mobile offers the fastest mobile internet overall in the USA. As you can expect, Sprint is dead last.
Ookla didn't just rank carriers, but cities too. After all, speed can vary by location since performance can be impacted by number of towers, terrain, and other factors. Shockingly, the overall fastest city in the USA is not New York or Los Angeles, but Minneapolis -- located in the cold state of Minnesota.

aLTEr: Hackers can spy on your 4G browsing sessions thanks to LTE flaws
Vulnerabilities have been discovered in LTE that would make it possible for an attacker to tap into 4G networks for the purposes of spying on and hijacking 4G browsing sessions.
Security researchers from Ruhr-Universität, Bochum and New York University, Abu Dhabi show how three different attacks can be launched on the second layer of LTE -- also known as the data link layer. Two passive attacks allow for identity mapping and website fingerprinting, while the active cryptographic aLTEr attack allows for DNS spoofing and network connection redirection.

One in every 17 mobile devices is used to conduct bad bot attacks
Cybercriminals are using mobile devices to avoid detection and execute a number of nefarious acts, according to a new report.
The study from bot mitigation specialist Distil Networks finds 5.8 percent -- around one in 17 -- of all mobile devices across six major cellular networks are used in such automated attacks and represent eight percent of all bad bot traffic.

T-Mobile is ready to launch FamilyMode to help parents monitor and control internet and device usage
Parents have concerns about not only how long their children spend online, but also what they are using various connected devices for. In just a few days' time, T-Mobile is launching its answer to the problem: FamilyMode.
This is a service that makes it possible to keep an eye on how long devices are being used for, and to monitor internet usage. FamilyMode uses a hardware base station and a mobile app (available for iOS and Android) to give parents monitoring and control over devices connected via either Wi-Fi or cellular.
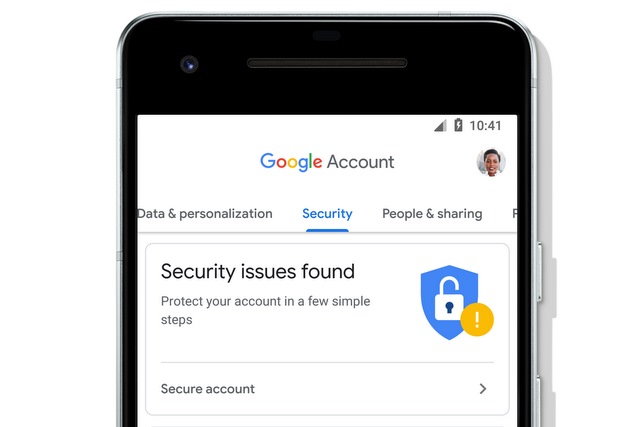
Google Account revamped -- increased transparency and new security and privacy options
Google has unveiled a new look for users' accounts, making information clearer, improving transparency and adding new options.
To make it easy to find information, Google has added a search function and there's also a cleaner look to aid navigation. Building on the previous update to Security Checkup, your Google account now also highlights settings you can change to improve your security.

Media and entertainment companies have riskier mobile apps
As the world increasingly turns to mobile devices to access the internet and conduct business, so firms are eager to put out their own apps.
But new research from security ratings company BitSight reveals that many companies may be rushing out apps that have vulnerabilities which could lead to data leakage, privilege abuse, unencrypted personally identifiable information (PII), and credential theft.

EE launches smart number technology, enabling customers to call and text across multiple devices with a single phone number
EE has announced the launch of a new smart number technology which enables its customers to use their phone number across multiple devices at no extra cost.
Initially, the service will be available to Apple users, giving them the option of using their iPhone, iPad, Apple Watch or Mac -- up to five devices in total -- to send and receive text messages, and place and receive phone calls. The same options will make their way to Android devices at some point in the future.

The challenges of securing mobile devices
Mobile devices now account for around half of web traffic and inevitably that makes them more attractive to hackers who see new attack routes via mobile apps.
The Information Security Forum is launching a new paper, Securing Mobile Apps: Embracing Mobile, Balancing Control, describing the security challenges associated with acquiring, using and operating mobile apps, and suggesting actions to manage those challenges, while maintaining the business benefits.

A third of IT professionals don't know how many endpoints they manage
A poll of 1,000 IT professionals across North America and Europe finds that while 88 percent of respondents acknowledge the importance of endpoint management, nearly a third don't know how many endpoints they actually manage.
The study by identity and access management company LogMeIn shows a worrying 30 percent of IT professionals don't know how many endpoint devices exist within their organization. Those who do report an average of 750 endpoints including servers, employee computers and mobile devices.

Cryptomining dominates mobile threat landscape
Threat actors are increasingly looking to exploit the popularity and volatility of cryptocurrency in their attacks on mobile devices according to a new report.
The latest Mobile Threat Landscape report from threat management specialist RiskIQ analyzed 120 mobile app stores and more than two billion daily scanned resources.

Enterprise data increasingly accessed from mobile devices
Enterprise users are increasingly authenticating into applications from non-office networks, with a 10 percent increase in the average number of unique networks according to the latest Trusted Access Report from Duo Security.
Duo also found that 43 percent of requests to access protected applications and data came from outside of the corporate office and network. People are logging into applications, networks and systems wherever, and whenever as work hours start to flex to fit different lifestyles, time zones and travel.
